A list of CVEs was identified on a web server. The systems administrator decides to close the ports and disable weak TLS ciphers. Which of the following describes this vulnerability management stage?
Which of the following storage resources provides higher availability and speed for currently used files?
Project team members enter their time sheets into a system that also displays incurred project cost. Which of the following systems can perform this task?
A highly regulated business is required to work remotely, and the risk tolerance is very low. You are tasked with providing an identity solution to the company cloud that includes the following:
secure connectivity that minimizes user login
tracks user activity and monitors for anomalous activity
requires secondary authentication
INSTRUCTIONS
Select controls and servers for the proper control points.
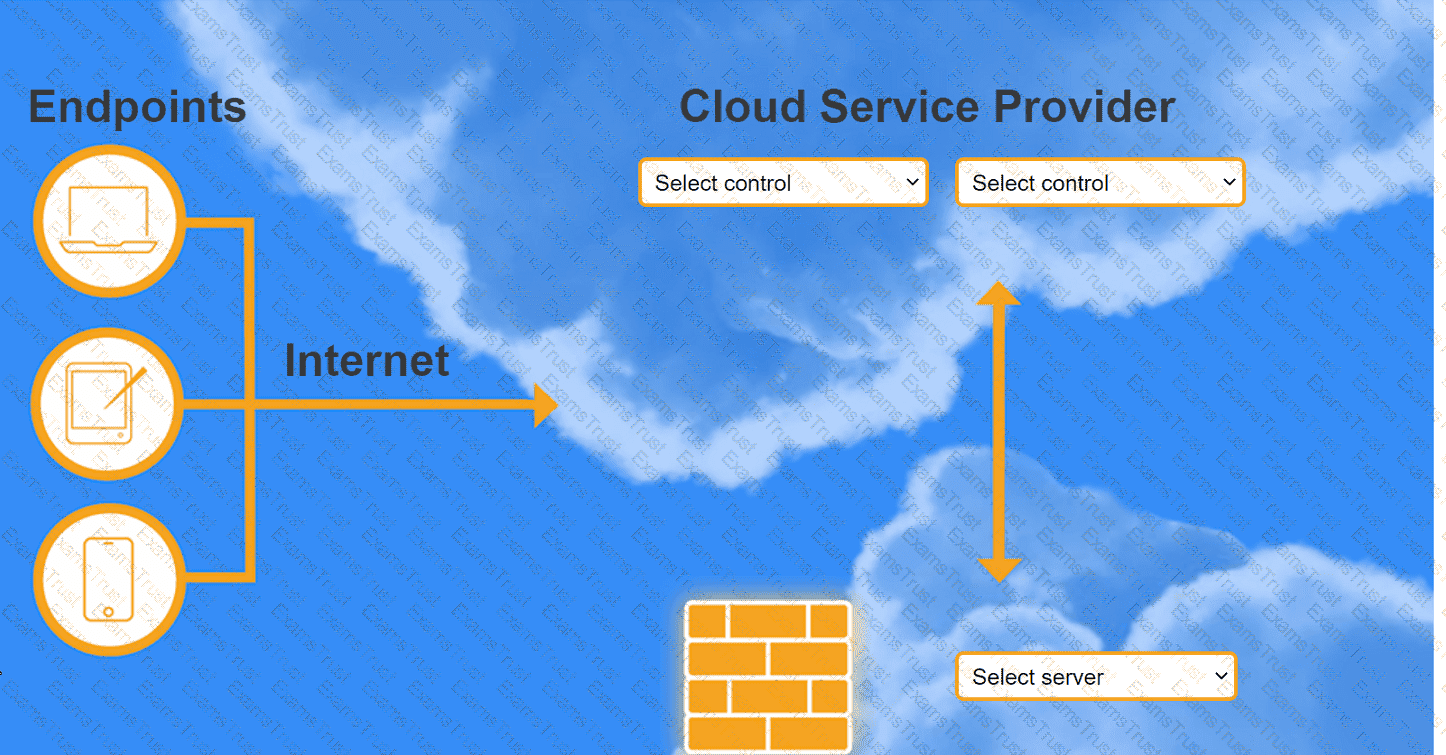
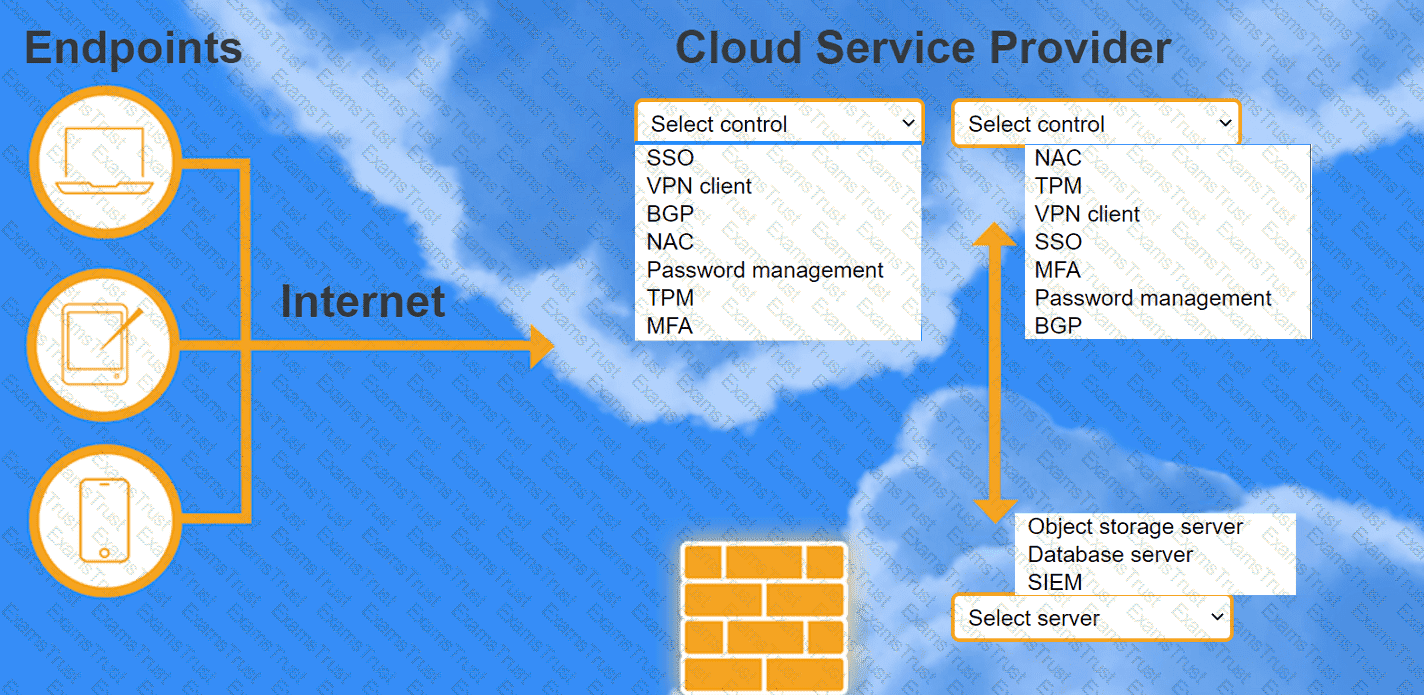
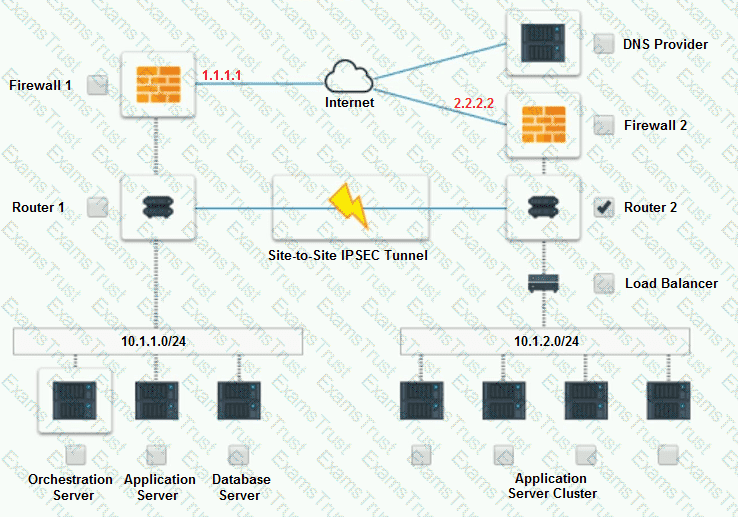
A company has decided to scale its e-commerce application from its corporate datacenter to a commercial cloud provider to meet an anticipated increase in demand during an upcoming holiday.
The majority of the application load takes place on the application server under normal conditions. For this reason, the company decides to deploy additional application servers into a commercial cloud provider using the on-premises orchestration engine that installs and configures common software and network configurations.
