When do modifications to the Event Policy take effect?
When migrating the SmartEvent data base from one server to another, the first step is to back up the files on the original server. Which of the following commands should you run to back up the SmartEvent data base?
Which command allows you to view the contents of an R77 table?
Select the correct statement about Secure Internal Communications (SIC) Certificates. SIC Certificates:
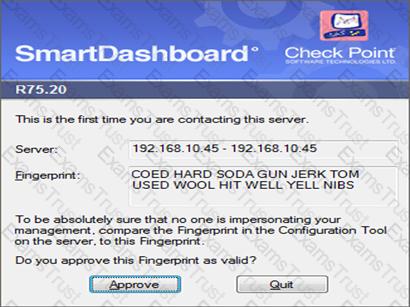
How could you compare the Fingerprint shown to the Fingerprint on the server?
Exhibit:
Fill in the blank. The user wants to replace a failed Windows-based firewall with a new server running GAiA. For the most complete restore of an GAiA configuration, he or she will use the command
Fill in the blank with a numeric value. The default port number for standard TCP connections with the LDAP server is
Which process should you debug if SmartDashboard login fails?
Study the Rule base and Client Authentication Action properties screen -
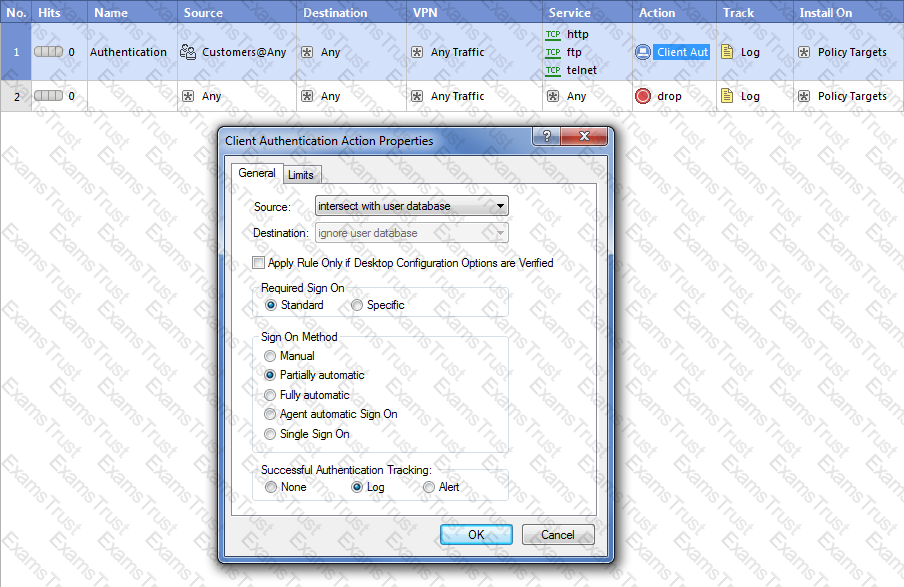
After being authenticated by the Security Gateway, when a user starts an HTTP connection to a Web site, the user tries to FTP to another site using the command line. What happens to the user? The:
You find that Users are not prompted for authentication when they access their Web servers, even though you have created an HTTP rule via User Authentication. Choose the BEST reason why.
Complete this statement from the options provided. Using Captive Portal, unidentified users may be either; blocked, allowed to enter required credentials, or required to download the _____________.
The Identity Agent is a lightweight endpoint agent that authenticates securely with Single Sign-On (SSO). What is not a recommended usage of this method?
Which of the following CLISH commands would you use to set the admin user's shell to bash?
You are troubleshooting a HTTP connection problem. You've started fw monitor -o http.pcap. When you open http.pcap with Wireshark there is only one line. What is the most likely reason?
Fill in the blank. You can set Acceleration to ON or OFF using command syntax ___________ .
Type the command and syntax to configure the Cluster Control Protocol (CCP) to use Broadcast.
Fill in the blank. To save your OSPF configuration in GAiA, enter the command ___________ .
You want to establish a VPN, using certificates. Your VPN will exchange certificates with an external partner. Which of the following activities should you do first?
What command syntax would you use to turn on PDP logging in a distributed environment?
What command syntax would you use to see accounts the gateway suspects are service accounts?
You cannot use SmartDashboard’s User Directory features to connect to the LDAP server. What should you investigate?
1) Verify you have read-only permissions as administrator for the operating system.
2) Verify there are no restrictions blocking SmartDashboard's User Manager from connecting to the LDAP server.
3) Check that the login Distinguished Name configured has root permission (or at least write permission Administrative access) in the LDAP Server's access control configuration.
As a Security Administrator, you must refresh the Client Authentication authorization time-out every time a new user connection is authorized. How do you do this? Enable the Refreshable Timeout setting:
Which of the following statements accurately describes the command upgrade_export?
Suppose the Security Gateway hard drive fails and you are forced to rebuild it. You have a snapshot file stored to a TFTP server and backups of your Security Management Server. What is the correct procedure for rebuilding the Gateway quickly?
A host on the Internet initiates traffic to the Static NAT IP of your Web server behind the Security Gateway. With the default settings in place for NAT, the initiating packet will translate the _________.
You are MegaCorp’s Security Administrator. There are various network objects which must be NATed. Some of them use the Automatic Hide NAT method, while others use the Automatic Static NAT method. What is the rule order if both methods are used together? Give the BEST answer.
Jennifer McHanry is CEO of ACME. She recently bought her own personal iPad. She wants use her iPad to access the internal Finance Web server. Because the iPad is not a member of the Active Directory domain, she cannot identify seamlessly with AD Query. However, she can enter her AD credentials in the Captive Portal and then get the same access as on her office computer. Her access to resources is based on rules in the R77 Firewall Rule Base.
To make this scenario work, the IT administrator must:
1) Enable Identity Awareness on a gateway and select Captive Portal as one of the Identity Sources.
2) In the Portal Settings window in the User Access section, make sure that Name and password login is selected.
3) Create a new rule in the Firewall Rule Base to let Jennifer McHanry access network destinations. Select accept as the Action.
Ms. McHanry tries to access the resource but is unable. What should she do?
John Adams is an HR partner in the ACME organization. ACME IT wants to limit access to HR servers to designated IP addresses to minimize malware infection and unauthorized access risks. Thus, the gateway policy permits access only from John's desktop which is assigned a static IP address 10.0.0.19.
John received a laptop and wants to access the HR Web Server from anywhere in the organization. The IT department gave the laptop a static IP address, but that limits him to operating it only from his desk. The current Rule Base contains a rule that lets John Adams access the HR Web Server from his laptop with a static IP (10.0.0.19). He wants to move around the organization and continue to have access to the HR Web Server.
To make this scenario work, the IT administrator:
1) Enables Identity Awareness on a gateway, selects AD Query as one of the Identity Sources installs the policy.
2) Adds an access role object to the Firewall Rule Base that lets John Adams PC access the HR Web Server from any machine and from any location.
What should John do when he cannot access the web server from a different personal computer?
Which of the following is NOT defined by an Access Role object?
Where do you verify that UserDirectory is enabled?