A security team is running vulnerability scans against a CI/CD pipeline. The reports show that RDBMS secrets were found hardcoded in Ansible scripts. The RDBMS resides in the internal network but is accessible from a jump server that resides in a public network.
If an attacker gains access to the scripts, what is the risk exposure?
Refer to the exhibit.
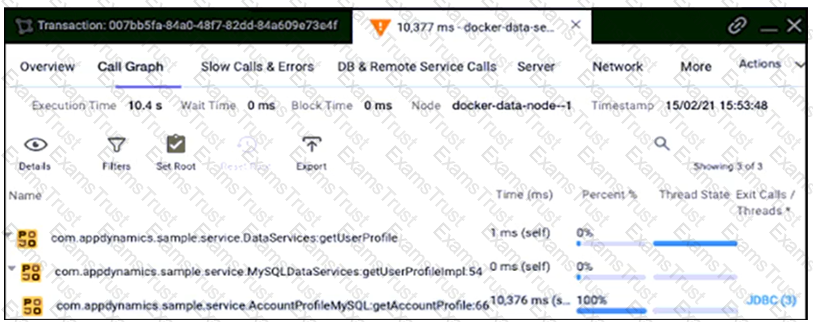
A distributed application contains data services that connect to databases via JDBC and to other remote services via HTTP. The overall response time is too long, and AppDynamics is used to investigate the root cause. From the application flow map, a specific data service running on Docker has been identified whose response time is over 10 seconds.
Which action resolves the issue?
Which two characteristics of a build tool that is used in an automated build pipeline? (Choose two.)
What is a benefit of monitoring the CI/CD pipeline?
An organization is developing an application using Git. Each team member is assigned to work on specific parts of the application. At the end of each task, individual code parts are merged in the main build.
Which two requirements should be implemented to increase the likelihood of continuous integration? (Choose two.)
Drag and drop the code from the bottom onto the box where the code is missing to create a Terraform configuration that builds the network environment for a multitier software application. More EPG, Contract, and Filter definitions have been removed from the code.

A developer is nearing the end of a software development cycle and is ready to deploy the software. The customer wants to continue using a secure software development lifecycle methodology and must plan for postproduction components. Which two areas should be the developer address? (Choose two.)
AppDynamics is being used to monitor your distributed Python application. Each individual container of the application is instrumented with an AppD agent. Which two configuration variables uniquely determine the module being monitored? (Choose two.)
Refer to the exhibit.
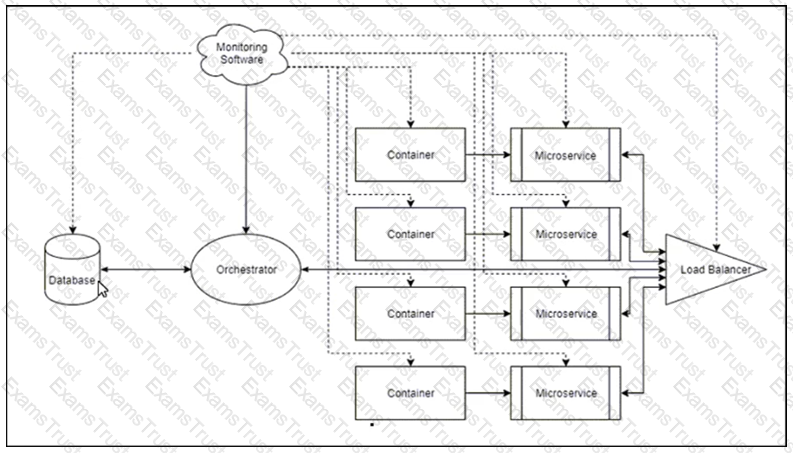
How does the architecture respond to a usage spike?
An application is being developed to be used by the HR department of a company on a global scale. The application will be used as a central repository for employee contracts. For user access, a RADIUS server will be used with authorized user groups.
Which action must be used to prevent developers from accidentally committing secrets in the code?
Microservices architecture pattern has been applied and the system has been architected as a set of services. Each service is deployed as a set of instances for throughput and availability. In which two ways are these services packaged and deployed? (Choose two.)
What is a capability of node-level logging in Kubernetes?
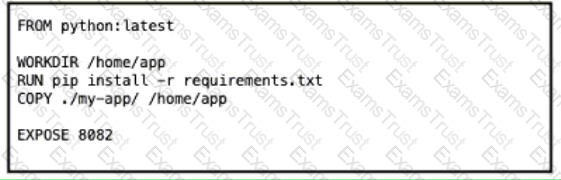
Which Dockerfile yields the most predictable builds?
A)
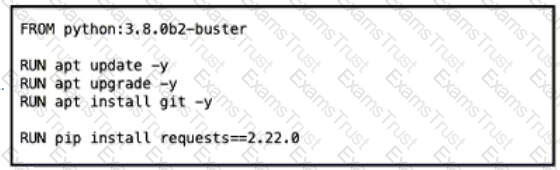
B)

