A systems administrator is troubleshooting performance issues with a Windows VDI environment. Users have reported that VDI performance is very slow at the start of the workday, but the performance is fine during the rest of the day. Which of the following is the MOST likely cause of the issue? (Choose two.)
An IaaS application has a two-hour RTO and a four-hour RPO. The application takes one hour to back up its data or restore from a local backup file. A systems administrator is tasked with configuring the backup policy.
Which of the following should the administrator configure to achieve the application requirements with the LEAST cost?
A systems administrator recently upgraded the processors in a web application host. Upon the next login, the administrator sees a new alert regarding the license being out of compliance.
Which of the following licensing models is the application MOST likely using?
Company A has acquired Company B and is in the process of integrating their cloud resources. Company B needs access to Company A’s cloud resources while retaining its IAM solution.
Which of the following should be implemented?
A company has decided to get multiple compliance and security certifications for its public cloud environment. However, the company has few staff members to handle the extra workload, and it has limited knowledge of the current infrastructure.
Which of the following will help the company meet the compliance requirements as quickly as possible?
A SaaS provider wants to maintain maximum availability for its service.
Which of the following should be implemented to attain the maximum SLA?
A systems administrator is configuring RAID for a new server. This server will host files for users and replicate to an identical server. While redundancy is necessary, the most important need is to maximize storage.
Which of the following RAID types should the administrator choose?
An organization requires the following to be achieved between the finance and marketing departments:
Allow HTTPS/HTTP.
Disable FTP and SMB traffic.
Which of the following is the MOST suitable method to meet the requirements?
A systems administrator is creating a playbook to run tasks against a server on a set schedule.
Which of the following authentication techniques should the systems administrator use within the playbook?
Which of the following strategies will mitigate the risk of a zero-day vulnerability MOST efficiently?
The security team for a large corporation is investigating a data breach. The team members are all trying to do the same tasks but are interfering with each other’s work.
Which of the following did the team MOST likely forget to implement?
An organization will be deploying a web application in a public cloud with two web servers, two database servers, and a load balancer that is accessible over a single public IP.
Taking into account the gateway for this subnet and the potential to add two more web servers, which of the following will meet the minimum IP requirement?
A systems administrator would like to reduce the network delay between two servers.
Which of the following will reduce the network delay without taxing other system resources?
A systems administrator disabled TLS 1.0 and 1.1, as well as RC4, 3DES, and AES-128 ciphers for TLS 1.2, on a web server. A client now reports being unable to access the web server, but the administrator verifies that the server is online, the web service is running, and other users can reach the server as well.
Which of the following should the administrator recommend the user do FIRST?
A global web-hosting company is concerned about the availability of its platform during an upcoming event. Web traffic is forecasted to increase substantially during the next week. The site contains mainly static content.
Which of the following solutions will assist with the increased workload?
A company wants to check its infrastructure and application for security issues regularly. Which of the following should the company implement?
A systems administrator is deploying a solution that requires a virtual network in a private cloud environment. The solution design requires the virtual network to transport multiple payload types.
Which of the following network virtualization options would BEST satisfy the requirement?
A systems administrator is deploying a new storage array for backups. The array provides 1PB of raw disk space and uses 14TB nearline SAS drives. The solution must tolerate at least two failed drives in a single RAID set.
Which of the following RAID levels satisfies this requirement?
Which of the following cloud deployment models allows a company to have full control over its IT infrastructure?
Lateral-moving malware has infected the server infrastructure.
Which of the following network changes would MOST effectively prevent lateral movement in the future?
An organization purchased new servers with GPUs for render farms. The servers have limited CPU resources.
Which of the following GPU configurations will be the MOST optimal for virtualizing this environment?
An organization has the following requirements that need to be met when implementing cloud services:
SSO to cloud infrastructure
On-premises directory service
RBAC for IT staff
Which of the following cloud models would meet these requirements?
A systems administrator needs to convert ten physical servers to virtual.
Which of the following would be the MOST efficient conversion method for the administrator to use?
