Which statements are true regarding securing communications between FortiAnalyzer and FortiGate with IPsec? (Choose two.)
Refer to the exhibit.
What is the purpose of using the Chart Builder feature on FortiAnalyzer?
Which statement describes online logs on FortiAnalyzer?
An administrator has moved FortiGate A from the root ADOM to ADOM1. However, the administrator is not able to generate reports for FortiGate A in ADOM1.
What should the administrator do to solve this issue?
What purposes does the auto-cache setting on reports serve? (Choose two.)
In order for FortiAnalyzer to collect logs from a FortiGate device, what configuration is required? (Choose two.)
Which two statements are true regarding FortiAnalyzer operating modes? (Choose two.)
Which two statements about log forwarding are true? (Choose two.)
Which two of the following must you configure on FortiAnalyzer to email a FortiAnalyzer report externally?
(Choose two.)
In FortiAnalyzer’s FormView, source and destination IP addresses from FortiGate devices are not resolving to
a hostname. How can you resolve the source and destination IPs, without introducing any additional
performance impact to FortiAnalyzer?
What is the best approach to handle a hard disk failure on a FortiAnalyzer that supports hardware RAID?
Refer to the exhibit.
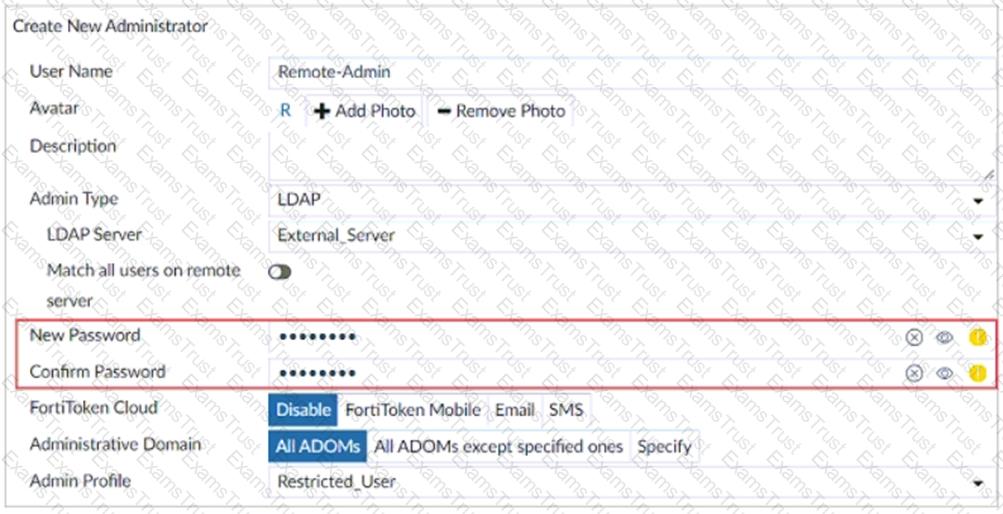
The exhibit shows the creation of a new administrator on FortiAnalyzer. The new account uses the credentials stored on an LDAP server.
Why would an administrator configure a password for this account?
Which two statements are true regarding the outbreak detection service? (Choose two.)
In Log View, you can use the Chart Builder feature to build a dataset and chart based on the filtered search results.
Similarly, which feature you can use for FortiView?
Which two parameters are used to calculate the Total Quota value available on FortiAnalyzer? (Choose two.)
Why must you wait for several minutes before you run a playbook that you just created?
Which statement describes a dataset in FortiAnalyzer?
What are offline logs on FortiAnalyzer?
A play book contains five tasks in total. An administrator executed the playbook and four out of five tasks finished successfully, but one task failed. What will be the status of the playbook after its execution?
You’ve moved a registered logging device out of one ADOM and into a new ADOM. What happens when you rebuild the new ADOM database?
Which two methods are the most common methods to control and restrict administrative access on FortiAnalyzer? (Choose two.)
Refer to the exhibit.
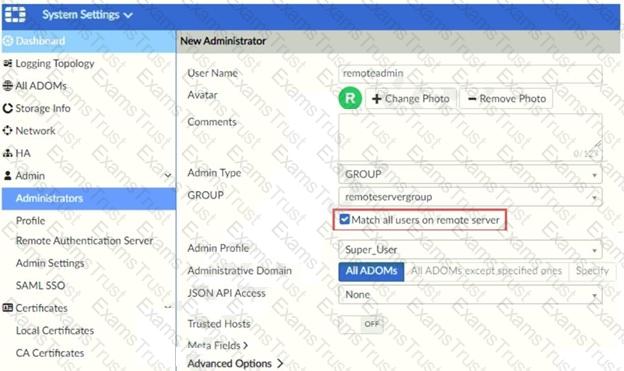
The exhibit shows “remoteservergroup” is an authentication server group with LDAP and RADIUS servers.
