What are two key capabilities of Cisco Finesse? (Choose two.)
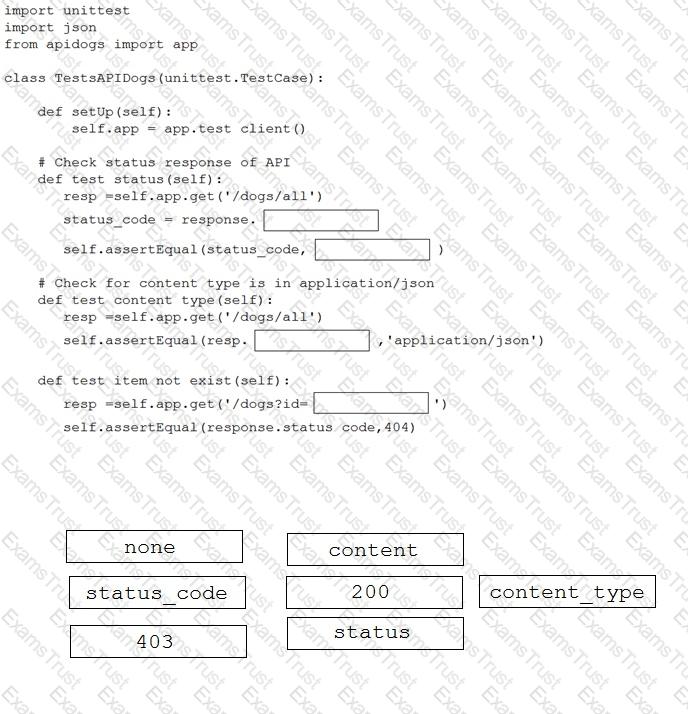
Drag and drop the code snippets from the bottom to the blanks in the code to test the API response through the Python unittest library. Not all options are used.
Refer to the exhibit.
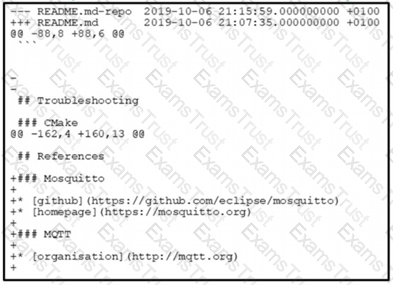
The output of the diff-u README.md-repo README.md command is shown. The original file was 165 lines long How many lines are in the edited copy of the file?
A file that already exists in a local repository is updated. Which command must be executed to ensure that the changes in the file are included in the next Git commit?
What is a requirement when authenticating a RESTCONF API session with a router that runs Cisco IOS XE Software?
Which Cisco platform provides organization-wide automation, security, policy enforcement, any agility across wired and wireless networks?
Refer to the exhibit.

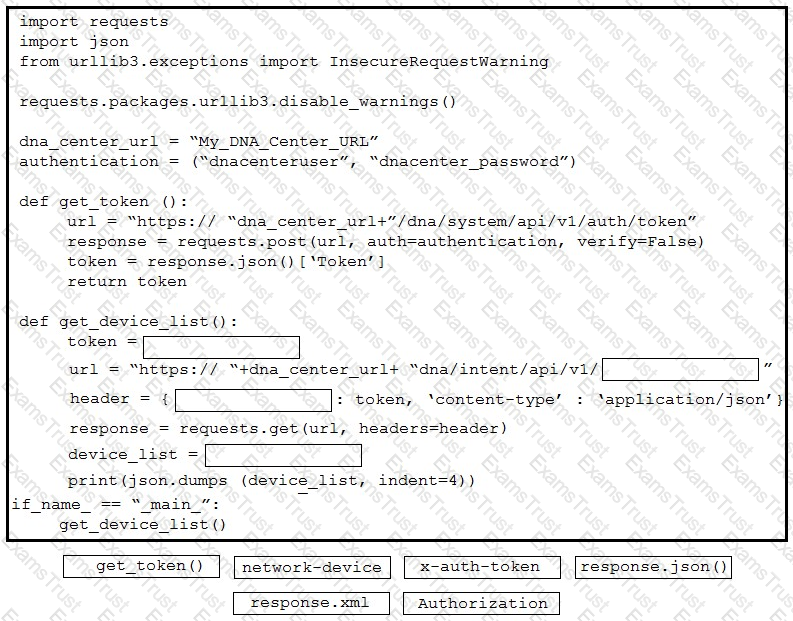
A developer creates a script to obtain a list of devices by using the Cisco DNA Center API. The remote server authorizes the request only if an authentication token is supplied in the headers. A function named get_auth_token() must retrieve a valid token by using HTTP Basic Authentication. Which code must be added to complete the get_auth_token() function?
A developer creates a script that configured multiple Cisco IOS XE devices in a corporate infrastructure. The internal test environment is unavailable, and no maintenance window is available to test on a low-priority production environment. Which resource is used to test the code before it is applied to the production environment?
How does a developer create and switch to a new branch called "my-bug-fix" to develop a product fix?
What is a benefit of model-driven programmability?
Which implementation creates a group of devices on one or more LANs that are configured to communicate as if they were attached to the same wire?
Which Cisco product provides malware and content filtering through DNS?
What are two functions of a routing table on a network device? (Choose two.)
Which tool is used to block all traffic to the domain by using a single API call?
Into which type of Python data structure should common data formats be parsed?
What are two considerations when selecting the "best route" for a network device to reach its destination? (Choose two.)
What is a functionality of the Waterfall method as compared to the Agile method for software development?
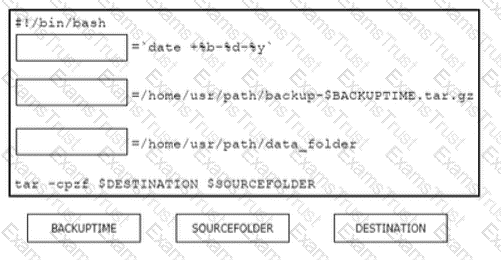
Drag and drop the code from the bottom onto the box where the code is missing in the Bash script to complete the missing assignment.
Refer to the exhibit.
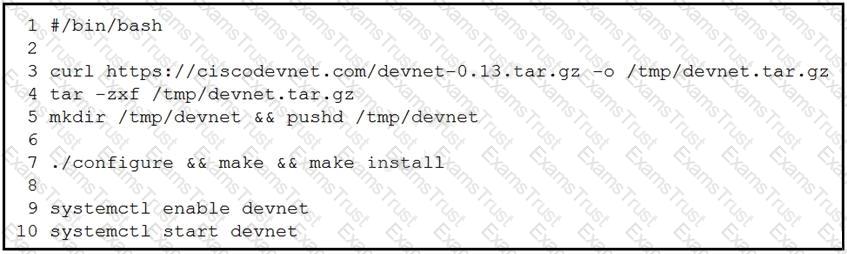
A network engineer works on a Cisco DevNet application that is available for download on the Cisco DevNet website. The engineer prepares a bash script to automate operations that relate to the application. Which workflow is being automated in the bash script?
What is a capability of the NETCONF protocol?
Which HTTP code group is issued when a request is received successfully, understood, and processed?
Refer to the exhibit.
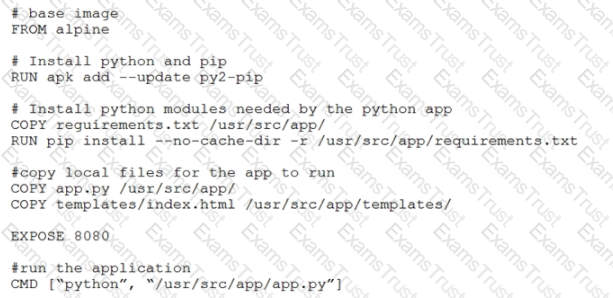
Which function does the EXPOSE line perform when building an image from this Dockerfile?
Which application should be used to externally access all applications deployed in the same host machine with a single public IP address and port, when each application listens on different local ports?
How are load balancers used in modern application deployment?
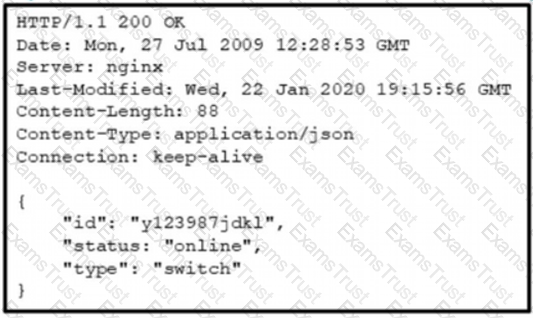
Which data is specified in the response header?
A developer needs a list of clients connected to a specific device in a Meraki network. After making a REST API call, the developer receives an unfamiliar response code. Which Cisco DevNet resource should be used to identify the meaning of the response code?
In the test-driven development model, what is changed after a test fails?
Refer to the exhibit.