A cloud administrator is setting up a DR site on a different zone of the same CSP. The application servers are replicated using the VM replication, and the database replication is set up using log shipping. Upon testing the DR site, the application servers are unable to access the database servers. The administrator has verified the systems are running and are accessible from the CSP portal.
Which of the following should the administrator do to fix this issue?
A company has deployed a new cloud solution and is required to meet security compliance.
Which of the following will MOST likely be executed in the cloud solution to meet security requirements?
Which of the following will mitigate the risk of users who have access to an instance modifying the system configurations?
A technician is working with an American company that is using cloud services to provide video-based training for its customers. Recently, due to a surge in demand, customers in Europe are experiencing latency.
Which of the following services should the technician deploy to eliminate the latency issue?
A systems administrator wants the VMs on the hypervisor to share CPU resources on the same core when feasible.
Which of the following will BEST achieve this goal?
A company is switching from one cloud provider to another and needs to complete the migration as quickly as possible.
Which of the following is the MOST important consideration to ensure a seamless migration?
Which of the following is relevant to capacity planning in a SaaS environment?
A systems administrator is provisioning VMs in a cloud environment and has been told to select an OS build with the furthest end-of-life date.
Which of the following OS builds would be BEST for the systems administrator to use?
A storage array that is used exclusively for datastores is being decommissioned, and a new array has been installed. Now the private cloud administrator needs to migrate the data.
Which of the following migration methods would be the BEST to use?
A cloud engineer is responsible for managing two cloud environments from different MSPs. The security department would like to inspect all traffic from the two cloud environments.
Which of the following network topology solutions should the cloud engineer implement to reduce long-term maintenance?
A systems administrator needs to configure a set of policies to protect the data to comply with mandatory regulations.
Which of the following should the administrator implement to ensure DLP efficiently prevents the exposure of sensitive data in a cloud environment?
One of the web applications in a public subnet is vulnerable to a newly discovered zero-day vulnerability. Which of the following actions can a security engineer perform to reduce the risk of exploitation and application downtime?
A cloud solutions architect has an environment that must only be accessed during work hours. Which of the following processes should be automated to BEST reduce cost?
Which of the following are advantages of a public cloud? (Select TWO).
A systems administrator has verified that a physical switchport that is connected to a virtualization host is using all available bandwidth. Which of the following would best address this issue?
A company is using laaS services from two different providers: one for its primary site, and the other for a secondary site. The primary site is completely inaccessible, and the management team has decided to run through the BCP procedures. Which of the following will provide the complete asset information?
A cloud engineer needs to perform a database migration. The database has a restricted SLA and cannot be offline for more than ten minutes per month. The database stores 800GB of data, and the network bandwidth to the CSP is 100MBps Which of the following is the best option to perform the migration?
A cloud administrator for a retail business identified a significant month-to-month increase in the cost of storage. The current IaaS instances are hosting the organization's ERP solution. Which of the following is the most likely cause for the cost increase?
A cloud engineer is troubleshooting a performance issue for a high-traffic, cloud-based application that provides static content to its geographically distributed users. The engineer needs to:
Improve the performance of an application.
Implement a static content caching mechanism.
Protect against DDoS attacks.
Maintain low cost.
Which of the following strategies would best accomplish this task?
An IT administrator is implementing security controls on an OS. Which of the following will provide the best protection against a brute-force attack? (Select two).
An integration application that communicates between different application and database servers is currently hosted on a physical machine. A P2V migration needs to be done to reduce the hardware footprint. Which of the following should be considered to maintain the same level of network throughput and latency in the virtual server?
A company is moving its entire infrastructure to the cloud. The infrastructure consists of:
100 virtual desktops
10 database servers
10 web servers
15 application servers
15 development servers
7 VDI servers
Each server, except for web, application, and database servers, needs to be on an isolated subnet. The CSP has allocated a /24 subnet. Which of the following would best divide the IP space to meet these requirements?
Options:
A systems administrator is deploying a new version of a website. The website is deployed in the cloud using a VM cluster. The administrator must then deploy the new version into one VM first. After a period of time, if there are no issues detected, a second VM will be updated. This process must continue until all the VMS are updated. Which of the following upgrade methods is being implemented?
