What are two steps in the OAuth2 protocol flow? (Choose two.)
What is a consideration for using gRPC as the model-driven telemetry protocol on a Cisco IOS XE device?
Refer to the exhibit.
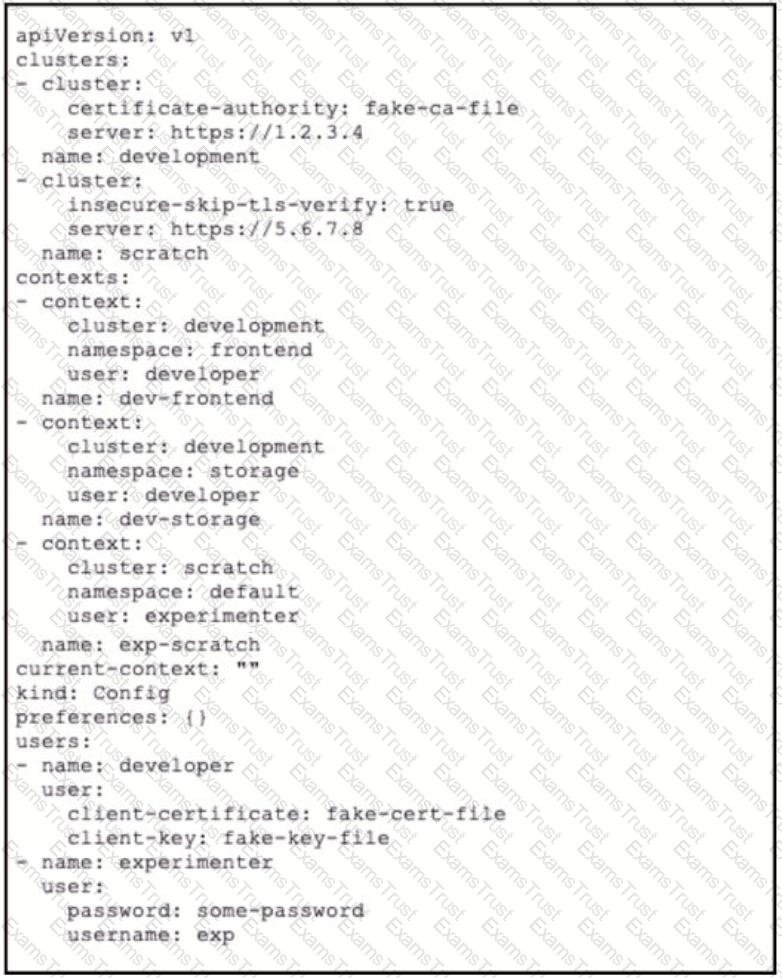
A kubeconfig file to manage access to Kubernetes clusters is shown. How many Kubernetes clusters are defined in the
file, and which cluster FS accessed using username/password authentication rather than using a certificate?
A developer must containerize a Python application to integrate into a prebuilt CD environment by creating a Docker image. It will be hosted as a web application to enable end users from accessing it remotely. Drag and drop the code from the bottom onto the box where the code is missing in the Docker file Not all options are used.
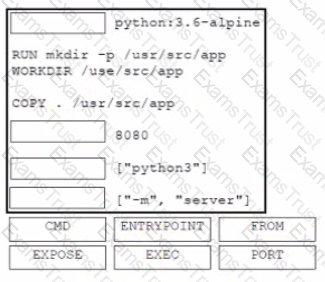
Drag and drop the expressions from below onto the code to implement error handling. Not all options are used.
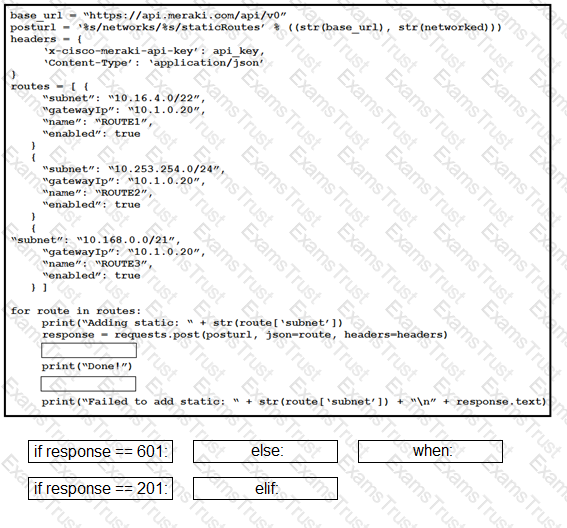
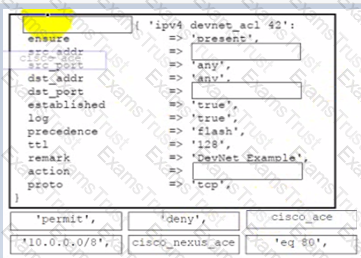
Drag and drop the code from the bottom onto the box where the code is missing to permit network traffic between 10.0.0.0/8 and all other networks on port 80 for a Cisco Nexus 9000 switch by using the Puppet module. Not all options are used.
A developer must deploy a containerized application foe network device inventory management. The developer sets up a Kubernetes duster on two separate hypervisors. The SLA is not currently meeting a specified maximum value for network latencyjitter CPU/memory and disk I/O are functioning property. Which two design approaches resolve the issue'' (Choose two.)
Refer to the exhibit.
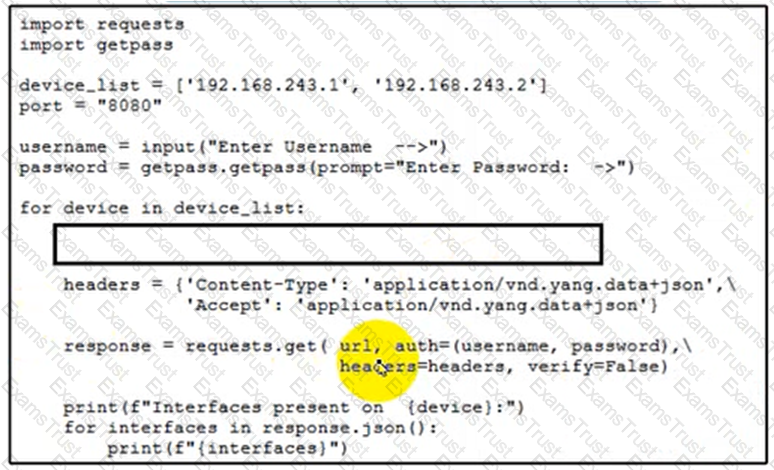
Cisco IOS XE switches are used across the entire network and the description that is filed for all interfaces must be configured. Which code snippet must be placed in the blank in the script to leverage RESTCONF to query all the devices in the device list for the interfaces that are present?
A)

