Refer to the exhibit.
A security analyst is investigating unusual activity from an unknown IP address Which type of evidence is this file1?
Refer to the exhibit.
Which application protocol is in this PCAP file?
What is the impact of false positive alerts on business compared to true positive?
An engineer discovered a breach, identified the threat’s entry point, and removed access. The engineer was able to identify the host, the IP address of the threat actor, and the application the threat actor targeted. What is the next step the engineer should take according to the NIST SP 800-61 Incident handling guide?
An analyst is investigating a host in the network that appears to be communicating to a command and control server on the Internet. After collecting this packet capture, the analyst cannot determine the technique and payload used for the communication.
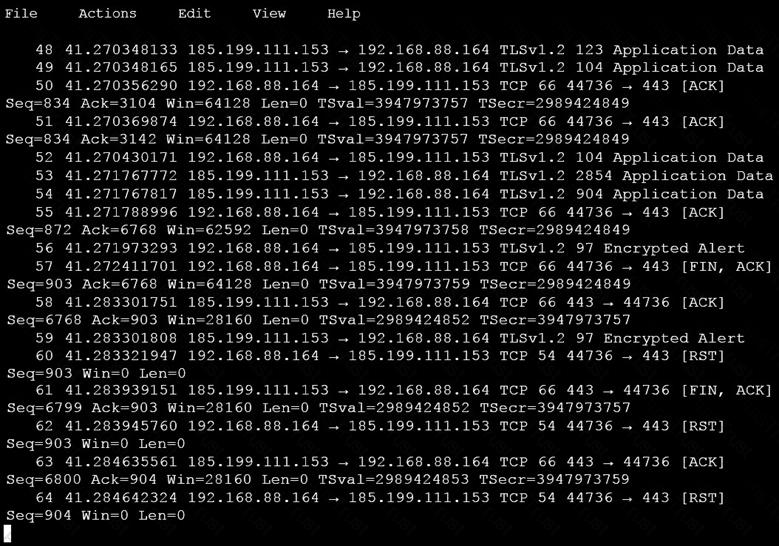
Which obfuscation technique is the attacker using?
Refer to the exhibit.
What is the potential threat identified in this Stealthwatch dashboard?
Which are two denial-of-service attacks? (Choose two.)
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
What does cyber attribution identify in an investigation?
What is the principle of defense-in-depth?
An analyst is using the SIEM platform and must extract a custom property from a Cisco device and capture the phrase, "File: Clean." Which regex must the analyst import?
Refer to the exhibit.
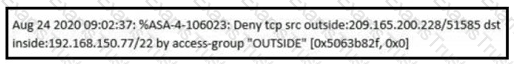
An analyst received this alert from the Cisco ASA device, and numerous activity logs were produced. How should this type of evidence be categorized?
What describes the impact of false-positive alerts compared to false-negative alerts?
Drag and drop the data source from the left onto the data type on the right.
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
Drag and drop the event term from the left onto the description on the right.
Refer to the exhibit.
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
What is a difference between SOAR and SIEM?
Refer to the exhibit.
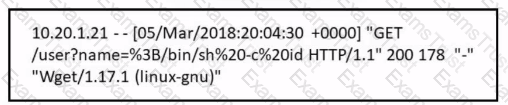
Which attack is being attempted against a web application?
What is the difference between the rule-based detection when compared to behavioral detection?
An engineer is investigating a case of the unauthorized usage of the “Tcpdump” tool. The analysis revealed that a malicious insider attempted to sniff traffic on a specific interface. What type of information did the malicious insider attempt to obtain?
What is a difference between a threat and a risk?
Which action matches the weaponization step of the Cyber Kill Chain Model?
An engineer must configure network systems to detect command-and-control communications by decrypting ingress and egress perimeter traffic and allowing network security devices to detect malicious outbound communications. Which technology must be used to accomplish this task?
How does an attack surface differ from an attack vector?
Which tool provides a full packet capture from network traffic?
What are the two characteristics of the full packet captures? (Choose two.)
Refer to the exhibit.
What is occurring within the exhibit?
Refer to the exhibit.
During the analysis of a suspicious scanning activity incident, an analyst discovered multiple local TCP connection events Which technology provided these logs?
Refer to the exhibit.
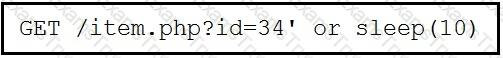
This request was sent to a web application server driven by a database. Which type of web server attack is represented?
Drag and drop the uses on the left onto the type of security system on the right.
Drag and drop the security concept on the left onto the example of that concept on the right.
At which layer is deep packet inspection investigated on a firewall?
Refer to the exhibit. An attacker scanned the server using Nmap. What did the attacker obtain from this scan?
Drag and drop the technology on the left onto the data type the technology provides on the right.
Refer to the exhibit.
What is depicted in the exhibit?
Which metric in CVSS indicates an attack that takes a destination bank account number and replaces it with a different bank account number?
Which two measures are used by the defense-m-depth strategy? (Choose two)
Which event is a vishing attack?
Refer to the exhibit.
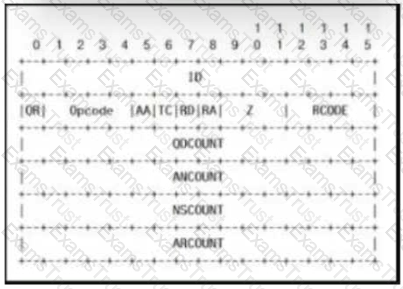
Which field contains DNS header information if the payload is a query or a response?
