A tester is performing an external phishing assessment on the top executives at a company. Two-factor authentication is enabled on the executives’ accounts that are in the scope of work. Which of the following should the tester do to get access to these accounts?
Which of the following OT protocols sends information in cleartext?
A company hires a penetration tester to perform an external attack surface review as part of a security engagement. The company informs the tester that the main company domain to investigate is comptia.org. Which of the following should the tester do to accomplish the assessment objective?
A penetration tester needs to help create a threat model of a custom application. Which of the following is the most likely framework the tester will use?
Which of the following elements in a lock should be aligned to a specific level to allow the key cylinder to turn?
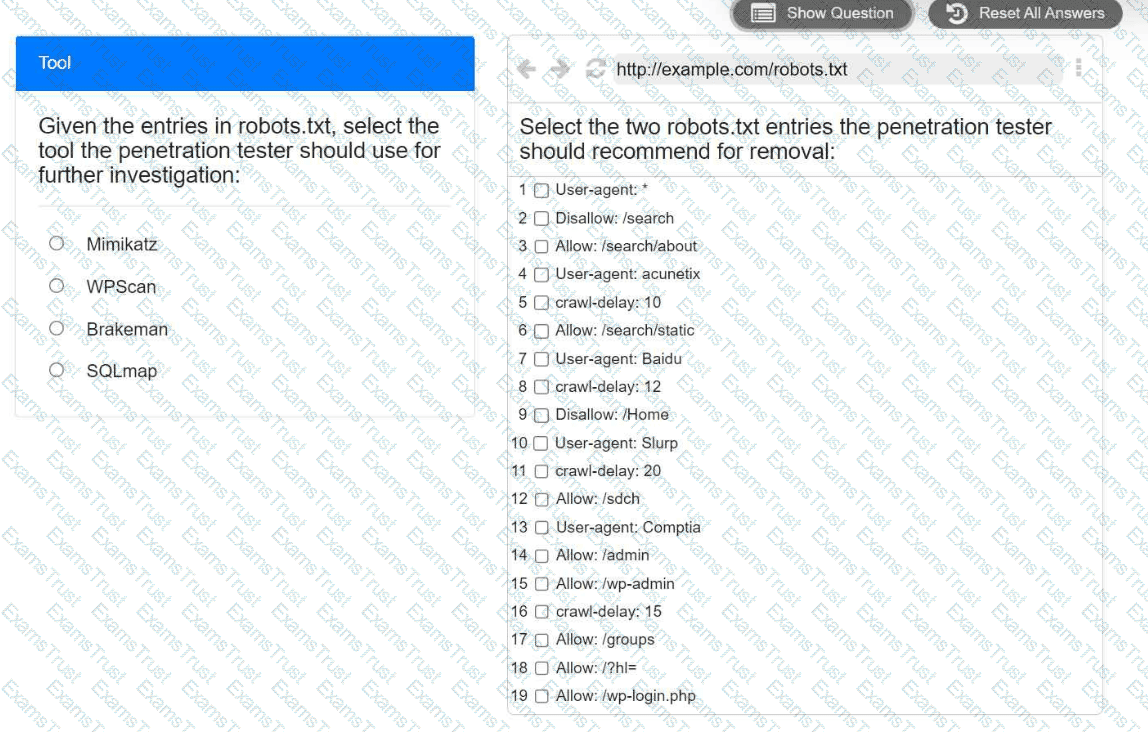
A penetration tester is performing reconnaissance for a web application assessment. Upon investigation, the tester reviews the robots.txt file for items of interest.
INSTRUCTIONS
Select the tool the penetration tester should use for further investigation.
Select the two entries in the robots.txt file that the penetration tester should recommend for removal.
A penetration tester downloads a JAR file that is used in an organization's production environment. The tester evaluates the contents of the JAR file to identify potentially vulnerable components that can be targeted for exploit. Which of the following describes the tester's activities?
A penetration tester identifies an exposed corporate directory containing first and last names and phone numbers for employees. Which of the following attack techniques would be the most effective to pursue if the penetration tester wants to compromise user accounts?
A penetration tester creates a list of target domains that require further enumeration. The tester writes the following script to perform vulnerability scanning across the domains:
line 1: #!/usr/bin/bash
line 2: DOMAINS_LIST = "/path/to/list.txt"
line 3: while read -r i; do
line 4: nikto -h $i -o scan-$i.txt &
line 5: done
The script does not work as intended. Which of the following should the tester do to fix the script?
A penetration tester is authorized to perform a DoS attack against a host on a network. Given the following input:
ip = IP("192.168.50.2")
tcp = TCP(sport=RandShort(), dport=80, flags="S")
raw = RAW(b"X"*1024)
p = ip/tcp/raw
send(p, loop=1, verbose=0)
Which of the following attack types is most likely being used in the test?
Which of the following is most important when communicating the need for vulnerability remediation to a client at the conclusion of a penetration test?
During a red-team exercise, a penetration tester obtains an employee's access badge. The tester uses the badge's information to create a duplicate for unauthorized entry. Which of the following best describes this action?
A penetration tester performs a service enumeration process and receives the following result after scanning a server using the Nmap tool:
bash
PORT STATE SERVICE
22/tcp open ssh
25/tcp filtered smtp
111/tcp open rpcbind
2049/tcp open nfs
Based on the output, which of the following services provides the best target for launching an attack?
A client warns the assessment team that an ICS application is maintained by the manufacturer. Any tampering of the host could void the enterprise support terms of use.
Which of the following techniques would be most effective to validate whether the application encrypts communications in transit?
Which of the following describes the process of determining why a vulnerability scanner is not providing results?
Which of the following is the most efficient way to exfiltrate a file containing data that could be sensitive?
During an assessment, a penetration tester exploits an SQLi vulnerability. Which of the following commands would allow the penetration tester to enumerate password hashes?
A penetration tester has discovered sensitive files on a system. Assuming exfiltration of the files is part of the scope of the test, which of the following is most likely to evade DLP systems?
A penetration tester attempts unauthorized entry to the company's server room as part of a security assessment. Which of the following is the best technique to manipulate the lock pins and open the door without the original key?
A tester runs an Nmap scan against a Windows server and receives the following results:
Nmap scan report for win_dns.local (10.0.0.5)
Host is up (0.014s latency)
Port State Service
53/tcp open domain
161/tcp open snmp
445/tcp open smb-ds
3389/tcp open rdp
Which of the following TCP ports should be prioritized for using hash-based relays?
A tester compromises a target host and then wants to maintain persistent access. Which of the following is the best way for the attacker to accomplish the objective?
A penetration tester wants to maintain access to a compromised system after a reboot. Which of the following techniques would be best for the tester to use?
A penetration testing team needs to determine whether it is possible to disrupt the wireless communications for PCs deployed in the client's offices. Which of the following techniques should the penetration tester leverage?
A penetration tester has found a web application that is running on a cloud virtual machine instance. Vulnerability scans show a potential SSRF for the same application URL path with an injectable parameter. Which of the following commands should the tester run to successfully test for secrets exposure exploitability?