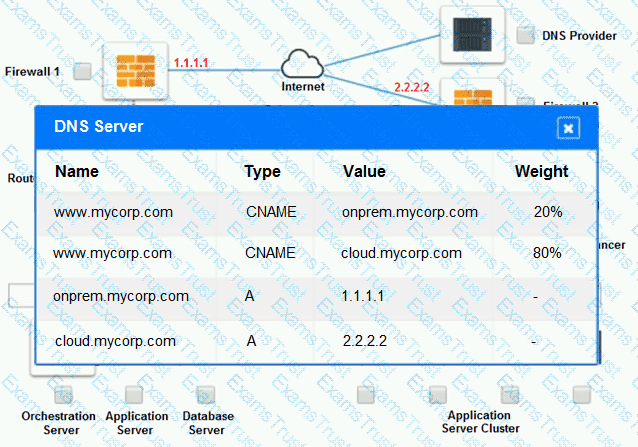
The remote computing environment is connected to the on-premises datacenter via a site-to-site IPSec tunnel. The external DNS provider has been configured to use weighted round-robin routing to load balance connections from the Internet.
During testing, the company discovers that only 20% of connections completed successfully.
INSTRUCTIONS
Review the network architecture and supporting documents and fulfill these requirements:
Part 1:
 Analyze the configuration of the following components: DNS, Firewall 1, Firewall 2, Router 1, Router 2, VPN and Orchestrator Server.
Analyze the configuration of the following components: DNS, Firewall 1, Firewall 2, Router 1, Router 2, VPN and Orchestrator Server.
 Identify the problematic device(s).
Identify the problematic device(s).
Part 2:
 Identify the correct options to provide adequate configuration for hybrid cloud architecture.
Identify the correct options to provide adequate configuration for hybrid cloud architecture.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Part 1:
Cloud Hybrid Network Diagram
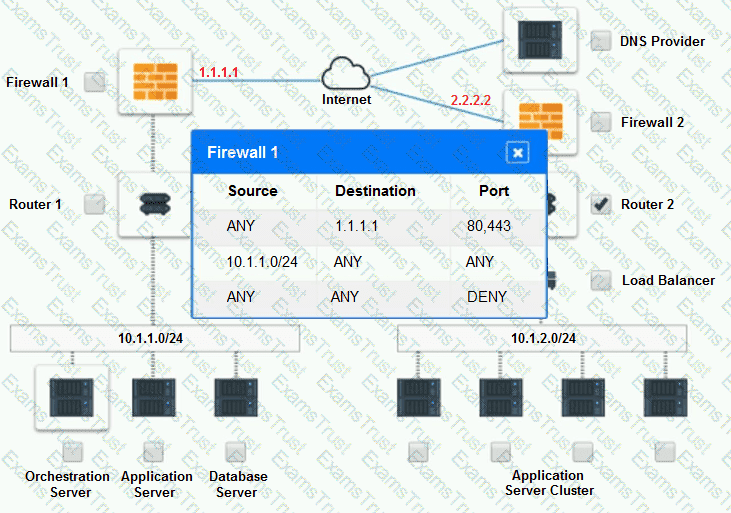
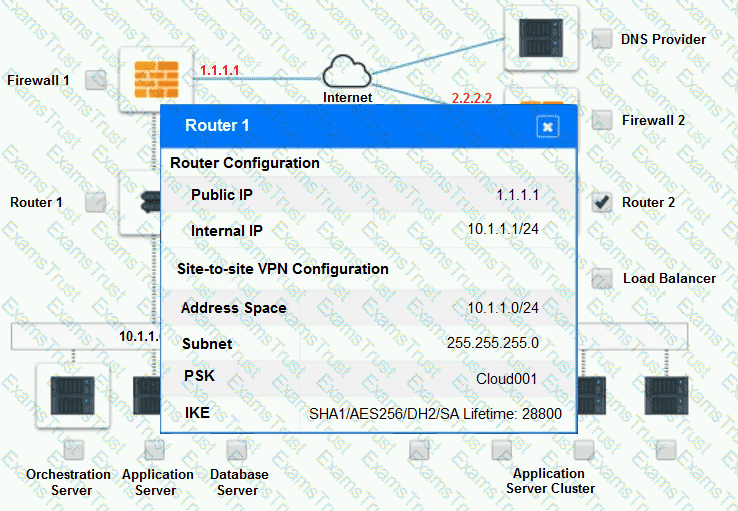
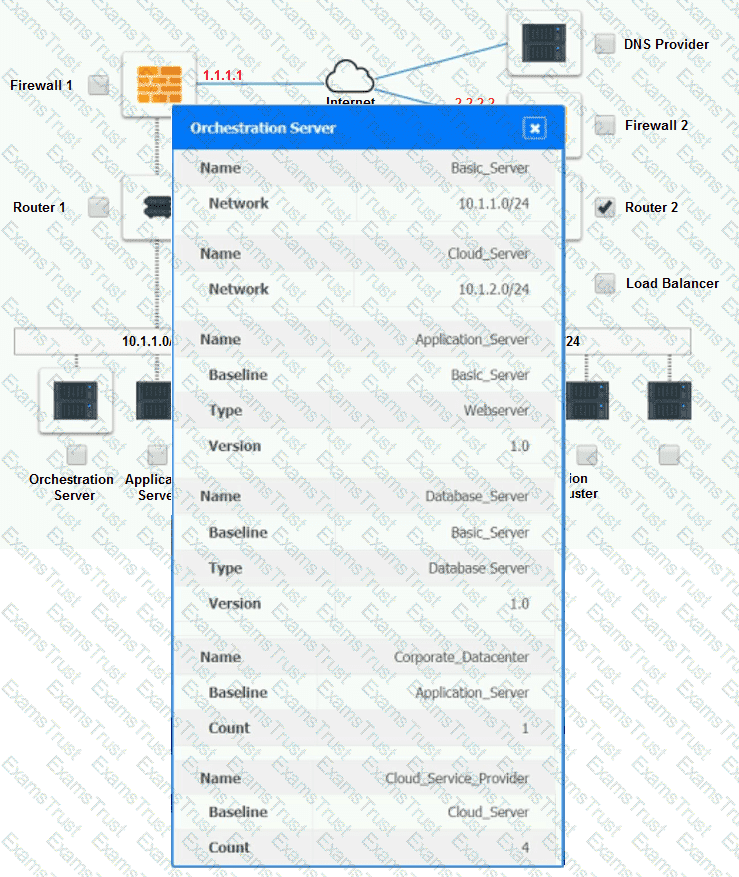
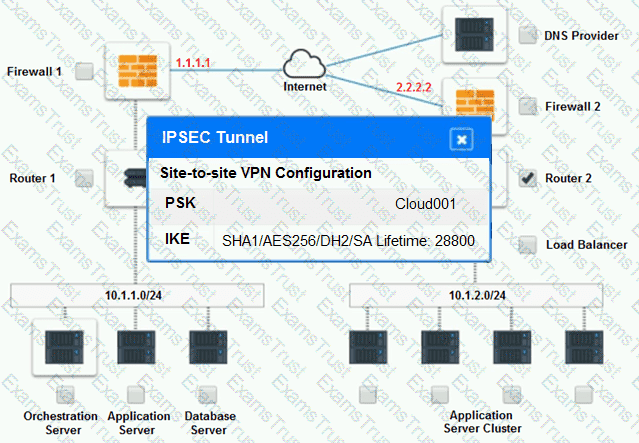
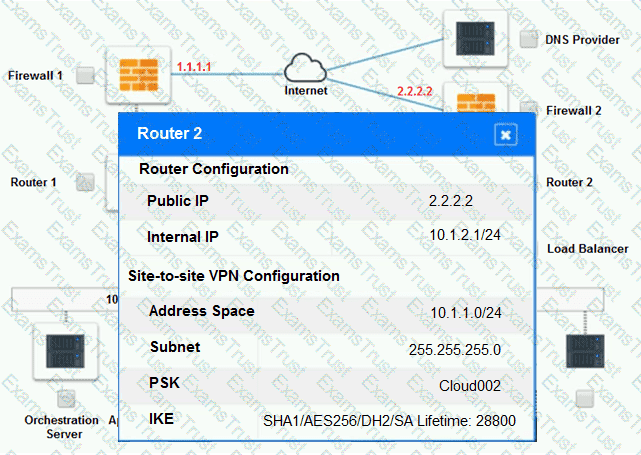
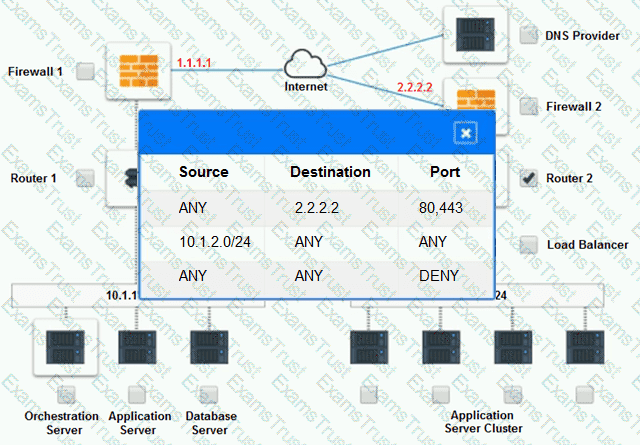
Part 2:
Only select a maximum of TWO options from the multiple choice question
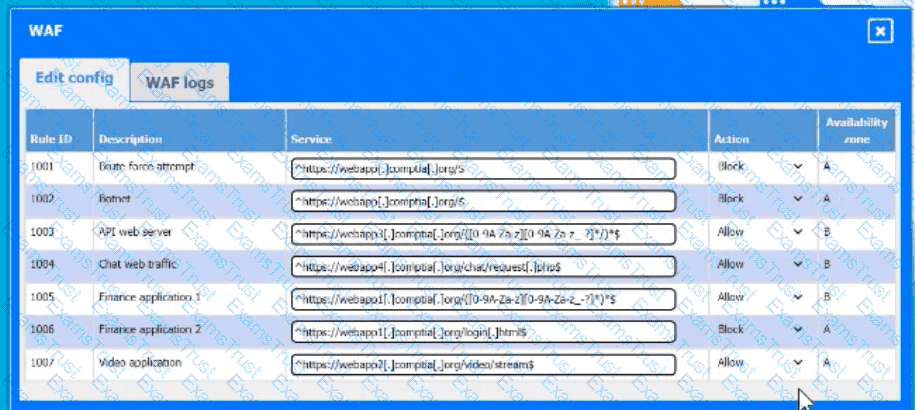
A company hosts various containerized applications for business uses. A client reports that one of its routine business applications fails to load the web-based login prompt hosted in the company cloud.