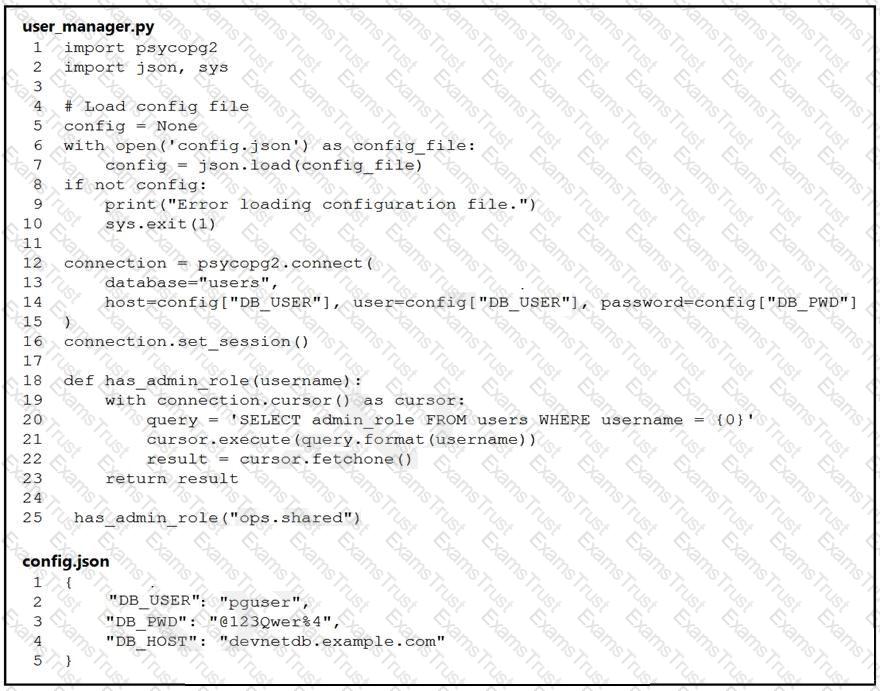
An engineer must check the admin rights of users on a database regularly and prepares
the Python script to automate the process. The script connects to the database and runs a query. What is a security issue about the secrets in the code that relates to secret protection?
Refer to the exhibit.
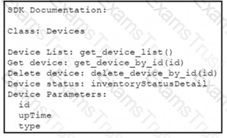
A Python script must delete all Cisco Catayst 9300 Series switches that have an uptime that is greater than 90 days The script must also query for the status of all the other devices Drag and drop the code from the bottom onto the bottom box the code is missing to complete the script Not at options are used

Several teams at a company are developing a new CRM solution to track customer interactions with a goal of improving customer satisfaction and driving higher revenue. The proposed solution contains these components:
• MySQL database that stores data about customers
• HTML5 and JavaScript UI that runs on Apache
• REST API written in Python
What are two advantages of applying the MVC design pattern to the development of the solution? (Choose two.)
Refer to the exhibit.
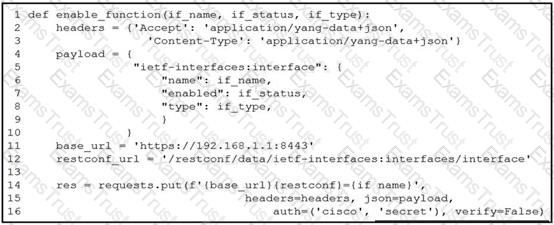
A network engineer wants to automate the port enable/disable process on specific Cisco switches. The engineer creates a script to send a request through RESTCONF and uses ietf as the YANG model and JSON as payload. Which command enables an interface named Loopback1?
Refer to the exhibit.
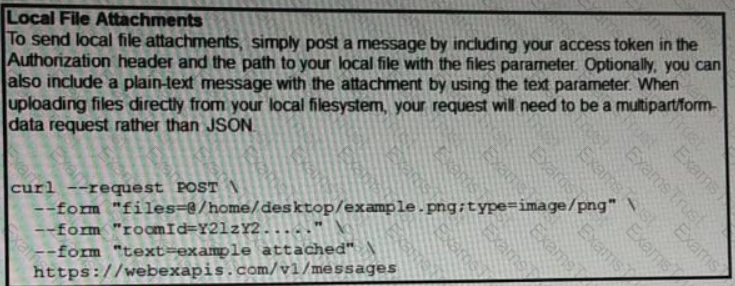
A developer needs to upload a local file by using the REST API. The developer gathers information according to the documentation and sends the request by using the cURL command in the exhibit but gets an error code. Which action should be followed to get valid response?
Which HTTP response status code means “Forbidden”?
What are two benefits of using VLANs? (Choose two.)
Which configuration management tool has an agentless capability?
In test-driven development, what are two of the green bar patterns? (Choose two.)
Refer to the exhibit.
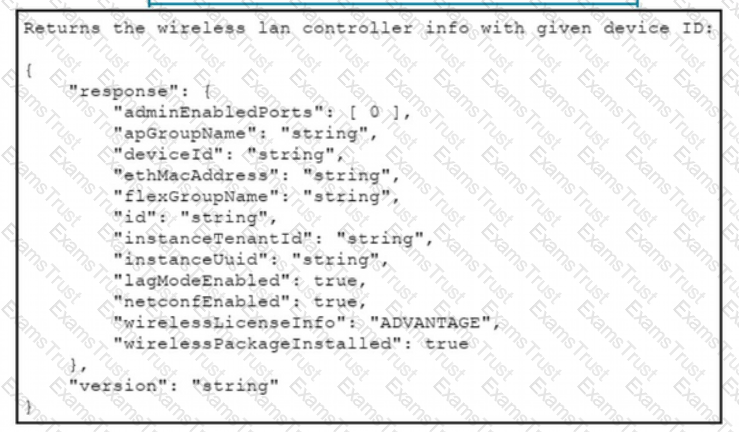
Drag and drop the code from the bottom onto the blanks in the code to construct a cURL command using the Cisco DNA Center API. which will provide the details of a WLAN controller with Id af397748444. Not at options are used.
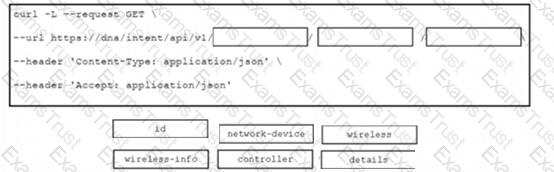
Refer to the exhibit.
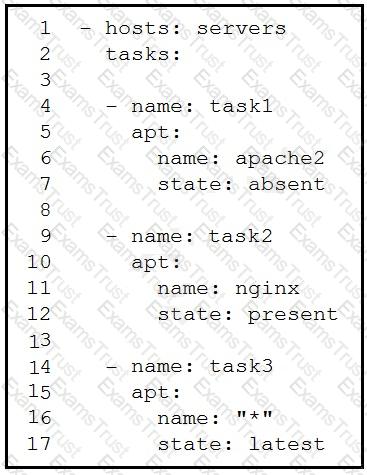
A developer must check packages on web load balancers that use nginx packages. The developer updates the servers as required in Ansible inventory and prepares an Ansible playbook to automate this workflow on related servers. Which process is being automated by the Ansible playbook?
Refer to the exhibit.
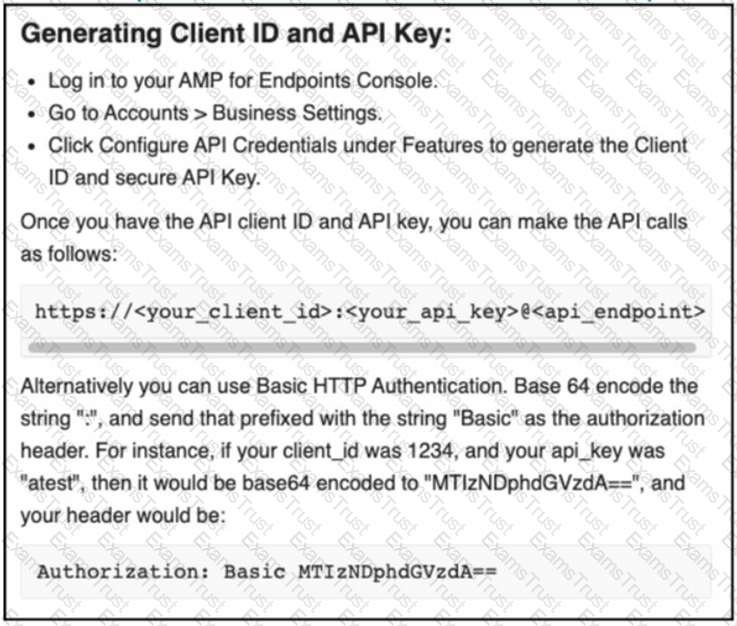
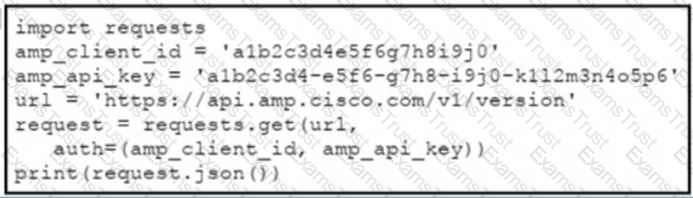
The documentation outlines how to use credentials for the AMP API Which script successfully performs an API call using basic authentication?
