Which of the following database instances are created by default when SQL Server is installed? (Choose two.)
A server administrator wants to analyze a database server's disk throughput. Which of the following should the administrator measure?
Which of the following is recommended in order to provide encrypted data communication pathways for information as it is transmitted over a network?
A database administrator needs to ensure continuous availability of a database in case the server fails. Which of the following should the administrator implement to ensure high availability of the database?
Which of the following is used to hide data in a database so the data can only be read by a user who has a key?
A group of developers needs access to a database in a development environment, but the database contains sensitive data. Which of the following should the database administrator do before giving the developers access to the environment?
A database administrator is updating an organization's ERD. Which of the following is thebestoption for the database administrator to use?
Which of the following cloud storage options provides users with endpoints to retrieve data via REST API?
Which of the following types of RAID, if configured with the same number and type of disks, would provide thebestwrite performance?
A database is configured to use undo management with temporary undo enabled. AnUPDATEis run on the table.
Which of the following describes where the undo is stored?
A company wants to deploy a new application that will distribute the workload to five different database instances. The database administrator needs to ensure that, for each copy of the database, users are able to read and write data that will be synchronized across all of the instances.
Which of the following should the administrator use to achieve this objective?
A database administrator needs to aggregate data from multiple tables in a way that does not impact the original tables, and then provide this information to a department. Which of the following is thebestway for the administrator to accomplish this task?
Which of the following is the correct order of the steps in the database deployment process?
A)
1. Connect
2. Install
3. Configure
4. Confirm prerequisites
5. Validate
6. Test
7. Release
B)
1. Configure
2. Install
3. Connect
4. Test
5. Confirm prerequisites
6. Validate
7. Release
C)
1. Confirm prerequisites
2. Install
3. Configure
4. Connect
5. Test
6. Validate
7. Release
D)
1. Install
2. Configure
3. Confirm prerequisites
4. Connect
5. Test
6. Validate
7. Release
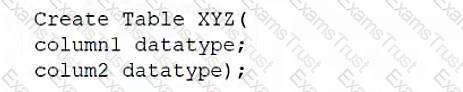
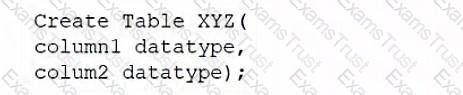
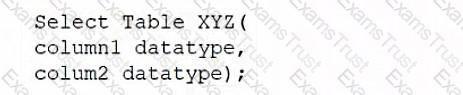
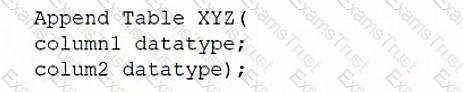
A database administrator would like to create a table named XYZ. Which of the following queries should the database administrator use to create the table?
A)
B)
C)
D)
A database administrator needs to provide access to data from two different tables to multiple group users in order to facilitate ongoing reporting. However, some columns in each table are restricted, and users should not be able to see the values in these columns.
Which of the following is thebestaction for the administrator to take?
Which of the following is thebestway to migrate a large data load from one table to another, considering total time and blocking?
A database professional is considering denormalizing a database. Which of the following documents should be used to analyze the database's structure?
Which of the following commands is part of DDL?
Which of the following concepts applies to situations that require court files to be scanned for permanent reference and original documents be stored for ten years before they can be discarded?
Which of the following firewall types allows an administrator to control traffic and make decisions based on factors such as connection information and data flow communications?
Which of the following is an attack in which an attacker hopes to profit from locking the database software?
A business analyst is using a client table and an invoice table to create a database view that shows clients who have not made purchases yet. Which of the following joins ismostappropriate for the analyst to use to create this database view?
Which of the following describes a scenario in which a database administrator would use a relational database rather than a non-relational database?
Which of the following resources is the best way to lock rows in SQL Server?