Which of the following can the administrator do to verify that a tape backup can be recovered in its entirety?
In order to show improvement of security over time, what must be developed?
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
Bluetooth uses which digital modulation technique to exchange information between paired devices?
Which of the following programs is usually targeted at Microsoft Office products?
A large company intends to use Blackberry for corporate mobile phones and a security analyst is assigned to evaluate the possible threats. The analyst will use the Blackjacking attack method to demonstrate how an attacker could circumvent perimeter defenses and gain access to the corporate network. What tool should the analyst use to perform a Blackjacking attack?
Which of the following is an application that requires a host application for replication?
Which statement is TRUE regarding network firewalls preventing Web Application attacks?
Which of the following describes the characteristics of a Boot Sector Virus?
What is the main difference between a “Normal” SQL Injection and a “Blind” SQL Injection vulnerability?
Which of the following is a strong post designed to stop a car?
Firewalk has just completed the second phase (the scanning phase) and a technician receives the output shown below. What conclusions can be drawn based on these scan results?

A penetration tester is conducting a port scan on a specific host. The tester found several ports opened that were confusing in concluding the Operating System (OS) version installed. Considering the NMAP result below, which of the following is likely to be installed on the target machine by the OS?
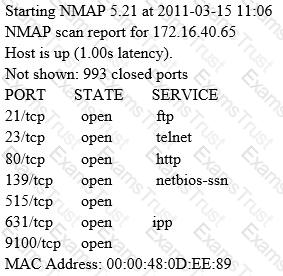
An NMAP scan of a server shows port 69 is open. What risk could this pose?
Which results will be returned with the following Google search query?
site:target.com -site:Marketing.target.com accounting
An NMAP scan of a server shows port 25 is open. What risk could this pose?
Which security control role does encryption meet?
Which system consists of a publicly available set of databases that contain domain name registration contact information?
A penetration tester was hired to perform a penetration test for a bank. The tester began searching for IP ranges owned by the bank, performing lookups on the bank's DNS servers, reading news articles online about the bank, watching what times the bank employees come into work and leave from work, searching the bank's job postings (paying special attention to IT related jobs), and visiting the local dumpster for the bank's corporate office. What phase of the penetration test is the tester currently in?
What type of OS fingerprinting technique sends specially crafted packets to the remote OS and analyzes the received response?
A penetration tester is hired to do a risk assessment of a company's DMZ. The rules of engagement states that the penetration test be done from an external IP address with no prior knowledge of the internal IT systems. What kind of test is being performed?
The following is part of a log file taken from the machine on the network with the IP address of 192.168.1.106:
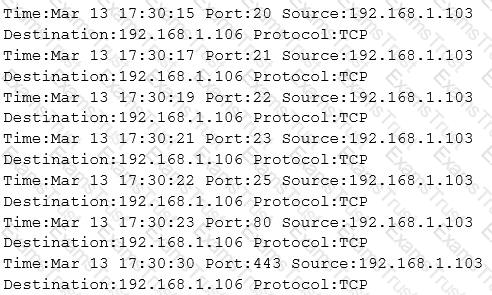
What type of activity has been logged?
Least privilege is a security concept that requires that a user is
The following is a sample of output from a penetration tester's machine targeting a machine with the IP address of 192.168.1.106:
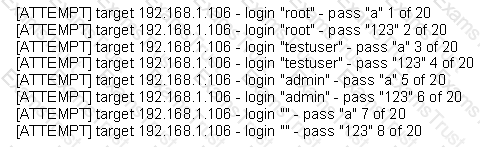
What is most likely taking place?
Which of the following processes of PKI (Public Key Infrastructure) ensures that a trust relationship exists and that a certificate is still valid for specific operations?
Which vital role does the U.S. Computer Security Incident Response Team (CSIRT) provide?
While testing the company's web applications, a tester attempts to insert the following test script into the search area on the company's web site:
Afterwards, when the tester presses the search button, a pop-up box appears on the screen with the text: "Testing Testing Testing". Which vulnerability has been detected in the web application?
SOAP services use which technology to format information?
Which security strategy requires using several, varying methods to protect IT systems against attacks?
In the OSI model, where does PPTP encryption take place?
A network security administrator is worried about potential man-in-the-middle attacks when users access a corporate web site from their workstations. Which of the following is the best remediation against this type of attack?
Which of the following is an example of IP spoofing?
Which element of Public Key Infrastructure (PKI) verifies the applicant?
Which Open Web Application Security Project (OWASP) implements a web application full of known vulnerabilities?
Employees in a company are no longer able to access Internet web sites on their computers. The network administrator is able to successfully ping IP address of web servers on the Internet and is able to open web sites by using an IP address in place of the URL. The administrator runs the nslookup command for and receives an error message stating there is no response from the server. What should the administrator do next?