A)
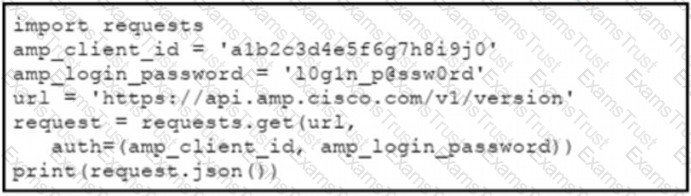
B)
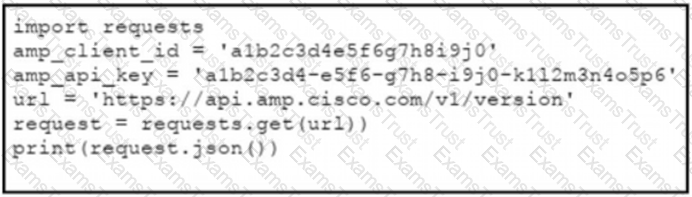
C)
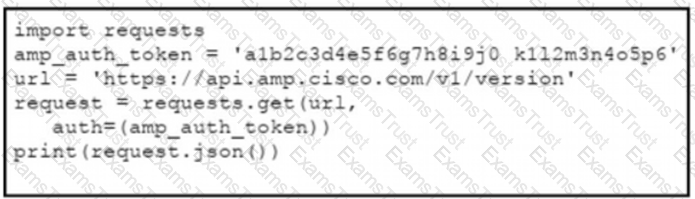
D)
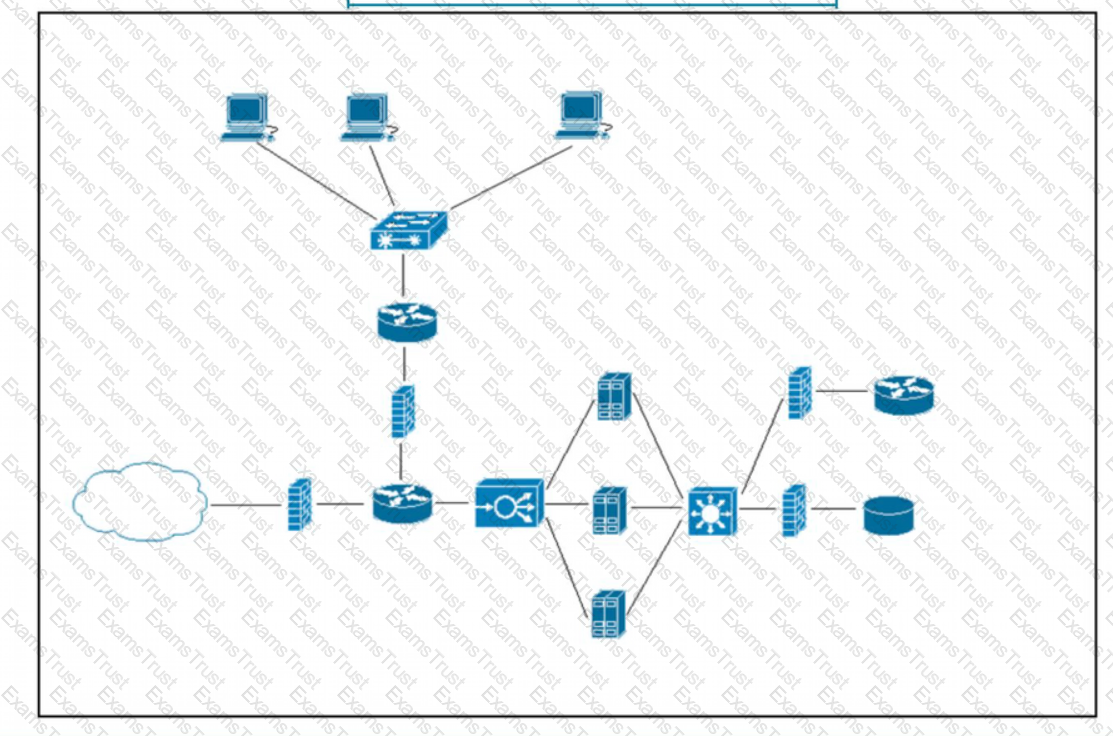
Refer to the exhibit. What does the load balancer enable in the network topology?
Refer to the exhibit.
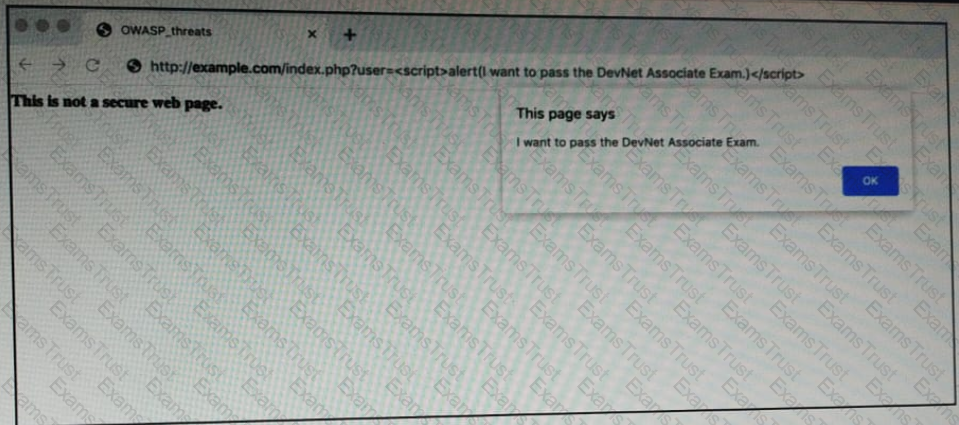
OWASP threat does this example demonstrate?
Refer to the exhibit.
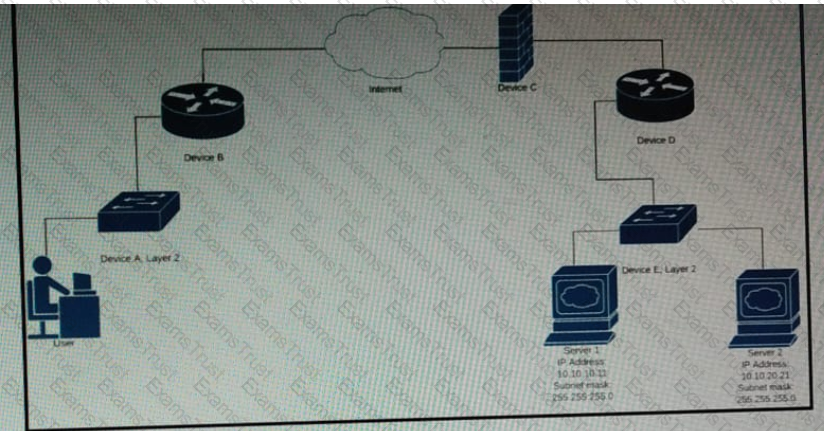
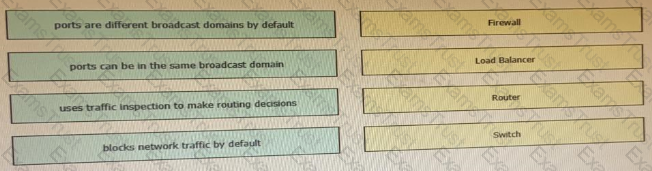
Which device limits traffic between server 1 and server 2?
Refer to the exhibit.
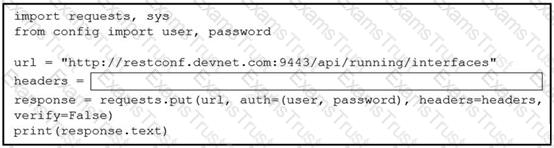
A network engineer wants to use an API to update information about device interfaces. The network devices are deployed in a Cisco DevNet Sandbox and have running interfaces. Which line of code needs to be placed in the snippet where the code is missing?
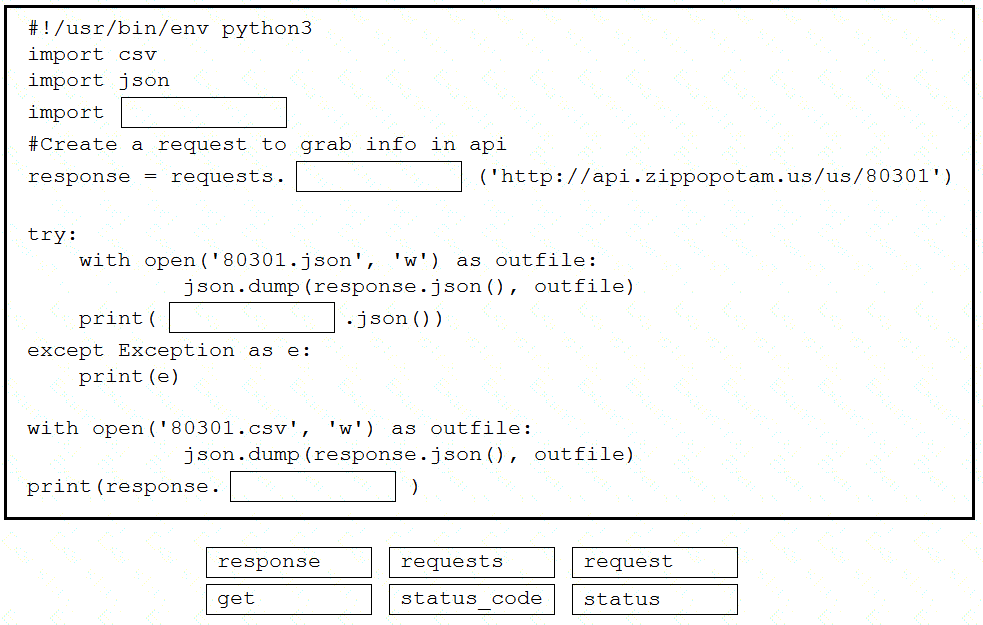
Drag and drop the code snippets from the bottom into the Python script to write API output to a csv file. Not all options are used.
While developing a real-Time VoIP application on a Cisco Webex platform, users report that their voice gets chopped or parts of the conversation drop out. Which network constraint is impacting the application?
An engineer must configure Cisco Nexus devices and wants to automate this workflow. The engineer enables the Cisco NX-OS REST API to configure the devices by using an Ansible playbook. Before running the code,
which resource must be used to verify that the code works correctly?
What does a load balancer distribute in a network environment?
