Which of the following actions must an organization take to comply with a person's request for the right to be forgotten?
An administrator was notified that a user logged in remotely after hours and copied large amounts of data to a personal device.
Which of the following best describes the user’s activity?
An administrator is installing an SSL certificate on a new system. During testing, errors indicate that the certificate is not trusted. The administrator has verified with the issuing CA and has validated the private key. Which of the following should the administrator check for next?
You are security administrator investigating a potential infection on a network.
Click on each host and firewall. Review all logs to determine which host originated the Infecton and then deny each remaining hosts clean or infected.
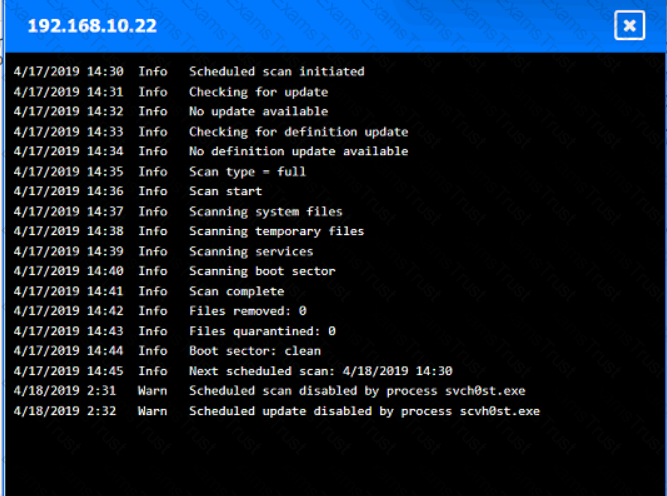
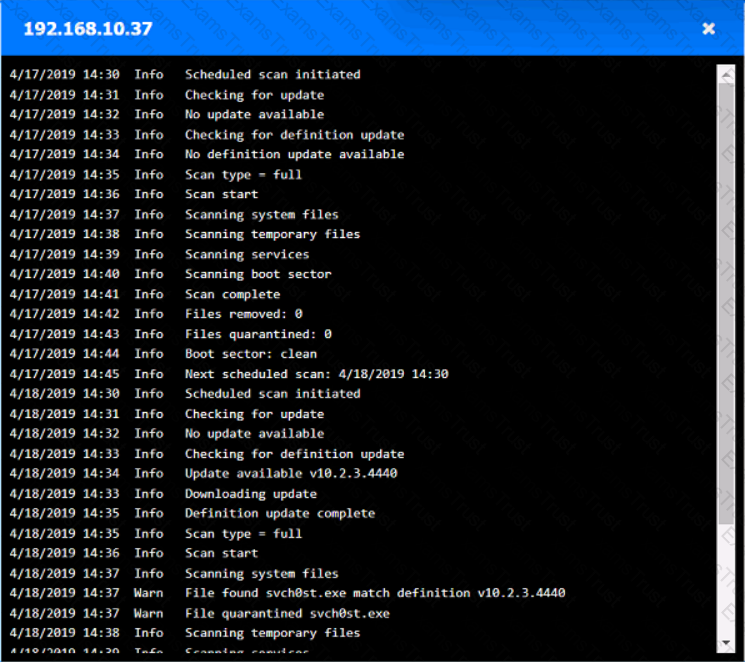

A company wants to get alerts when others are researching and doing reconnaissance on the company One approach would be to host a part of the Infrastructure online with known vulnerabilities that would appear to be company assets. Which of the following describes this approach?
The executive management team is mandating the company develop a disaster recovery plan. The cost must be kept to a minimum, and the money to fund additional internet connections is not available. Which of the following would be the best option?
Which of the following definitions best describes the concept of log co-relation?
Which of the following would be the best way to handle a critical business application that is running on a legacy server?
Which of the following strategies should an organization use to efficiently manage and analyze multiple types of logs?
After a recent ransomware attack on a company's system, an administrator reviewed the log files. Which of the following control types did the administrator use?
A systems administrator set up a perimeter firewall but continues to notice suspicious connections between internal endpoints. Which of the following should be set up in order to mitigate the threat posed by the suspicious activity?
A company purchased cyber insurance to address items listed on the risk register. Which of the following strategies does this represent?
Which of the following examples would be best mitigated by input sanitization?
A company decided to reduce the cost of its annual cyber insurance policy by removing the coverage for ransomware attacks.
