An administrator is deploying a new secure web server. The only administration method that is permitted is to connect via RDP. Which of the following
ports should be allowed? (Select TWO).
A technician has moved a data drive from a new Windows server to an older Windows server. The hardware recognizes the drive, but the data is not visible to the OS. Which of the following is the most likely cause of the issue?
A technician is setting up a small office that consists of five Windows 10 computers. The technician has been asked to use a simple IP configuration without manually adding any IP addresses. Which of the following will the technician MOST likely use for the IP address assignment?
After installing a new file server, a technician notices the read times for accessing the same file are slower than the read times for other file servers.
Which of the following is the first step the technician should take?
An application server's power cord was accidentally unplugged. After plugging the cord back in the server administrator notices some transactions were not written to the disk array. Which of the following is the MOST likely cause of the issue?
An administrator needs to increase the size of an existing RAID 6 array that is running out of available space. Which of the following is the best way the administrator can perform this task?
Which of the following concepts is in use when dual power supplies are connected to different power sources?
Which of the following is the most effective way to mitigate risks associated with privacy-related data leaks when sharing with a third party?
A security analyst completed a port scan of the corporate production-server network. Results of the scan were then provided to a systems administrator for immediate action. The following table represents the requested changes:
The systems administrator created local firewall rules to block the ports indicated above. Immediately, the service desk began receiving calls about the internet being down. The systems administrator then reversed the changes, and the internet became available again. Which of the following ports on DNSSrv must remain open when the firewall rules are reapplied?
Which of the following commands would MOST likely be used to register a new service on a Windows OS?
An administrator discovers a misconfiguration that impacts all servers but can be easily corrected. The administrator has a list of affected servers and a script to correct the issue. Which of the following scripting principles should the administrator use to cycle through the list of servers to deliver the needed change?
Which of the following BEST describes a warm site?
A server administrator is instating a new server in a data center. The administrator connects the server to a midplane but does not connect any cables Which of the following types of servers is the administrator MOST likely installing?
A new application server has been configured in the cloud to provide access to all clients within the network. On-site users are able to access all resources, but remote users are reporting issues connecting to the new application. The server administrator verifies that all users are configured with the appropriate group memberships. Which of the following is MOST likely causing the issue?
A developer is creating a web application that will contain five web nodes. The developer's main goal is to ensure the application is always available to the end users. Which ofthefollowing should the developer use when designing the web application?
An administrator gave Ann modify permissions to a shared folder called DATA, which is located on the company server. Other users need read access to the files in this folder. The current configuration is as follows:
The administrator has determined Ann cannot write anything to the DATA folder using the network. Which of the following would be the best practice to set up Ann's permissions correctly, exposing only the minimum rights required?
A newly installed server is accessible to local users, but remote users are unable to connect. Which of the following is MOST likely misconfigured?
A user logs in to a Linux server and attempts to run the following command:
sudo emacs /root/file
However the user gets the following message:
User userid is not allowed to execute Temacs' on this server. Which of the following would BEST allow the user to find out which commands can be used?
A technician learns users are unable to tog in to a Linux server with known-working LDAP credentials. The technician logs in to the server with a local account and confirms the system is functional can communicate over the network, and is configured correctly However, the server log has entries regarding Kerberos errors. Which of the following is the MOST likely source of the issue?
Which of the following backup methods protects all the changes that have occurred since the last full backup?
An administrate is helping to replicate a large amount of data between two Windows servers. The administrator is unsure how much data has already been transferred. Which of the following will BEST ensure all the data is copied consistently?
An organization purchased six new 4TB drives for a server. An administrator is tasked with creating an efficient RAID given the minimum disk space requirement of 19TBs. Which of the following should the administrator choose to get the most efficient use of space?
The accounting department needs more storage and wants to retain the current data for quick read-write access. The accounting server does not have any internet drive bays available to keep both disks however the server does have USB 3 0 and eSATA ports available. Which of the following is the BEST way to accomplish the department's goals?
