What is a benefit of unified storage systems?
An organization plans to deploy a deduplication solution in their data center environment They are concerned about the application servers' performance and a long backup window during backups. However, they want to retain their existing backup application.
Which deduplication solution(s) should be recommended?
What is true about Storage Class Memory (SCM)?
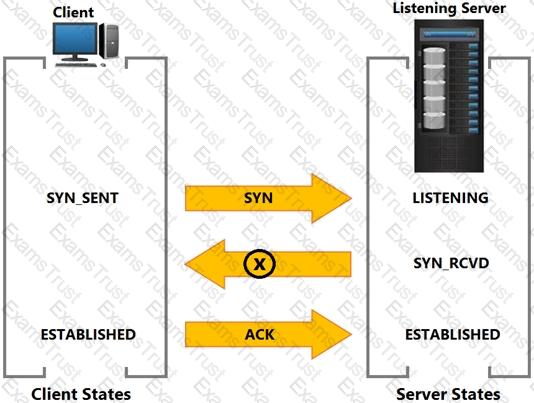
Based on the exhibit, what does the “X” represent?
Which set of factors govern the overall performance of a hard disk drive?
Which method automatically allocates a large capacity secondary cache using SSD and SCM?
An Ethernet switch has eight ports and all ports must be operational for 24 hours; from Monday through Friday. However, a failure of Port 5 occurs as follows:
Tuesday = 6 AM to 7 AM Thursday = 5 PM to 9 PM Friday = 8 AM to 9 AM
What is the MTBF of Port 5?
What occurs when a company’s IT infrastructure security is breached by a passive attack?
Which block storage device protocol achieves the optimal cost-effective balance between I/O performance and high storage capacity for midrange storage applications?
A user lost access to a key VM due to a hardware failure. A proxy server regularly takes PIT snapshots of the VM to protect the data.
What type of data protection method is this called'?
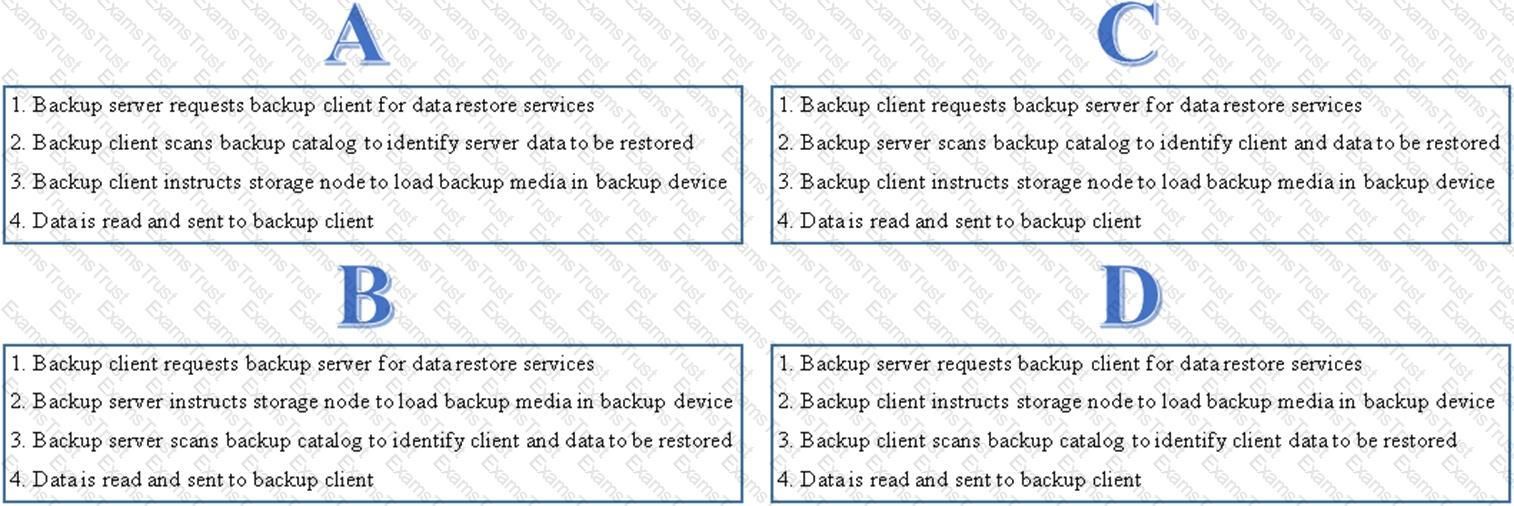
Which option shows the correct sequence of steps to perform a data recovery operation?
The Ethernet switch has eight ports and all ports must be operational for 24 hours, from Monday through Friday. However, a failure of Port 4 occurs as follows:
Monday = 8 PM to 11 PM -
Wednesday = 7 PM to 10 PM -
Thursday = 6 AM to 12 PM -
What is the MTTR of Port 4?
A company finance department needs 250 GB of storage for their business applications. A LUN is created with 250 GB, and RAID 1 protection. The LUN is configured to support application I/O performance.