Which of the following analysis elements did the company most likely use in making this decision?
A small business uses kiosks on the sales floor to display product information for customers. A security team discovers the kiosks use end-of-life operating systems. Which of the following is the security team most likely to document as a security implication of the current architecture?
While considering the organization's cloud-adoption strategy, the Chief Information Security Officer sets a goal to outsource patching of firmware, operating systems, and applications to the chosen cloud vendor. Which of the following best meets this goal?
A security analyst locates a potentially malicious video file on a server and needs to identify both the creation date and the file's creator. Which of the following actions would most likely give the security analyst the information required?
Which of the following is the most relevant reason a DPO would develop a data inventory?
A company is currently utilizing usernames and passwords, and it wants to integrate an MFA method that is seamless, can Integrate easily into a user's workflow, and can utilize employee-owned devices. Which of the following will meet these requirements?
Which of the following is used to protect a computer from viruses, malware, and Trojans being installed and moving laterally across the network?
A client asked a security company to provide a document outlining the project, the cost, and the completion time frame. Which of the following documents should the company provide to the client?
Which of the following is prevented by proper data sanitization?
A company wants to reduce the time and expense associated with code deployment. Which of the following technologies should the company utilize?
An organization is looking to optimize its environment and reduce the number of patches necessary for operating systems. Which of the following will best help to achieve this objective?
A company with a high-availability website is looking to harden its controls at any cost. The company wants to ensure that the site is secure by finding any possible issues. Which of the following would most likely achieve this goal?
An IT administrator needs to ensure data retention standards are implemented on an enterprise application. Which of the Mowing describes the administrator's role?
A company is utilizing an offshore team to help support the finance department. The company wants to keep the data secure by keeping it on a company device but does not want to provide equipment to the offshore team. Which of the following should the company implement to meet this requirement?
An organization is adopting cloud services at a rapid pace and now has multiple SaaS applications in use. Each application has a separate log-in. so the security team wants to reduce the number of credentials each employee must maintain. Which of the following is the first step the security team should take?
An organization is developing a security program that conveys the responsibilities associated with the general operation of systems and software within the organization. Which of the following documents would most likely communicate these expectations?
Security controls in a data center are being reviewed to ensure data is properly protected and that human life considerations are included. Which of the following best describes how the controls should be set up?
Which of the following activities is included in the post-incident review phase?
A Chief Information Security Officer (CISO) wants to explicitly raise awareness about the increase of ransomware-as-a-service in a report to the management team. Which of the following best describes the threat actor in the CISO's report?
An employee clicked a link in an email from a payment website that asked the employee to update contact information. The employee entered the log-in information but received a “page not found” error message. Which of the following types of social engineering attacks occurred?
An administrator assists the legal and compliance team with ensuring information about customer transactions is archived for the proper time period. Which of the following data policies is the administrator carrying out?
A security engineer configured a remote access VPN. The remote access VPN allows end users to connect to the network by using an agent that is installed on the endpoint, which establishes an encrypted tunnel. Which of the following protocols did the engineer most likely implement?
Which of the following is a common data removal option for companies that want to wipe sensitive data from hard drives in a repeatable manner but allow the hard drives to be reused?
Which of the following are cases in which an engineer should recommend the decommissioning of a network device? (Select two).
Which of the following activities should a systems administrator perform to quarantine a potentially infected system?
An unexpected and out-of-character email message from a Chief Executive Officer’s corporate account asked an employee to provide financial information and to change the recipient's contact number. Which of the following attack vectors is most likely being used?
A company is concerned about weather events causing damage to the server room and downtime. Which of the following should the company consider?
Which of the following most accurately describes the order in which a security engineer should implement secure baselines?
Users at a company are reporting they are unable to access the URL for a new retail website because it is flagged as gambling and is being blocked.
Which of the following changes would allow users to access the site?
Which of the following should a security administrator adhere to when setting up a new set of firewall rules?
Which of the following is the best way to consistently determine on a daily basis whether security settings on servers have been modified?
Which of the following is required for an organization to properly manage its restore process in the event of system failure?
An administrator needs to perform server hardening before deployment. Which of the following steps should the administrator take? (Select two).
A systems administrator is changing the password policy within an enterprise environment and wants this update implemented on all systems as quickly as possible. Which of the following operating system security measures will the administrator most likely use?