Which two statements express the significance of enabling “Match all users on remote server” when configuring a new administrator? (Choose two.)
How do you restrict an administrator’s access to a subset of your organization’s ADOMs?
Which statement regarding the FortiAnalyzer Fabric is true?
Which daemon is responsible for enforcing the log file size?
Refer to the exhibit.
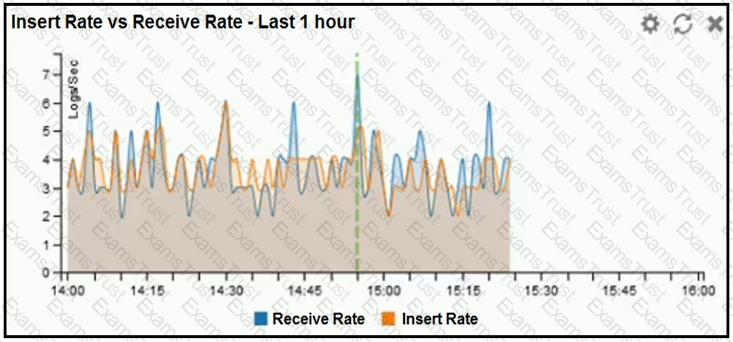
What does the data point at 14:55 tell you?
Which two statements are true about FortiAnalyzer log forwarding modes? (Choose two.)
If a hard disk fails on a FortiAnalyzer that supports software RAID, what should you do to bring the
FortiAnalyzer back to functioning normally, without losing data?
You crested a playbook on FortiAnalyzer that uses a FortiOS connector
When configuring the FortiGate side, which type of trigger must be used so that the actions in an automation stitch are available in the FortiOS connector?
In the FortiAnalyzer FortiView, source and destination IP addresses from FortiGate devices are not resolving to a hostname.
How can you resolve the source and destination IP addresses, without introducing any additional performance impact to FortiAnalyzer?
After generating a report, you notice the information you were expecting to see is not included in it. What are two possible reasons for this scenario? (Choose two.)
Which statement is true when you are upgrading the firmware on an HA cluster made up of two FortiAnalyzer devices?
Which two of the available registration methods place the device automatically in its assigned ADOM? {Choose two.)
What is the purpose of a predefined template on the FortiAnalyzer?
Which two statements about high availability (HA) on FortiAnalyzer are true? (Choose two.)
Which two statements about FortiAnalyzer operating modes are true? (Choose two.)
An administrator has configured the following settings:
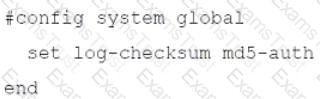
What is the purpose of executing these commands?
An administrator, fortinet, can view logs and perform device management tasks, such as adding and removing registered devices. However, administrator fortinet is not able to create a mail server that can be used to send alert emails.
What can be the problem?
An administrator has configured the following settings:
config system fortiview settings
set resolve-ip enable
end
What is the significance of executing this command?
Which two statements are true regarding ADOM modes? (Choose two.)
What is the purpose of the FortiAnalyzer command execute format disk?
When you perform a system backup, what does the backup configuration contain? (Choose two.)
Which statements are true regarding securing communications between FortiAnalyzer and FortiGate with SSL? (Choose two.)
You are trying to initiate an authorization request from FortiGate to FortiAnalyzer, but the Security Fabric window does not open when you click Authorize.
Which two reasons can cause this to happen? (Choose two.)
After you have moved a registered logging device out of one ADOM and into a new ADOM, what is the
purpose of running the following CLI command?
execute sql-local rebuild-adom
In a Fortinet Security Fabric, what can make an upstream FortiGate create traffic logs associated with sessions initiated on downstream FortiGate devices?
Which daemon is responsible for enforcing raw log file size?
Consider the CLI command:
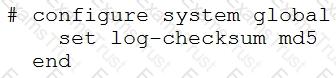
What is the purpose of the command?
What statements are true regarding disk log quota? (Choose two)
Which two statements regarding ADOM modes are true? (Choose two.)
On FortiAnalyzer, what is a wildcard administrator account?
For proper log correlation between the logging devices and FortiAnalyzer, FortiAnalyzer and all registered
devices should:
Which statement about the FortiSOAR management extension is correct?