A cloud engineer is configuring automated backups for a database. The engineer wants to ensure that backups can be restored quickly and consistently to meet the SLA. Which of the following backup methods would be the most appropriate?
A cloud engineer is deploying a server in a cloud platform. The engineer reviews a security scan report. Which of the following recommended services should be disabled? (Select TWO).
A cloud administrator needs to verify domain ownership with a third party. The third party has provided a secret that must be added to the DNS server. Which of the following DNS records does the administrator need to update to include the secret?
A cloud engineer is required to move legacy systems to a public cloud. The system configuration is provided below:
Server Name
Cores
OS Disk (Used)
Data Disk (Used)
Encryption
Web1
2
500GB (45%)
1TB (20%)
OS
Web2
2
500GB (40%)
1TB (90%)
OS
App1
4
250GB (90%)
2TB (65%)
No
App2
4
250GB (70%)
2TB (95%)
No
DB1
16
250GB (25%)
4TB (65%)
Data
The public cloud provider VMs support a maximum OS disk size of 250GB and a data disk size of 2TB. Which of the following tasks will contribute to a successful migration to the cloud environment? (Select two).
A company is concerned it will run out of VLANs on its private cloud platform in the next couple months, and the product currently offered to customers requires the company to allocate three dedicated, segmented tiers. Which of the following can the company implement to continue adding new customers and to maintain the required level of isolation from other tenants?
A company that performs passive vulnerability scanning at its transit VPC has detected a vulnerability related to outdated web-server software on one of its public subnets. Which of the following can the company use to verify if this is a true positive with the least effort and cost? (Select two).
A company is comparing an application environment to be hosted on site versus a SaaS model of the same application. Which of the following SaaS-based licensing models should the administrator consider?
A cloud administrator created four VLANs to autoscale the container environment. Two of the VLANs are on premises, while two VLANs are on a public cloud provider with a direct link between them. Firewalls are between the links with an additional subnet for communication, which is 192.168.5.0/24.
The on-premises gateways are:
192.168.1.1/24
192.168.2.1/24
The cloud gateways are:
192.168.3.1/24
192.168.4.1/24
The orchestrator is unable to communicate with the cloud subnets. Which Of the following should the administrator do to resolve the issue?
A systems administrator needs to implement a way for users to verify software integrity. Which of the following tools would BEST meet the administrator's needs?
A company has entered into a business relationship with another organization and needs to provide access to internal resources through directory services. Which of the following should a systems administrator implement?
A cloud administrator is assessing the scaling of an infrastructure stack. When viewing the configuration, the cloud administrator notices that the servers have a maximum limit of three. Which of the following is a way to increase throughput for the three servers without adjusting the maximum scaling limits?
A company uses multiple SaaS-based cloud applications. All the applications require authentication upon access. An administrator has been asked to address this issue and enhance security. Which of the following technologies would be the BEST solution?
A cloud administrator is reviewing the performance of a database cluster hosted in a public cloud and sees that the CPU and memory utilization is high during periods of non-peak usage. The administrator wants to proactively prevent any performance issues during periods of high-peak usage. The database software is using an instance-based licensing model. Which of the following scaling strategies should the administrator consider?
A systems administrator is troubleshooting a VDI deployment that is used to run high-frame-rate rendering. Users are reporting frequent application crashes. After running a benchmark, the administrator discovers the following:
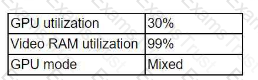
Which of the following should the administrator do to resolve this issue?
A systems administrator is diagnosing performance issues on a web application. The web application sends thousands of extremely complex SQL queries to a database server, which has trouble retrieving the information in time. The administrator checks the database server and notes the following resource utilization:
CPU: 64%
RAM: 97%
Network throughput: 384/1000 Kbps
Disk throughput: 382,700 Kbps
The administrator also notices that the storage for the database server is consistently near its IOPS limit. Which of the following will best resolve these performance issues?
A cloud administrator notices an e-commerce website was recently warned that the connection is not private. Which of the following is most likely the cause?