A security team is setting up a new environment for hosting the organization's on-premises software application as a cloud-based service. Which of the following should the team ensure is in place in order for the organization to follow security best practices?
Which of the following methods would most likely be used to identify legacy systems?
A security engineer is implementing FDE for all laptops in an organization. Which of the following are the most important for the engineer to consider as part of the planning process? (Select two).
A security analyst learns that an attack vector, used as part of a recent incident, was a well-known IoT device exploit. The analyst needs to review logs to identify the time of the initial exploit. Which of the following logs should the analyst review first?
An organization is struggling with scaling issues on its VPN concentrator and internet circuit due to remote work. The organization is looking for a software solution that will allow it to reduce traffic on the VPN and internet circuit, while still providing encrypted tunnel access to the data center and monitoring of remote employee internet traffic. Which of the following will help achieve these objectives?
Which of the following is the primary purpose of a service that tracks log-ins and time spent using the service?
A security analyst receives alerts about an internal system sending a large amount of unusual DNS queries to systems on the internet over short periods of time during non-business hours. Which of the following is most likely occurring?
A company is developing a critical system for the government and storing project information on a fileshare. Which of the following describes how this data will most likely be classified? (Select two).
A cybersecurity incident response team at a large company receives notification that malware is present on several corporate desktops No known Indicators of compromise have been found on the network. Which of the following should the team do first to secure the environment?
Which of the following vulnerabilities is associated with installing software outside of a manufacturer’s approved software repository?
Which of the following best explains a concern with OS-based vulnerabilities?
Which of the following teams combines both offensive and defensive testing techniques to protect an organization's critical systems?
Which of the following is a reason why a forensic specialist would create a plan to preserve data after an modem and prioritize the sequence for performing forensic analysis?
During a recent company safety stand-down, the cyber-awareness team gave a presentation on the importance of cyber hygiene. One topic the team covered was best practices for printing centers. Which of the following describes an attack method that relates to printing centers?
A security analyst developed a script to automate a trivial and repeatable task. Which of the following best describes the benefits of ensuring other team members understand how the script works?
An IT manager is putting together a documented plan describing how the organization will keep operating in the event of a global incident. Which of the following plans is the IT manager creating?
A security operations center determines that the malicious activity detected on a server is normal. Which of the following activities describes the act of ignoring detected activity in the future?
Which of the following is the best method to reduce the attack surface of an enterprise network?
Which of the following should a systems administrator use to ensure an easy deployment of resources within the cloud provider?
A company is expanding its threat surface program and allowing individuals to security test the company’s internet-facing application. The company will compensate researchers based on the vulnerabilities discovered. Which of the following best describes the program the company is setting up?
An organization issued new laptops to all employees and wants to provide web filtering both in and out of the office without configuring additional access to the network. Which of the following types of web filtering should a systems administrator configure?
A company is discarding a classified storage array and hires an outside vendor to complete the disposal. Which of the following should the company request from the vendor?
While conducting a business continuity tabletop exercise, the security team becomes concerned by potential impacts if a generator fails during failover. Which of the following is the team most likely to consider in regard to risk management activities?
A company is redesigning its infrastructure and wants to reduce the number of physical servers in use. Which of the following architectures is best suited for this goal?
A company's marketing department collects, modifies, and stores sensitive customer data. The infrastructure team is responsible for securing the data while in transit and at rest. Which of the following data roles describes the customer?
Which of the following is the first step to secure a newly deployed server?
Which of the following best represents an application that does not have an on-premises requirement and is accessible from anywhere?
An enterprise security team is researching a new security architecture to better protect the company's networks and applications against the latest cyberthreats. The company has a fully remoteworkforce. The solution should be highly redundant and enable users to connect to a VPN with an integrated, software-based firewall. Which of the following solutions meets these requirements?
Which of the following allows for the attribution of messages to individuals?
Which of the following should be used to ensure an attacker is unable to read the contents of a mobile device's drive if the device is lost?
The security operations center is researching an event concerning a suspicious IP address A security analyst looks at the following event logs and discovers that a significant portion of the user accounts have experienced faded log-In attempts when authenticating from the same IP address:
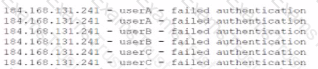
Which of the following most likely describes attack that took place?
Which of the following automation use cases would best enhance the security posture of an organization by rapidly updating permissions when employees leave a company?
Which of the following practices would be best to prevent an insider from introducing malicious code into a company's development process?
