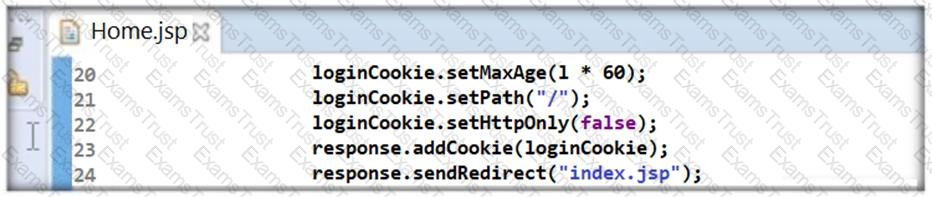
Thomas is not skilled in secure coding. He neither underwent secure coding training nor is aware of the consequences of insecure coding. One day, he wrote code as shown in the following screenshot. He passed 'false' parameter to setHttpOnly() method that may result in the existence of a certain type of vulnerability. Identify the attack that could exploit the vulnerability in the above case.
Alice works as a Java developer in Fygo software Services Ltd. He is given the responsibility to design a bookstore website for one of their clients. This website is supposed to store articles in .pdf format. Alice is advised by his superior to design ArticlesList.jsp page in such a way that it should display a list of all the articles in one page and should send a selected filename as a query string to redirect users to articledetails.jsp page.
Alice wrote the following code on page load to read the file name.
String myfilename = request.getParameter("filename");
String txtFileNameVariable = myfilename;
String locationVariable = request.getServletContext().getRealPath("/");
String PathVariable = "";
PathVariable = locationVariable + txtFileNameVariable;
BufferedInputStream bufferedInputStream = null;
Path filepath = Paths.get(PathVariable);
After reviewing this code, his superior pointed out the security mistake in the code and instructed him not repeat the same in future. Can you point the type of vulnerability that may exist in the above code?
Which of the following can be derived from abuse cases to elicit security requirements for software system?
Which of the following state management method works only for a sequence of dynamically generated forms?
The developer wants to remove the HttpSessionobject and its values from the client' system.
Which of the following method should he use for the above purpose?
Which of the threat classification model is used to classify threats during threat modeling process?
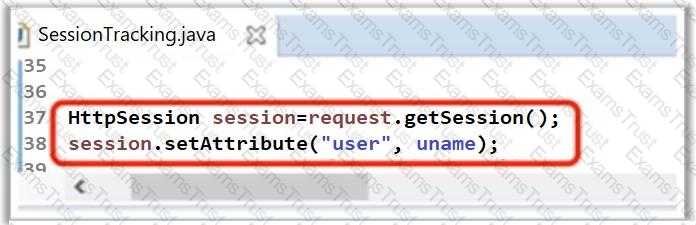
A developer has written the following line of code to handle and maintain session in the application. What did he do in the below scenario?
Which of the following relationship is used to describe abuse case scenarios?
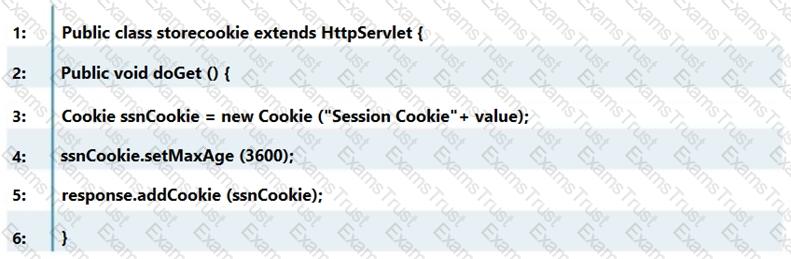
Which line of the following example of Java Code can make application vulnerable to a session attack?
The software developer has implemented encryption in the code as shown in the following screenshot.
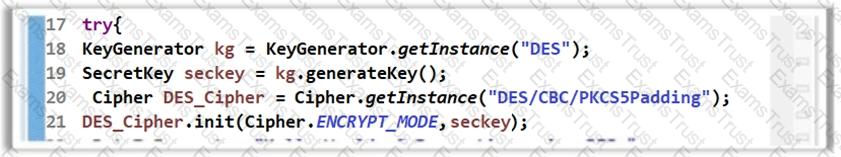
However, using the DES algorithm for encryption is considered to be an insecure coding practice as DES is a weak encryption algorithm. Which of the following symmetric encryption algorithms will you suggest for strong encryption?
Ted is an application security engineer who ensures application security activities are being followed during the entire lifecycle of the project. One day, he was analyzing various interactions of users depicted in the use cases of the project under inception. Based on the use case in hand, he started depicting the scenarios where attacker could misuse the application. Can you identify the activity on which Ted is working?
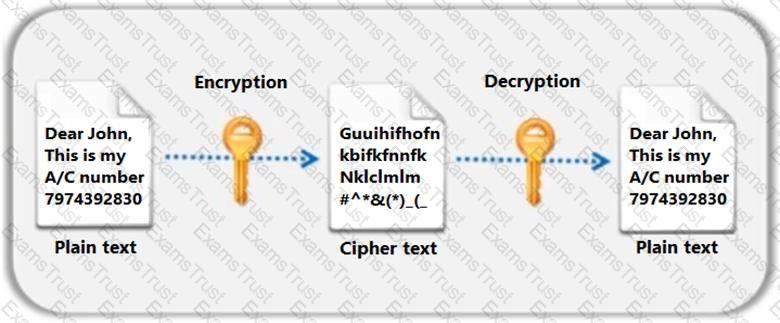
Identify the type of encryption depicted in the following figure.
Which of the risk assessment model is used to rate the threats-based risk to the application during threat modeling process?
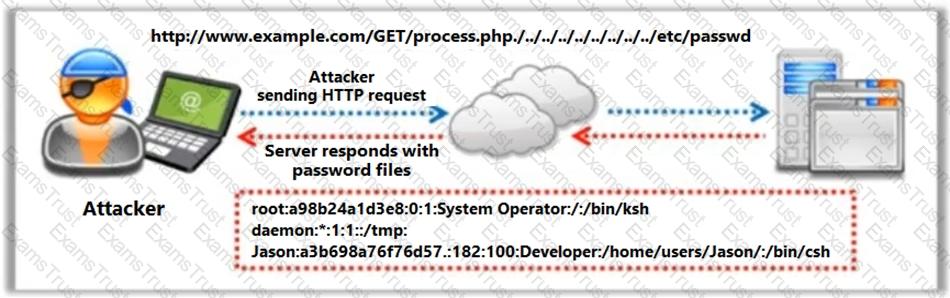
Identify the type of attack depicted in the following figure.