B)
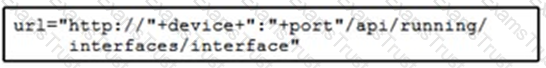
C)
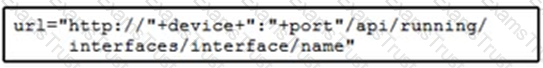
D)

An organization manages a large cloud-deployed application that employs a microservices architecture. No notable issues occur with downtime because the services of this application are redundantly deployed over three or more data center regions. However, several times a week reports are received about application slowness. The container orchestration logs show faults in a variety of containers that cause them to fail and then spin up brand new.
Which action must be taken to improve the resiliency design of the application while maintaining current scale?
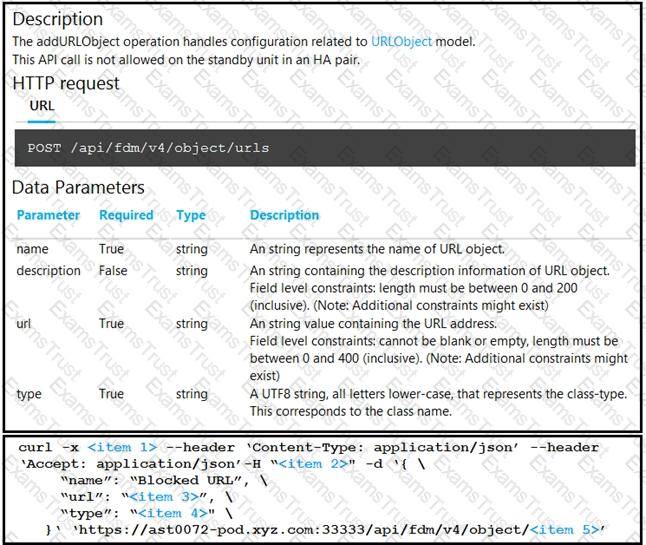
Refer to the exhibit. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the curl exhibit to complete the cURL request to FirePower Device Manager API to create objects. Not all code snippets are used.
An architect must optimize traffic that targets a popular API endpoint Currently, the application downloads a large file hourly, but often the file is unchanged and the download causes unnecessary load and delays Which cURL command must be used to determine the last modified date of the file and to optimize the API usage?
What are two benefits of using a centralized logging service? (Choose two.)
DRAG DROP
Refer to the exhibit above and click on the resource tabs in the top left corner to view resources to help with this question.
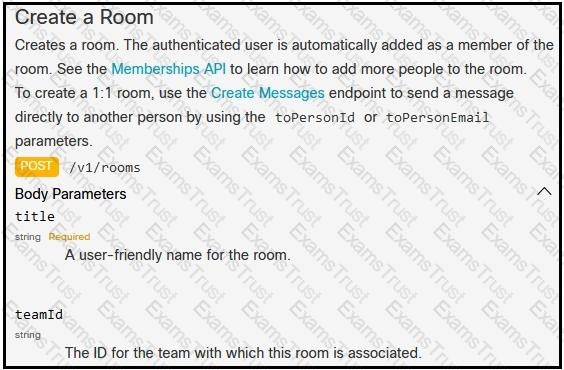
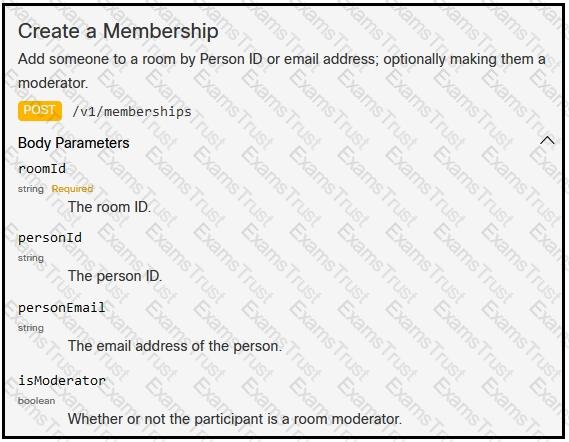
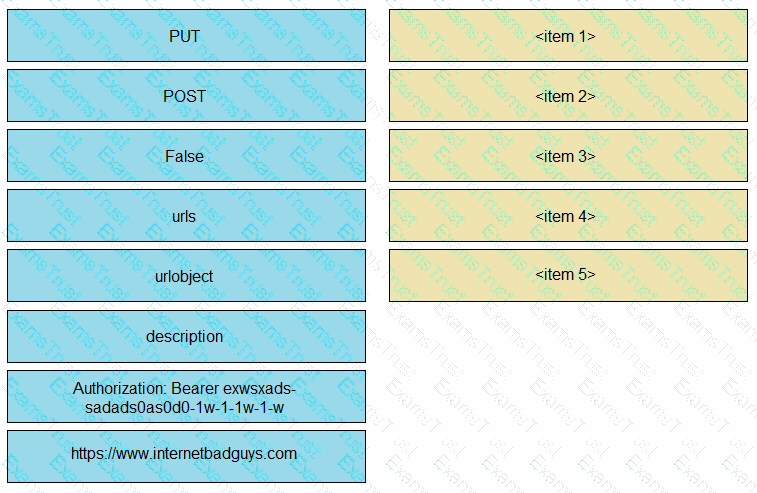
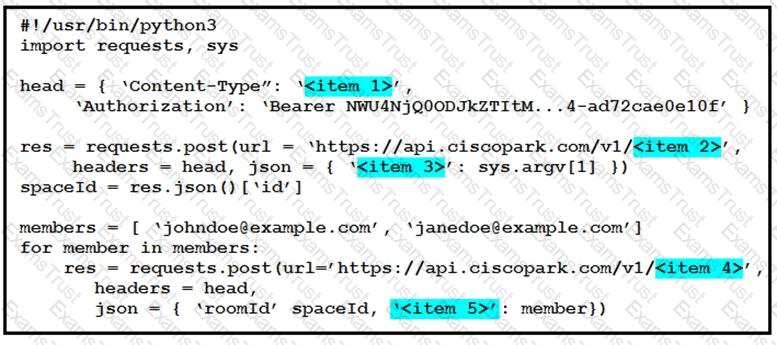
A developer is creating a Python Script that will use the Webex Teams REST API to automatically create a new collaboration space with him and his team leads on-demand via a Linux terminal command. Drag and drop the code snippets from the left onto the numbers on the right that match the missing sections in the exhibit to complete the script. Not all code snippets are used.
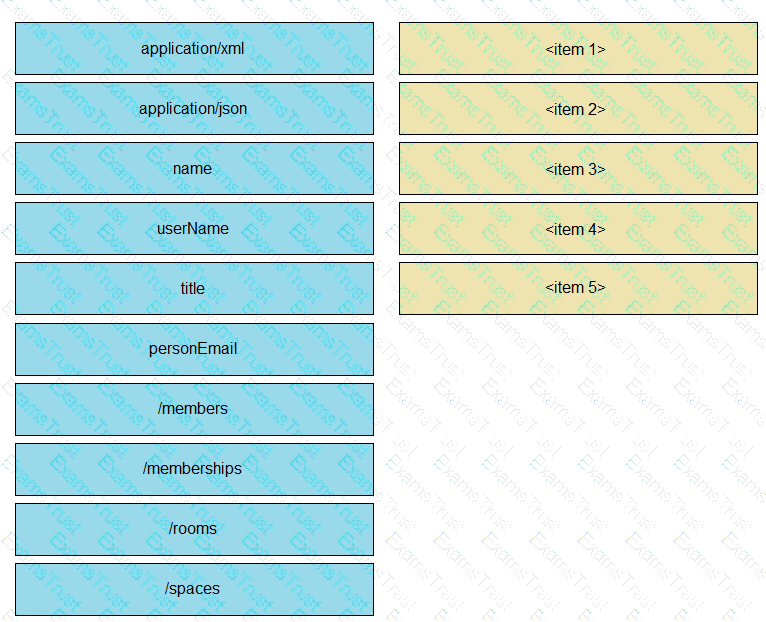
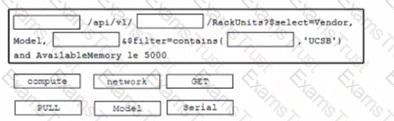
Click on the resource lab in the top left comer to view resources to help with this question An engineer is managing a data center with 6000 Cisco UCS servers installed and running The engineer is asked to identify all resources where the model is in the UCSB family and the available memory is less than or equal to 5 GB Drag and drop the code from the bottom onto the blanks in the code snippet to construct a REST API call to accomplish this task Not all options are used.
