This sample code is vulnerable to which of the following attacks? Select all that apply.
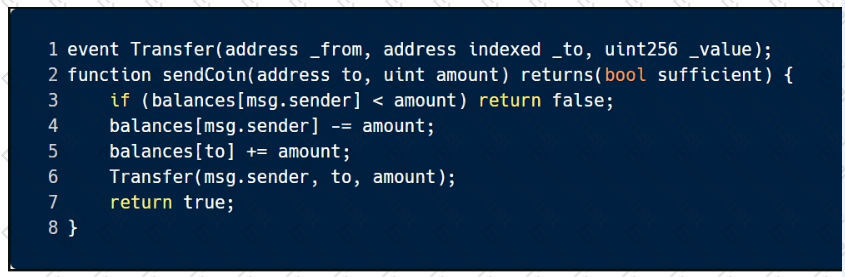
Which smart contract vulnerabilities can be exploited by a malicious miner? Select all that apply
Which smart contract auditing strategy involves graphing how the code executes and looks for anomalies?
Implementing data access as a blockchain smart contract is a good solution for generating an audit log of access to sensitive data
Data subject to deletion procedures should be stored encrypted on-chain.
Blockchain consensus algorithms use the scarcity of a resource and economic incentives to protect the security of the distributed ledger.
Which of the following does NOT rely on the security of public key cryptography?
Poorly designed smart contracts can only be disabled on the blockchain if this functionality was built in from the beginning
Which of the following blockchains separates transaction validation and ordering of transactions in blocks into separate steps?
Which of the following is a takenaway from the pigeocoin/Bitcom Core hack?
In which of the following attacks targeting Proof of Stake does an attacker create a divergent chain and race to make their chain longer than the real chain?
Using a distributed ledger decreases risk of data loss since all data is not stored in the same place.
Confidential Transactions prove that inputs and outputs ot a transaction are equal.