Click on each device and resource. Review the configurations, logs, and characteristics of each node in the architecture to diagnose the issue. Then, make the necessary changes to the WAF configuration to remediate the issue.
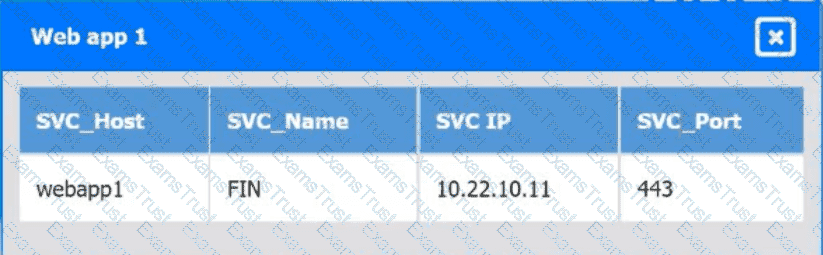
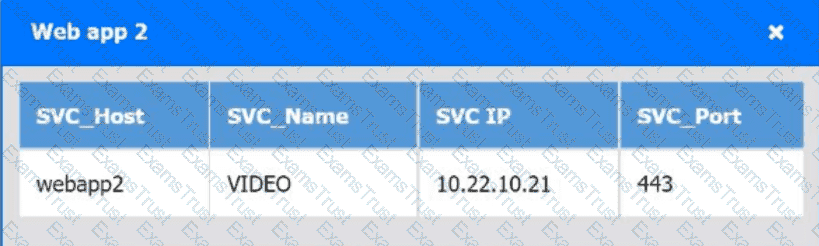
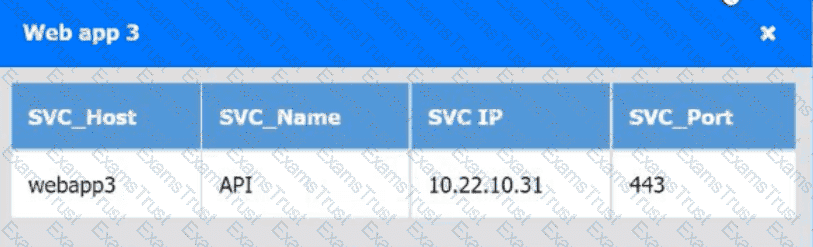
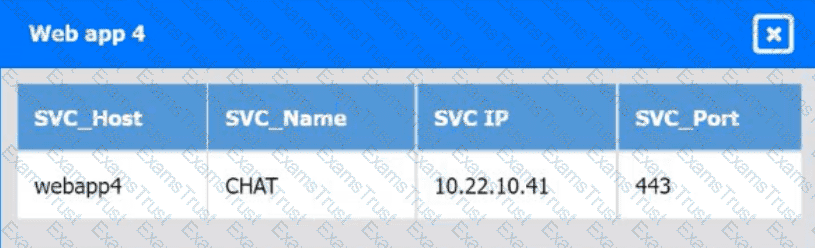
A company's engineering department is conducting a month-long test on the scalability of an in-house-developed software that requires a cluster of 100 or more servers. Which of
the following models is the best to use?
An organization wants to ensure its data is protected in the event of a natural disaster. To support this effort, the company has rented a colocation space in another part of the
country. Which of the following disaster recovery practices can be used to best protect the data?
