Which compliance status is shown when a configured posture policy requirement is not met?
What Cisco command shows you the status of an 802.1X connection on interface gi0/1?
What are two reasons for implementing a multifactor authentication solution such as Duo Security provide to an
organization? (Choose two)
Which command enables 802.1X globally on a Cisco switch?
When Cisco and other industry organizations publish and inform users of known security findings and
vulnerabilities, which name is used?
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two)
Which PKI enrollment method allows the user to separate authentication and enrollment actions and also
provides an option to specify HTTP/TFTP commands to perform file retrieval from the server?
What is the purpose of the Decrypt for Application Detection feature within the WSA Decryption options?
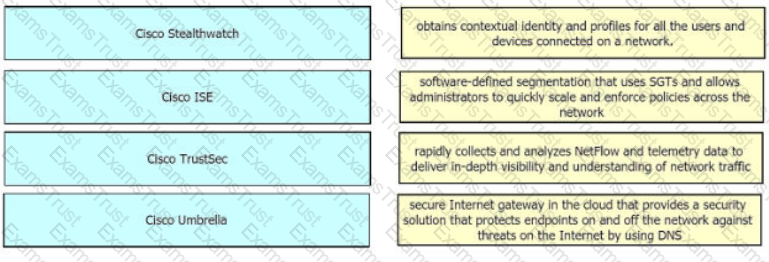
Which solution protects hybrid cloud deployment workloads with application visibility and segmentation?
Which two behavioral patterns characterize a ping of death attack? (Choose two)
What is the difference between deceptive phishing and spear phishing?
Which two conditions are prerequisites for stateful failover for IPsec? (Choose two)
A network administrator configures Dynamic ARP Inspection on a switch. After Dynamic ARP Inspection is applied, all users on that switch are unable to communicate with any destination. The network administrator checks the interface status of all interfaces, and there is no err-disabled interface. What is causing this problem?
Which two features of Cisco Email Security can protect your organization against email threats? (Choose two)
Which capability is exclusive to a Cisco AMP public cloud instance as compared to a private cloud instance?
How many interfaces per bridge group does an ASA bridge group deployment support?
Which two features are used to configure Cisco ESA with a multilayer approach to fight viruses and malware?
(Choose two)
An engineer configured a new network identity in Cisco Umbrella but must verify that traffic is being routed
through the Cisco Umbrella network. Which action tests the routing?
How does Cisco Stealthwatch Cloud provide security for cloud environments?
What are two list types within AMP for Endpoints Outbreak Control? (Choose two)
Where are individual sites specified to be blacklisted in Cisco Umbrella?
An administrator wants to ensure that all endpoints are compliant before users are allowed access on the
corporate network. The endpoints must have the corporate antivirus application installed and be running the
latest build of Windows 10.
What must the administrator implement to ensure that all devices are compliant before they are allowed on the
network?
Which exfiltration method does an attacker use to hide and encode data inside DNS requests and queries?
Which API is used for Content Security?
Which cloud service model offers an environment for cloud consumers to develop and deploy applications
without needing to manage or maintain the underlying cloud infrastructure?
An engineer is trying to securely connect to a router and wants to prevent insecure algorithms from being used.
However, the connection is failing. Which action should be taken to accomplish this goal?
An engineer needs a solution for TACACS+ authentication and authorization for device administration.
The engineer also wants to enhance wired and wireless network security by requiring users and endpoints to
use 802.1X, MAB, or WebAuth. Which product meets all of these requirements?
What is the primary benefit of deploying an ESA in hybrid mode?
An engineer wants to automatically assign endpoints that have a specific OUI into a new endpoint group. Which
probe must be enabled for this type of profiling to work?
Refer to the exhibit.
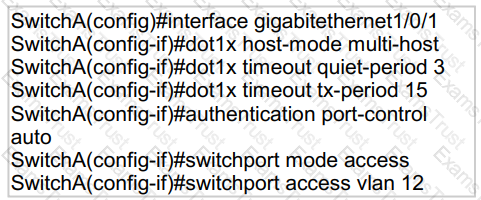
An engineer configured wired 802.1x on the network and is unable to get a laptop to authenticate. Which port configuration is missing?
An organization is trying to improve their Defense in Depth by blocking malicious destinations prior to a
connection being established. The solution must be able to block certain applications from being used within the network. Which product should be used to accomplish this goal?