On a Cisco Catalyst 9300 Series Switch, the guest shell is being used to create a service within a container. Which change is needed to allow the service to have external access?
There is a requirement to securely store unique usernames and passwords. Given a valid username, it is also required to validate that the password provided is correct. Which action accomplishes this task?
Refer to the exhibit.
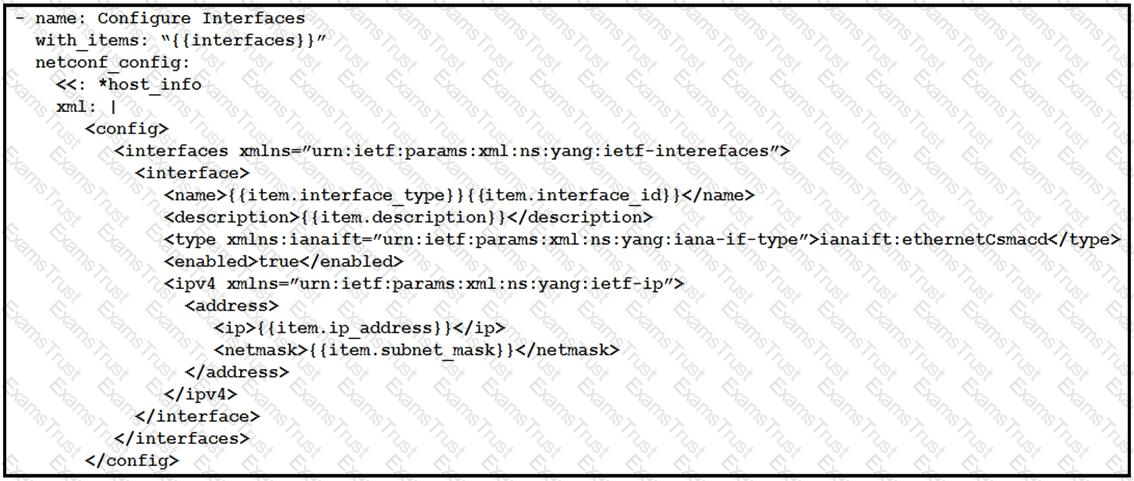
As part of the Ansible playbook workflow, several new interfaces are being configured using the netconf_config module. The task references the interface variables that are unique per device.
In which directory is the YAML file with these variables found?
A client is written that uses a REST API to interact with a server. Using HTTPS as the transport, an HTTP request is sent and received an HTTP response. The response contains the HTTP response status code: 503 Service Unavailable.
Which action is the appropriate response?
Refer to the exhibit.
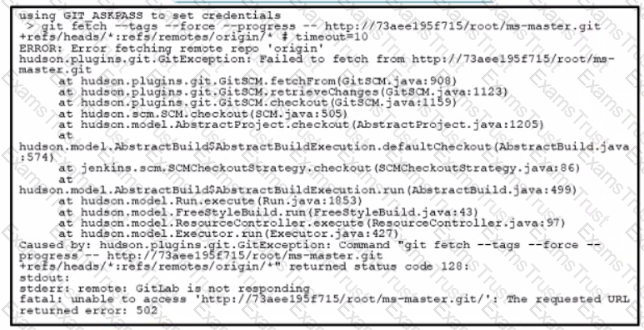
An attempt to execute a CI/CD pipeline results m the error shown What is the cause of the error?
Refer to the exhibit.
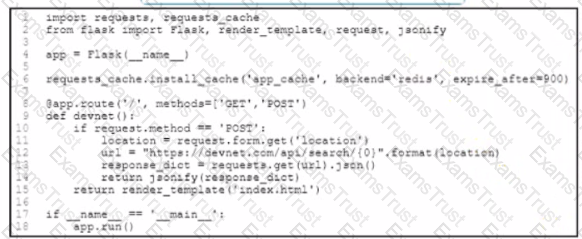
An application has been developed to serve the users in an enterprise After HTTP cache controls are implemented m the application users report that they receive state data when they refresh the page Without removing HTTP cache controls, which change ensures that the users get current data when refreshing the page'
Which type of file is created from issued intermediate, root, and primary certificates for SSL installation on a server?
Refer to the exhibit.
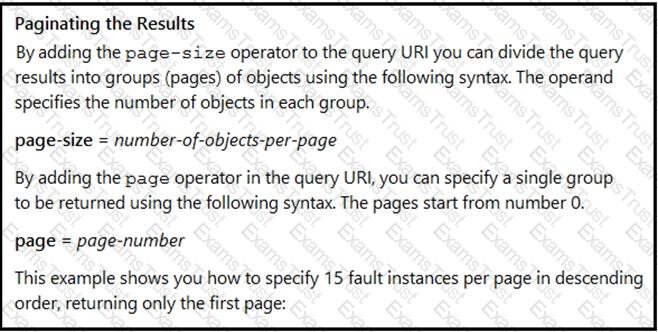
Many faults have occurred in the ACI environment and a sample of them needs to be examined. Which API call retrieves faults 30 through 45?
Which two countermeasures help reduce the risk of playback attacks? (Choose two.)
What are two advantages of using model-driven telemetry, such as gRPC. instead of traditional telemetry gathering methods? (Choose two.)
Drag and drop the code from the bottom onto the box where the code is missing the snippet to complete this Ansible Playbook. Not all options are used.