A systems administrator has a redundant backup system in place. Which of the following should the systems administrator perform to maintain efficient operation and comply with the global standard in the corporate backup policies?
A cloud engineer receives an alert that a newly provisioned server is running a non-supported Linux version. The automation scripts are performing as expected on the server. Which of the following should the engineer check first?
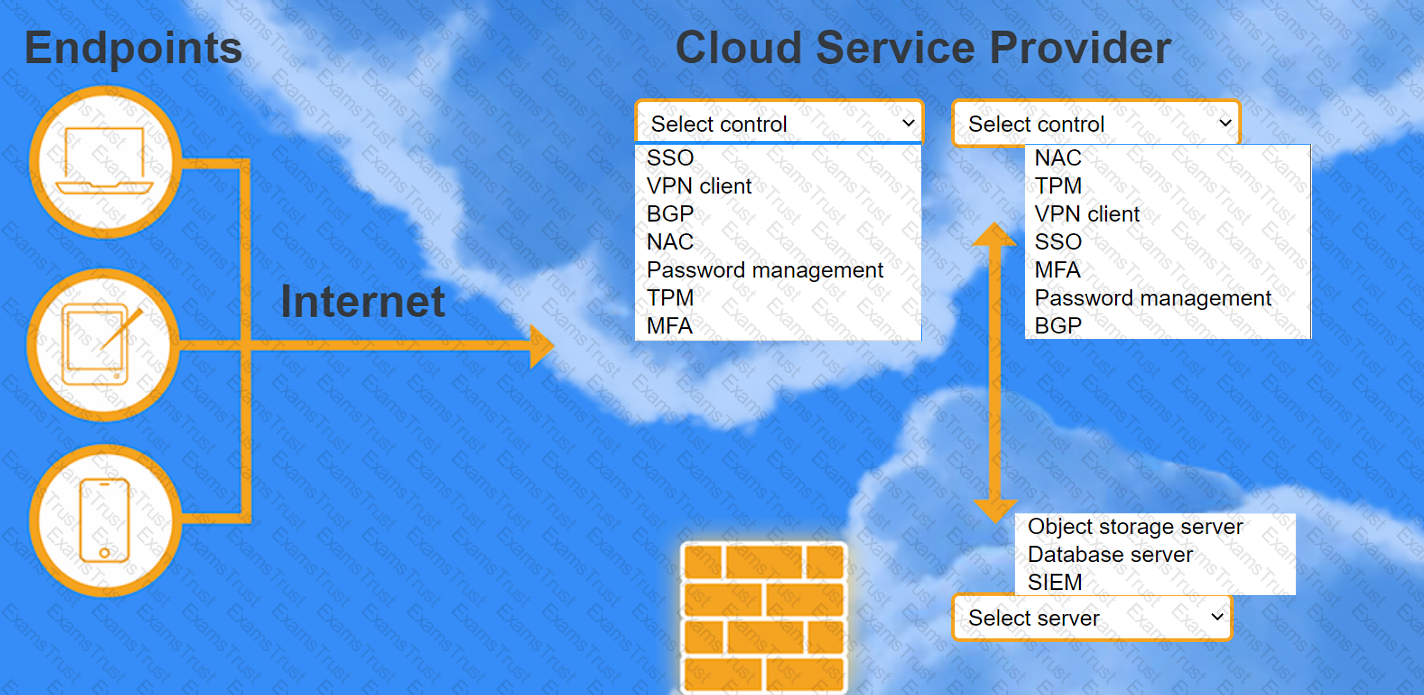
A highly regulated business is required to work remotely, and the risk tolerance is very low. You are tasked with providing an identity solution to the company cloud that includes the following:
secure connectivity that minimizes user login
tracks user activity and monitors for anomalous activity
requires secondary authentication
INSTRUCTIONS
Select controls and servers for the proper control points.
A cloud administrator is configuring a CDN for an organization’s website to improve performance for users in remote regions. Which of the following CDN features will help achieve this goal?
A VDI administrator is deploying 512 desktops for remote workers. Which of the following would meet the minimum number of IP addresses needed for the desktops?