A cloud solution needs to be replaced without interruptions. The replacement process can be completed in phases, but the cost should be kept as low as possible. Which of the
following is the best strategy to implement?
A newly configured VM fails to run application updates despite having internet access. The updates download automatically from a third-party network. Given the following output:
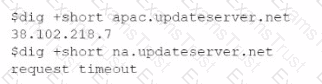
Which of the following troubleshooting steps would be best to take?
A security engineer Identifies a vulnerability m a containerized application. The vulnerability can be exploited by a privileged process to read tie content of the host's memory. The security engineer reviews the following Dockerfile to determine a solution to mitigate similar exploits:

Which of the following is the best solution to prevent similar exploits by privileged processes?
A cloud engineer is reviewing a disaster recovery plan that includes the following requirements:
• System state, files, and configurations must be backed up on a weekly basis.
• The system state, file, and configuration backups must be tested annually.
Which of the following backup methods should the engineer implement for the first week the plan is executed?
A developer is testing code that will be used to deploy a web farm in a public cloud. The main code block is a function to create a load balancer and a loop to create 1.000 web servers, as shown below:
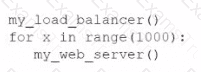
The developer runs the code against the company's cloud account and observes that the load balancer is successfully created, but only 100 web servers have been created. Which of the following should the developer do to fix this issue?
Which of the following is the most cost-effective and efficient strategy when migrating to the cloud?
A cloud administrator shortens the amount of time a backup runs. An executive in the company requires a guarantee that the backups can be restored with no data loss. Which of th€ following backup features should the administrator lest for?
A cloud administrator is building a company-standard VM image, which will be based on a public image. Which of the following should the administrator implement to secure the image?
Which of the following do developers use to keep track of changes made during software development projects?
A security team recently hired multiple interns who all need the same level of access. Which of the following controls should the security team implement to provide access to the
cloud environment with the least amount of overhead?
A company operates a website that allows customers to upload, share, and retain full ownership of their photographs. Which of the following could affect image ownership as the website usage expands globally?
A software engineer at a cybersecurity company wants to access the cloud environment. Per company policy, the cloud environment should not be directly accessible via the internet. Which of the following options best describes how the software engineer can access the cloud resources?
A cloud engineer wants to implement a disaster recovery strategy that:
. Is cost-effective.
. Reduces the amount of data loss in case of a disaster.
. Enables recovery with the least amount of downtime.
Which of the following disaster recovery strategies best describes what the cloud engineer wants to achieve?
A cloud engineer needs to integrate a new payment processor with an existing e-commerce website. Which of the following technologies is the best fit for this integration?
Which of the following is a customer be responsible for in a provider-managed database service? (Select two).
Which of the following is a difference between a SAN and a NAS?
A project stakeholder has asked the project manager to provide the performance data of a project. Which of the following should the project manager send to the stakeholder?
Which of the following integration systems would best reduce unnecessary network traffic by allowing data to travel bidirectionally and facilitating real-time results for developers who need to display critical information within applications?
A company receives files daily from a bank. The company requires that the files must be copied from the cloud storage resource to another cloud storage resource for further
processing. Which of the following methods requires the least amount of effort to achieve the task?
A systems administrator is provisioning VMs according to the following requirements:
· A VM instance needs to be present in at least two data centers.
. During replication, the application hosted on the VM tolerates a maximum latency of one second.
· When a VM is unavailable, failover must be immediate.
Which of the following replication methods will best meet these requirements?
An IT manager is migrating the production environment to the cloud but needs to keep control of the operating systems, patches, and settings of all resources. Which of the following deployment models will best meet the requirements?
A company's VMs that are created using the noncritical application tag are automatically shut down at 5:00 p.m. using a cronjob. Which of the following actions would allow a cloud engineer to stop all unresponsive instances with the least effort in case the automation fails?
Which of the following container storage types loses data after a restart?
A systems administrator needs to configure a script that will monitor whether an application is healthy and stop the VM if an unsuccessful code is returned. Which of the following
scripts should the systems administrator use to achieve this goal?
An administrator is setting up a cloud backup solution that requires the following features:
• Cost effective
• Granular recovery
• Multilocation
Which of the following backup types best meets these requirements?
A cloud engineer has provisioned a VM for a high-frequency trading application. After the VM is put into production, users report high latency in trades. The engineer checks the last six hours of VM metrics and sees the following:
• CPU utilization is between 30% to 60%.
• Networkln is between 50Kbps and 70Kbps.
• NetworkOut is between 3.000Kpbs and 5.000Kbps.
• DiskReadOps is at 30.