A security analyst is investigating an application server and discovers that software on the server is behaving abnormally. The software normally runs batch jobs locally and does not generate traffic, but the process is now generating outbound traffic over random high ports. Which of the following vulnerabilities has likely been exploited in this software?
Which of the following is an example of memory injection?
An organization plans to expand its operations internationally and needs to keep data at the new location secure. The organization wants to use the most secure architecture model possible. Which of the following models offers the highest level of security?
A security analyst is assessing several company firewalls. Which of the following cools would The analyst most likely use to generate custom packets to use during the assessment?
During a SQL update of a database, a temporary field that was created was replaced by an attacker in order to allow access to the system. Which of the following best describes this type of vulnerability?
Which of the following Is a common, passive reconnaissance technique employed by penetration testers in the early phases of an engagement?
Which of the following best describes the concept of information being stored outside of its country of origin while still being subject to the laws and requirements of the country of origin?
A security analyst scans a company's public network and discovers a host is running a remote desktop that can be used to access the production network. Which of the following changes should the security analyst recommend?
An employee receives a text message from an unknown number claiming to be the company's Chief Executive Officer and asking the employee to purchase several gift cards. Which of the following types of attacks does this describe?
Company A jointly develops a product with Company B, which is located in a different country. Company A finds out that their intellectual property is being shared with unauthorized companies. Which of the following has been breached?
Which of the following security concepts is the best reason for permissions on a human resources fileshare to follow the principle of least privilege?
A malicious update was distributed to a common software platform and disabled services at many organizations. Which of the following best describes this type of vulnerability?
A security team created a document that details the order in which critical systems should be through back online after a major outage. Which of the following documents did the team create?
Which of the following types of vulnerabilities is primarily caused by improper use and management of cryptographic certificates?
Which of the following security concepts is accomplished with the installation of a RADIUS server?
A human resources (HR) employee working from home leaves their company laptop open on the kitchen table. A family member walking through the kitchen reads an email from the Chief Financial Officer addressed to the HR department. The email contains information referencing company layoffs. The family member posts the content of the email to social media. Which of the following policies will the HR employee most likely need to review after this incident?
A systems administrator creates a script that validates OS version, patch levels, and installed applications when users log in. Which of the following examples best describes the purpose of this script?
A security professional discovers a folder containing an employee's personal information on the enterprise's shared drive. Which of the following best describes the data type the securityprofessional should use to identify organizational policies and standards concerning the storage of employees' personal information?
Which of the following should an organization focus on the most when making decisions about vulnerability prioritization?
An organization would like to calculate the time needed to resolve a hardware issue with a server. Which of the following risk management processes describes this example?
A spoofed identity was detected for a digital certificate. Which of the following are the type of unidentified key and the certificate mat could be in use on the company domain?
An organization recently updated its security policy to include the following statement:
Regular expressions are included in source code to remove special characters such as $, |, ;. &, `, and ? from variables set by forms in a web application.
Which of the following best explains the security technique the organization adopted by making this addition to the policy?
Which of the following would be the best solution to deploy a low-cost standby site that includes hardware and internet access?
An engineer moved to another team and is unable to access the new team's shared folders while still being able to access the shared folders from the former team. After opening a ticket, the engineer discovers that the account was never moved to the new group. Which of the following access controls is most likely causing the lack of access? 1
A Chief Information Security Officer wants to monitor the company's servers for SQLi attacks and allow for comprehensive investigations if an attack occurs. The company uses SSL decryption to allow traffic monitoring. Which of the following strategies would best accomplish this goal?
Which of the following explains how to determine the global regulations that data is subject to regardless of the country where the data is stored?
Which of the following is the most likely outcome if a large bank fails an internal PCI DSS compliance assessment?
An administrator discovers that some files on a database server were recently encrypted. The administrator sees from the security logs that the data was last accessed by a domain user. Which of the following best describes the type of attack that occurred?
Which of the following is a risk of conducting a vulnerability assessment?
Which of the following is a compensating control for providing user access to a high-risk website?
Which of the following organizational documents is most often used to establish and communicate expectations associated with integrity and ethical behavior within an organization?
A systems administrator is concerned users are accessing emails through a duplicate site that is not run by the company. Which of the following is used in this scenario?