Which technology is used to improve web traffic performance by proxy caching?
What is a characteristic of Firepower NGIPS inline deployment mode?
Which feature of Cisco ASA allows VPN users to be postured against Cisco ISE without requiring an inline
posture node?
Which ID store requires that a shadow user be created on Cisco ISE for the admin login to work?
An engineer must force an endpoint to re-authenticate an already authenticated session without disrupting the
endpoint to apply a new or updated policy from ISE. Which CoA type achieves this goal?
Which feature requires a network discovery policy on the Cisco Firepower Next Generation Intrusion Prevention
System?
Which action controls the amount of URI text that is stored in Cisco WSA logs files?
Which CLI command is used to register a Cisco FirePower sensor to Firepower Management Center?
Which telemetry data captures variations seen within the flow, such as the packets TTL, IP/TCP flags, and payload length?
Which RADIUS attribute can you use to filter MAB requests in an 802.1 x deployment?
Which algorithm provides encryption and authentication for data plane communication?
The main function of northbound APIs in the SDN architecture is to enable communication between which two areas of a network?
Which two are valid suppression types on a Cisco Next Generation Intrusion Prevention System? (Choose two)
Which two features of Cisco DNA Center are used in a Software Defined Network solution? (Choose two)
What is a characteristic of Cisco ASA Netflow v9 Secure Event Logging?
An organization has two machines hosting web applications. Machine 1 is vulnerable to SQL injection while machine 2 is vulnerable to buffer overflows. What action would allow the attacker to gain access to machine 1 but not machine 2?
Which Cisco Advanced Malware protection for Endpoints deployment architecture is designed to keep data
within a network perimeter?
Which policy represents a shared set of features or parameters that define the aspects of a managed device that are likely to be similar to other managed devices in a deployment?
Elliptic curve cryptography is a stronger more efficient cryptography method meant to replace which current
encryption technology?
How is ICMP used an exfiltration technique?
What is a characteristic of a bridge group in ASA Firewall transparent mode?
How does Cisco Umbrella archive logs to an enterprise owned storage?
Refer to the exhibit.
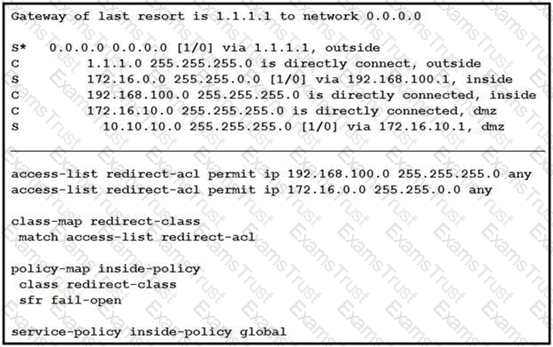
What is a result of the configuration?
Which Cisco command enables authentication, authorization, and accounting globally so that CoA is supported on the device?
Which network monitoring solution uses streams and pushes operational data to provide a near real-time view
of activity?
What is the function of Cisco Cloudlock for data security?
Which flaw does an attacker leverage when exploiting SQL injection vulnerabilities?
Under which two circumstances is a CoA issued? (Choose two)
Which two descriptions of AES encryption are true? (Choose two)
Which two tasks allow NetFlow on a Cisco ASA 5500 Series firewall? (Choose two)
An engineer used a posture check on a Microsoft Windows endpoint and discovered that the MS17-010 patch
was not installed, which left the endpoint vulnerable to WannaCry ransomware. Which two solutions mitigate
the risk of this ransom ware infection? (Choose two)
Which two prevention techniques are used to mitigate SQL injection attacks? (Choose two)
What is a benefit of using Cisco FMC over Cisco ASDM?
What must be configured in Cisco ISE to enforce reauthentication of an endpoint session when an endpoint is
deleted from an identity group?
What is a feature of Cisco NetFlow Secure Event Logging for Cisco ASAs?
An engineer notices traffic interruption on the network. Upon further investigation, it is learned that broadcast
packets have been flooding the network. What must be configured, based on a predefined threshold, to
address this issue?
A network engineer has been tasked with adding a new medical device to the network. Cisco ISE is being used as the NAC server, and the new device does not have a supplicant available. What must be done in order to securely connect this device to the network?
