A security analyst must create a new report within Cisco FMC to show an overview of the daily attacks, vulnerabilities, and connections. The analyst wants to reuse specific dashboards from other reports to create this consolidated one. Which action accomplishes this task?
Which license type is required on Cisco ISE to integrate with Cisco FMC pxGrid?
What is the advantage of having Cisco Firepower devices send events to Cisco Threat response via the security services exchange portal directly as opposed to using syslog?
An engineer is implementing Cisco FTD in the network and is determining which Firepower mode to use. The organization needs to have multiple virtual Firepower devices working separately inside of the FTD appliance to provide traffic segmentation Which deployment mode should be configured in the Cisco Firepower Management Console to support these requirements?
An engineer is working on a LAN switch and has noticed that its network connection to the mime Cisco IPS has gone down Upon troubleshooting it is determined that the switch is working as expected What must have been implemented for this failure to occur?
An administrator is configuring a transparent Cisco FTD device to receive ERSPAN traffic from multiple switches on a passive port but the FTD is not processing the traffic What is the problem?
An organization has a Cisco IPS running in inline mode and is inspecting traffic for malicious activity. When traffic is received by the Cisco IRS, if it is not dropped, how does the traffic get to its destination?
While integrating Cisco Umbrella with Cisco Threat Response, a network security engineer wants to automatically push blocking of domains from the Cisco Threat Response interface to Cisco Umbrella. Which API meets this requirement?
A network administrator reviews me attack risk report and notices several Low-Impact attacks. What does this type of attack indicate?
Which Cisco FMC report gives the analyst information about the ports and protocols that are related to the configured sensitive network for analysis?
An administrator is adding a new URL-based category feed to the Cisco FMC for use within the policies. The intelligence source does not use STIX. but instead uses a .txt file format. Which action ensures that regular updates are provided?
An analyst using the security analyst account permissions is trying to view the Correlations Events Widget but is not able to access it. However, other dashboards are accessible. Why is this occurring?
An organization is configuring a new Cisco Firepower High Availability deployment. Which action must be taken to ensure that failover is as seamless as possible to end users?
An engineer must configure a Cisco FMC dashboard in a child domain. Which action must be taken so that the dashboard is visible to the parent domain?
An engineer installs a Cisco FTD device and wants to inspect traffic within the same subnet passing through a firewall and inspect traffic destined to the internet.
Which configuration will meet this requirement?
An engineer has been tasked with using Cisco FMC to determine if files being sent through the network are malware. Which two configuration tasks must be performed to achieve this file lookup? (Choose two).
A network administrator is configuring a Cisco AMP public cloud instance and wants to capture infections and polymorphic variants of a threat to help detect families of malware. Which detection engine meets this requirement?
A network security engineer must replace a faulty Cisco FTD device in a high availability pair. Which action must be taken while replacing the faulty unit?
On the advanced tab under inline set properties, which allows interfaces to emulate a passive interface?
An organization has a Cisco FTD that uses bridge groups to pass traffic from the inside interfaces to the outside interfaces. They are unable to gather information about neighbouring Cisco devices or use multicast in their environment. What must be done to resolve this issue?
Which two deployment types support high availability? (Choose two.)
An administrator is optimizing the Cisco FTD rules to improve network performance, and wants to bypass inspection for certain traffic types to reduce the load on the Cisco FTD. Which policy must be configured to accomplish this goal?
Which protocol establishes network redundancy in a switched Firepower device deployment?
Which two conditions must be met to enable high availability between two Cisco FTD devices? (Choose two.)
Which two dynamic routing protocols are supported in Firepower Threat Defense without using FlexConfig? (Choose two.)
What is the difference between inline and inline tap on Cisco Firepower?
Which firewall design allows a firewall to forward traffic at layer 2 and layer 3 for the same subnet?
Which Cisco Firepower Threat Defense, which two interface settings are required when configuring a routed interface? (Choose two.)
An engineer is tasked with deploying an internal perimeter firewall that will support multiple DMZs Each DMZ has a unique private IP subnet range. How is this requirement satisfied?
What is a result of enabling Cisco FTD clustering?
What are two application layer preprocessors? (Choose two.)
An engineer is building a new access control policy using Cisco FMC. The policy must inspect a unique IPS policy as well as log rule matching. Which action must be taken to meet these requirements?