• DiskWriteOps is at 70
• Memory utilization is between 50% and 70%.
Which of the following steps should the engineer take next to solve the latency issue?
Which of the following application migration strategies will best suit a customer who wants to move a simple web application from an on-premises server to the cloud?
A cloud engineer is in charge of deploying a platform in an laaS public cloud. The application tracks the state using session cookies, and there are no affinity restrictions. Which of
the following will help the engineer reduce monthly expenses and allow the application to provide the service?
Which of the following technologies should be used by a person who is visually impaired to access data from the cloud?
An administrator used a script that worked in the past to create and tag five virtual machines. All of the virtual machines have been created: however, the administrator sees the following results:
{ tags: [ ] }
Which of the following is the most likely reason for this result?
A system surpasses 75% to 80% of resource consumption. Which of the following scaling approaches is the most appropriate?
A cloud engineer is designing a cloud-native, three-tier application. The engineer must adhere to the following security best practices:
• Minimal services should run on all layers of the stack.
• The solution should be vendor agnostic.
• Virealization could be used over physical hardware.
Which of the following concepts should the engineer use to design the system to best meet these requirements?
Which of the following vulnerability management concepts is best defined as the process of discovering vulnerabilities?
A bank informs an administrator that changes must be made to backups for long-term reporting purposes. Which of the following is the most important change the administrator
should make to satisfy these requirements?
Following a ransomware attack, the legal department at a company instructs the IT administrator to store the data from the affected virtual machines for a minimum of one year.
Which of the following is this an example of?
A cloud engineer is running a latency-sensitive workload that must be resilient and highly available across multiple regions. Which of the following concepts best addresses these
requirements?
Which of the following describes what CRUD is typically used for?
A retail store is rolling out a new point-of-sale solution to several locations where the staff members normally use cash registers. Which of the following activities will best assist staff members with integrating this new solution? (Select two).
Which of the following will best reduce the cost of running workloads while maintaining the same performance? (Select two).
A cloud administrator learns that a major version update. 4.6.0. is available for a business-critical application. The application is currently on version 4.5.2. with additional minor versions 3, 4, and 5 available. The administrator needs to perform the update while minimizing downtime. Which of the following should the administrator do first?
A highly scored negative risk causes a risk trigger, but the issue has not started yet. Which of the following is the next step the project team should take?
An on-premises data center is located in an earthquake-prone location. The workload consists of real-time, online transaction processing. Which ot the following data protection strategies should be used to back up on-premises data to the cloud while also being cost effective?
A cloud engineer is reviewing the following Dockerfile to deploy a Python web application:
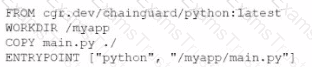
Which of the following changes should the engineer make lo the file to improve container security?
A company developed an online trading platform. The engineering team selected event-based scaling for the platform's underlying resources. The platform resources scale up with every 2,000 subscribed users. The engineering team finds out that although compute utilization is low, scaling is still occurring. Which of the following statements best explains why this is the case?
Which of the following is used to detect signals and measure physical properties, such as the temperature of the human body?
A cloud engineer needs to deploy a new version of a web application to 100 servers. In the past, new version deployments have caused outages. Which of the following deployment types should the cloud engineer implement to prevent the outages from happening this time?
A developer at a small startup company deployed some code for a new feature to its public repository. A few days later, a data breach occurred. A security team investigated the
incident and found that the database was hacked. Which of the following is the most likely cause of this breach?
Users have been reporting that a remotely hosted application is not accessible following a recent migration. However, the cloud administrator is able to access the application from
the same site as the users. Which of the following should the administrator update?
A group of cloud administrators frequently uses the same deployment template to recreate a cloud-based development environment. The administrators are unable to go back and
review the history of changes they have made to the template. Which of the following cloud resource deployment concepts should the administrator start using?
A video surveillance system records road incidents and stores the videos locally before uploading them to the cloud and deleting them from local storage. Which of the following
best describes the nature of the local storage?
A customer is migrating applications to the cloud and wants to grant authorization based on the classification levels of each system. Which of the following should the customer implement to ensure authorisation to systems is granted when the user and system classification properties match? (Select two).
A cloud solutions architect needs to design a solution that will collect a report and upload it to an object storage service every time a virtual machine is gracefully or non-gracefully
stopped. Which of the following will best satisfy this requirement?
Which of the following compute resources is the most optimal for running a single scripted task on a schedule?
A systems administrator needs to configure backups for the company's on-premises VM cluster. The storage used for backups will be constrained on free space until the company
can implement cloud backups. Which of the following backup types will save the most space, assuming the frequency of backups is kept the same?