What operation is performed with YANG model-driven programmability in NX-OS?
Which REST architectural constraint indicates that no client context should be stored on the server between requests?
Which network device monitors incoming and outgoing traffic and decides whether to allow or block specific traffic based on a defined set of rules?
Refer to the exhibit.
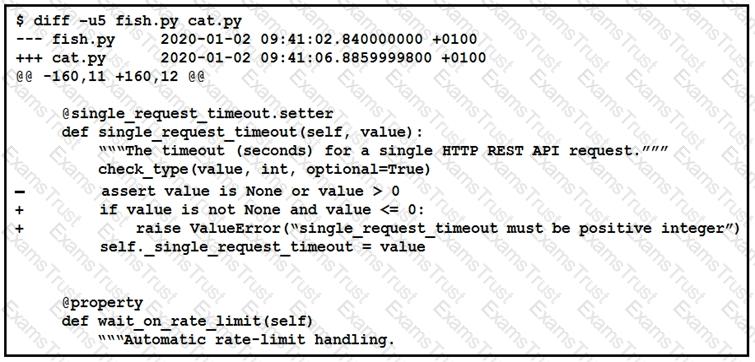
The output of a unified diff when comparing two versions of a python script is shown. Which two “single_request _timeout ()”
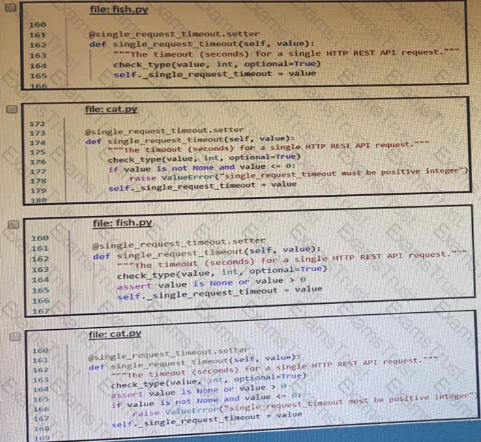
What is the purpose of the Cisco VIRL software tool?
Which platform is run directly using a hypervisor?
Refer to the exhibit.
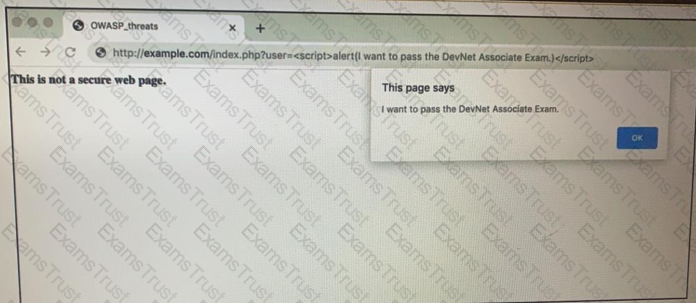
Which OWASP threat does this example demonstrate?
Refer to the exhibit.
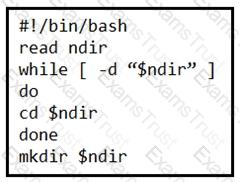
What is the action of the Bash script that is shown?
What are two advantages of YANG-based approaches for infrastructure automation? (Choose two.)
A Company is looking for cloud deployment which will use the on-premise infrastructure, is user self-service, and easy to scale. Which cloud solution should be selected for these requirements?
Which two use cases are supported by Meraki APIs? (Choose two.)
Refer to the exhibit.
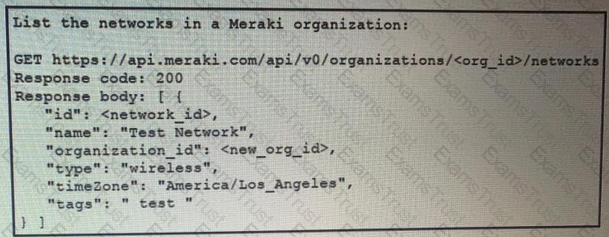
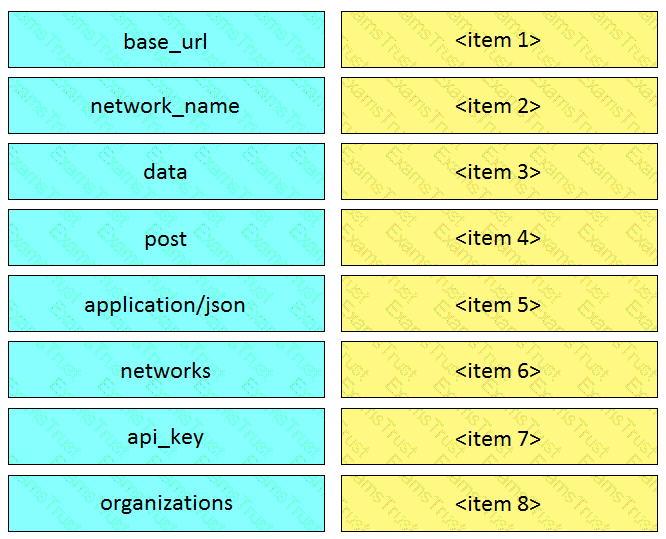
Fill in the blanks to complete the cURL command to the list of networks in the Meraki organization with an id of 384279060
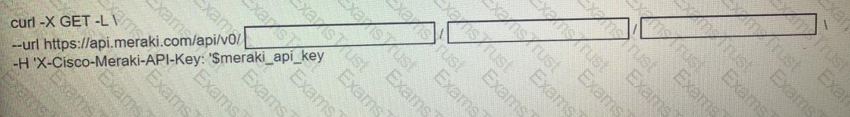
Which status code is used by a REST API to indicate that the submitted payload is incorrect?
A company has written a script that creates a log bundle from the Cisco DNA Center every day. The script runs without error and the bundles are produced. However, when the script is run during business hours, report poor voice quality of phones calls. What explains this behavior?
Refer to Exhibit.
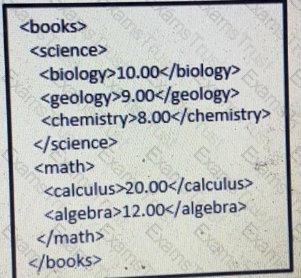
Which JSON is equivalent to the XML-encoded data.
A)

B)
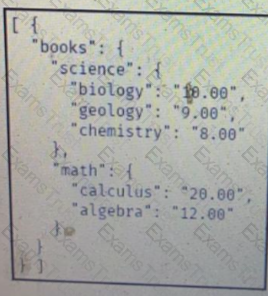
C)
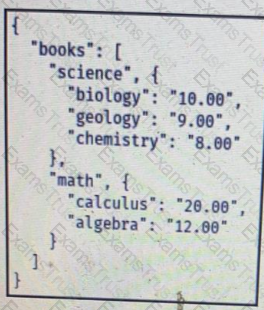
D)
Refer to the exhibit.
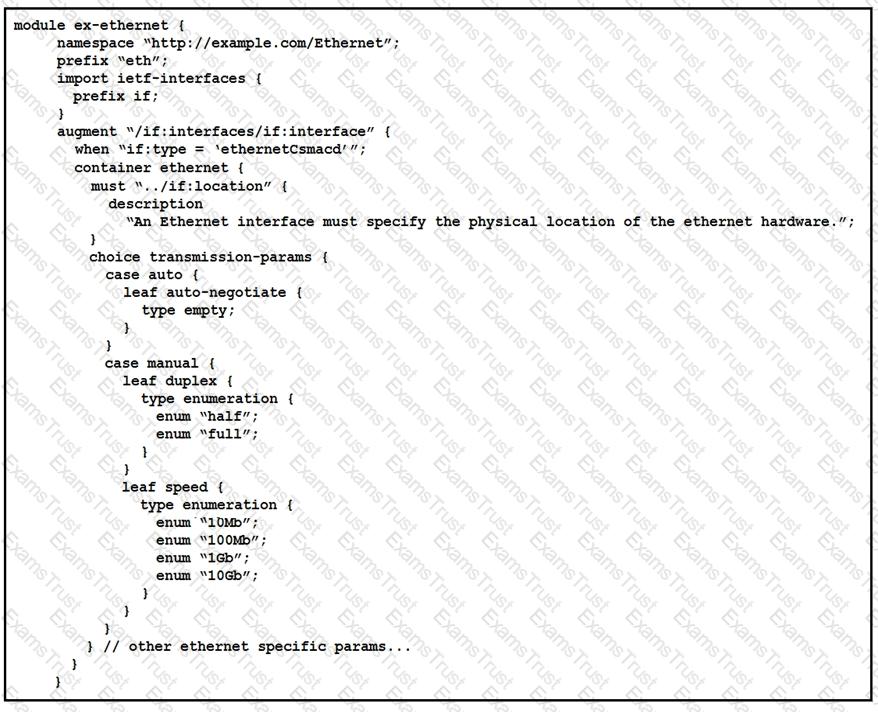
What is represented in this YANG module?
Which two statements describe the traits of an asynchronous API call? (Choose two.)
Which two statements are true about Cisco UCS manager, Cisco Intersight APIs? (Choose two.)
What is the Git command to delete a local branch named “experiment” without a warning?
Drag and drop the Python code from the left onto the correct step on the right to call a REST API.
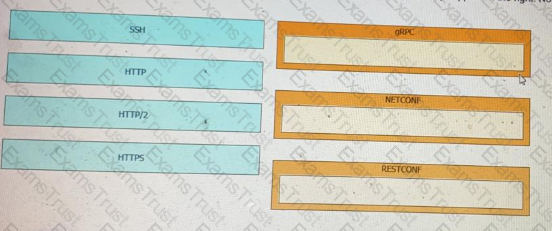
Drag and drop the network automation interfaces from the left onto the transport protocols that they support on the right. Not all options are used.