A developer is creating a Python function that adds network engineers to a Webex room to troubleshoot after a monitoring alert Drag and drop the code from the bottom onto the box where the code is missing in the Python function to add the engineers to the room. Not all options are used.
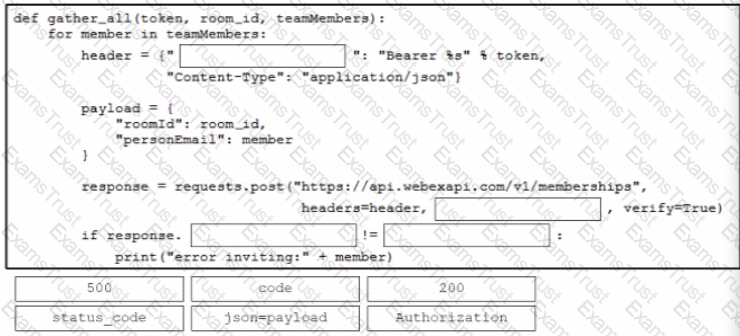
A Cisco Catalyst 9000 switch has guest shell enabled. Which Linux command installs a third-party application?
Refer to the exhibit.
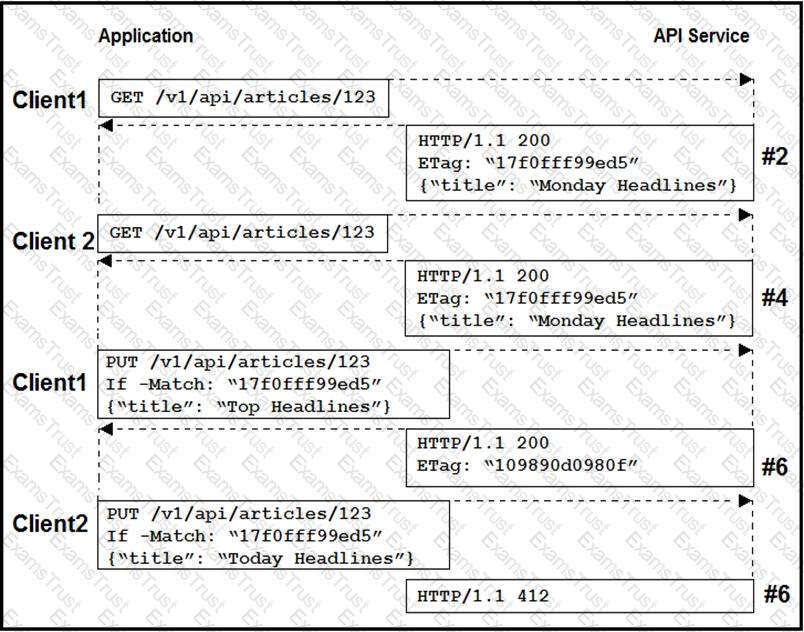
Two editors are concurrently updating an article’s headline from their mobile devices. What results from this scenario based on this REST API sequence?
A developer needs to build a new Docker image and has created a tag by using the command:
$ docker tag 32df423320458 local/app.1.2
Which command must be executed next to build the Docker image using the tag?
A)