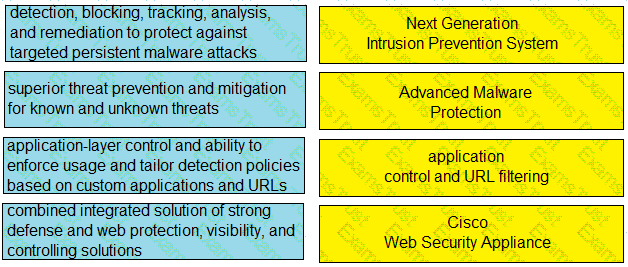
Drag and drop the capabilities from the left onto the correct technologies on the right.
After a recent breach, an organization determined that phishing was used to gain initial access to the network before regaining persistence. The information gained from the phishing attack was a result of users visiting known malicious websites. What must be done in order to prevent this from happening in the future?
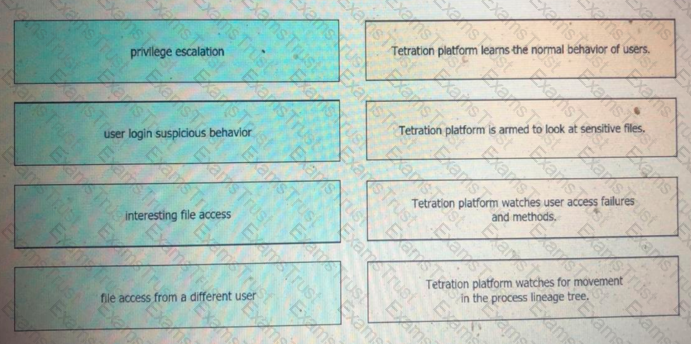
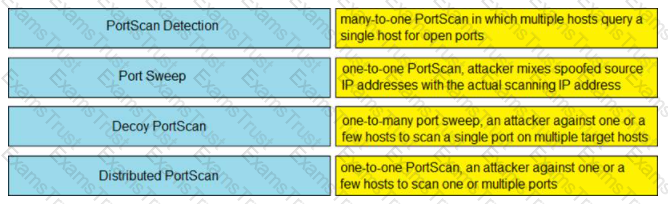
Drag and drop the suspicious patterns for the Cisco Tetration platform from the left onto the correct definitions on the right.
What is the function of SDN southbound API protocols?
Which attack type attempts to shut down a machine or network so that users are not able to access it?
What is the role of an endpoint in protecting a user from a phishing attack?
What is a benefit of performing device compliance?
What is a benefit of conducting device compliance checks?
Which two cryptographic algorithms are used with IPsec? (Choose two)
An organization wants to secure users, data, and applications in the cloud. The solution must be API-based and
operate as a cloud-native CASB. Which solution must be used for this implementation?
What are two Trojan malware attacks? (Choose two)
A user has a device in the network that is receiving too many connection requests from multiple machines.
Which type of attack is the device undergoing?
Refer to the exhibit.
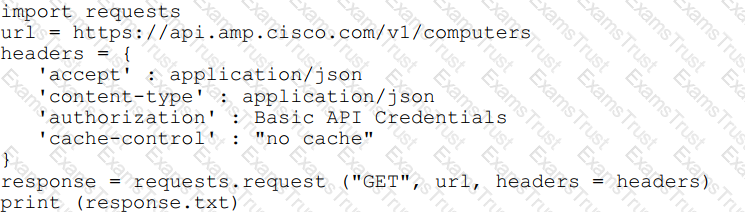
What will happen when this Python script is run?
Which component of Cisco umbrella architecture increases reliability of the service?
What is the benefit of installing Cisco AMP for Endpoints on a network?
Which two aspects of the cloud PaaS model are managed by the customer but not the provider? (Choose two)
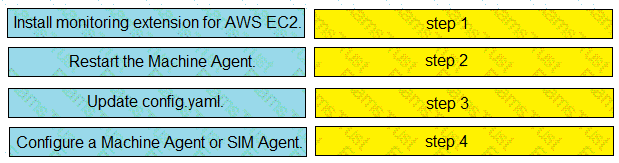
Drag and drop the steps from the left into the correct order on the right to enable AppDynamics to monitor an EC2 instance in Amazon Web Services.
Which type of protection encrypts RSA keys when they are exported and imported?
Which factor must be considered when choosing the on-premise solution over the cloud-based one?
