A database administrator has created a primary table and must ensure the date column in the table only accepts date values. Which of the following does the administrator need to set?
Which of the following is an example of information a company would ask employees to handle in a sensitive manner?
A technician overhears a systems administrator mention the term “IOPS”. To which of the following operating
system functions would the term BEST apply?
The computer language that is closest to machine code is:
A user is trying to set up a new wireless access point. Which of the following should the user do first?
Which of the following commands can be used to remove a database permanently?
Which of the following would be the easiest component to upgrade on a laptop that is experiencing slow performance?
Which of the following best explains the reason for password expiration?
A product advertising kiosk at a mall is set up using a thin client without a hard drive and is running a web application managed and updated through an internet connection. Which of the following application delivery methods is most likely being used for the kiosk?
When a user types a web page name in an internet browser address field, this information is translated to an IP address behind the scenes. Which of the following is being used?
Which of the following concerns does installing cross-platform software address?
Which of the following actions is the FINAL step in the standard troubleshooting methodology?
Which of the following BEST describes the physical location of the data in the database?
Which of the following is a value that uniquely identifies a database record?
Which of the following language types most likely controls the way a web page looks?
Which of the following troubleshooting steps happens before establishing a theory of probable cause?
After purchasing a flash drive, the buyer notices that the packaging had already been opened. Which of the following is this is an example of?
A programmer is modifying the code of an existing application to include an additional subroutine that is needed for a new product line. Which of the following will most likely be added to the existing code?
Which of the following is the equivalent of 1 KB?
A technician is troubleshooting a problem. The technician tests the theory and determines the theory is
confirmed. Which of the following should be the technician’s NEXT step?
After a user connects a laptop to a newly purchased printer, the user is unable to print. Which of the following is most likely causing the issue?
A user inserts a USB flash drive into a computer tor the first time and sees a message on the screen indicating the device is being set up. The message quickly changes to indicate the device is ready for use. Which of the following device configuration types most likely occurred?
A customer is looking for a device that uses tap to pay when making purchases. Which of the following technologies should the customer use?
A user wants to prevent web history logging. Which of the following features will allow the user to achieve this goal?
Which of following PC components operates only as an input device?
A technician is installing an MFD. After installation, all functions work except faxing. Which of the following interfaces is required to enable faxing functionality?
Which of the following intellectual property concepts BEST represents a legally protected slogan of a
business?
Which of the following violates password best practices?
Which of the following are the primary functions of an operating system? (Choose two.)
Which of the following is both an input and output device?
Which of the following is best used to store many integers in one container?
A systems administrator is setting up a new server using RAID technology. If one hard drive in the array fails,
the data is stored on another drive, preventing data loss. Which of the following business continuity concepts
does this explain?
Given the following pseudocode:
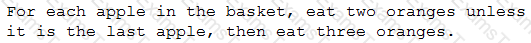
If there are seven apples in the basket, which of the following would be the number of oranges a person eats?
A global variable called “age” will be created in a program and incremented through the use of a function.
Which of the following data types should be defined with the age variable?
Which of the following computing devices would be used to provide a centralized means to distribute services to a group of clients and usually possesses a role on a LAN?
Which of the following utilities has the ability to remove drivers and scan for hardware changes?
Which of the following data types is used to implement a simple counter application?
Which of the following filesystems is compatible with the greatest number of operating systems?
Which of the following would be used to send messages using the SMTP protocol?
An online retailer experienced an outage. An investigation revealed that the server received more requests than it could handle, and customers could not log in as a result. Which of the following best describes this scenario?
An end user’s computer has been failing to open its word processing software. An IT technician successfully solves the problem. Which of the following best describes the technician’s NEXT step?
Which of the following is required for a cloud network?
A game developer is purchasing a computing device to develop a game and recognizes the game engine
software will require a device with high-end specifications that can be upgraded. Which of the following
devices would be BEST for the developer to buy?
Which of the following is an example of a query language?
Which of the following file extensions is used for a consolidated group of files?
A user is purchasing from an online retailer. The user has entered all the required information and has clicked the "Submit" button, yet the page does not refresh, and the user does not get a confirmation. Which of the following might be the causes of the issue? (Select two).
Which of the following would indicate the FASTEST processor speed?
A company’s team members have both old and new laptops. Which of the following connectors should be available in the conference room to ensure everyone can use the conference room projectors? (Choose two.)
Ann, the president of a company, has requested assistance with choosing the appropriate Internet connectivity for her home. The home is in a remote location and has no connectivity to existing infrastructure. Which of the following Internet service types should MOST likely be used?
Which of the following would MOST likely prevent malware sent as compromised file via email from infecting a person’s computer?
Which of the following best describes the process of comparing MD5 values after downloading software?
The finance department needs software that includes depreciation functionality for asset management. Which of the following types of software would best accomplish this goal?