A company implemented an MDM policy 10 mitigate risks after repealed instances of employees losing company-provided mobile phones. In several cases. The lost phones were used maliciously to perform social engineering attacks against other employees. Which of the following MDM features should be configured to best address this issue? (Select two).
Which of the following is the most effective way to protect an application server running software that is no longer supported from network threats?
Which of the following has been implemented when a host-based firewall on a legacy Linux system allows connections from only specific internal IP addresses?
Which of the following describes the procedures a penetration tester must follow while conducting a test?
A systems administrator is looking for a low-cost application-hosting solution that is cloud-based. Which of the following meets these requirements?
A visitor plugs a laptop into a network jack in the lobby and is able to connect to the company's network. Which of the following should be configured on the existing network infrastructure to best prevent this activity?
A company is working with a vendor to perform a penetration test Which of the following includes an estimate about the number of hours required to complete the engagement?
Which of the following is the most likely to be used to document risks, responsible parties, and thresholds?
An organization wants to limit potential impact to its log-in database in the event of a breach. Which of the following options is the security team most likely to recommend?
After failing an audit twice, an organization has been ordered by a government regulatory agency to pay fines. Which of the following caused this action?
An organization is required to provide assurance that its controls are properly designed and operating effectively. Which of the following reports will best achieve the objective?
A security analyst is evaluating a SaaS application that the human resources department would like to implement. The analyst requests a SOC 2 report from the SaaS vendor. Which of the following processes is the analyst most likely conducting?
Which of the following should be used to aggregate log data in order to create alerts and detect anomalous activity?
An accounting clerk sent money to an attacker's bank account after receiving fraudulent instructions over the phone to use a new account. Which of the following would most likely prevent this activity in the future?
An administrator finds that all user workstations and servers are displaying a message that is associated with files containing an extension of .ryk. Which of the following types of infections is present on the systems?
Which of the following explains why an attacker cannot easily decrypt passwords using a rainbow table attack?
Which of the following threat actors is the most likely to use large financial resources to attack critical systems located in other countries?
An employee fell for a phishing scam, which allowed an attacker to gain access to a company PC. The attacker scraped the PC’s memory to find other credentials. Without cracking these credentials, the attacker used them to move laterally through the corporate network. Which of the following describes this type of attack?
Which of the following types of identification methods can be performed on a deployed application during runtime?
A company is adding a clause to its AUP that states employees are not allowed to modify the operating system on mobile devices. Which of the following vulnerabilities is the organization addressing?
Which of the following would be most useful in determining whether the long-term cost to transfer a risk is less than the impact of the risk?
A security analyst has determined that a security breach would have a financial impact of $15,000 and is expected to occur twice within a three-year period. Which of the following is the ALE for this risk?
A malicious insider from the marketing team alters records and transfers company funds to a personal account. Which of the following methods would be the best way to secure company records in the future?
Which of the following is a benefit of vendor diversity?
The Cruel Information Security Officer (CISO) asks a security analyst to install an OS update to a production VM that has a 99% uptime SLA. The CISO tells me analyst the installation must be done as quickly as possible. Which of the following courses of action should the security analyst take first?
A systems administrator works for a local hospital and needs to ensure patient data is protected and secure. Which of the following data classifications should be used to secure patient data?
While investigating a possible incident, a security analyst discovers the following log entries:
67.118.34.157 ----- [28/Jul/2022:10:26:59 -0300] "GET /query.php?q-wireless%20headphones / HTTP/1.0" 200 12737
132.18.222.103 ----[28/Jul/2022:10:27:10 -0300] "GET /query.php?q=123 INSERT INTO users VALUES('temp', 'pass123')# / HTTP/1.0" 200 935
12.45.101.121 ----- [28/Jul/2022:10:27:22 -0300] "GET /query.php?q=mp3%20players I HTTP/1.0" 200 14650
Which of the following should the analyst do first?
Which of the following is the stage in an investigation when forensic images are obtained?
A systems administrator is redesigning now devices will perform network authentication. The following requirements need to be met:
• An existing Internal certificate must be used.
• Wired and wireless networks must be supported
• Any unapproved device should be Isolated in a quarantine subnet
• Approved devices should be updated before accessing resources
Which of the following would best meet the requirements?
An attacker used XSS to compromise a web server. Which of the following solutions could have been used to prevent this attack?
Which of the following should an internal auditor check for first when conducting an audit of the organization's risk management program?
Which of the following can a security director use to prioritize vulnerability patching within a company's IT environment?