Drag and drop the Firepower Next Generation Intrusion Prevention System detectors from the left onto the correct definitions on the right.
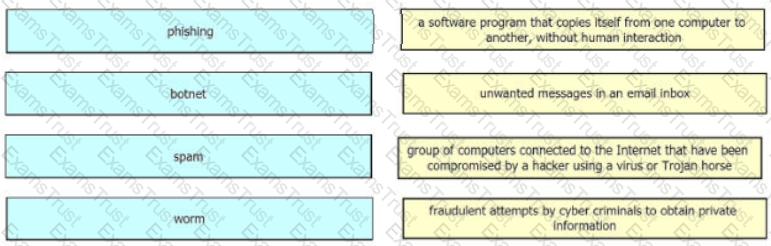
Drag and drop the common security threats from the left onto the definitions on the right.
What is a difference between DMVPN and sVTI?
What is the Cisco API-based broker that helps reduce compromises, application risks, and data breaches in an environment that is not on-premise?
What is provided by the Secure Hash Algorithm in a VPN?
Why is it important to implement MFA inside of an organization?
What is a function of 3DES in reference to cryptography?
Which Cisco platform ensures that machines that connect to organizational networks have the recommended
antivirus definitions and patches to help prevent an organizational malware outbreak?
An organization is using Cisco Firepower and Cisco Meraki MX for network security and needs to centrally
manage cloud policies across these platforms. Which software should be used to accomplish this goal?
How does Cisco Advanced Phishing Protection protect users?
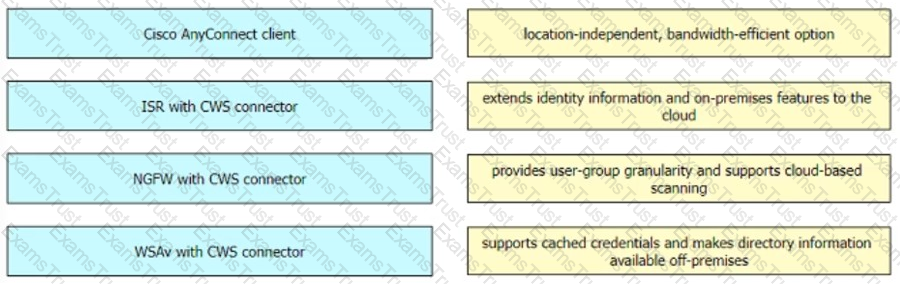
Drag and drop the solutions from the left onto the solution's benefits on the right.
A network administrator is using the Cisco ESA with AMP to upload files to the cloud for analysis. The network
is congested and is affecting communication. How will the Cisco ESA handle any files which need analysis?
An organization is receiving SPAM emails from a known malicious domain. What must be configured in order to
prevent the session during the initial TCP communication?
A network administrator is configuring a switch to use Cisco ISE for 802.1X. An endpoint is failing
authentication and is unable to access the network. Where should the administrator begin troubleshooting to verify the authentication details?
Why is it important to have logical security controls on endpoints even though the users are trained to spot security threats and the network devices already help prevent them?
Which suspicious pattern enables the Cisco Tetration platform to learn the normal behavior of users?
An engineer is configuring 802.1X authentication on Cisco switches in the network and is using CoA as a mechanism. Which port on the firewall must be opened to allow the CoA traffic to traverse the network?
A Cisco Firepower administrator needs to configure a rule to allow a new application that has never been seen
on the network. Which two actions should be selected to allow the traffic to pass without inspection? (Choose
two)
Which product allows Cisco FMC to push security intelligence observable to its sensors from other products?
Using Cisco Firepower’s Security Intelligence policies, upon which two criteria is Firepower block based?
(Choose two)
With which components does a southbound API within a software-defined network architecture communicate?
What are two differences between a Cisco WSA that is running in transparent mode and one running in explicit mode? (Choose two)
What is the role of Cisco Umbrella Roaming when it is installed on an endpoint?
A network administrator is configuring SNMPv3 on a new router. The users have already been created;
however, an additional configuration is needed to facilitate access to the SNMP views. What must the
administrator do to accomplish this?
An organization has two systems in their DMZ that have an unencrypted link between them for communication.
The organization does not have a defined password policy and uses several default accounts on the systems.
The application used on those systems also have not gone through stringent code reviews. Which vulnerability
would help an attacker brute force their way into the systems?