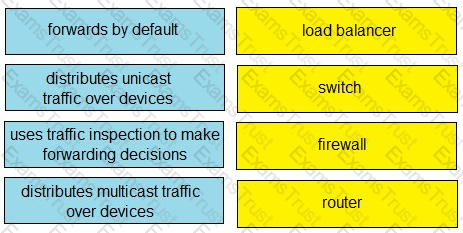
Drag and drop the functionalities from the left onto correct networking devices on the right.
When using the Bash shell, how it the output of the devnet command saved to a tile named “output.txt”?
In python, which expression checks whether the script returns a success status code when the Requests library is used?
Refer to the exhibit.
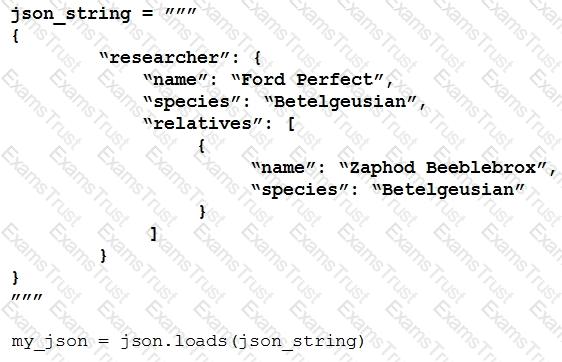
Which python data structure does my_json contain?
Fill in the blanks to complete the cURL command that invokes a RESTful API to retrieve a resource in JSON format using OAuth.

Which type of threat occur when an attacker can send hostile data to an interpreter within an application?
Refer to the exhibit.
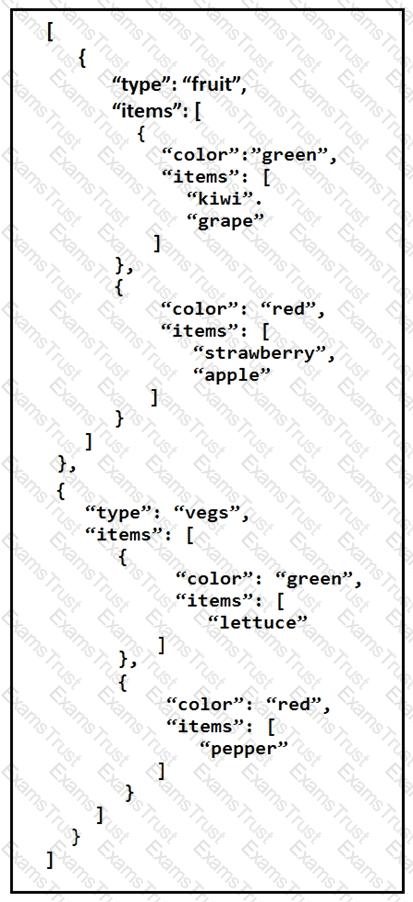
A REST API retune this JSON output for a GET HTTP request, Which has assigned to a variable called “vegetables” Using python, which output is the result of this command?

Refer to the exhibit.
A process on the host wants to access the service running inside this Docker container. Which port is used to make a connection?
Which description of a default gateway if true?
An application calls a REST API and expects a result set of more than 550 records, but each time the call is made, only 25 are returned. Which feature limits the amount of data that is returned by the API?
Refer to the exhibit.
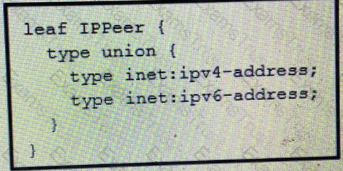
What is the value of the node defined by this YANG structure?
Which Cisco DevNet resource allows access to products in a development lab to explore, learn, and build application that use Cisco APLs?
Refer to the exhibit.
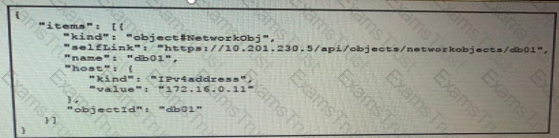
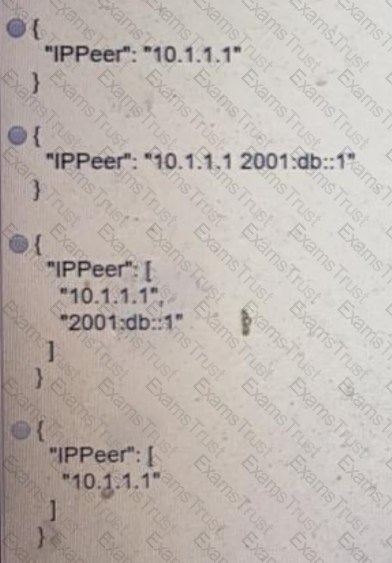
The JSON data in the exhibit has been parsed and stored in a variable, “data”. What returns the value “172.16.0.11” ?
Refer to the exhibit.
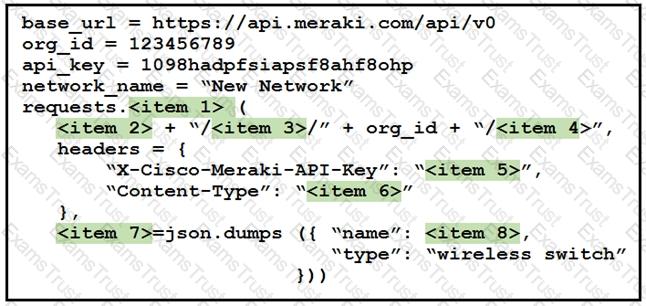
Drag and drop the code from the left onto the item numbers on the right to complete to Meraki python script shown in the exhibit.
What are the two purposes for using a VLAN in a network? (Choose two)
Refer to the exhibit.
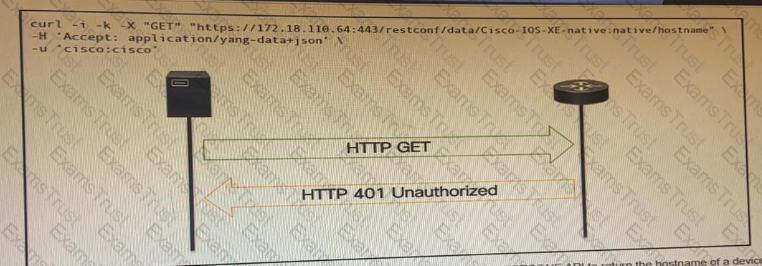
OR
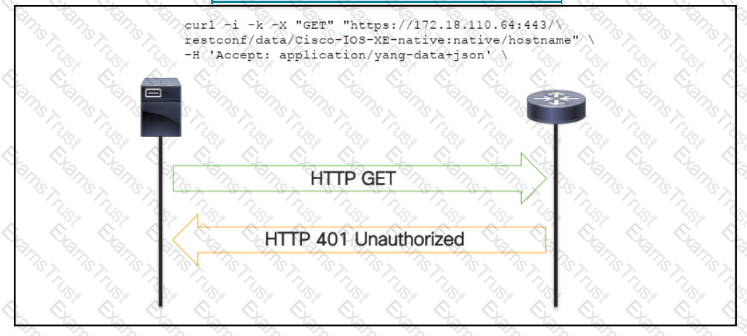
An administrator attempts to perform a GET using the Cisco IOS XE RESTOCNF API to return the hostname of a device. The sequence diagram illustrated the HTTP message observed. Which change to the API request resolves the issue?
Which two NETCONF operations cover the RESTCONF GET operation? (Choose two.)
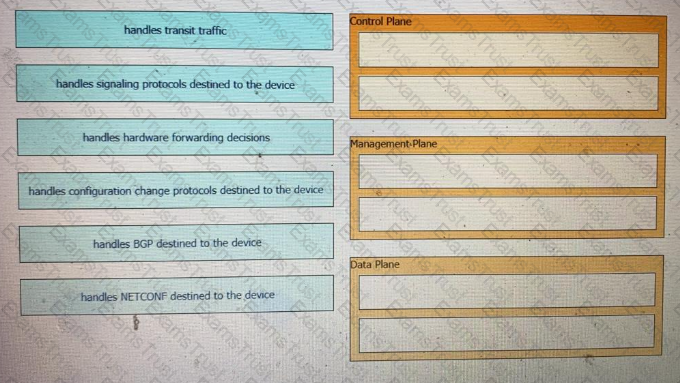
Drag and drop the function on the left onto the type of plane that handles the function on the right.
What is the purpose of a MAC address?
Fill in the blanks to complete the statement.
Cisco DNA provide the capability to send an HTTP _______________ request to the API endpoint and receive the network __________ list in __________ format.
On which port does NETCONF operate by default?
Which two descriptions can be given to an application that is interacting with a webhook? (Choose two.)
what is an advantage of a version control system?
Refer to the exhibit.
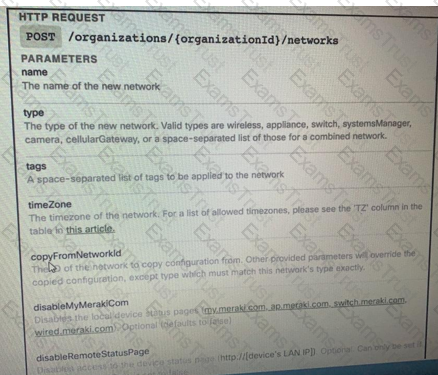
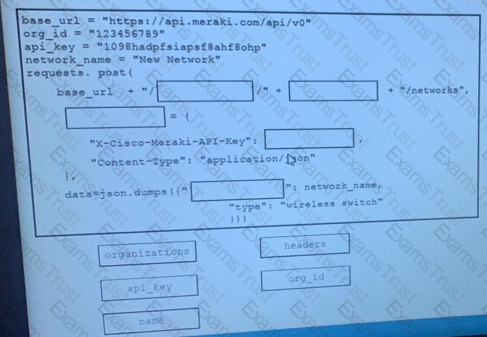
Drag and Drop the code from the bottom onto the box where the code is missing on the Meraki Python script to create a new network
What is the purpose of a firewall in application deployment?
