You want to create a new onboarding rule.
Where do you accomplish this?
What does the minvalidity parameter on a platform policy determine?
What are the mandatory fields when onboarding from Pending Accounts? (Choose two.)
You need to enable the PSM for all platforms.
Where do you perform this task?
Secure Connect provides the following. Choose all that apply.
Which file must be edited on the Vault to configure it to send data to PTA?
What is the purpose of the PrivateArk Server service?
Where can reconcile and/or logon accounts be linked to an account? (Choose two.)
Platform settings are applied to _________.
Which built-in report from the reports page in PVWA displays the number of days until a password is due to expire?
A Logon Account can be specified in the Master Policy.
If a user is a member of more than one group that has authorizations on a safe, by default that user is granted________.
Where can you check that the LDAP binding is using TCP/636?
What is the chief benefit of PSM?
A Simple Mail Transfer Protocol (SMTP) integration is critical for monitoring Vault activity and facilitating workflow processes, such as Dual Control.
Which Master Policy Setting must be active in order to have an account checked-out by one user for a pre-determined amount of time?
You want to build a connector that connects to a website through the Web applications for PSM framework.
Which default connector do you duplicate and modify?
To change the safe where recordings are kept for a specific platform, which setting must you update in the platform configuration?
When running a “Privileged Accounts Inventory” Report through the Reports page in PVWA on a specific safe, which permission/s are required on that safe to show complete account inventory information?
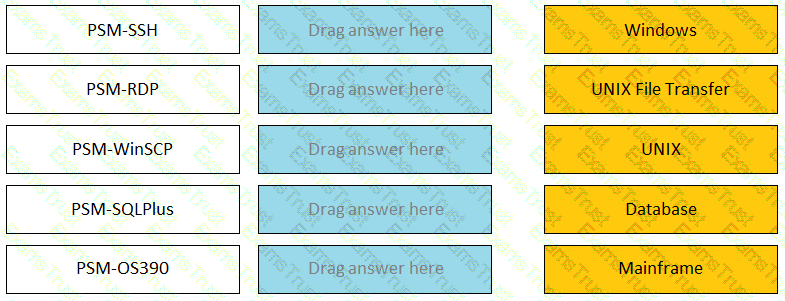
Match the connection component to the corresponding OS/Function.
Which report provides a list of account stored in the vault.
How much disk space do you need on the server for a PAReplicate?
If PTA is integrated with a supported SIEM solution, which detection becomes available?
What is the maximum number of levels of authorization you can set up in Dual Control?
Which report shows the accounts that are accessible to each user?
Which user(s) can access all passwords in the Vault?
When a group is granted the 'Authorize Account Requests' permission on a safe Dual Control requests must be approved by
What can you do to ensure each component server is operational?
Users are unable to launch Web Type Connection components from the PSM server. Your manager asked you to open the case with CyberArk Support.
Which logs will help the CyberArk Support Team debug the issue? (Choose three.)
The Privileged Access Management solution provides an out-of-the-box target platform to manage SSH keys, called UNIX Via SSH Keys.
How are these keys managed?
During a High Availability node switch you notice an error and the Cluster Vault Manager Utility fails back to the original node.
Which log files should you check to investigate the cause of the issue? (Choose three.)
Which of the following logs contains information about errors related to PTA?
Before failing back to the production infrastructure after a DR exercise, what must you do to maintain audit history during the DR event?
Which of the following files must be created or configured m order to run Password Upload Utility? Select all that apply.
How much disk space do you need on a server to run a full replication with PAReplicate?
The password upload utility must run from the CPM server
tsparm.ini is the main configuration file for the Vault.
When a DR Vault Server becomes an active vault, it will automatically revert back to DR mode once the Primary Vault comes back online.
Which command generates a full backup of the Vault?
Which keys are required to be present in order to start the PrivateArk Server service?
Which usage can be added as a service account platform?
You have associated a logon account to one your UNIX cool accounts in the vault. When attempting to [b]change [/b] the root account’s password the CPM will…..
Users can be resulted to using certain CyberArk interfaces (e.g.PVWA or PACLI).
The Vault administrator can change the Vault license by uploading the new license to the system Safe.
VAULT authorizations may be granted to_____.
Which change could CyberArk make to the REST API that could cause existing scripts to fail?
Which dependent accounts does the CPM support out-of-the-box? (Choose three.)
You are configuring a Vault HA cluster.
Which file should you check to confirm the correct drives have been assigned for the location of the Quorum and Safes data disks?
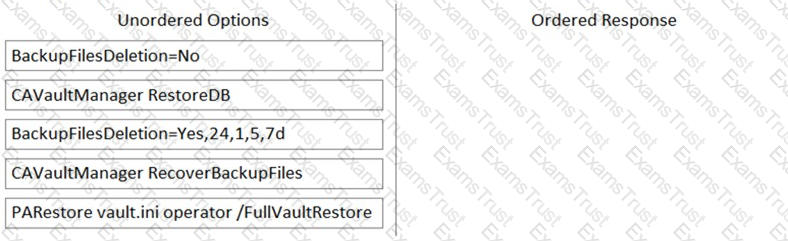
Arrange the steps to restore a Vault using PARestore for a Backup in the correct sequence.
You are configuring CyberArk to use HTML5 gateways exclusively for PSM connections.
In the PVWA, where do you set DefaultConnectionMethod to HTML5?
Which one the following reports is NOT generated by using the PVWA?
In a default CyberArk installation, which group must a user be a member of to view the “reports” page in PVWA?
Which Cyber Are components or products can be used to discover Windows Services or Scheduled Tasks that use privileged accounts? Select all that apply.
By default, members of which built-in groups will be able to view and configure Automatic Remediation and Session Analysis and Response in the PVWA?
In order to connect to a target device through PSM, the account credentials used for the connection must be stored in the vault?
The Accounts Feed contains:
Vault admins must manually add the auditors group to newly created safes so auditors will have sufficient access to run reports.
When are external vault users and groups synchronized by default?
Which processes reduce the risk of credential theft? (Choose two.)
Which statement is correct concerning accounts that are discovered, but cannot be added to the Vault by an automated onboarding rule?
A user with administrative privileges to the vault can only grant other users privileges that he himself has.
CyberArk recommends implementing object level access control on all Safes.
Which of these accounts onboarding methods is considered proactive?
Which Vault authorization does a user need to have assigned to able to generate the "Entitlement Report" from the reports page in PVWA? (Choose two.)
What is the configuration file used by the CPM scanner when scanning UNIX/Linux devices?
In the Private Ark client, how do you add an LDAP group to a CyberArk group?
When managing SSH keys, the CPM stores the Public Key
Ad-Hoc Access (formerly Secure Connect) provides the following features. Choose all that apply.
In addition to add accounts and update account contents, which additional permission on the safe is required to add a single account?
What is the purpose of the HeadStartlnterval setting m a platform?
You are creating a Dual Control workflow for a team’s safe.
Which safe permissions must you grant to the Approvers group?
A new HTML5 Gateway has been deployed in your organization.
Where do you configure the PSM to use the HTML5 Gateway?