A technician needs to restore data from a backup. The technician has these files in the backup inventory:
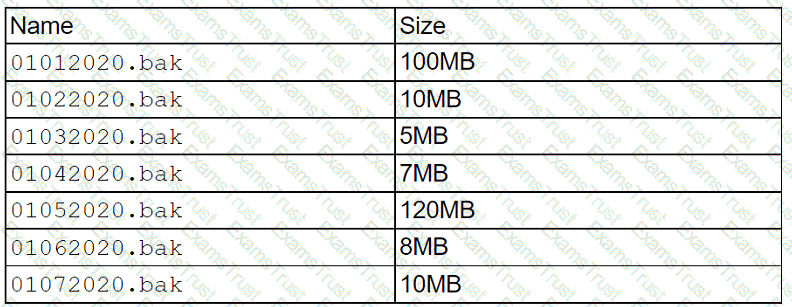
Which of the following backup types is being used if the file 01062020.bak requires another file to restore data?
Which of the following concepts refers to prioritizing a connection that had previously worked successfully?
A server administrator is setting up a new payroll application. Compliance regulations require that all financial systems logs be stored in a central location. Which of the following should the administrator configure to ensure this requirement is met?
An administrator is only able to log on to a server with a local account. The server has been successfully joined to the domain and can ping other servers by IP address. Which of the following locally defined settings is MOST likely misconfigured?
A systems administrator needs to back up changes made to a data store on a daily basis during a short time frame. The administrator wants to maximize RTO when restoring data. Which of the following backup methodologies would best fit this scenario?
A technician has moved a data drive from a new Windows server to an orderWindows server. The hardware recognizes the drive, but the data is not visible to the OS. Which of the following is the MOST Likely cause of the issue?
A systems administrator is setting up a server farm for a new company. The company has a public range of IP addresses and uses the addresses internally. Which of the following IP addresses best fits this scenario?
A server administrator is implementing an authentication policy that will require users to use a token during login. Which of the following types of authentication is the administrator implementing?
A server administrator is creating a script that will move files only if they were created before a date input by the user. Which of the following constructs will allow the script to apply this test until all available files are assessed?
In which of the following media rotation schemes are daily, weekly, and monthly backup media utilized in a first-in, first-out method?
A data center has 4U rack servers that needto be replaced using VMsbutwithout losingany data. Whichofthefollowingmethodswill MOST likelybe used to replace these servers?
A server administrator noticesthe/var/log/audit/audit.logfileon a Linux server is rotating loo frequently. The administrator would like to decrease the number of times the leg rotates without losing any of the information in the logs. Which of the following should the administrator configure?
Which of the following script types uses commands That start with sec-?
A systems administrator is trying to determine why users in the human resources department cannot access an application server. The systems administrator reviews the application logs but does not see any attempts by the users to access the application. Which of the following is preventing the users from accessing the application server?
Which of the following is used for fail over, providing access to all the services currently in use by an organization without having to physically move any servers or employees?
Which of the following cloud models is BEST described as running workloads on resources that are owned by the company and hosted in a company-owned data center, as well as on rented servers in another company's data center?
A junior administrator needs to configure a single RAID 5 volume out of four 200GB drives attached to the server using the maximum possible capacity. Upon completion, the server reports that all drives were used, and the approximate volume size is 400GB. Which of the following BEST describes the result of this configuration?
The HIDS logs on a server indicate a significant number of unauthorized access attempts via USB devices at startup. Which of the following steps should a server administrator take to BEST secure the server without limiting functionality?
A server administrator is taking advantage of all the available bandwidth of the four NICs on the server. Which of the following NIC-teaming technologies should the server administrator utilize?
A server shut down after an extended power outage. When power was restored, the system failed to start. A few seconds into booting, the Num Lock, Scroll Lock, and Caps Lock LEDs flashed several times, and the system stopped. Which of the following is the MOST likely cause of the issue?
An administrator is installing a new file server that has four drive bays available. Which of the following RAID types would provide the MOST storage as well as disk redundancy?
A server administrator has received calls regarding latency and performance issues with a file server. After reviewing all logs and server features the administrator discovers the server came with four Ethernet ports, out only one port is currently in use. Which of the following features will enable the use of all available ports using a single IP address?
Which of the following backup types resets the archive bit each time it is run?
An organization recently experienced power outages. The administrator noticed the server did not have enough time to shut down properly. After the outages, the administrator had additional batteries installed in the UPS. Which of the following best describes the solution the administrator implemented?