If storage cost is $2 per GB, what is the chargeback amount to the department for application storage?
What is an accurate statement about governance?
A Fibre Channel switch has eight ports and all ports must be operational from 8 AM to 8 PM, Monday through Friday. However, a failure of Port 2 occurs on a particular week as follows:
Monday = 10 AM to 12 PM Wednesday = 4 PM to 9 PM Thursday = 4 PM to 7 PM
Friday = 3 PM to 6 PM Saturday = 9 AM to 1 PM
What is the availability of Port 2 in that week?
Which is a characteristic of RAID 6?
Which process eliminates data redundancy in a data set?
What information is available in a capacity planning report for storage infrastructure?
Which network performance attribute is achieved when using flow control in FOP?
Which Dell EMC product is designed to host both file and object data?
Refer to the Exhibit:
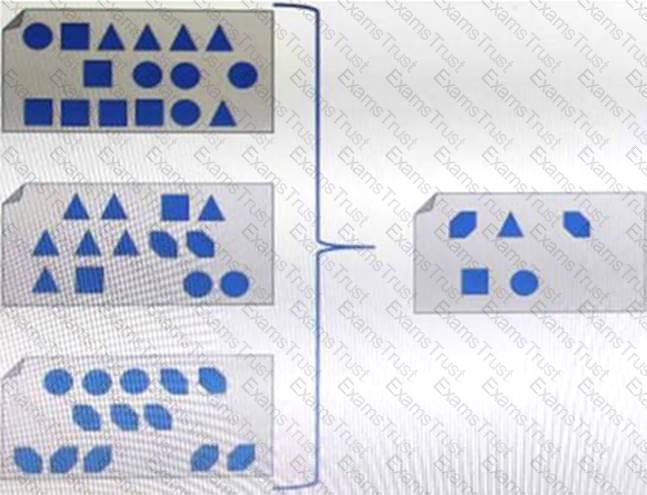
What type of process, when performed on data, would produce the result shown?
What accurately describes an object-based storage device (OSD)?
How is NVMe used to connect a host to M.2 storage devices?
In a NAS environment, which file system enables file sharing with Windows clients and uses the TCP/IP protocol?
What type of technology is used in SSD devices to provide non-volatile data storage?
An organization is planning to secure the connection between the data center and cloud while performing data backup and replication.
Which security control mechanism will help organization to achieve the desired security?
What triggers an appropriate workflow upon receiving a service provisioning or management request?
Which data deduplication method increases the probability of identifying duplicate data even when there is only a minor difference between two documents?
What is a benefit of differential backup over incremental backup?
What type of backup method allows a client to be installed in a VM that sends the data to the backup device?
What is a function of VM hardening?
What functionality does the control layer provide in a software-defined networking architecture?
Which Connectrix FC switch model supports NVMe in a 32Gb/s SAN fabric exclusively?
Which Dell EMC product is a disk-based backup and recovery solution that provides inherent source-based deduplication?
A Fibre Channel switch has eight ports and all ports must be operational from 6 AM to 6 PM, Monday through Friday.
However, a failure of Port 4 occurs with the week as follows:
Monday= 11 AM to 1 PM
Wednesday= 5 PM to 10 PM
Thursday= 7 AM to 10 AM
Saturday= 11 AM to 1 PM
What is the availability of Port 4 in that week?
Which type of data protection is used to move primary data to lower cost storage and helps to enforce compliance requirement?
Refer to the Exhibit:
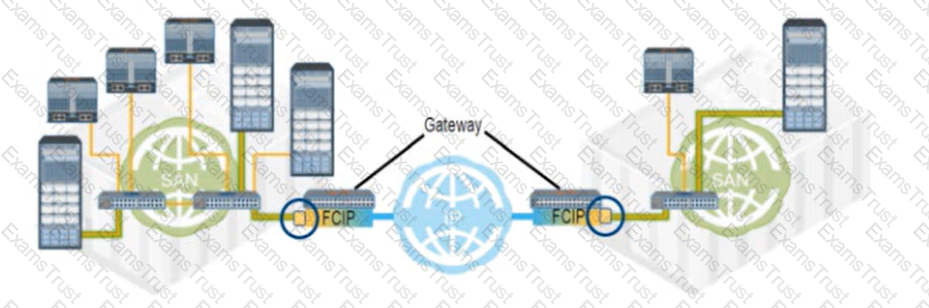
What type of FC port connects each FCIP gateway to each FC SAN?
An IT organization wants to deploy four FC switches for compute and storage system connectivity. To meet performance requirements, a maximum of one active ISL and redundant ISLs for their compute to storage traffic.
Which FC SAN topology should be recommended?
A company's assets are continuously under attack.
To deploy a security control mechanism to protect these assets, what should be considered?
In an SDS environment, which protocol supports the resource-oriented architecture for the development of scalable and lightweight web applications while adhering to a set of constraints?
Why is it important to automate the operations management process in a data center environment?
What is true about scale-out NAS storage architecture?
