Which statement is correct regarding the use of application control for inspecting web applications?
A network administrator has configured an SSL/SSH inspection profile defined for full SSL inspection and set with a private CA certificate. The firewall policy that allows the traffic uses this profile for SSL inspection and performs web filtering. When visiting any HTTPS websites, the browser reports certificate warning errors.
What is the reason for the certificate warning errors?
An administrator is configuring an IPsec VPN between site A and site В. The Remote Gateway setting in both sites has been configured as Static IP Address.
For site A, the local quick mode selector is 192.168.1.0/24 and the remote quick mode selector is 192.168.2.0/24.
Which subnet must the administrator configure for the local quick mode selector for site B?
When FortiGate performs SSL/SSH full inspection, you can decide how it should react when it detects an invalid certificate.
Which three actions are valid actions that FortiGate can perform when it detects an invalid certificate? (Choose three.)
A network administrator is configuring an IPsec VPN tunnel for a sales employee travelling abroad.
Which IPsec Wizard template must the administrator apply?
A network administrator enabled antivirus and selected an SSL inspection profile on a firewall policy.
When downloading an EICAR test file through HTTP, FortiGate detects the virus and blocks the file. When downloading the same file through HTTPS, FortiGate does not detect the
and does not block the file allowing it to be downloaded.
The administrator confirms that the traffic matches the configured firewall policy.
What are two reasons for the failed virus detection by FortiGate? (Choose two.)
Refer to the exhibit.
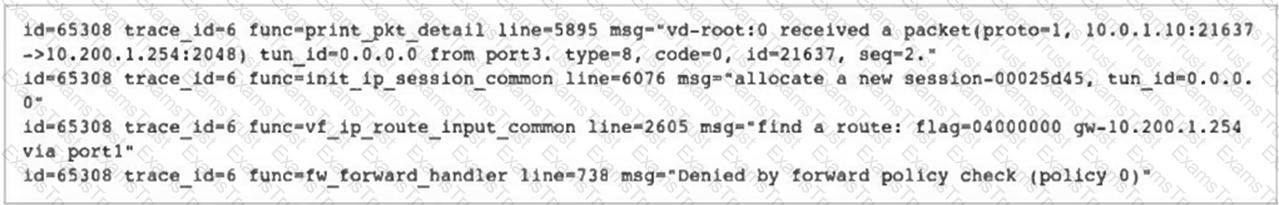
Why did FortiGate drop the packet?
Refer to the exhibits.
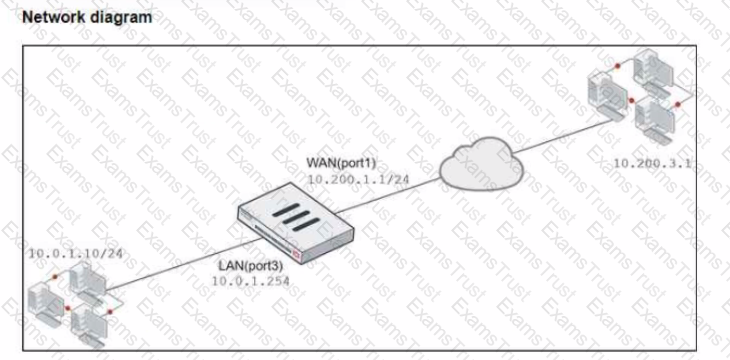

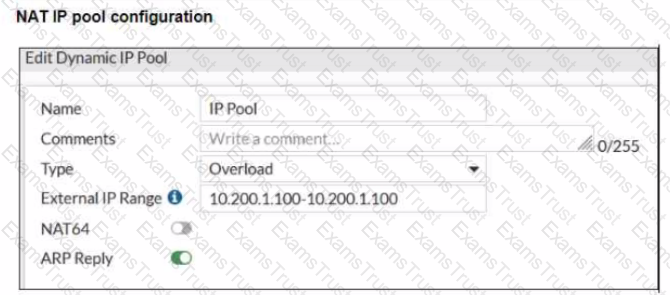
The exhibits show a diagram of a FortiGate device connected to the network, and the firewall policies configuration VIP configuration and IP pool configuration on the FortiGate device
The WAN (port1) interface has the IP address 10.200. l. 1/24 The LAN (port3) interface has the IP address 10.0.1.254/24
The first firewall policy has NAT enabled using the IP pool The second firewall policy is configured with a VIP as the destination address.