B)
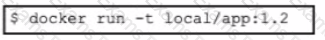
C)

D)

A timeframe custom dashboard must be developed to present data collected from Cisco Meraki. The dashboard must include a wireless health alert count. What needs to be built as a prerequisite?
Refer to the exhibit.

Which URL retrieves the errors in the GigabitEthernet 1 interface?
A)

B)

C)

D)

Which two design considerations should be considered when building a Cisco Meraki dashboard out of available APIs? (Choose two,)
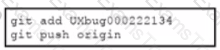
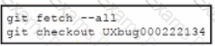
A development team is working on a bug fix in a remote branch named "UXbug000222134' and the current working primary branch is named ,prod409024967’ A developer who just joined the learn needs to checkout the remote branch Which Git commands must be used?
A)
B)

C)

D)
What is a benefit of continuous testing?
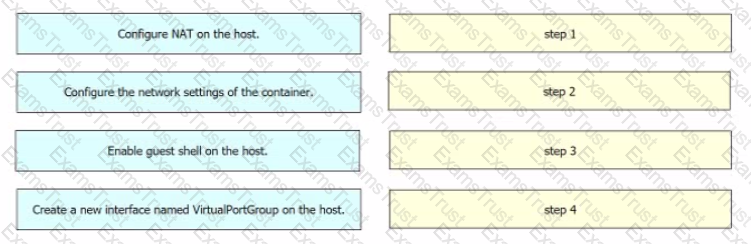
Drag and drop the steps from the left into the order on the right to ensure that an application requiring communication to the external network is hosted on a Cisco Catalyst 9000 switch.
A developer is creating a Python script to analyze errors during REST API call operations. The script will be used with Cisco solution and devices. Drag and drop the code from the bottom to the box where the code is missing to implement control flow for handling unrecoverable REST API calls. Not all options are used.

Refer to the exhibit.
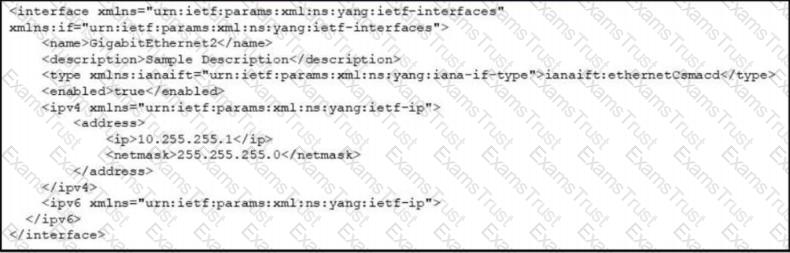
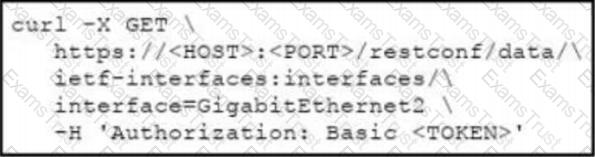
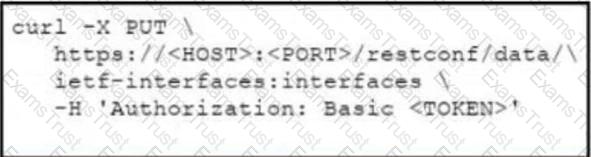
Which cURL request is included in the presented XML as the body of the response?
A)