C)
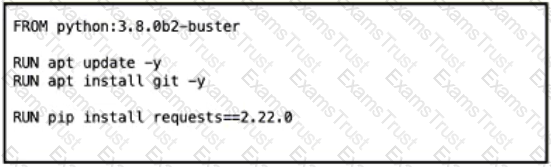
D)

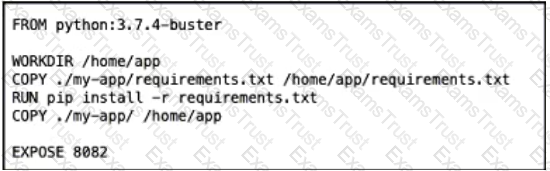
Which Dockerfile produces an efficient image rebuild when the exposed port Python dependency, or MyApp source code is modified?
A)

B)

C)
D)
Which method is a safe way to provide a username/password combination to an application running as a service in a Docker container?
When static routes are added to a router in a network using a CI/CD pipeline, an Ansible playbook is used to make these changes. Which steps must be added to the pipeline to validate that the changes have the intended effect on the traffic flow?
Refer to the exhibit.
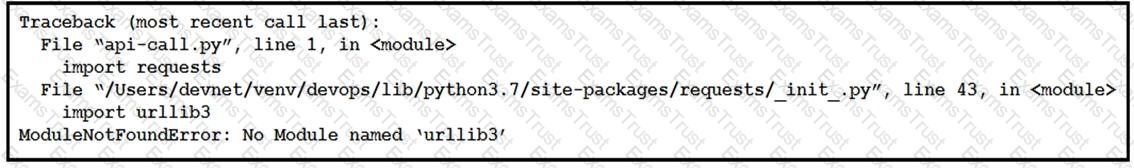
What is the reason for this error message?
What is included in ansible playbook instructions?
Fill in the blank to complete the statement.
A user wants a Kubernetes deployment to run three separate pods of a web application at one time. In the deployment YAML, the user must configure the___________field in the________subsection.
A new version of an application is being released by creating a separate instance of the application that is running the new code. Only a small portion of the user base will be directed to the new instance until that version has been proven stable. Which deployment strategy is this example of?
What are two reasons a Docker golden image should be updated? (Choose two.)
Which approach must be used to integrate DevOps practices into the team structure in an existing organization?
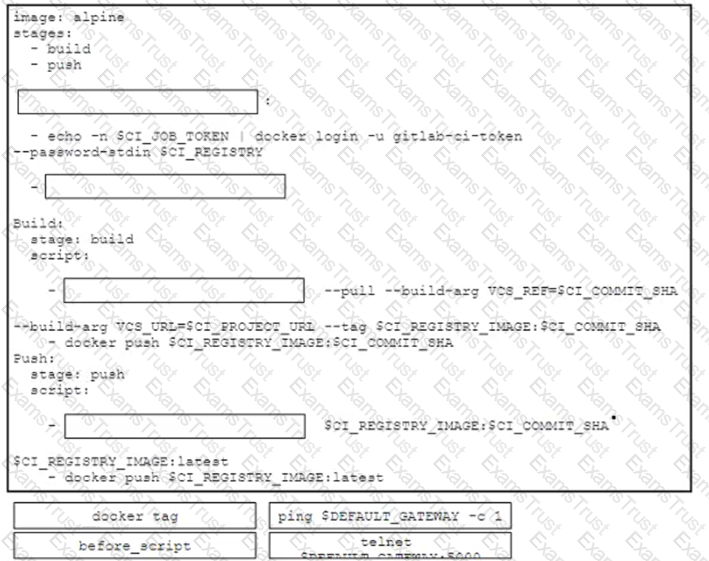
A DevOps engineer is designing a precheck validation of the network state in a CI/CD pipeline and must implement this workflow:
• Take a source Docker image named alpine
• Define two stages named build and push
• Check network connectivity before the stages run
• Fetch the latest Docker image
• Create a new Docker image and push it to the registry
• Tag the new Docker image as the latest version
Drag and drop the code snippets from the bottom onto the boxes in the GitLab CI configuration to achieve the requirements for the design. Not all options are used.