Which IP address will be used to source NAT (SNAT) the internet traffic coming from a workstation with the IP address 10.0.1.10?
Refer to the exhibit.
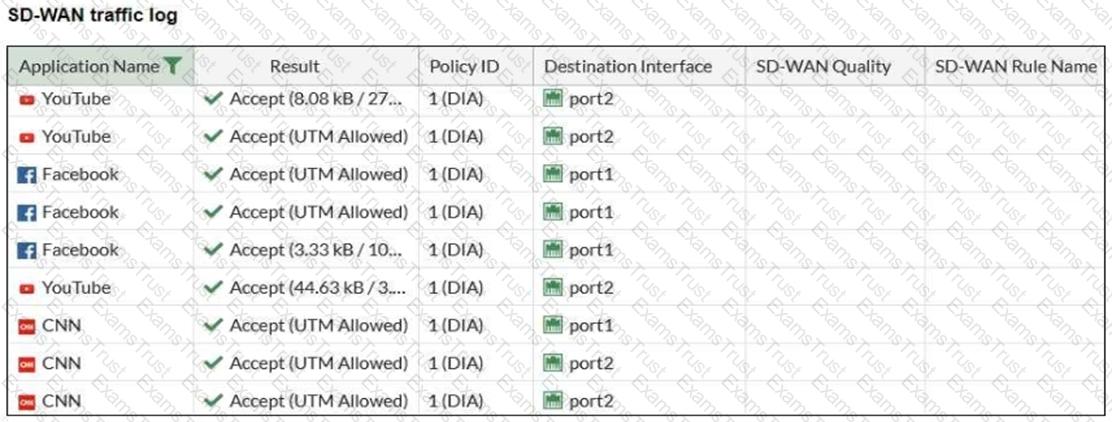
The administrator configured SD-WAN rules and set the FortiGate traffic log page to display SD-WAN-specific columns: SD-WAN Quality and SD-WAN Rule Name.
FortiGate allows the traffic according to policy ID 1. This is the policy that allows SD-WAN traffic.
Despite these settings the traffic logs do not show the name of the SD-WAN rule used to steer those traffic flows.
What can be the reason?
What are two features of collector agent advanced mode? (Choose two.)
How can you disable RPF checking?
Refer to the exhibits, which show the firewall policy and an antivirus profile configuration.
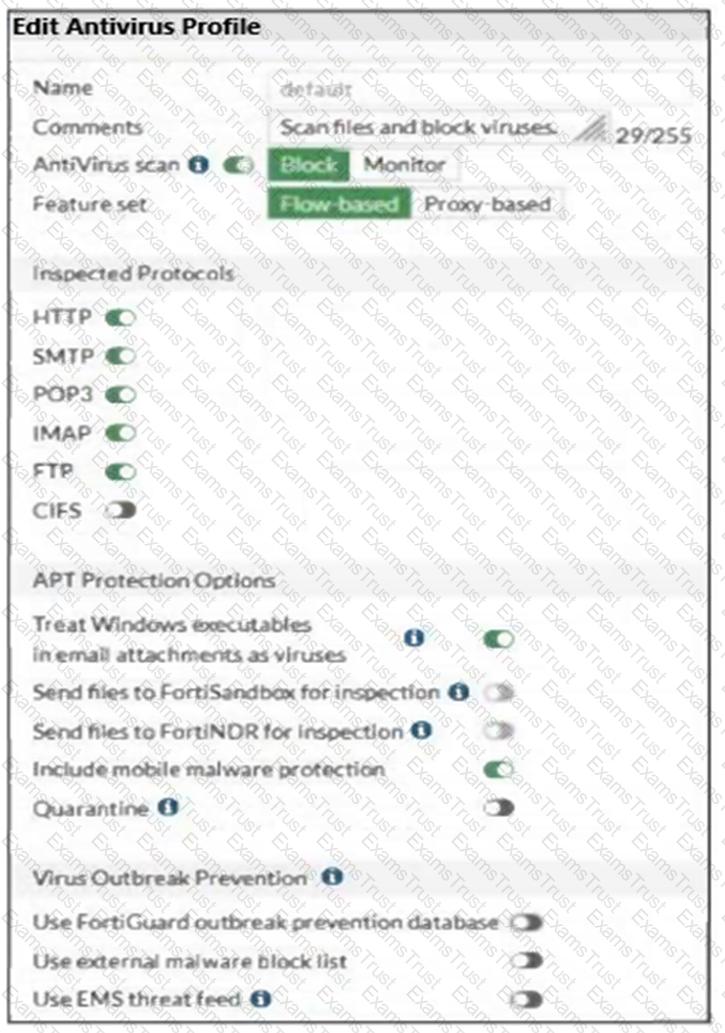
Why is the user unable to receive a block replacement message when downloading an infected file for the first time?