B)

C)
D)
A new record-keeping application for employees to track customer orders must be deployed to a company's existing infrastructure. The host servers reside in a data center in a different country to where the majority of users work. The new network configuration for the database server is: •IP: 10.8.32.10
• Subnet Mask: 255.255.255.0
• Hostname: CustOrd423320458-Prod-010
• MAC: 18-46-AC-6F-F4-52.
The performance of the client-side application is a priority due to the high demand placed on it by employees. Which area should the team consider in terms of impact to application performance due to the planned deployment?
Refer to the exhibit.
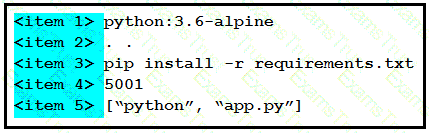
Drag and drop the correct parts of the Dockerfile from the left onto the item numbers on the right that match the missing sections in the exhibit to complete the Dockerfile to successfully build and deploy a container running a Python application. Not all parts of the Dockerfile are used.
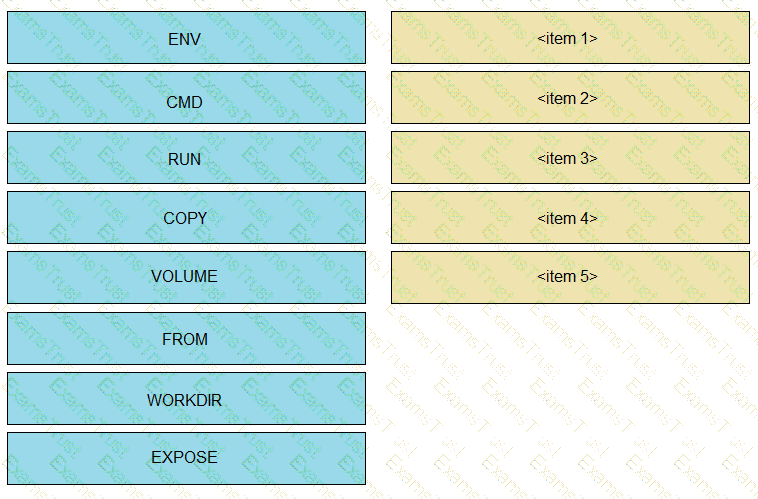
Refer to the exhibit.
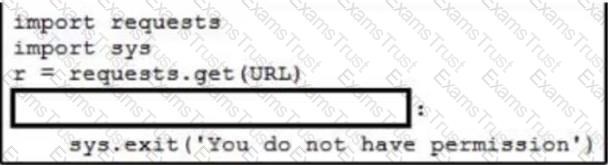
A network engineer needs to handle API errors in their requests when users do not have permission to access the resource, even if they are authenticated and authorized. Which line of code needs to be placed on the snippet where the code is missing to handle these API errors?
Refer to the exhibit.

A Python script must list network clients in the Cisco Meraki API that have used a network with an ID of 2 The number of client entries per returned page is restricted to 1.000 according to the API specification Network 2 has 2.500 clients What must be added where the code is missing to print the content of each response?
A)
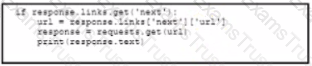
B)

C)

D)

Refer to the exhibit.
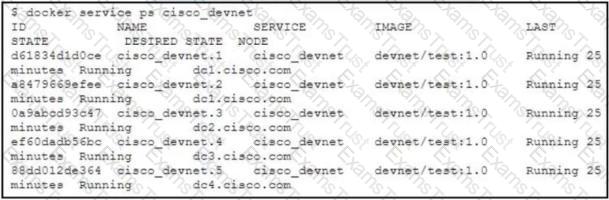
The cisco_devnet Docker swarm service runs across five replicas.The development team tags and imports a new image named devnet/ test:1.1 and requests that the image be upgraded on each container.There must be no service outages during the upgrade process. Which two design approaches must be used? (Choose two.)
Refer to the exhibit.
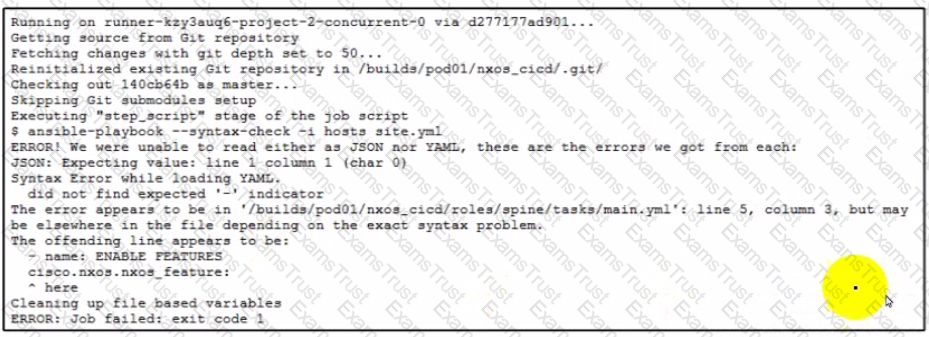
A network engineer developed an Ansible playbook and committed it to GitLab. A GitLab CI pipeline is started but immediately fails. What is the issue?
An application is developed in order to communicate with Cisco Webex. For reporting, the application must retrieve all the messages sent to a Cisco Webex room on a monthly basis.
Which action calls /v1/messages directly?
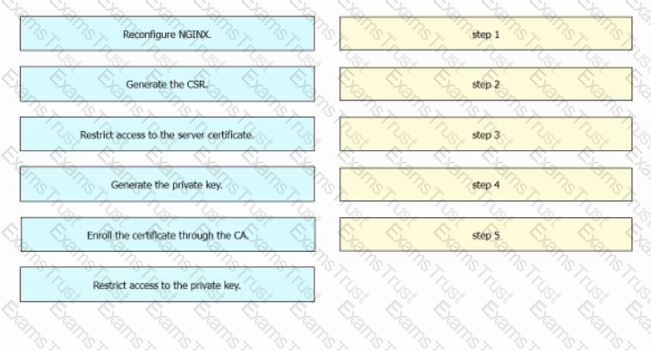
An engineer has created an NGINX web server. The server will be accessible from outside the organization. A public-key certificate must be installed before external access is allowed Drag and drop the steps from the left into the order on the right to configure the certificate. Not all options are used
{'lat': 37.4180951010362, 'lng': -122.098531723022, 'address': '', 'serial': 'Q2HP-F5K5-F98Q',
'mac': '88:15:44:ea:f5:bf', 'lanIp': '10.10.10.15',
'url': 'https://n149.meraki.com/DevNet-Sandbox/n/EFZDavc/manage/nodes/new_list/78214561218351',
'model': 'MS220-8P', 'switchProfileId': None, 'firmware': 'switch-11-31', 'floorPlanId': None}
Refer to the exhibit. A developer needs to find the geographical coordinates of a device on the network L_397561557481105433 using a Python script to query the Meraki API. After running response = requests.get() against the Meraki API, the value of response.text is shown in the exhibit.
What Python code is needed to retrieve the longitude and latitude coordinates of the device?
Where mus! the data be encrypted to ensure end-to-end encryption when using an API?
Refer to the exhibit.