A systems administrator received a report stating resumes submitted through the company's website are being exposed at the URL Which of the following actions should the administrator take to fix the issue?
A company is deploying a public cloud solution for an existing application using lift and shift. The requirements for the applications are scalability and external access. Which of the following should the company implement? (Select TWO).
A DevOps administrator is building a new application slack in a private cloud. This application will store sensitive information and be accessible from the internet. Which of the following would be MOST useful in maintaining confidentiality?
A company would like to migrate its current on-premises workloads to the public cloud. The current platform requires at least 80 instances running at all times to work properly. The company wants the workload to be highly available, even if the cloud provider loses one region due to a catastrophe, and the costs to be kept to a minimum. Which of the following strategies should the company implement?
A web-application company recently released some new marketing promotions without notifying the IT staff. The systems administrator has since been noticing twice the normal traffic consumption every two hours for the last three hours in the container environment. Which of the following should the company implement to accommodate the new traffic?
A systems administrator needs to migrate email services to the cloud model that requires the least amount of administrative effort. Which of the following should the administrator select?
A company is performing a DR drill and is looking to validate its documentation. Which of the following metrics will determine the service recovery duration?
A systems administrator is setting up a backup solution to follow the 3-2-1 policy. Currently, the solution is set to back up from the servers to an on-site storage server. Which of the following should the administrator configure to comply with the 3-2-1 policy?
A systems administrator is planning a penetration test for company resources that are hosted in a public cloud. Which of the following must the systems administrator do FIRST?
While investigating network traffic, a cloud administrator discovers the monthly billing has increased substantially. Upon further review, it appears the servers have been compromised, and sensitive files have been exfiltrated. Which of the following can be implemented to maintain data confidentiality?
A cloud administrator needs to control the connections between a group of web servers and database servers as part of the financial application security review. Which of the following would be the BEST way to achieve this objective?
A company has hired a security firm to perform a vulnerability assessment of its environment. In the first phase, an engineer needs to scan the network services exposed by the hosts. Which of the following will help achieve this with the LEAST privileges?
An administrator needs to back up all the data from each VM daily while also saving space. Which of the following backup types will BEST fit this scenario?
A production engineer is configuring a new application, which is running in containers, that requires access to a database. Which of the following methods will allow the application to authenticate to the database in the MOST secure way?
A cloud administrator is responsible for managing a VDI environment that provides end users with access to limited applications. Which of the following should the administrator make changes to when a new application needs to be provided?
A cloud administrator configured a local cloud-resource pool lo offer 64GB of memory, 64 cores, and 640GB of storage. Thirty-two machines with identical resource allocations are started. but one machine is unable to handle requests. Which of the following is the MOST likely cause?
A systems administrator is asked to implement a new three-host cluster. The cloud architect specifies this should be a testing environment, and the budget is limited. The estimated resource consumption for each application is as follows:
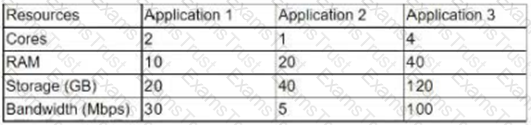
A systems administrator deployed a new application release to the green stack of a blue-green infrastructure model and made the green stack primary. Immediately afterward, users began reporting application issues. The systems administrator must take action to bring the service online as quickly as possible. Which of the following is the FASTEST way to restore the service?
A large pharmaceutical company needs to ensure it is in compliance with the following requirements:
• An application must run on its own virtual machine.
• The hardware the application is hosted on does not change.
Which of the following will BEST ensure compliance?
A cloud administrator is troubleshooting a highly available web application running within three containers behind a Layer 7 load balancer with a WAF inspecting all traffic. The application frequently asks the users to log in again even when the session timeout has not been reached. Which of the following should the cloud administrator configure to solve this issue?
A cloud administrator has created a new asynchronous workflow lo deploy VMs to the cloud in bulk. When the workflow is tested for a single VM, it completes successfully. However, if the workflow is used to create 50 VMs at once, the job fails. Which of the following is the MOST likely cause of the issue? (Choose two.)
A cloud security engineer needs to ensure authentication to the cloud pro-vider console is secure. Which of the following would BEST achieve this ob-jective?