Which two elements of the incident response process are stated in NIST SP 800-61 r2? (Choose two.)
What is a comparison between rule-based and statistical detection?
Drag and drop the definition from the left onto the phase on the right to classify intrusion events according to the Cyber Kill Chain model.
An engineer receives a security alert that traffic with a known TOR exit node has occurred on the network. What is the impact of this traffic?
Refer to the exhibit.
An engineer is reviewing a Cuckoo report of a file. What must the engineer interpret from the report?
Which step in the incident response process researches an attacking host through logs in a SIEM?
What do host-based firewalls protect workstations from?
What matches the regular expression c(rgr)+e?
Which metric should be used when evaluating the effectiveness and scope of a Security Operations Center?
What is the practice of giving employees only those permissions necessary to perform their specific role within an organization?
Which system monitors local system operation and local network access for violations of a security policy?
Why should an engineer use a full packet capture to investigate a security breach?
What does an attacker use to determine which network ports are listening on a potential target device?
What are the two differences between stateful and deep packet inspection? (Choose two )
According to CVSS, what is a description of the attack vector score?
Refer to the exhibit.
What is occurring?
A user received an email attachment named "Hr405-report2609-empl094.exe" but did not run it. Which category of the cyber kill chain should be assigned to this type of event?
A security engineer has a video of a suspect entering a data center that was captured on the same day that files in the same data center were transferred to a competitor.
Which type of evidence is this?
Refer to the exhibit.
Which technology produced the log?
What is a description of a social engineering attack?
Which technique is a low-bandwidth attack?
What is a difference between tampered and untampered disk images?
How can TOR impact data visibility inside an organization?
Refer to the exhibit. An employee received an email from an unknown sender with an attachment and reported it as a phishing attempt. An engineer uploaded the file to Cuckoo for further analysis. What should an engineer interpret from the provided Cuckoo report?
What is the impact of false positive alerts on business compared to true positive?
Which attack method intercepts traffic on a switched network?
Which event is a vishing attack?
What is a difference between SI EM and SOAR security systems?
An engineer is working with the compliance teams to identify the data passing through the network. During analysis, the engineer informs the compliance team that external penmeter data flows contain records, writings, and artwork Internal segregated network flows contain the customer choices by gender, addresses, and product preferences by age. The engineer must identify protected data. Which two types of data must be identified'? (Choose two.)
How does agentless monitoring differ from agent-based monitoring?
An employee received an email from a colleague’s address asking for the password for the domain controller. The employee noticed a missing letter within the sender’s address. What does this incident describe?
Which two elements are used for profiling a network? (Choose two.)
Which regular expression matches "color" and "colour"?
What is a purpose of a vulnerability management framework?
What is the difference between the ACK flag and the RST flag in the NetFlow log session?
Drag and drop the elements from the left into the correct order for incident handling on the right.
What is an incident response plan?
What is obtained using NetFlow?
What is the difference between vulnerability and risk?
Refer to the exhibit.
Which component is identifiable in this exhibit?
What is the difference between mandatory access control (MAC) and discretionary access control (DAC)?
A system administrator is ensuring that specific registry information is accurate.
Which type of configuration information does the HKEY_LOCAL_MACHINE hive contain?
A security engineer notices confidential data being exfiltrated to a domain "Ranso4134-mware31-895" address that is attributed to a known advanced persistent threat group The engineer discovers that the activity is part of a real attack and not a network misconfiguration. Which category does this event fall under as defined in the Cyber Kill Chain?
What is the difference between inline traffic interrogation (TAPS) and traffic mirroring (SPAN)?
A user reports difficulties accessing certain external web pages. When an engineer examines traffic to and from the external domain in full packet captures, they notice that many SYNs have the same sequence number, source, and destination IP address, but they have different payloads. What is causing this situation?
Refer to the exhibit.
Which frame numbers contain a file that is extractable via TCP stream within Wireshark?
An analyst is investigating an incident in a SOC environment. Which method is used to identify a session from a group of logs?
After a large influx of network traffic to externally facing devices, a security engineer begins investigating what appears to be a denial of service attack When the packet capture data is reviewed, the engineer notices that the traffic is a single SYN packet to each port Which type of attack is occurring?
What is the difference between discretionary access control (DAC) and role-based access control (RBAC)?
Refer to the exhibit.
An engineer received a ticket about a slowed-down web application. The engineer runs the #netstat -an command. How must the engineer interpret the results?
A malicious file has been identified in a sandbox analysis tool.
Which piece of information is needed to search for additional downloads of this file by other hosts?
An employee reports that someone has logged into their system and made unapproved changes, files are out of order, and several documents have been placed in the recycle bin. The security specialist reviewed the system logs, found nothing suspicious, and was not able to determine what occurred. The software is up to date; there are no alerts from antivirus and no failed login attempts. What is causing the lack of data visibility needed to detect the attack?
Which evasion technique is a function of ransomware?
In a SOC environment, what is a vulnerability management metric?
What is the difference between inline traffic interrogation and traffic mirroring?
Which regular expression is needed to capture the IP address 192.168.20.232?
Which items is an end-point application greylist used?
What does an attacker use to determine which network ports are listening on a potential target device?
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?