An engineer is configuring a Cisco IPS to protect the network and wants to test a policy before deploying it. A copy of each incoming packet needs to be monitored while traffic flow remains constant. Which IPS mode should be implemented to meet these requirements?
What are the minimum requirements to deploy a managed device inline?
What is a valid Cisco AMP file disposition?
Which action should you take when Cisco Threat Response notifies you that AMP has identified a file as malware?
Which Cisco Advanced Malware Protection for Endpoints policy is used only for monitoring endpoint actively?
Which two features of Cisco AMP for Endpoints allow for an uploaded file to be blocked? (Choose two.)
What is the maximum SHA level of filtering that Threat Intelligence Director supports?
In a Cisco AMP for Networks deployment, which disposition is returned if the cloud cannot be reached?
Which two remediation options are available when Cisco FMC is integrated with Cisco ISE? (Choose two.)
Which connector is used to integrate Cisco ISE with Cisco FMC for Rapid Threat Containment?
An organization does not want to use the default Cisco Firepower block page when blocking HTTP traffic. The organization wants to include information about its policies and procedures to help educate the users whenever a block occurs. Which two steps must be taken to meet these requirements? (Choose two.)
A company has many Cisco FTD devices managed by a Cisco FMC. The security model requires that access control rule logs be collected for analysis. The security engineer is concerned that the Cisco FMC will not be able to process the volume of logging that will be generated. Which configuration addresses this concern?
In which two ways do access control policies operate on a Cisco Firepower system? (Choose two.)
Which two OSPF routing features are configured in Cisco FMC and propagated to Cisco FTD? (Choose two.)
A company is in the process of deploying intrusion prevention with Cisco FTDs managed by a Cisco FMC. An engineer must configure policies to detect potential intrusions but not block the suspicious traffic. Which action accomplishes this task?
Which two routing options are valid with Cisco Firepower Threat Defense? (Choose two.)
An engineer is using the configure manager add
What is the disadvantage of setting up a site-to-site VPN in a clustered-units environment?
An organization is using a Cisco FTD and Cisco ISE to perform identity-based access controls. A network administrator is analyzing the Cisco FTD events and notices that unknown user traffic is being allowed through the firewall. How should this be addressed to block the traffic while allowing legitimate user traffic?
Which command-line mode is supported from the Cisco Firepower Management Center CLI?
Which command is typed at the CLI on the primary Cisco FTD unit to temporarily stop running high- availability?
Which command should be used on the Cisco FTD CLI to capture all the packets that hit an interface?
Within Cisco Firepower Management Center, where does a user add or modify widgets?
Which CLI command is used to generate firewall debug messages on a Cisco Firepower?
Which command must be run to generate troubleshooting files on an FTD?
Which Cisco Firepower feature is used to reduce the number of events received in a period of time?
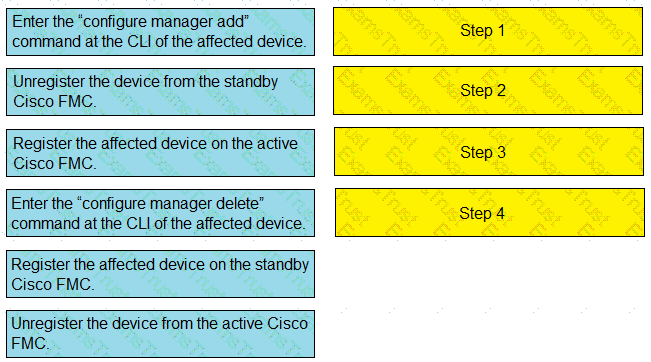
Drag and drop the steps to restore an automatic device registration failure on the standby Cisco FMC from the left into the correct order on the right. Not all options are used.
Which action should be taken after editing an object that is used inside an access control policy?
Which CLI command is used to control special handling of ClientHello messages?
Which two statements about deleting and re-adding a device to Cisco FMC are true? (Choose two.)
Which group within Cisco does the Threat Response team use for threat analysis and research?
What is the benefit of selecting the trace option for packet capture?
Which report template field format is available in Cisco FMC?
After deploying a network-monitoring tool to manage and monitor networking devices in your organization, you realize that you need to manually upload an MIB for the Cisco FMC. In which folder should you upload the MIB file?
What is the maximum bit size that Cisco FMC supports for HTTPS certificates?
Which limitation applies to Cisco Firepower Management Center dashboards in a multidomain environment?