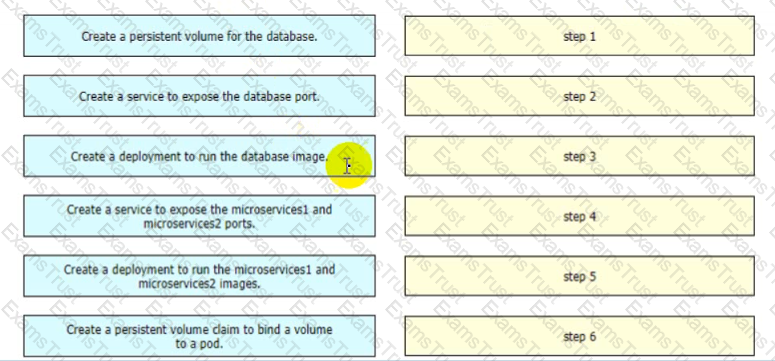
Refer to the exhibit A DevOps engineer must deploy two microservices The deployment must be installed in a new Kubernetes cluster. The microservices currently run in Docker and are managed by using the provided docker-compose yml file Drag and drop the steps from the left into order on the right to successfully deploy the microservices
A company has a CI/CD pipeline implemented to automate application deployment. An urgent change is required in the production environment. A developer produces and tests the required change in the company's environment, but the pipeline fails when pushed.
Which action conforms to the rules of a CI/CD pipeline and enables the pipeline to pass?
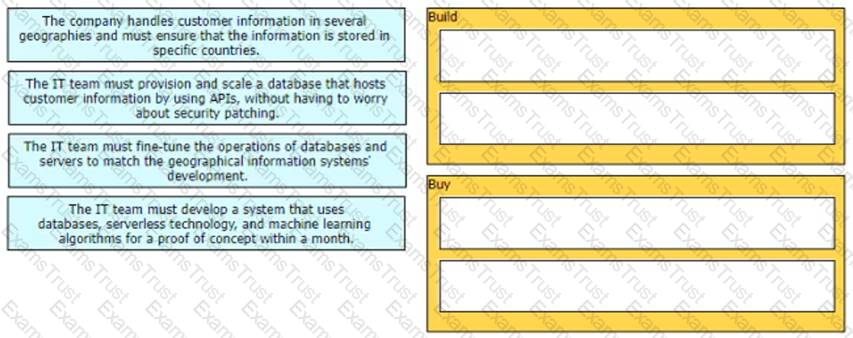
Drag and drop the scenarios from the left onto the cloud strategy categories on the right.
Which two practices help make the security of an application a more integral part of the software development lifecycle? (Choose two.)
Which description of a canary deployment is true?
A DevOps engineer has built a new container and must open port 8080 for intercontainer communication. Which command must be added in a Dockerfile to accomplish this goal?
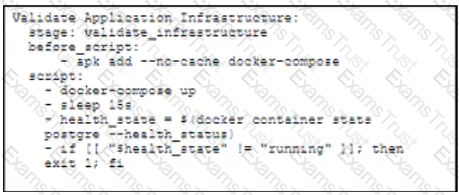
Refer to the exhibit.
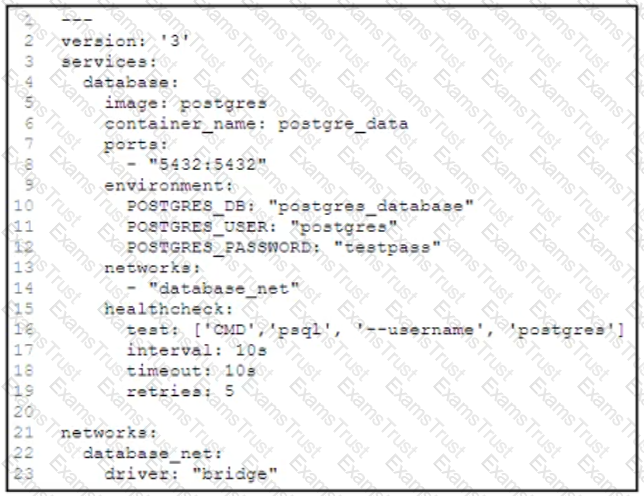
A docker-compose.yml file implements a postgres database container.
Which .gitlab-ci.yml code block checks the health status of the container and stops the pipeline if the container is unhealthy?
A)

B)
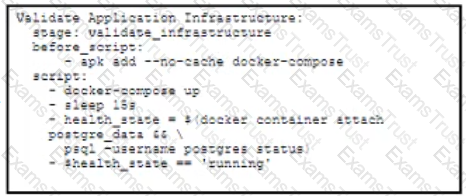
C)

D)
What is the purpose of using a build tool in software development?
A CI/CD pipeline that builds infrastructure components using Terraform must be designed. A step in the pipeline is needed that checks for errors in any of the .tf files in the working directory. It also checks the existing state of the defined infrastructure.
Which command does the pipeline run to accomplish this goal?
An application for storing and categorizing has been developed. The application uses dual-factor authentication for user access. After authentication, users can upload sensitive data. The application has been hacked through system exploits and most of the saved data has been lost.
Which action prevents new security threats in the environment?
What are two testing scenarios of the chaos engineering principle? (Choose two.)
Refer to the exhibit.

A Python script implements a logger server. The log receives a message from Base that contains this text: TextMessage. How is the log formatted?
A new banking application is being developed as the main currency exchange resource for all the customers on a global scale. The application must comply with the security based on the deployed region. Therefore, the CI/CD pipeline must be created with the highest security possible.
Which approach accomplishes this goal?
A DevOps engineer has built a container to host a web-server and it must run as an executable. Which command must be configured in a Dockerfile to accomplish this goal?
The E-commerce application is being monitored using AppDynamics. AppDynamics has noticed that the application response has degraded and has identified some thread contention that might be the cause of the delays.
Where in the interface does AppDynamics bring this to your attention?
An IT team plans to deploy a new service built on top of an existing service. The capacity needed for the new service is difficult to estimate because the demand for the new service is undetermined. The team has these deployment requirements:
• A subset of the users of the original service must be migrated to the new service based on their profile
• The new service must be rolled back easily if capacity exceeds estimates
Which deployment strategy must be used?