A systems engineer is migrating a batch of 25 VMs from an on-premises compute cluster to a public cloud using the public cloud's migration agent. The migration job shows data
copies at a rate of 250Mbps. After five servers migrate, the data copies at a rate of 25Mbps. Which of the following should the engineer review first to troubleshoot?
A company that has several branches worldwide needs to facilitate full access to a specific cloud resource to a branch in Spain. Other branches will have only read access. Which of
the following is the best way to grant access to the branch in Spain?
Two CVEs are discovered on servers in the company's public cloud virtual network. The CVEs are listed as having an attack vector value of network and CVSS score of 9.0. Which
of the following actions would be the best way to mitigate the vulnerabilities?
A cloud service provider requires users to migrate to a new type of VM within three months. Which of the following is the best justification for this requirement?
During project initiation, a project manager needs to identify goals and deliverables that should be completed by the end of the project and also meet certain cost and time factors. Which of the following would best align with these needs?
Which of the following cloud deployment models is the best way to replicate a workload non-disruptively between on-premises servers and a public cloud?
A company requests that its cloud administrator provision virtual desktops for every user. Given the following information:
• One hundred users are at the company.
• A maximum of 30 users work at the same time.
• Users cannot be interrupted while working on the desktop.
Which of the following strategies will reduce costs the most?
The company's IDS has reported an anomaly. The cloud engineer remotely accesses the cloud instance, runs a command, and receives the following information:
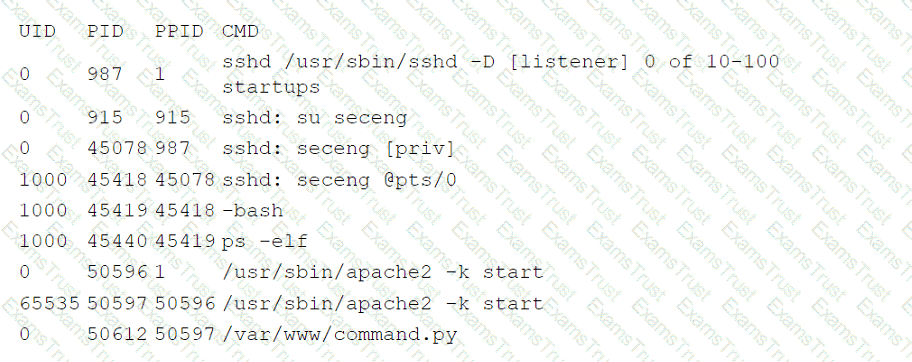
Which of the following is the most likely root cause of this anomaly?
A software engineer needs to transfer data over the internet using programmatic access while also being able to query the data. Which of the following will best help the engineer to complete this task?
A cloud developer needs to update a REST API endpoint to resolve a defect. When too many users attempt to call the API simultaneously, the following message is displayed:
Error: Request Timeout - Please Try Again Later
Which of the following concepts should the developer consider to resolve this error?
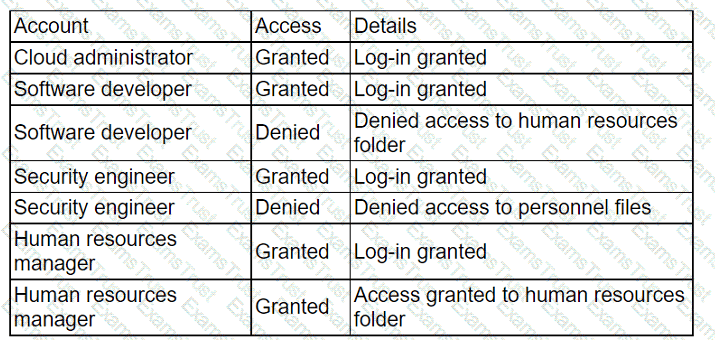
An administrator received a report that company data has been compromised. The compromise occurred on a holiday, and no one in the organization was working. While reviewing
the logs from the holiday, the administrator noted the following details:
The most appropriate action for the cloud security analyst to recommend is using CIS-hardened images. These images are pre-configured by the Center for Internet Security to provide security benchmark standards that help in mitigating vulnerabilities in publicly available container images. References: CompTIA Cloud+ Study Guide (Exam CV0-004) - Chapter on Cloud Security Posture
Which of the following accounts should the administrator disable to prevent a further breach?
A company has one cloud-based web server that is prone to downtime during maintenance. Which ot the following should the cloud engineer add to ensure high availability?
Which of the following network protocols is generally used in a NAS environment?
A cloud administrator needs to collect process-level, memory-usage tracking for the virtual machines that are part of an autoscaling group. Which of the following is the best way to
accomplish the goal by using cloud-native monitoring services?