What are two characteristics of Cisco DNA Center APIs? (Choose two)
Which public cloud provider supports the Cisco Next Generation Firewall Virtual?
In an IaaS cloud services model, which security function is the provider responsible for managing?
An administrator is configuring a DHCP server to better secure their environment. They need to be able to ratelimit the traffic and ensure that legitimate requests are not dropped. How would this be accomplished?
Which risk is created when using an Internet browser to access cloud-based service?
When configuring ISAKMP for IKEv1 Phase1 on a Cisco IOS router, an administrator needs to input the
command crypto isakmp key cisco address 0.0.0.0. The administrator is not sure what the IP addressing in this command issued for. What would be the effect of changing the IP address from 0.0.0.0 to 1.2.3.4?
An organization is implementing URL blocking using Cisco Umbrella. The users are able to go to some sites
but other sites are not accessible due to an error. Why is the error occurring?
Refer to the exhibit.
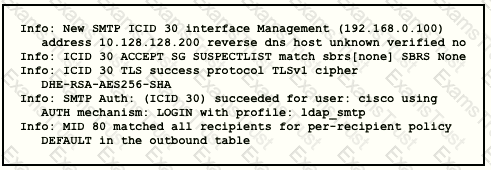
Which type of authentication is in use?
What is a functional difference between a Cisco ASA and a Cisco IOS router with Zone-based policy firewall?
Which method is used to deploy certificates and configure the supplicant on mobile devices to gain access to
network resources?
What are two DDoS attack categories? (Choose two)
An organization has a Cisco Stealthwatch Cloud deployment in their environment. Cloud logging is working as expected, but logs are not being received from the on-premise network, what action will resolve this issue?
Refer to the exhibit.
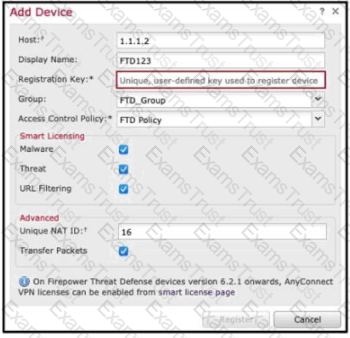
An administrator is adding a new Cisco FTD device to their network and wants to manage it with Cisco FMC.
The Cisco FTD is not behind a NAT device. Which command is needed to enable this on the Cisco FTD?
An engineer has been tasked with implementing a solution that can be leveraged for securing the cloud users,
data, and applications. There is a requirement to use the Cisco cloud native CASB and cloud cybersecurity
platform. What should be used to meet these requirements?
An engineer must configure Cisco AMP for Endpoints so that it contains a list of files that should not be executed by users. These files must not be quarantined. Which action meets this configuration requirement?
Which endpoint solution protects a user from a phishing attack?
Which Cisco platform onboards the endpoint and can issue a CA signed certificate while also automatically configuring endpoint network settings to use the signed endpoint certificate, allowing the endpoint to gain network access?
What are two functions of TAXII in threat intelligence sharing? (Choose two.)
What is an advantage of the Cisco Umbrella roaming client?
Which security product enables administrators to deploy Kubernetes clusters in air-gapped sites without needing Internet access?
What is the difference between a vulnerability and an exploit?
An engineer is configuring Dropbox integration with Cisco Cloudlock. Which action must be taken before granting API access in the Dropbox admin console?
Refer to the exhibit.
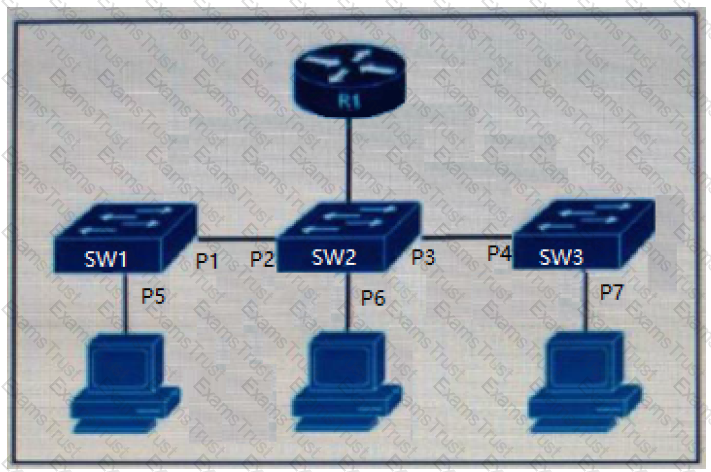
The DHCP snooping database resides on router R1, and dynamic ARP inspection is configured only on switch SW2. Which ports must be configured as untrusted so that dynamic ARP inspection operates normally?