An administrator is configuring a new server for use as a database server. It will have two mirrored drives to hold the operating system, and there will be three drive bays remaining for storage Which of the following RAID levels will yield the BEST combination of available space and redundancy?
Which of the following ensures a secondary network path is available if the primary connection fails?
A server administrator is exporting Windows system files before patching and saving them to the following location:
\\server1\ITDept\
Which of the following is a storage protocol that the administrator is MOST likely using to save this data?
Which of the following documents would be useful when trying to restore IT infrastructure operations after a non-planned interruption?
A storage administrator is investigating an issue with a failed hard drive. A technician replaced the drive in the storage array; however, there is still an issue with the logical volume. Which of the following best describes the NEXT step that should be completed to restore the volume?
A server administrator is installing a new server that uses 40G0 network connectivity. The administrator needs to find the proper cables to connect the server to the switch. Which of the following connectors should the administrator use?
A company is building a new datacenter next to a busy parking lot. Which of the following is the BEST strategy to ensure wayward vehicle traffic does not interfere with datacenter operations?
A technician is working on a Linux server. The customer has reported that files in the home directory are missing. The /etc/ f stab file has the following entry:
nfsserver:/home /home nfs defaults 0 0
However, a df -h /home command returns the following information:
/dev/sda2 10G 1G 9G 10% /home
Which of the following should the technician attempt FIRST to resolve the issue?
A systems administrator needs to configure a new server and external storage for a new production application environment. Based on end-user specifications, the new solution needs to adhere to the following basic requirements:
1. The OS must be installed in a separate disk partition. In case of hard drive failure, it cannot be affected.
2. Application data IOPS performance is a must.
3. Data availability is a high priority, even in the case of multiple hard drive failures.
Which of the following are the BEST options to comply with the user requirements? (Choose three.)
A server is performing slowly, and users are reporting issues connecting to the application on that server. Upon investigation, the server administrator notices several unauthorizedservices running on that server that are successfully communicating to an external site. Which of the following are MOST likely causing the issue?
(Choose two.)
Hosting data in different regional locations but not moving it for long periods of time describes:
A server technician has been asked to upload a few files from the internal web server to the internal FTP server. The technician logs in to the web server using PuTTY, but the connection to the FTP server fails. However, the FTP connection from the technician’s workstation is suсcessful. To troubleshoot the issue, the technician executes the following command on both the web server and the workstation:
ping ftp.acme.local
The IP address in the command output is different on each machine. Which of the following is the MOST likely reason for the connection failure?
A technician is checking a server rack. Upon entering the room, the technician notices the tans on a particular server in the rack are running at high speeds. This is the only server in the rack that is experiencing this behavior. The ambient temperature in the room appears to be normal. Which of the following is the MOST likely reason why the fans in that server are operating at full speed?
Network connectivity to a server was lost when it was pulled from the rack during maintenance. Which of the following should the server administrator use to prevent this situation in the future?
A technician recently upgraded several pieces of firmware on a server. Ever since the technician rebooted the server, it no longer communicates with the network. Which of the following should the technician do FIRST to return the server to service as soon as possible?
A server administrator has connected a new server to the network. During testing, the administrator discovers the server is not reachable via server but can be accessed by IP address. Which of the following steps should the server administrator take NEXT? (Select TWO).
A technician is trying to determine the reason why a Linux server is not communicating on a network. The returned network configuration is as follows:
eth0: flags=4163<UP, BROADCAST,RUNNING,MULTICAST> mtu 1500
inet 127.0.0.1 network 255.255.0.0 broadcast 127.0.0.1
Which of the following BEST describes what is happening?
Which of the following allows for a connection of devices to both sides inside of a blade enclosure?
Which of the following licenses would MOST likely include vendor assistance?
A datacenter technician is attempting to troubleshoot a server that keeps crashing. The server runs normally for approximately five minutes, but then it crashes. After restoring the server to operation, the same cycle repeats. The technician confirms none of the configurations have changed, and the load on the server is steady from power-on until the crash. Which of the following will MOST likely resolve the issue?
Alter rack mounting a server, a technician must install four network cables and two power cables for the server. Which of the following is the MOST appropriate way to complete this task?
A technician is configuring a server that requires secure remote access. Which of the following ports should the technician use?