An automation script fails to connect to an internal server exactly 1 out of 2 times it is executed. This behavior is seen from different clients. Which networking device mut be at fault?
A team of developers is responsible for a network orchestration application in the company. The responsibilities also include:
developing and improving the application in a continuous manner
deployment of the application and management of CI/CD frameworks
monitoring the usage and problems and managing the performance improvements
Which principle best describes this DevOps practice?
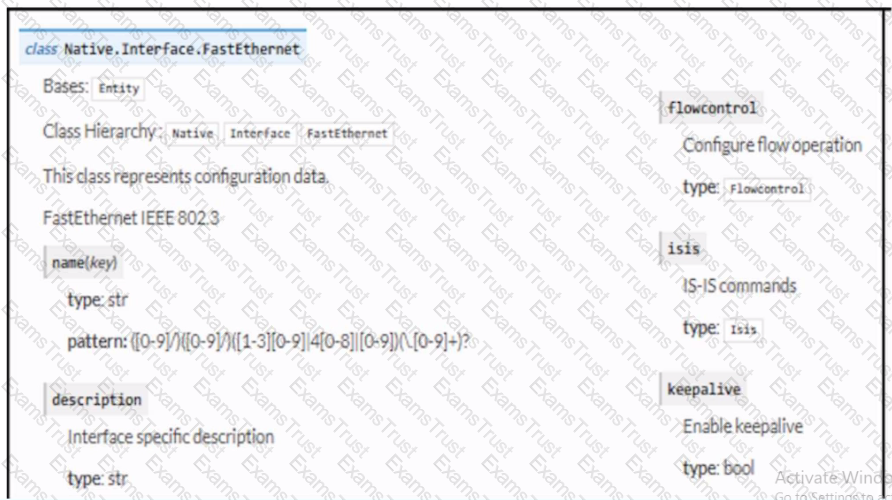
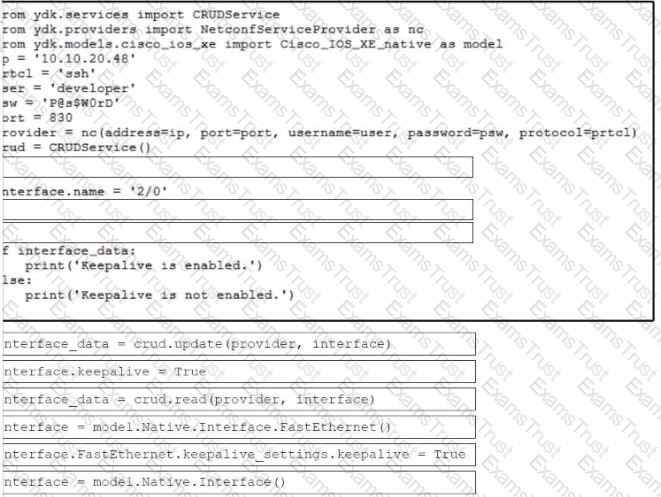
Refer to the exhibit. Drag and drop the code snippets from the bottom to the blanks in the code to enable keepalive for the FastEthernet 2/0 interface. Not all options are used.
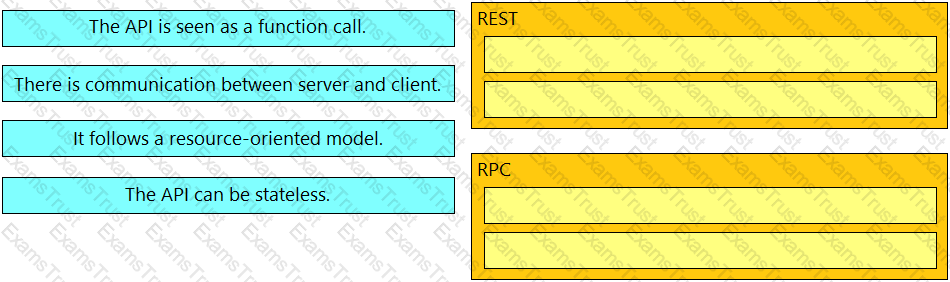
Drag and drop the API characteristics from the left onto the categories on the right.
What is an advantage of device-level management as compared to controller-level management to automate the configuration of network devices?
Which function does a router provide to a network?
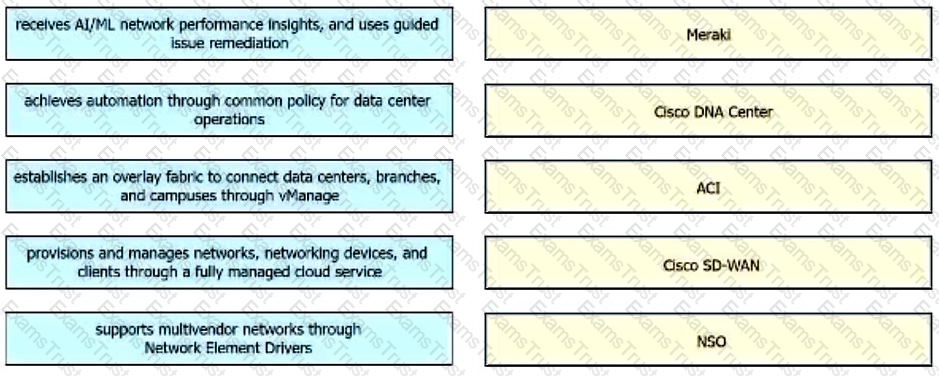
Drag and drop the capabilities from the left onto the Cisco Network Management Platforms that support the capabilities on the right.
Which network component enables communication between broadcast domains?
Drag and drop the functions from the left onto the networking devices on the right.

Refer to the exhibit. Which action does the script perform?
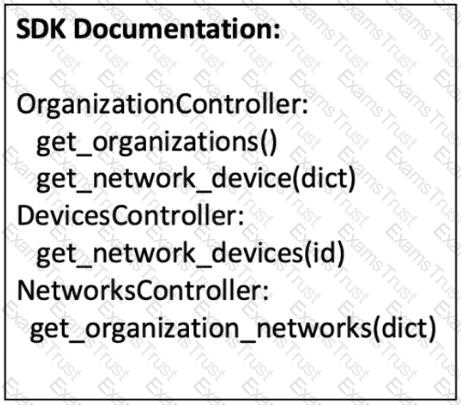
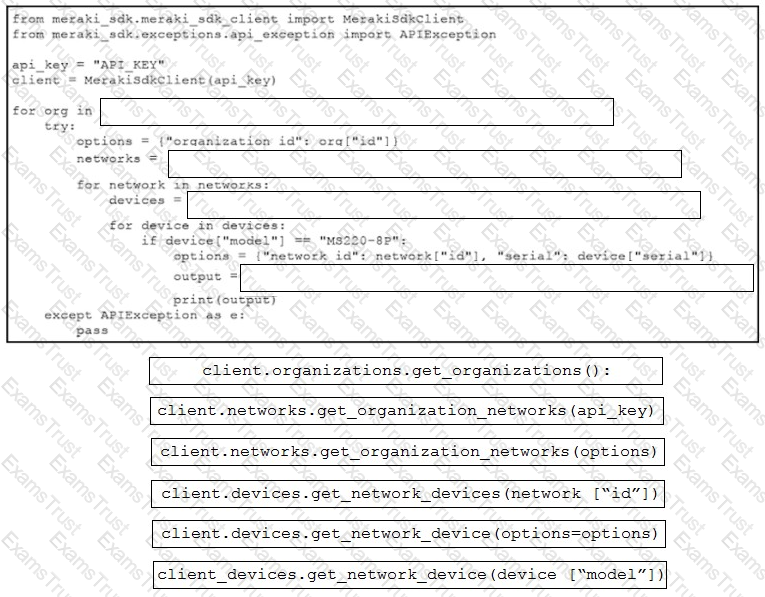
Refer to the exhibit. A script must output details of all the Cisco Meraki MS220-BP switches across all organizations and networks. Drag and drop the code snippets from the bottom onto the boxes in the code to complete the script. Not all options are used.
A developer must test the performance and reliability of an application. After functional and load tests are run, the application crashes due to traffic spikes from users. Which type of API constraint must be implemented to maintain reliability?

Refer to the exhibit. An engineer must authorize a REST API call. The API password is "Cisco123!". Which Bash command must be placed in the code to authorize the call?
Refer to the exhibit.
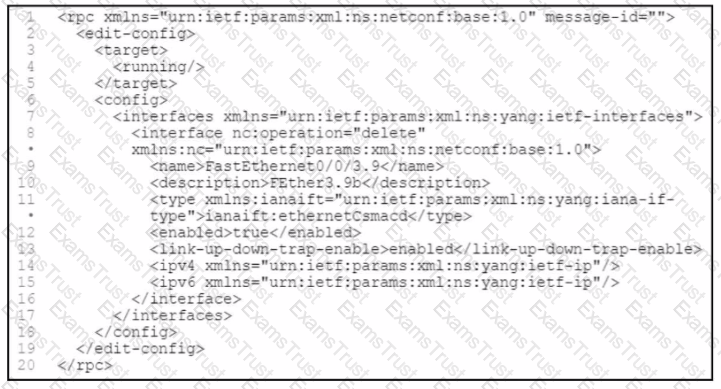
Refer to the exhibit.