A financial industry services firm was the victim of an internal data breach, and the perpetrator was a member of the company's development team. During the investigation, one of the security administrators accidentally deleted the perpetrator's user data. Even though the data is recoverable, which of the following has been violated?
A product-based company wants to transition to a method that provides the capability to enhance the product seamlessly and keep the development iterations to a shorter time frame. Which of the following would BEST meet these requirements?
Which of the following should a cloud architect consider for a containerized cluster in a cloud environment?
An enterprise recently upgraded the memory of its on-premises VMs from 8GB to 16GB. However, users are not experiencing any performance benefit. Which of the following is the MOST likely reason?
A cloud administrator needs to coordinate and automate the management of a company's secrets and keys for all its cloud services with minimal effort and low cost. Which of the following is the BEST option to achieve the goal?
A security team is conducting an audit of the security group configurations for the Linux servers that are hosted in a public laaS. The team identifies the following rule as a potential
A cloud administrator, who is working remotely, logs in to the cloud management console and modifies the rule to set the source to "My IR" Shortly after deploying the rule, an internal developer receives the following error message when attempting to log in to the server using SSH: Network error: connection timed out. However, the administrator is able to connect successfully to the same server using SSH. Which of the following is the BEST option for both the developer and the administrator to access the
server from their locations?
A systems administrator must ensure confidential company information is not leaked to competitors. Which of the following services will BEST accomplish this goal?
A cloud engineer recently used a deployment script template to implement changes on a cloud-hosted web application. The web application communicates with a managed database on the back end. The engineer later notices the web application is no longer receiving data from the managed database. Which of the following is the MOST likely cause of the issue?
A company has two primary offices, one in the United States and one in Europe. The company uses a public laaS service that has a global data center presence to host its marketing materials. The marketing team, which is primarily based in Europe, has reported latency issues when retrieving these materials. Which of the following is the BEST option to reduce the latency issues?
After initial stress testing showed that a platform performed well with the specification of a single 32 vCPU node, which of the following will provide the desired service with the LOWEST cost and downtime?
A cloud solutions architect has received guidance to migrate an application from on premises to a public cloud. Which of the following requirements will help predict the operational expenditures in the cloud?
An organization is hosting its dedicated email infrastructure with unlimited mailbox creation capability. The management team would like to migrate to a SaaS-based solution. Which of the following must be considered before the migration?
A cloud administrator would like to maintain file integrity checks through hashing on a cloud object store. Which of the following is MOST suitable from a performance perspective?
Which of the following will provide a systems administrator with the MOST information about potential attacks on a cloud IaaS instance?
A system administrator has provisioned a new web server. Which of the following, in combination, form the best practice to secure the server's OS? (Choose three.)
A system administrator supports an application in the cloud, which includes a restful API that receives an encrypted message that is passed to a calculator system. The administrator needs to ensure the proper function of the API using a new automation tool. Which of the following techniques would be BEST for the administrator to use to accomplish this requirement?
A technician needs to deploy two virtual machines in preparation for the configuration of a financial application next week. Which of the following cloud deployment models should the technician use?
A systems administrator is deploying a new cloud application and needs to provision cloud services with minimal effort. The administrator wants to reduce the tasks required for maintenance, such as OS patching, VM and volume provisioning, and autoscaling configurations. Which of the following would be the BEST option to deploy the new application?
A company is preparing a hypervisor environment to implement a database cluster. One of the requirements is to share the disks between the nodes of the cluster to access the same LUN. Which of the following protocols should the company use? (Choose two.)
Users of a public website that is hosted on a cloud platform are receiving a message indicating the connection is not secure when landing on the website. The administrator has found that only a single protocol is opened to the service and accessed through the URL Which of the following would MOST likely resolve the issue?
A company needs a solution to find content in images. Which of the following technologies, when used in conjunction with cloud services, would facilitate the BEST solution?
Some VMs that are hosted on a dedicated host server have each been allocated with 32GB of memory. Some of VMs are not utilizing more than 30% of the allocation. Which of the following should be enabled to optimize the memory utilization?