Users have noticed a server is performing below Baseline expectations. While diagnosing me server, an administrator discovers disk drive performance has degraded. The administrator checks the diagnostics on the RAID controller and sees the battery on me controller has gone bad. Which of the following is causing the poor performance on the RAID array?
Which of the following encryption methodologies would MOST likely be used to ensure encrypted data cannot be retrieved if a device is stolen?
A backup application is copying only changed files each line it runs. During a restore, however, only a single file is used. Which of the following backup methods does this describe?
A technician has been asked to check on a SAN. Upon arrival, the technician notices the red LED indicator shows a disk has failed. Which of the following should the technician do NEXT, given the disk is hot swappable?
Which of me following BEST describes a disaster recovery site with a target storage array that receives replication traffic and servers that are only powered on In the event of a disaster?
A systems administrator is investigating a server with a RAID array that will not boot into the OS. The administrator notices all the hard drives are reporting to be offline. The administrator checks the RAID controller and verifies the configuration is correct. The administrator then replaces one of the drives with a known-good drive, but it appears to be unavailable as well. Next, the administrator takes a drive out of the server and places it in a spare server, and the drive is available and functional. Which of the following is MOST likely causing the issue?
A company has implemented a requirement to encrypt all the hard drives on its servers as part of a data loss prevention strategy. Which of the following should the company also perform as a data loss prevention method?
Which of the following is a method that is used to prevent motor vehicles from getting too close to building entrances and exits?
Which of the following policies would be BEST to deter a brute-force login attack?
Which of the following relates to how much data loss a company agrees to tolerate in the event of a disaster?
Users cannot access a new server by name, but the server does respond to a ping request using its IP address. All the user workstations receive their IP information from a DHCP server. Which of the following would be the best step to perform NEXT?
A company uses a hot-site, disaster-recovery model. Which of the following types of data replication is required?
A technician has several possible solutions to a reported server issue. Which of the following BEST represents how the technician should proceed with troubleshooting?
A technician is unable to access a server’s package repository internally or externally. Which of the following are the MOST likely reasons? (Choose two.)
A system administrator has been alerted to a zero-day vulnerability that is impacting a service enabled on a server OS. Which of the following would work BEST to limit an attacker from exploiting this vulnerability?
An administrator is configuring a server to communicate with a new storage array. To do so, the administrator enters the WWPN of the new array in the server’s storage configuration. Which of the following technologies is the new connection using?
A server technician is installing a new server OS on legacy server hardware. Which of the following should the technician do FIRST to ensure the OS will work as intended?
A server technician installs a new NIC on a server and configures the NIC for IP connectivity. The technician then tests the connection using thepingcommand. Given the following partial output of thepingandipconfigcommands:
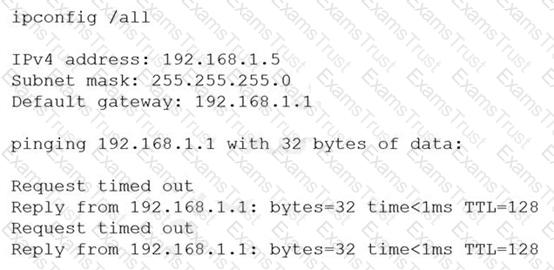
Which of the following caused the issue?
A security analyst suspects a remote server is running vulnerable network applications. The analyst does not have administrative credentials for the server. Which of the following would MOST likely help the analyst determine if the applications are running?
A systems administrator is preparing to install two servers in a single rack. The administrator is concerned that having both servers in one rack will increase the chance of power issues due to the increased load. Which of the following should the administrator implement FIRST to address the issue?
After configuring IP networking on a newly commissioned server, a server administrator installs a straight- through network cable from the patch panel to the switch. The administrator then returns to the server to test network connectivity using the ping command. The partial output of the ping and ipconfig commands are displayed below:
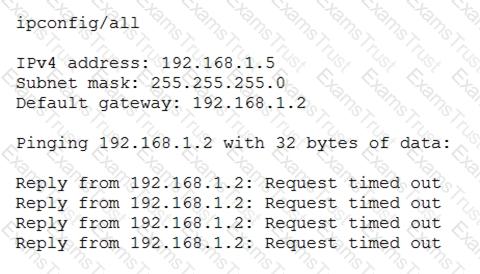
The administrator returns to the switch and notices an amber link light on the port where the server is connected. Which of the following is the MOST likely reason for the lack of network connectivity?