Refer to the exhibit.
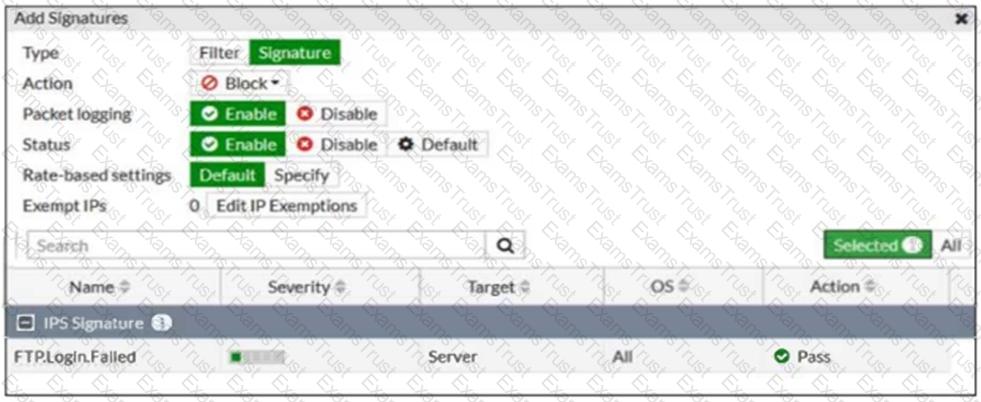
Review the intrusion prevention system (IPS) profile signature settings shown in the exhibit.
What do you conclude when adding the FTP.Login.Failed signature to the IPS sensor profile?
Which two statements about equal-cost multi-path (ECMP) configuration on FortiGate are true? (Choose two.)
Refer to the exhibits.
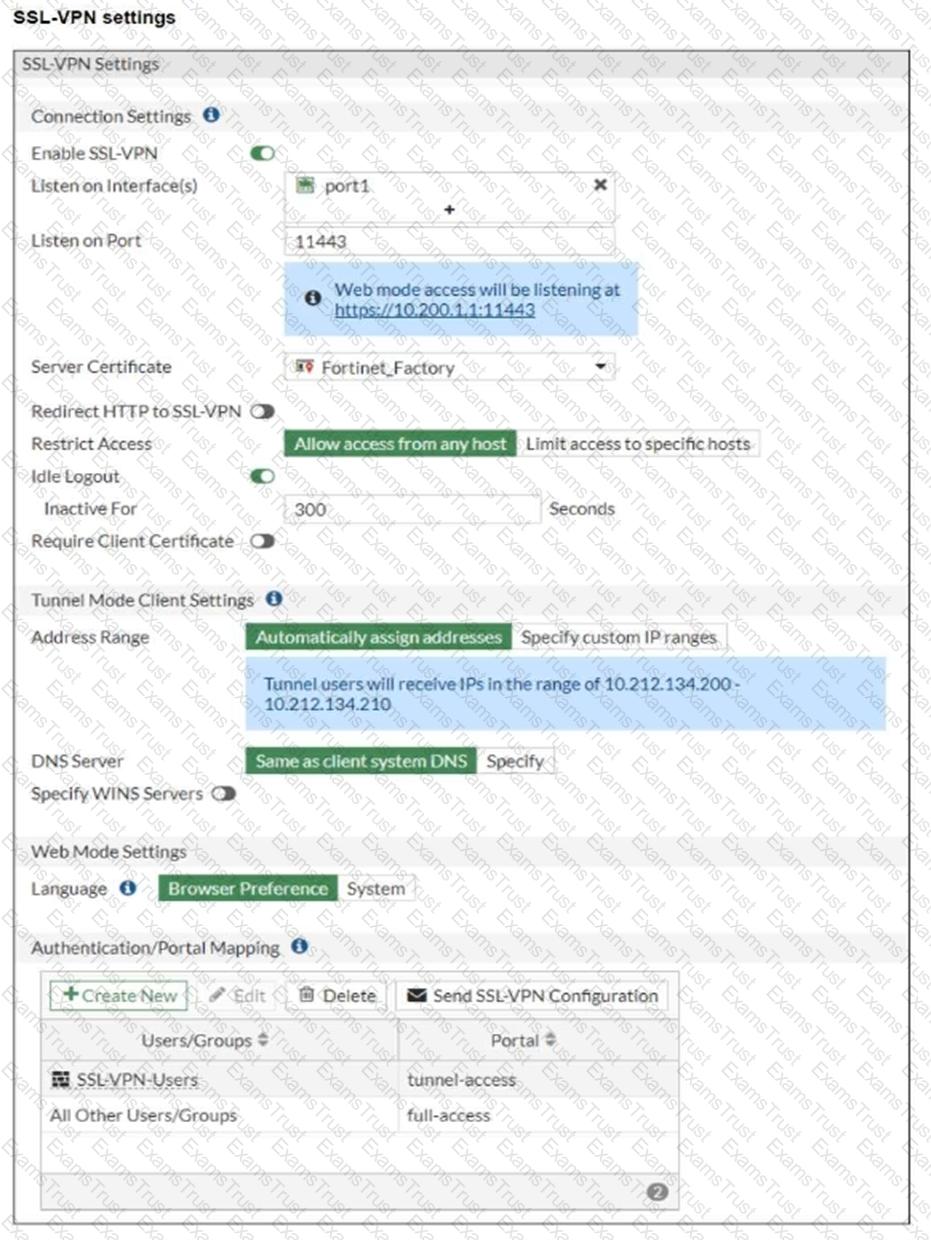
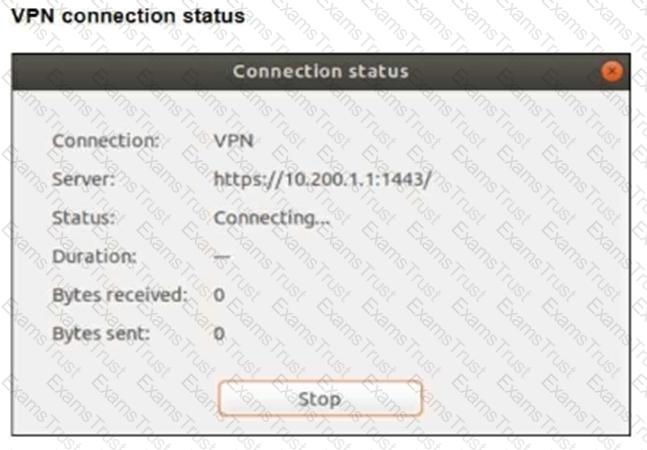
The SSL VPN connection fails when a user attempts to connect to it.
What should the user do to successfully connect to the SSL VPN?
Refer to the exhibit.

The NOC team connects to the FortiGate GUI with the NOC_Access admin profile. They request that their GUI sessions do not disconnect too early during inactivity.
What must the administrator configure to answer this specific request from the NOC team?
Which inspection mode does FortiGate use for application profiles if it is configured as a profile-based next-generation firewall (NGFW)?
What are three key routing principles in SD-WAN? (Choose three.)
Refer to the exhibit showing a debug flow output.