An engineer writes a script to retrieve data from a REST API and must build support for cases where the response that contains data from the server may take a longer time than normal Which code must be added to the snippet where the code is missing to catch such a timeout?
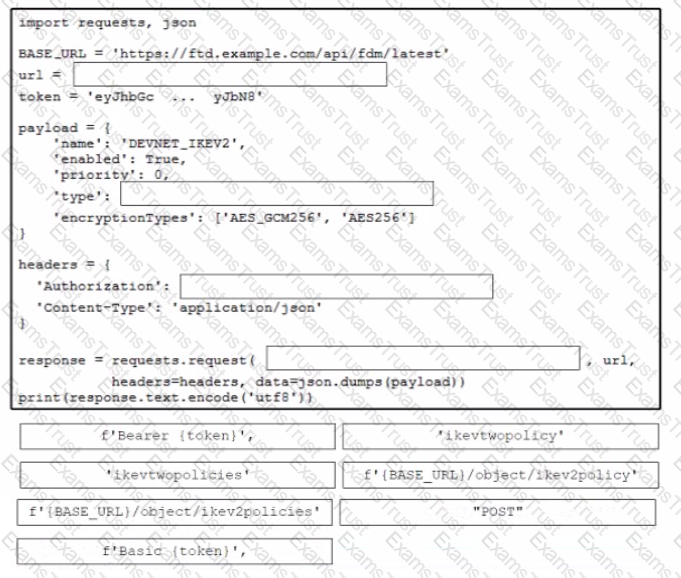
Drag and drop the code from the bottom onto the box where the code is missing to create a new IKEv2 policy Not all options are used
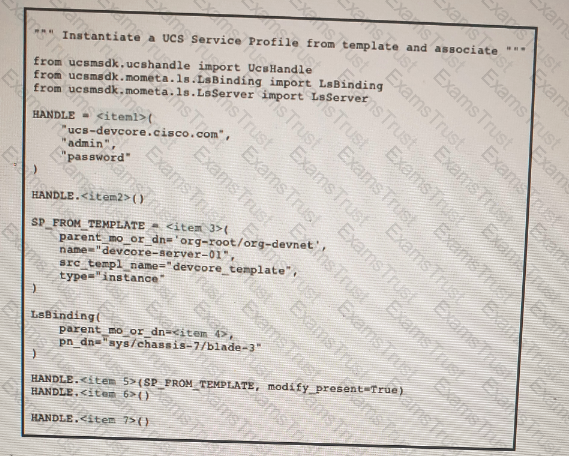
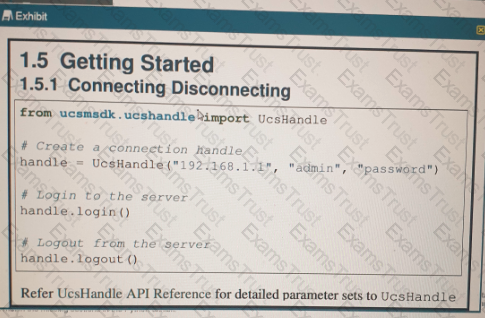
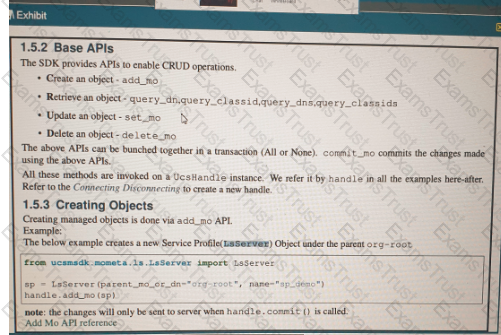
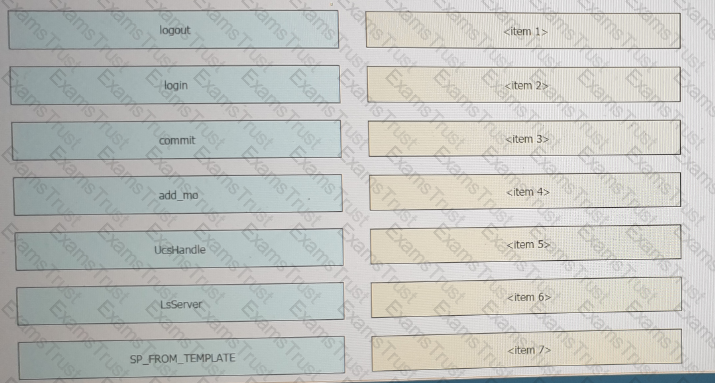
Refer to the exhibit above and click on the resource tabs in the top left corner to view resources to help with this question. Python code that uses the UCS Python SDK is instantiating a service profile named ''devcore-server-01'' from service profile template ''device-template'' , then associating the service profile instance to blade 3 in chassis 7. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the Python exhibit.
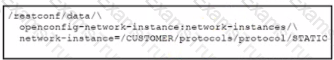
Refer to the exhibit.