A company is reviewing options for its current disaster recovery plan and potential changes to it. The security team will not allow customer data to egress to non-company equipment, and the company has requested recovery in the shortest possible time. Which of the following will BEST meet these goals?
A server administrator has been creating new VMs one by one. The administrator notices the system requirements are very similar, even with different applications. Which of the following would help the administrator accomplish this task in the SHORTEST amount of time and meet the system requirements?
Which of the following is the MOST appropriate scripting language to use for a logon script for a Linux box?
Which of the following backup types only records changes to the data blocks on a virtual machine?
Which of the following describes the installation of an OS contained entirely within another OS installation?
Which of the following would be BEST to help protect an organization against social engineering?
Which of the following, if properly configured, would prevent a user from installing an OS on a server? (Select TWO).
Due to a recent application migration, a company’s current storage solution does not meet the necessary requirements tor hosting data without impacting performance when the data is accessed in real time by multiple users. Which of the following is the BEST solution for this Issue?
Which of the following will protect critical data during a natural disaster?
Which of the following would protect data in transit?
A bad actor leaves a USB drive with malicious code on it in a company's parking lot. Which of the following describes this scenario?
IDS alerts indicate abnormal traffic patterns are coming from a specific server in a data center that hosts sensitive data. Upon further investigation, the server administrator notices this server has been infected with a virus due to an exploit of a known vulnerability from its database software. Which of the following should the administrator perform after removing the virus to mitigate this issue from reoccurring and to maintain high availability? (Select three).
Which of the following supports virtualization?
A user is unable to access the database server from a workstation. All other workstations are able to access the database server. The technician issues the following command to check the workstation:
userGhost:!# nmap localhost
Nmap scan report for localhost (127.0.0.1)
Host is up (0.001 ms latency).
Not shown: 1023 closed ports
PORT STATE SERVICE
3306 open mysql
Which of the following should the technician perform next to allow access?
Which of the following symbols is used to write a text description per line within a PowerShell script?
Which of the following is a benefit of failover NIC teaming?
When a user plugs a USB drive into a workstation and attempts to transfer a file from the server, an error appears that indicates the file cannot be copied. However, the user can copy or create new files from the local workstation. Which of the following is part of this security strategy?
Which of the following benefits of virtualization is most important during a data center migration?
A server technician notices several of the servers in a data center are making loud noises. The servers are still working correctly, and no indicator lights show any issues. Which of the following should the technician do first to ensure the issues are corrected and the servers remain online?
A Linux server requires repetitive tasks for reconfiguration. Which of the following would be the best scripting language to use?
Which of the following types of asset management documentation is commonly used as a reference when processing the replacement of a faulty server component?
Which of the following authentication types defines credentials as "something you have"?
An administrator is working locally in a data center with multiple server racks. Which of the following is the best low-cost option to connect to any server while on site?
An administrator notices high traffic on a certain subnet and would like to identify the source of the traffic. Which of the following tools should the administrator utilize?
A server is only able to connect to a gigabit switch at 100Mb. Other devices are able to access the network port at full gigabit speeds, and when the server is brought to another location, it is able to connect at full gigabit speed. Which of the following should an administrator check first?
A virtual host has four NICs and eight VMs. Which of the following should the technician configure to enable uplink redundancy?
A site is considered a warm site when it:
has basic technical facilities connected to it.
has faulty air conditioning that is awaiting service.
is almost ready to take over all operations from the primary site.
Which of the following license types most commonly describes a product that incurs a yearly cost regardless of how much it is used?
A systems administrator notices the fans are running at full speed in a newly upgraded server. Which of the following should be done to address this issue?
A startup is migrating a stand-alone application that stores Pll to the cloud. Which of the following should be encrypted?
Which of the following distributes a load across all interfaces?
A technician is installing an OS on ten servers. Which of the following media installation types would allow for the fastest installation time?
A server administrator needs to implement load balancing without purchasing any new hardware or implementing any new software. Which of the following will the administrator most likely implement?