Refer to the exhibit.
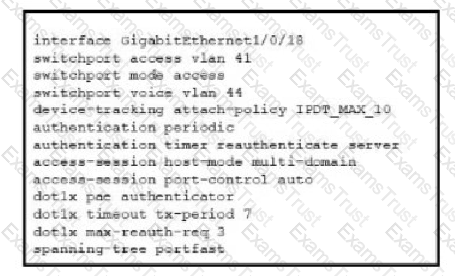
Refer to the exhibit. A Cisco ISE administrator adds a new switch to an 802.1X deployment and has difficulty with some endpoints gaining access.
Most PCs and IP phones can connect and authenticate using their machine certificate credentials. However printer and video cameras cannot base d on the interface configuration provided, what must be to get these devices on to the network using Cisco ISE for authentication and authorization while maintaining security controls?
A network engineer is tasked with configuring a Cisco ISE server to implement external authentication against Active Directory. What must be considered about the authentication requirements? (Choose two.)
How does a cloud access security broker function?
What is the purpose of joining Cisco WSAs to an appliance group?
Which Cisco cloud security software centrally manages policies on multiple platforms such as Cisco ASA, Cisco Firepower, Cisco Meraki, and AWS?
Which Cisco AMP feature allows an engineer to look back to trace past activities, such as file and process
activity on an endpoint?
An administrator configures new authorization policies within Cisco ISE and has difficulty profiling the devices. Attributes for the new Cisco IP phones that are profiled based on the RADIUS authentication are seen however the attributes for CDP or DHCP are not. What should the administrator do to address this issue?
Which two criteria must a certificate meet before the WSA uses it to decrypt application traffic? (Choose two.)
Which Cisco network security device supports contextual awareness?
What is a benefit of using Cisco Tetration?
An organization is implementing AAA for their users. They need to ensure that authorization is verified for every command that is being entered by the network administrator. Which protocol must be configured in order to provide this capability?
An engineer needs to detect and quarantine a file named abc424400664 zip based on the MD5 signature of the file using the Outbreak Control list feature within Cisco Advanced Malware Protection (AMP) for Endpoints The configured detection method must work on files of unknown disposition Which Outbreak Control list must be configured to provide this?
What must be configured on Cisco Secure Endpoint to create a custom detection tile list to detect and quarantine future files?
Which CLI command is used to enable URL filtering support for shortened URLs on the Cisco ESA?
An engineer adds a custom detection policy to a Cisco AMP deployment and encounters issues with the
configuration. The simple detection mechanism is configured, but the dashboard indicates that the hash is not 64 characters and is non-zero. What is the issue?
Which solution should be leveraged for secure access of a CI/CD pipeline?
What are two things to consider when using PAC files with the Cisco WSA? (Choose two.)
What must be enabled to secure SaaS-based applications?
An administrator needs to configure the Cisco ASA via ASDM such that the network management system
can actively monitor the host using SNMPv3. Which two tasks must be performed for this configuration?
(Choose two.)
What is a difference between GRE over IPsec and IPsec with crypto map?
What are two facts about WSA HTTP proxy configuration with a PAC file? (Choose two.)
What does endpoint isolation in Cisco AMP for Endpoints security protect from?
An engineer recently completed the system setup on a Cisco WSA Which URL information does the system send to SensorBase Network servers?
Which solution is made from a collection of secure development practices and guidelines that developers must follow to build secure applications?