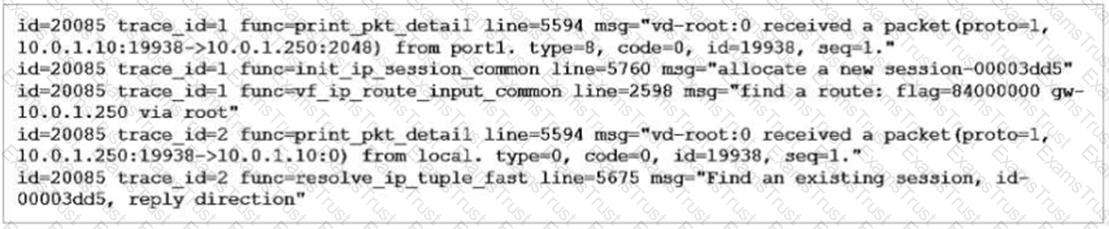
What two conclusions can you make from the debug flow output? (Choose two.)
Refer to the exhibit which contains a RADIUS server configuration.
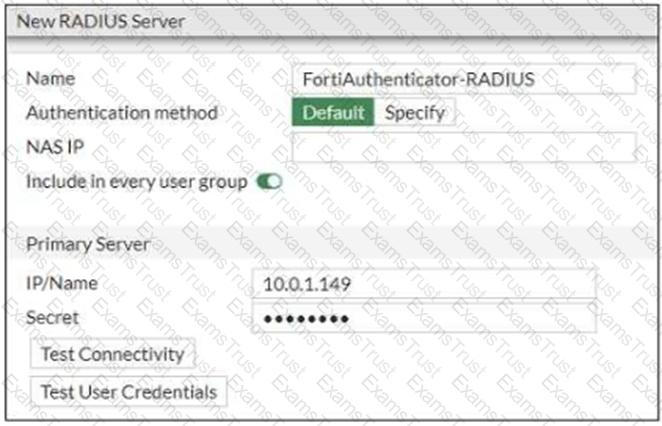
An administrator added a configuration for a new RADIUS server. While configuring, the administrator selected the Include in every user group option.
What is the impact of using the Include in every user group option in a RADIUS configuration?
There are multiple dial-up IPsec VPNs configured in aggressive mode on the HQ FortiGate. The requirement is to connect dial-up users to their respective department VPN tunnels.
Which phase 1 setting you can configure to match the user to the tunnel?
Which three statements explain a flow-based antivirus profile? (Choose three.)
Which three methods are used by the collector agent for AD polling? (Choose three.)
Refer to the exhibit.
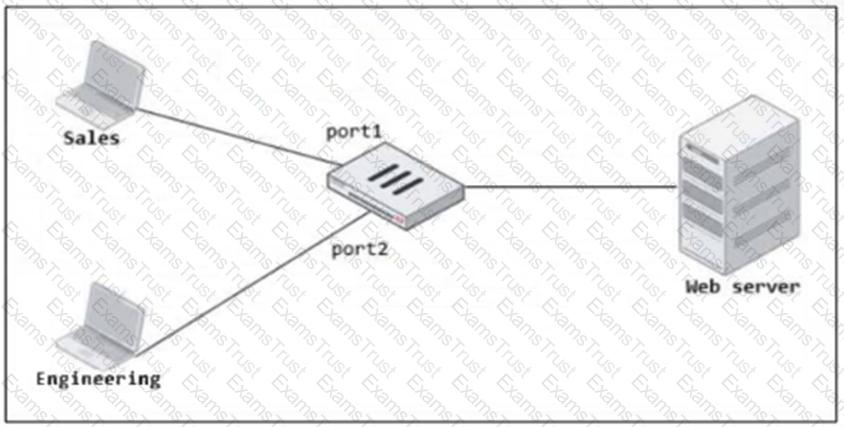
FortiGate has two separate firewall policies for Sales and Engineering to access the same web server with the same security profiles.
Which action must the administrator perform to consolidate the two policies into one?
What are two features of FortiGate FSSO agentless polling mode? (Choose two.)
Which two statements explain antivirus scanning modes? (Choose two.)