An administrator is patching a file and print server After rebooting the server, it begins acting strangely. The administrator tries to open Print Management, but it will not open Upon inspection, the spooler service has been disabled. The administrator then notices the server has services that should be enabled but are disabled. Which of the following actions should the administrator take next to resolve the issue as quickly as possible?
The management team has mandated the use of data-at-rest encryption for all data. Which of the following forms of encryption best achieves this goal?
A security administrator ran a port scanning tool against a virtual server that is hosting a secure website. A list of open ports was provided as documentation. The management team has requested that non-
essential ports be disabled on the firewall. Which of the following ports must remain open?
A systems administrator notices that a SAN is running out of space. There is no additional funding in the budget to upgrade the storage space. Which of the following will significantly reduce the storage space with the least effort? (Select two).
A server administrator needs to ensure proprietary data does not leave the company. Which of the following should the administrator implement to meet this requirement?
A technician set up a new multifunction printer. After adding the printer to the print server, the technician configured the printer on each user's machine. Several days later, users reported that they were no longer able to print, but scanning to email worked. Which of the following is most likely causing this issue?
Which of the following would a systems administrator most likely implement to encrypt data in transit for remote administration?
A systems administrator is installing Windows on an 8TB drive and would like to create a single 8TB partition on the disk. Which of the following options should the administrator use?
A systems administrator notices a newly added server cannot see any of the LUNs on the SAN. The SAN switch and the local HBA do not display any link lights. Which of the following is most likely the issue?
A server administrator notices drive C on a critical server does not have any available space, but plenty of unallocated space is left on the disk. Which of the following should the administrator perform to address the availability issue while minimizing downtime?
A server administrator is setting up a disk with enforcement policies on how much data each home share can hold. The amount of data that is redundant on the
server must also be minimized. Which of the following should the administrator perform on the server? (Select two).
An administrator is troubleshooting a server that is rebooting and crashing. The administrator notices that the server is making sounds that are louder than usual. Upon closer inspection, the administrator
discovers that the noises are coming from the front of the chassis. Which of the following is the most likely reason for this behavior?
A technician receives reports that a file server is performing slower than usual after a power failure. While investigating the issue, the technician discovers the write cache was disabled. The technician checks a server configuration document and confirms the cache was previously enabled. Which of the following events most likely caused this change?
A server technician is placing a newly configured server into a corporate environment. The server will be used by members of the accounting department, who are currently assigned by the VLAN identified below:
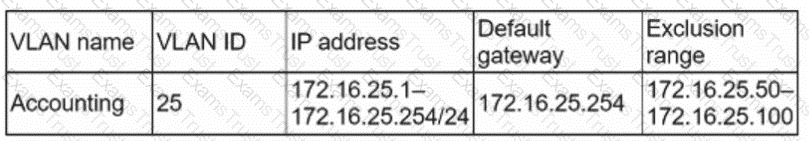
Which of the following IP address configurations should the technician assign to the new server so the members of the accounting group can access the server?
An administrator has deployed a new virtual server from a template. After confirming access to the subnet's gateway, the administrator is unable to log on with the domain credentials. Which of the following is the most likely cause of the issue?
A technician is configuring a server rack that will hold ten blade servers. Which of the following safety concerns should be observed? (Select three).
A web server that is being deployed in the perimeter network needs to be shielded from malicious traffic. Which of the following could help identify these threats?
An administrator has been troubleshooting a server issue. The administrator carefully questioned the users and examined the available logs. Using this information, the administrator was able to rule out several possible causes and develop a theory as to what the issue might be. Through further testing, the administrator's theory proved to be correct. Which of the following should be the next step to troubleshoot the issue?
A technician is configuring a server that will need to accommodate a planned network upgrade. All hosts will be changed from 10Gb copper to 25Gb fiber. Which of the following would best suit the requirements?
Under which of the following should a technician implement scripting?
Which of the following describes when a site is considered a warm site?
Multiple users have reported an issue accessing files on a specific server. Which of the following should be the first step in troubleshooting this issue?
A server located in an IDF of a paper mill reboots every other day at random times. Which of the following should the technician perform on the server first?
An administrator receives an alert that one of the virtual servers has suddenly crashed. The administrator confirms the data center does not have any power failures and then connects to the remote console of the crashed server After connecting to the server console, which of the following should the administrator complete first?