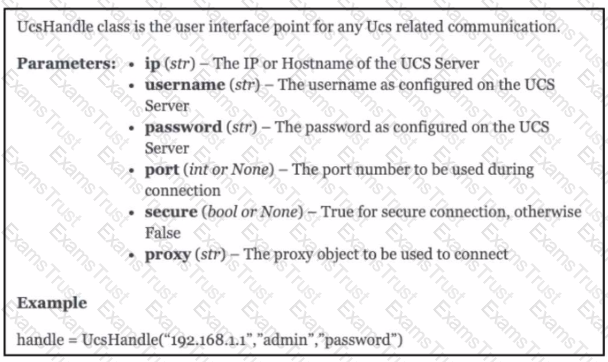
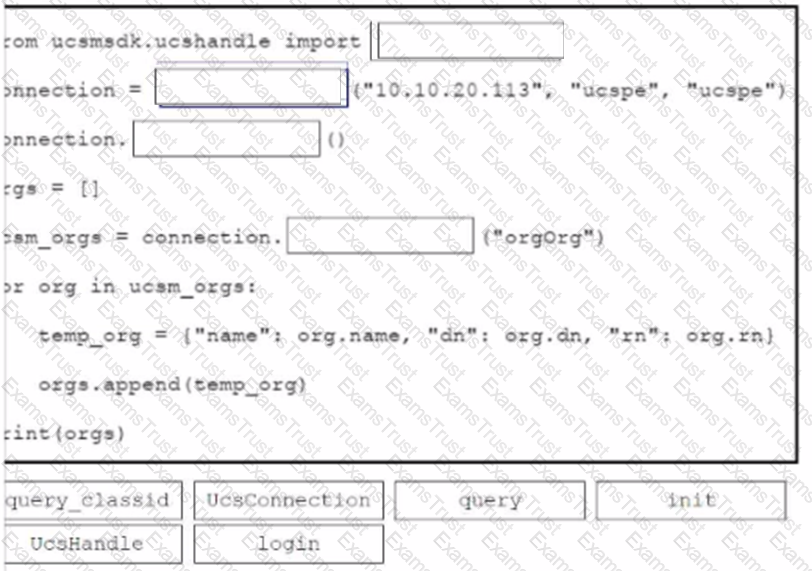
An engineer needs to retrieve all the organizations in a Cisco UCS Manager deployment. Drag and drop the code snippets from the bottom onto the blanks in.. Python script to print the information to standard output. Some options may be used more than once. Not all options are used.
An engineer must review and clean up a code repository. During the review, the engineer finds a file named config.json that contains API URLs, shared keys, and other application configurations. Which two methods, according to best practice, must be used to protect secrets? (Choose two.)
A developer plans to deploy a new application that will use an API to implement automated data collection from Webex with these requirements:
The application was created by using the request library.
Requires HTTP basic authentication.
Provides data in JSON or XML formats.
Which Cisco DevNet resource helps the developer with how to use the API?
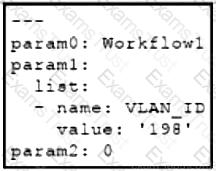
Refer to the exhibit. The YAML shown contains an object "param0" that is equal to "Workflow1", a second object "param1" that contains an object called "list" which contains an array of two objects, "name" (equal to "VLAN_ID") and "value" (equal to a text value "198"), and finally a third object "param2" that is equal to "0". What is the equivalent message in JSON data format?
Refer to the exhibit. Drag and drop the code snippets from the bottom onto the blanks in the Python script to retrieve a list of network devices from Cisco DNA Center. Not all options are used.
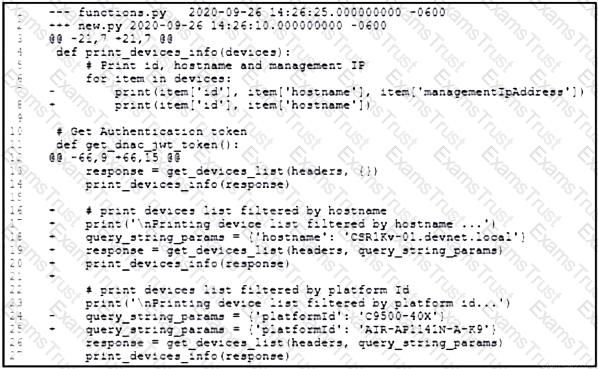
Refer to the exhibit. An engineer is comparing two files by using the unified diff format. Which cade snippet belongs to the new.py file?
A resource named /item is protected by oAuth2 authentication. An endpoint named /login must request authentication. Which method must be used to access the resource by using the REST API?
A developer has addressed a bug that was found in the production code of an application. A separate file named ‘bug427896191v_fix” has been created with the changes to the code. Which Git command must be used to incorporate the bug fix into the production code?
A group of software developers wants to improve its collaboration with the operations team. The group wants to deliver release-ready code that merges code changes back to the main branch and runs the automated testing as often as possible. Which DevOps concept does this scenario represent?
What is a feature of XML compared to other data formats?
Refer to the exhibit.
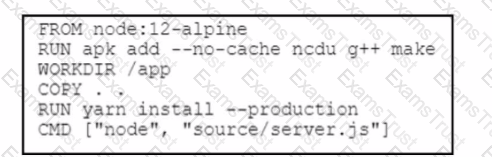
The server.js Node.js script runs after the Dockerfile creates its container. What is the working directory of the application inside the container?
Which HTTP error code series relates to redirection?
Drag and drop the code from the bottom onto the box where the code is missing to obtain a list of network devices by using the Cisco Meraki API. Not all options are used.
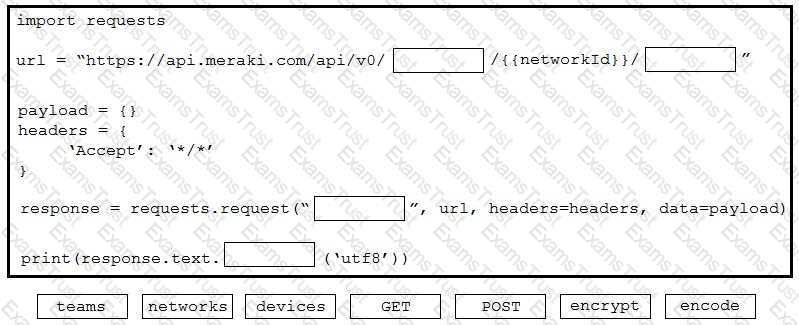
Which protocol runs over TCP port 830?
When a Cisco IOS XE networking device is configured by using RESTCONF, what is the default data encoding method?
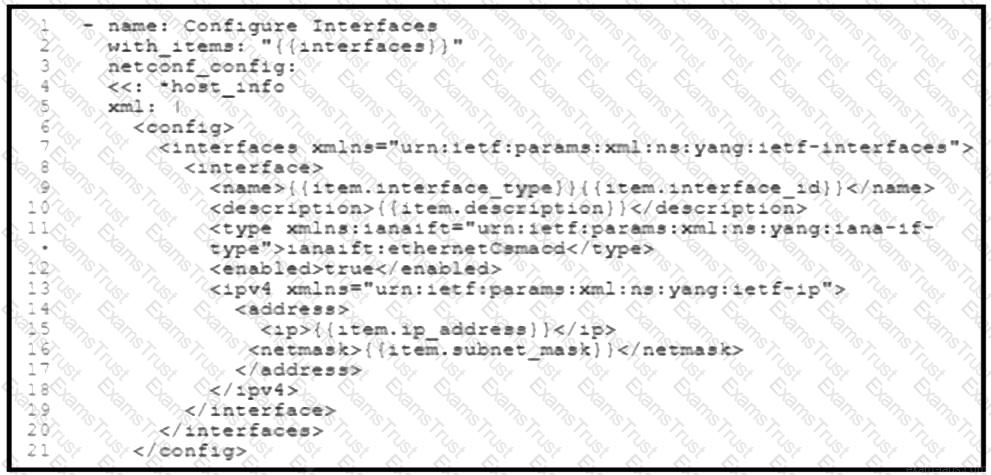
Refer to the exhibit. A network engineer must configure new interfaces on a set of devices and is planning to use an Ansible playbook for the task. All devices support SSH and NETCONF protocol, and the interface variables are unique per device. In which directory are the YAML files including variables hosted to automate the task with the netconf_config module?
An engineer deploys a Cisco CSR 1000 V instance to a virtual machine. The engineer must output the device configuration in JSON format. Which protocol is used for this task?
A network engineer makes several API calls lo Cisco Prime to retrieve a list of all devices. Each time a response is received, only a subset of the devices is returned. The engineer :ices that HTTP code 429 is returned instead of 200 for some API calls. Why did the response exclude some of the devices?
Which technology is responsible for resolving a host name to an IP address?
A developer pushes an application to production. The application receives a webhook over HTTPS without a secret. The webhook information contains credentials to service in cleartext. When the information is received, it is stored in the database with an SHA-256 hash. Credentials to the database are accessed at runtime through the use of a vault service. While troubleshooting, the developer sets the logging to debug to view the message from the webhook. What is the security issue in this scenario?
Which Cisco compute management platform controls server, network, storage, and virtual resources with policy-driven management for up to 10000 physical Cisco servers?