Which of the following describes the concept of a database record?
A user is attempting to print a document to a wireless printer and receives an error stating the operation could not be completed. Which of the following should the user do to correct this issue?
An engineer has been assigned the task of establishing network connectivity in a remote area where telephone lines are readily available but other infrastructure is limited. Which of the following technologies would be the best solution?
Which of the following scripting languages is most likely to be used in a Linux command-line environment?
Which of the following is required to view videos stored on a DVD?
Which of the following best describes the technology utilized in digital wallets?
Which of the following business continuity concepts is the best example of fault tolerance?
A flatbed scanner that is connected to a laptop is used to convert photographic prints to digital images for reproduction on a color printer. Which of the following is considered the input device for this process?
When transferring a file across the network, which of the following would be the FASTEST transfer rate?
An employee’s laptop does not connect to the Internet when it is used in a coffee shop. Which of the following
is the MOST likely cause?
Which of the following is an example of an interpreted language?
A user at a company visits a weather website often during the day. The user browses to the site in the afternoon and notices that the temperature listed is from the morning and is not the current temperature. The user closes the page and tries again with the same result. Which of the following is the MOST likely cause?
A programmer creates an object to retrieve customer names from a database. Which of the following best describes the object that is retrieving the names?
The sales department needs to keep a customer list that contains names, contact information, and sales
records. This list will need to be edited by multiple people at the same time. Which of the following applications should be used to create this list?
A script is designed to save the results of user input from a survey to a database table. Which of the following database access methods is used to add the survey data to the table?
A network technician is installing an RJ11 connector inside a home tor new internet service. Which ot the following network connection types is the technician most likely using?
Which of the following is the BEST option for a developer to use when storing the months of a year and when
performance is a key consideration?
Which of the following is the slowest processing speed?
Which of the following should a technician do to fix stability issues on a workstation?
A hotel guest is using the public computer to check travel plans. Which of the following is the best approach to prevent others from seeing what the guest was doing on the computer?
Which of the following should have the HIGHEST expectation of privacy?
Which of the following BEST describes a technology that allows multiple users to create and edit reports at the
same time?
A company wants to provide encrypted remote access to its email, file, and application servers to facilitate the ability to work remotely. Which of the following would best fulfill these requirements?
After creating a database, which of the following would a developer most likely use to put data in the database?
Which of the following is an example of utilizing a personalized code for continuous personal access to a software product?
Which of the following storage types is MOST vulnerable to magnetic damage?
Which of the following would most likely be used to protect the intellectual property of printed materials?
A user wants to ensure port 3389 is open for remote desktop on a PC. Which of the following describes where the user should verify the port is open?
A company purchased a software program. The EULA states that the software can be installed on as many computers as the company wants, but only four users can be using the software at any point in time. Which of the following types of licenses is this an example of?
A technician has been asked to install a video interface that can support both high bandwidth digital video and audio on a single cable. Which of the following should the technician use?
Which of the following availability concerns is mitigated by having a business continuity site?
Joe, a user, finds out his password for a social media site has been compromised. Joe tells a friend that his email and banking accounts are probably also compromised. Which of the following has Joe MOST likely performed?
Which of the following would be considered the BEST method of securely distributing medical records?
A technician has established a plan of action. Which of the following should the technician do next?
Which of the following would be the most cost-effective method to increase availability?
Which of the following statements BEST describes binary?
An administrator grants permission for a user to access data in a database. Which of the following actions was performed?
A function is BEST used for enabling programs to:
A user logs into a laptop using a username and complex password. This is an example of:
Which of the following authorization techniques is used to assign permissions and authorize a user based on job title or function?
Which of the following application delivery mechanisms BEST describes infrastructure located in an individual organization’s datacenter?
A programmer chooses a database for a new application that needs to store information, including dates, times, names, and amounts. Which of the following database features is this an example of?
Concerned with vulnerabilities on a home network, an administrator replaces the wireless router with a recently
released new device. After configuring the new device utilizing the old SSID and key, some light switches are
no longer communicating. Which of the following is the MOST likely cause?
Which of the following are benefits of a security awareness training program9 (Select two).
A company wants its employee to use an email client that downloads and removes messages from the email
server. Which of the following protocols must be configured in the email client to facilitate this?
A software developer has created a program for the accounting department. The finance department requests the same program but requires some changes to the code to meet its needs. Which of the following should be performed?
Which of the following is the best way to prevent malicious code from executing on a laptop based on attack signatures?
Which of the following network protocols will MOST likely be used when sending and receiving Internet email?
(Select TWO.)
Which of the following database types would be best in which to place financial data?
For which of the following is a relational database management system MOST commonly used?
A database administrator wants to populate a database with large amounts of data from an external source.
Which of the following actions should be used to get the database populated?