Which implementation is most suited for a deployment that must meet PCI DSS compliance criteria?
Refer to the exhibit.
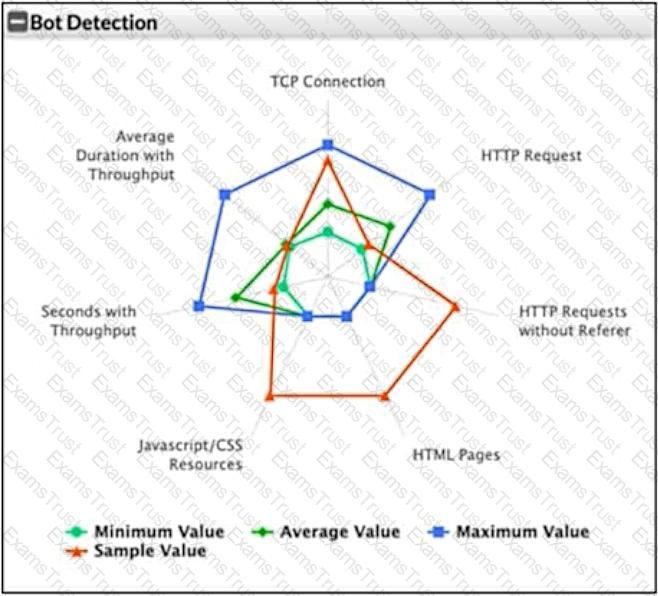
What can you conclude from this support vector machine (SVM) plot of a potential bot connection?
You are using HTTP content routing on FortiWeb. You want requests for web application A to be forwarded to a cluster of web servers, which all host the same web application. You want requests for web application B to be forwarded to a different, single web server.
Which statement regarding this solution is true?
Review the following configuration:

Which result would you expect from this configuration setting?
In which two operating modes can FortiWeb modify HTTP packets? (Choose two.)
Which three stages are part of creating a machine learning (ML) bot detection algorithm? (Choose three.)
What are two possible impacts of a DoS attack on your web server? (Choose two.)
How are bot machine learning (ML) models different from API or anomaly detection models?
An administrator notices multiple IP addresses attempting to log in to an application frequently, within a short time period. They suspect attackers are attempting to guess user passwords for a secure application.
What is the best way to limit this type of attack on FortiWeb, while still allowing legitimate traffic through?
Refer to the exhibits.
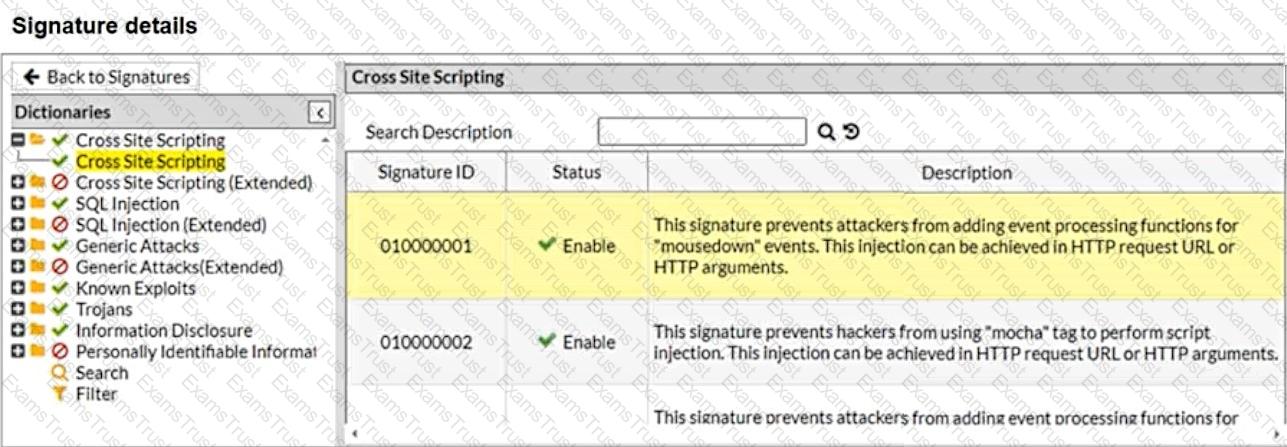
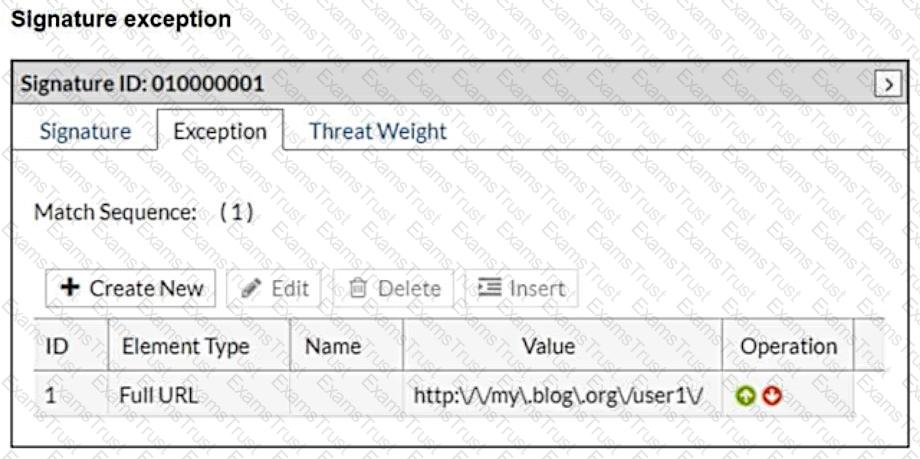
What will happen when a client attempts a mousedown cross-site scripting (XSS) attack against the site and FortiWeb is enforcing the highlighted signature?