When comparing the testing methodologies of Open Web Application Security Project (OWASP) and Open Source Security Testing Methodology Manual (OSSTMM) the main difference is
What tool and process are you going to use in order to remain undetected by an IDS while pivoting and passing traffic over a server you’ve compromised and gained root access to?
Which type of Nmap scan is the most reliable, but also the most visible, and likely to be picked up by and IDS?
Which of the following BEST describes the mechanism of a Boot Sector Virus?
Which mode of IPSec should you use to assure security and confidentiality of data within the same LAN?
Which of the following statements about a zone transfer is correct? (Choose three.)
Which type of security feature stops vehicles from crashing through the doors of a building?
Which of the following is a passive wireless packet analyzer that works on Linux-based systems?
Which of the following is the BEST way to protect Personally Identifiable Information (PII) from being exploited due to vulnerabilities of varying web applications?
This tool is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the PTW attack, thus making the attack much faster compared to other WEP cracking tools.
Which of the following tools is being described?
Peter, a Network Administrator, has come to you looking for advice on a tool that would help him perform SNMP enquires over the network.
Which of these tools would do the SNMP enumeration he is looking for? Select the best answers.
Which of the following statements is TRUE?
You receive an e-mail like the one shown below. When you click on the link contained in the mail, you are redirected to a website seeking you to download free Anti-Virus software.
Dear valued customers,
We are pleased to announce the newest version of Antivirus 2010 for Windows which will probe you with total security against the latest spyware, malware, viruses, Trojans and other online threats. Simply visit the link below and enter your antivirus code:
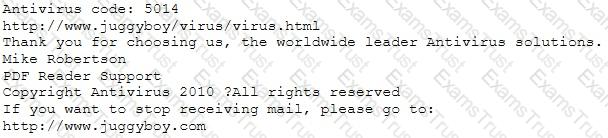
or you may contact us at the following address:
Media Internet Consultants, Edif. Neptuno, Planta
Baja, Ave. Ricardo J. Alfaro, Tumba Muerto, n/a Panama
How will you determine if this is Real Anti-Virus or Fake Anti-Virus website?
A security engineer is attempting to map a company’s internal network. The engineer enters in the following NMAP command:
NMAP –n –sS –P0 –p 80 ***.***.**.**
What type of scan is this?
An organization hires a tester to do a wireless penetration test. Previous reports indicate that the last test did not contain management or control packets in the submitted traces. Which of the following is the most likely reason for lack of management or control packets?
What is the best defense against privilege escalation vulnerability?
Which tool can be used to silently copy files from USB devices?
When an alert rule is matched in a network-based IDS like snort, the IDS does which of the following?
Which type of intrusion detection system can monitor and alert on attacks, but cannot stop them?
What is the main disadvantage of the scripting languages as opposed to compiled programming languages?
Which technical characteristic do Ethereal/Wireshark, TCPDump, and Snort have in common?
Smart cards use which protocol to transfer the certificate in a secure manner?
While checking the settings on the internet browser, a technician finds that the proxy server settings have been checked and a computer is trying to use itself as a proxy server. What specific octet within the subnet does the technician see?
What is the broadcast address for the subnet 190.86.168.0/22?
Which of the following tools will scan a network to perform vulnerability checks and compliance auditing?
A certified ethical hacker (CEH) completed a penetration test of the main headquarters of a company almost two months ago, but has yet to get paid. The customer is suffering from financial problems, and the CEH is worried that the company will go out of business and end up not paying. What actions should the CEH take?
A certified ethical hacker (CEH) is approached by a friend who believes her husband is cheating. She offers to pay to break into her husband's email account in order to find proof so she can take him to court. What is the ethical response?
An ethical hacker for a large security research firm performs penetration tests, vulnerability tests, and risk assessments. A friend recently started a company and asks the hacker to perform a penetration test and vulnerability assessment of the new company as a favor. What should the hacker's next step be before starting work on this job?
A computer technician is using a new version of a word processing software package when it is discovered that a special sequence of characters causes the entire computer to crash. The technician researches the bug and discovers that no one else experienced the problem. What is the appropriate next step?
A consultant has been hired by the V.P. of a large financial organization to assess the company's security posture. During the security testing, the consultant comes across child pornography on the V.P.'s computer. What is the consultant's obligation to the financial organization?
Which initial procedure should an ethical hacker perform after being brought into an organization?
Which type of security document is written with specific step-by-step details?
How do employers protect assets with security policies pertaining to employee surveillance activities?
International Organization for Standardization (ISO) standard 27002 provides guidance for compliance by outlining
Which of the following guidelines or standards is associated with the credit card industry?
Which of the following tools would be the best choice for achieving compliance with PCI Requirement 11?
Which method can provide a better return on IT security investment and provide a thorough and comprehensive assessment of organizational security covering policy, procedure design, and implementation?