A systems administrator swapped a failed hard drive on a server with a RAID 5 array. During the RAID resynchronization, a second hard drive failed.
Which of the following actions will make the server fully operational?
A systems administrator is examining a managed hosting agreement and wants to determine how much data would be lost if a server had to be restored from backups. To which of the following metrics should the administrator refer?
An organization is developing a new solution for hosting an external website. The systems administrator needs the ability to manage the OS. Which of the following methods would be MOST suitable to achieve this objective?
A systems administrator is deploying a VM and would like to minimize storage utilization by ensuring the VM uses only the storage if needs. Which of the following will BEST achieve this goal?
A technician is trying to delete six decommissioned VMs. Four VMs were deleted without issue. However, two of the VMs cannot be deleted due to an error. Which of the following would MOST likely enable the technician to delete the VMs?
An update is being deployed to a web application, and a systems administrator notices the cloud SQL database has stopped running. The VM is responding to pings, and there were not any configuration changes scheduled for the VM. Which of the following should the administrator check NEXT?
After a hardware upgrade on a private cloud system, the systems administrator notices a considerable drop in network performance. Which of the following is MOST likely the cause?
A cloud security analyst needs to ensure the web servers in the public subnet allow only secure communications and must remediate any possible issue. The stateful configuration for the public web servers is as follows:
Which of the following actions should the analyst take to accomplish the objective?
A systems administrator is creating a VM and wants to ensure disk space is not allocated to the VM until it is needed. Which of the following techniques should the administrator use to ensure?
A systems administrator adds servers to a round-robin, load-balanced pool, and then starts receiving reports of the website being intermittently unavailable. Which of the following is the MOST likely cause of the issue?
A cloud administrator needs to reduce the cost of cloud services by using the company's off-peak period. Which of the following would be the BEST way to achieve this with minimal effort?
A cloud administrator is managing an organization's infrastructure in a public cloud. All servers are currently located in a single virtual network with a single firewall that all traffic must pass through. Per security requirements, production, QA, and development servers should not be able to communicate directly with each other. Which of the following should an administrator perform to comply with the security requirement?
A company needs to migrate the storage system and batch jobs from the local storage system to a public cloud provider. Which of the following accounts will MOST likely be created to run the batch processes?
A systems administrator is working in a globally distributed cloud environment. After a file server VM was moved to another region, all users began reporting slowness when saving files. Which of the following is the FIRST thing the administrator should check while troubleshooting?
A private IaaS administrator is receiving reports that all newly provisioned Linux VMs are running an earlier version of the OS than they should be. The administrator reviews the automation scripts to troubleshoot the issue and determines the scripts ran successfully. Which of the following is the MOST likely cause of the issue?
A cloud administrator would like to deploy a cloud solution to its provider using automation techniques. Which of the following must be used? (Choose two.)
A systems administrator is deploying a solution that includes multiple network I/O-intensive VMs. The solution design requires that vNICs of the VMs provide low-latency, near-native performance of a physical NIC and data protection between the VMs. Which of the following would BEST satisfy these requirements?
A user reports a poor-quality remote VDI session. Which of the following should the help desk technician do FIRST to troubleshoot the issue?
A company is doing a cloud-to-cloud migration to lower costs. A systems administrator has to plan the migration accordingly.
Which of the following considerations is MOST important for a successful, future-proof, and low-cost migration?
A company is considering consolidating a number of physical machines into a virtual infrastructure that will be located at its main office. The company has the following requirements:
High-performance VMs
More secure
Has system independence
Which of the following is the BEST platform for the company to use?
A systems administrator is about to deploy a new VM to a cloud environment. Which of the following will the administrator MOST likely use to select an address for the VM?
Which of the following would be the BEST option for discussion of what individuals should do in an incident response or disaster recovery scenario?
A systems administrator has been asked to restore a VM from backup without changing the current VM's operating state. Which of the following restoration methods would BEST fit this scenario?
A company is concerned about the security of its data repository that contains customer PII. A systems administrator is asked to deploy a security control that will prevent the exfiltration of such data. Which of the following should the systems administrator implement?