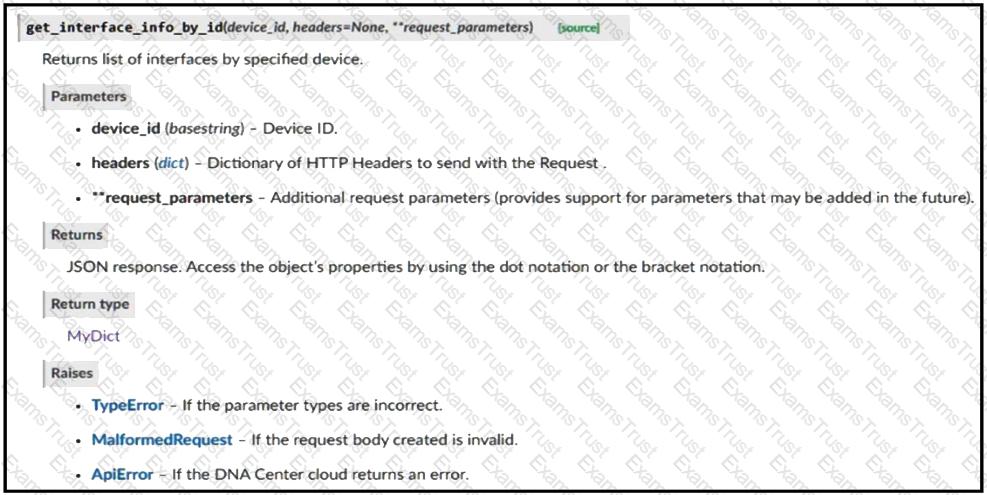
Refer to the exhibit. Drag and drop the code from the bottom onto the box where the code is missing to return the number of interfaces on a network device by using the Cisco DNA Center SDK. Not all options are used.
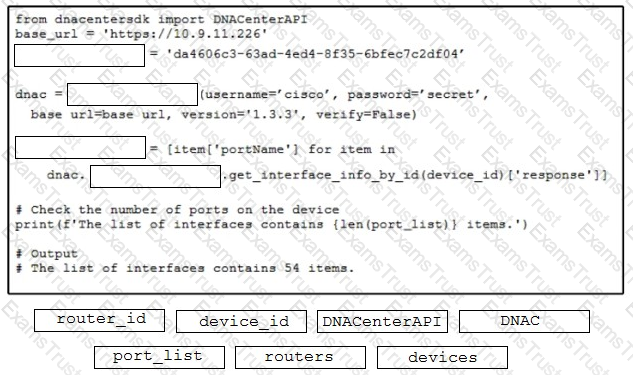
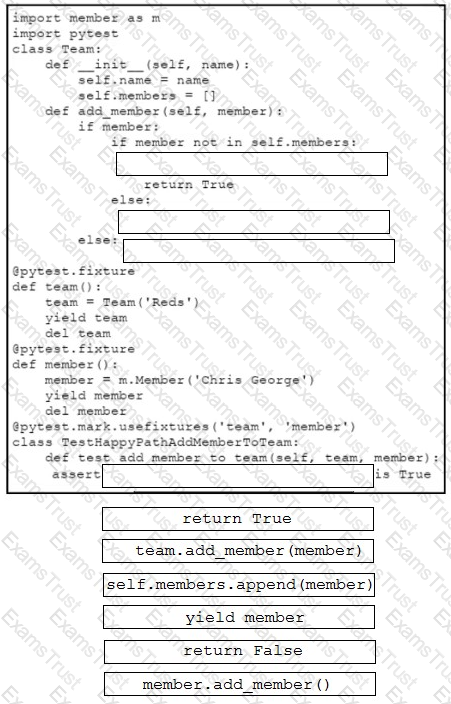
Drag and drop the code snippets from the bottom onto the blanks in the code to complete the happy path scenario. Not all options are used.
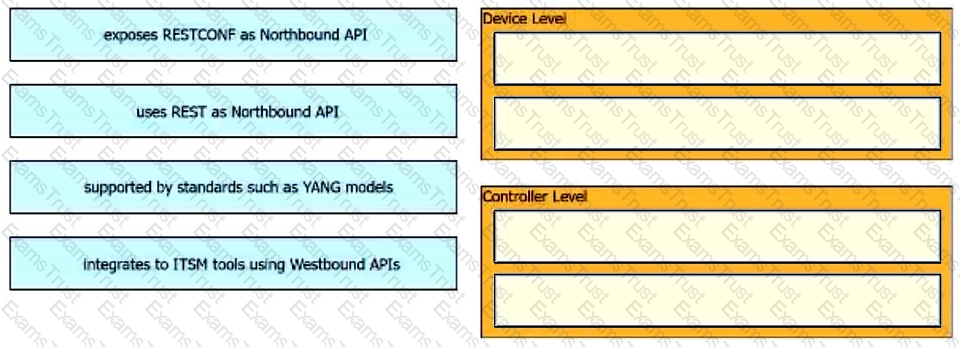
Users cannot access a webserver and after the traffic is captured, the capture tool snows an ICMP packet that reports "time exceeded in-transit". What is the cause of this webserver access issue?
What is a capability of Ansible playbooks?
Drag and drop characteristics from the left onto the infrastructure management methodologies on the right.
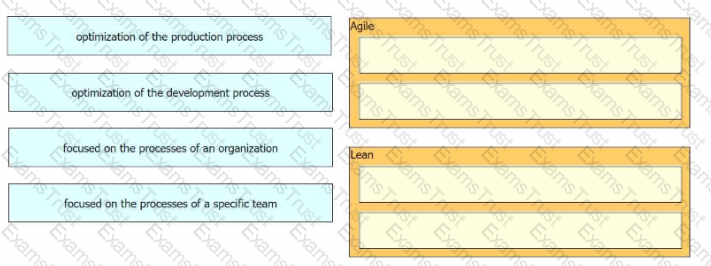
Drag and drop the characteristics from the left onto the software development methodologies on the right.
What is a feature of a MAC address?
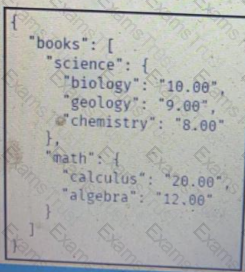
Refer to the exhibit.

What are two results of running the RESTCONF query? (Choose two.)
An engineer must configure Cisco Nexus devices and wants to automate this workflow. The engineer will use an Ansible playbook to configure devices through Cisco NX REST API. Before the code is run, which resource must be used to verify that the REST API requests work as expected?
What is a benefit of version control?
Refer to the exhibit.
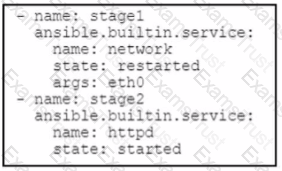
The IT team deployed a new Linux virtual machine for a software engineer to use. but the engineer is not comfortable configuring services using Bash. Which workflow is automated by the Ansible playbook?
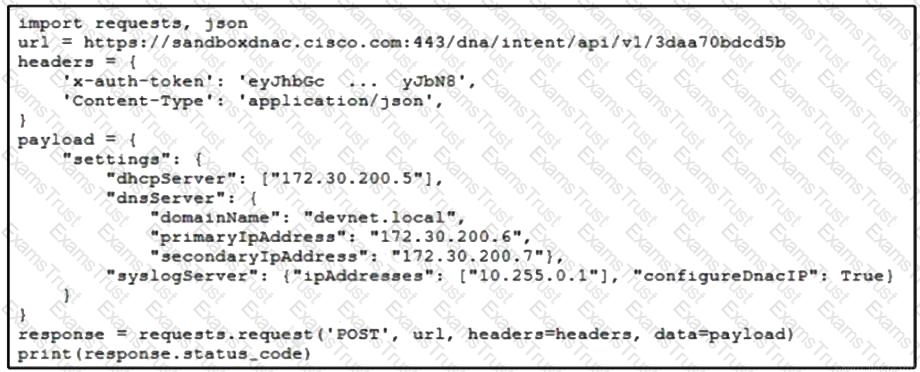
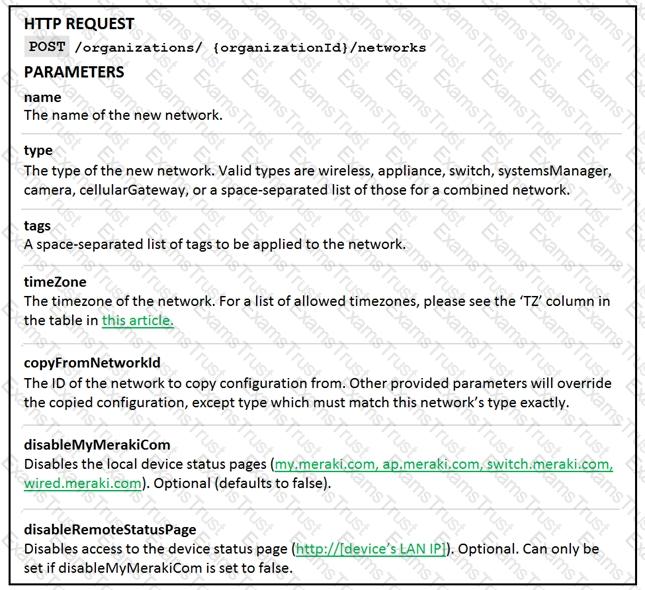
Refer to the exhibit. A developer writes a script to create a new network by using the Cisco DNA Center API. After running the script for the first time, the developer observes that HTTP code 404 is printed to the console. Which action resolves the problem?