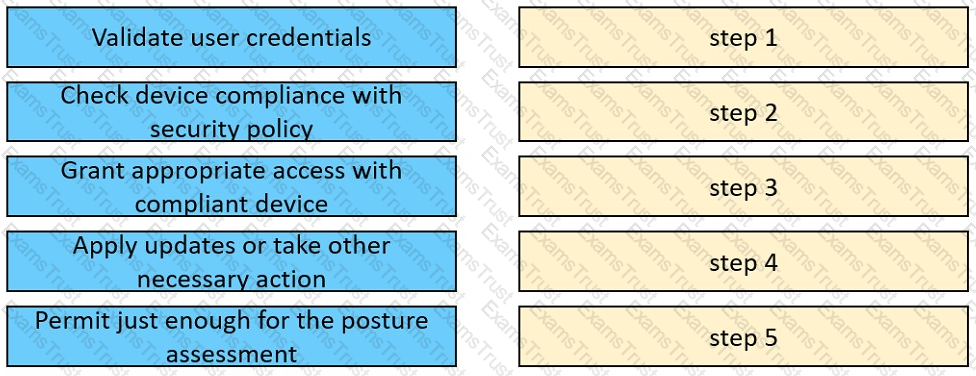
Drag and drop the posture assessment flow actions from the left into a sequence on the right.
Which two capabilities does an MDM provide? (Choose two.)
Using Cisco Cognitive Threat Analytics, which platform automatically blocks risky sites, and test unknown sites for hidden advanced threats before allowing users to click them?
What is the difference between EPP and EDR?
An organization wants to secure data in a cloud environment. Its security model requires that all users be
authenticated and authorized. Security configuration and posture must be continuously validated before access is granted or maintained to applications and data. There is also a need to allow certain application traffic and deny all other traffic by default. Which technology must be used to implement these requirements?
Which Talos reputation center allows for tracking the reputation of IP addresses for email and web traffic?
Why should organizations migrate to a multifactor authentication strategy?
Which posture assessment requirement provides options to the client for remediation and requires the
remediation within a certain timeframe?
Which Cisco security solution stops exfiltration using HTTPS?
What is a description of microsegmentation?
Which capability is provided by application visibility and control?
What are two recommended approaches to stop DNS tunneling for data exfiltration and command and control call backs? (Choose two.)
Which action configures the IEEE 802.1X Flexible Authentication feature lo support Layer 3 authentication mechanisms?
What is a benefit of using a multifactor authentication strategy?
What is the purpose of a NetFlow version 9 template record?
Drag and drop the Cisco CWS redirection options from the left onto the capabilities on the right.
A Cisco ISE engineer configures Central Web Authentication (CWA) for wireless guest access and must have the guest endpoints redirect to the guest portal for authentication and authorization. While testing the policy, the engineer notices that the device is not redirected and instead gets full guest access. What must be done for the redirect to work?
Which Cisco security solution gives the most complete view of the relationships and evolution of Internet domains IPs, and flies, and helps to pinpoint attackers' infrastructures and predict future threat?
Refer to the exhibit. When creating an access rule for URL filtering, a network engineer adds certain categories and individual URLs to block. What is the result of the configuration?
How does Cisco AMP for Endpoints provide next-generation protection?
A security test performed on one of the applications shows that user input is not validated. Which security vulnerability is the application more susceptible to because of this lack of validation?
Which method of attack is used by a hacker to send malicious code through a web application to an unsuspecting user to request that the victim's web browser executes the code?
Which feature enables a Cisco ISR to use the default bypass list automatically for web filtering?
Refer to the exhibit.
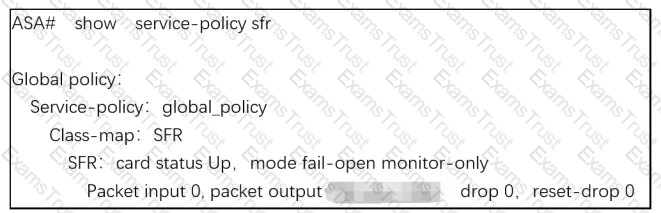
What are two indications of the Cisco Firepower Services Module configuration?
(Choose two.)
A customer has various external HTTP resources available including Intranet Extranet and Internet, with a
proxy configuration running in explicit mode. Which method allows the client desktop browsers to be configured
to select when to connect direct or when to use the proxy?
Which API method and required attribute are used to add a device into Cisco DNA Center with the native API?
Which benefit does DMVPN provide over GETVPN?
Which Cisco platform provides an agentless solution to provide visibility across the network including encrypted traffic analytics to detect malware in encrypted traffic without the need for decryption?
Which type of encryption uses a public key and private key?
An engineer has been tasked with configuring a Cisco FTD to analyze protocol fields and detect anomalies in the traffic from industrial systems. What must be done to meet these requirements?