A)
B)

C)

D)
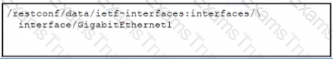
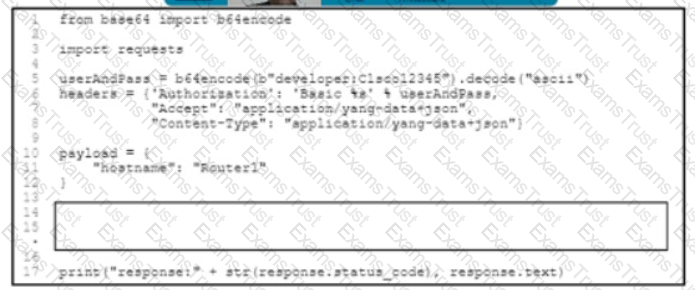
Refer to me exhibit The Python code manages a Cisco CSR 1000V router Which code snippet must be placed in the blank m the code to update the current configuration of the targeted resource?
A)

B)

C)
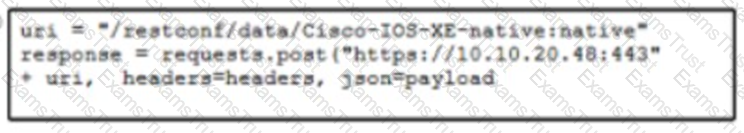
D)

Refer to the exhibit.
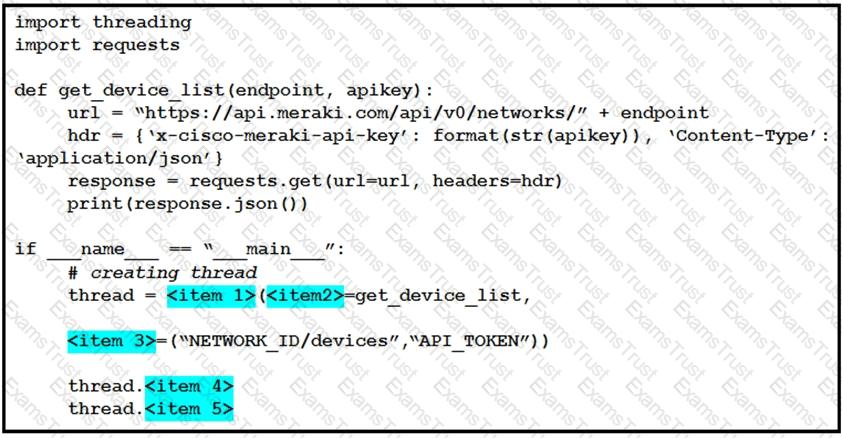
Python threading allows a developer to have different parts of a program run concurrently and simplify a design. Drag and drop the code snippets from the left onto the item numbers on the right that match the missing sections in the exhibit to create a thread instance.
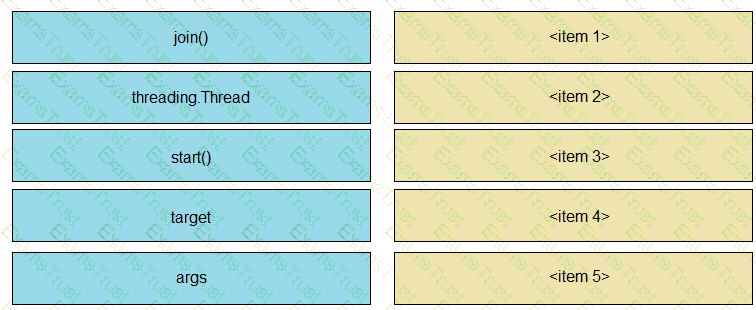
Refer to the exhibit.
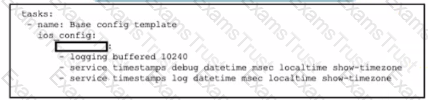
Which word is missing from this Ansible playbook shown, to allow the Cisco IOS XE commands for router configuration to be pushed after the playbook is executed?