Refer to the Exhibit:
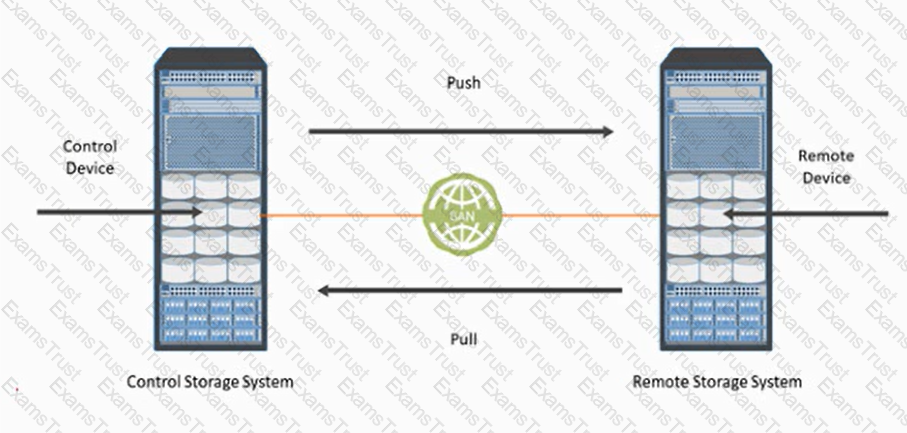
What type of data protection is represented?
What is an accurate statement about scale-out NAS?
Refer to the exhibit.
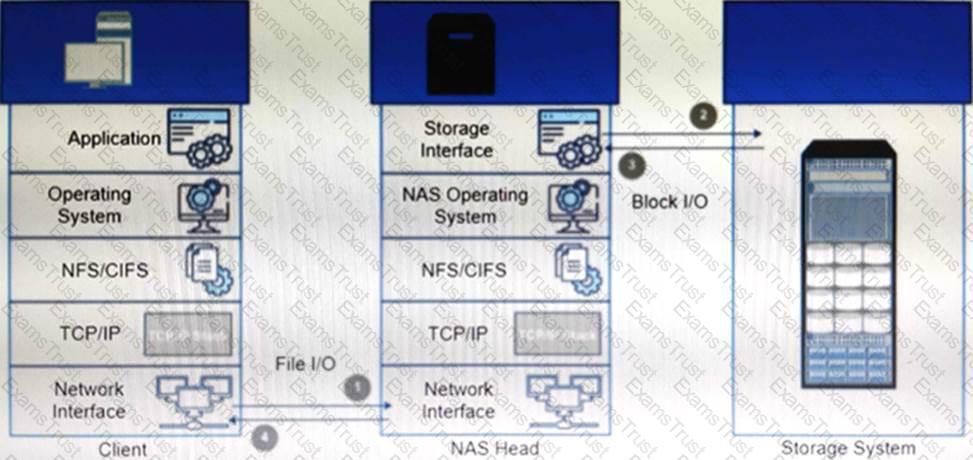
What type of NAS system(s) processes file write and read operations as described in the example?
What is determined by the amount of space configured for the journal in continuous data protection (CDP) replication?
An organization wants to consume compute, network, and storage resources through self-service portal.
Which cloud service model provides this capability?
What is true about a software defined data center?
What is an accurate statement about the Do-It-Yourself approach for building modern Infrastructure?
What is an advantage of implementing file-level virilization in a data center environment?
In a data center environment, what is an advantage of using parity-based RAID protection over mirroring?
A company plans to deploy a new application in their environment. The new application requires 5 TB of storage space. During peak workloads, the application is expected to generate 3000 IOPS with a typical I/O size of 3 KB. The capacity of each available disk drive is 750 GB. In addition, the maximum number of IOPS a drive can perform at with a 70% utilization is 90 IOPS.
What is the minimum number of disk drives needed to meet the application’s capacity and performance requirements for a RAID 0 configuration?
What is a driver for implementing end-to-end NVMe-oF?
What is the function of a control plane in the SDDC?
Why is it important for organizations to store protect and manage their data?
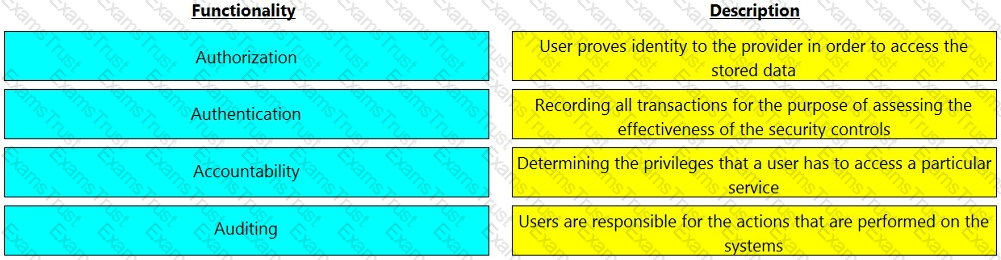
Match the functionality of a security goal with its description.