Refer to the web filter raw logs.
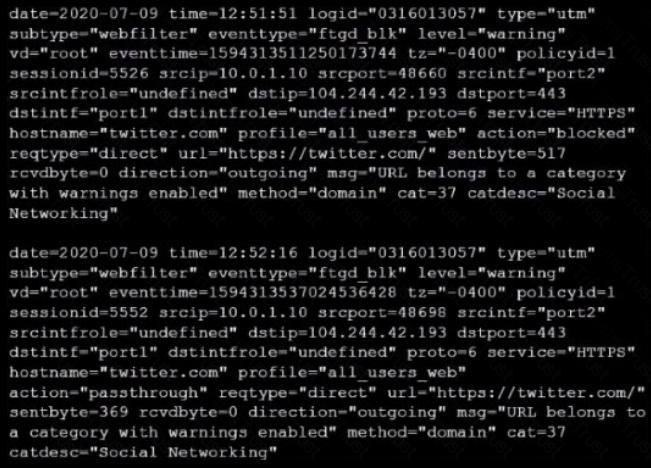
Based on the raw logs shown in the exhibit, which statement is correct?
34
The HTTP inspection process in web filtering follows a specific order when multiple features are enabled in the web filter profile. What order must FortiGate use when the web filter profile has features enabled, such as safe search?
Refer to the exhibit.
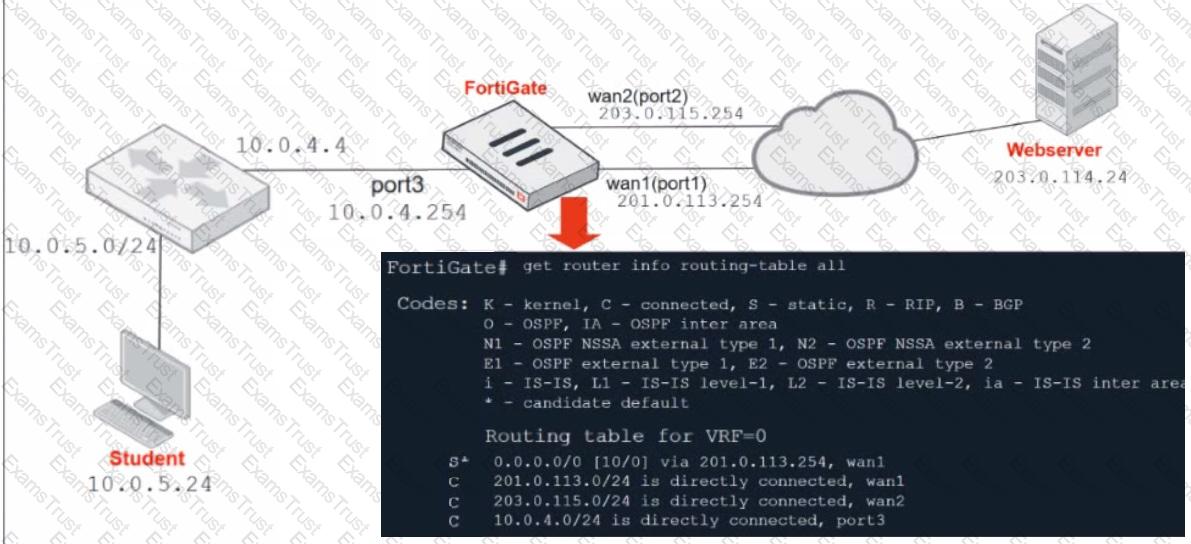
Which contains a network diagram and routing table output.
The Student is unable to access Webserver.
What is the cause of the problem and what is the solution for the problem?
82
Consider the topology:
Application on a Windows machine <--{SSL VPN} -->FGT--> Telnet to Linux server.
An administrator is investigating a problem where an application establishes a Telnet session to a Linux server over the SSL VPN through FortiGate and the idle session times out after about 90 minutes. The administrator would like to increase or disable this timeout.
The administrator has already verified that the issue is not caused by the application or Linux server. This issue does not happen when the application establishes a Telnet connection to the Linux server directly on the LAN.
What two changes can the administrator make to resolve the issue without affecting services running through FortiGate? (Choose two.)
Which timeout setting can be responsible for deleting SSL VPN associated sessions?
FortiGuard categories can be overridden and defined in different categories. To create a web rating override for example.com home page, the override must be configured using a specific syntax.
Which two syntaxes are correct to configure web rating for the home page? (Choose two.)
How does FortiGate act when using SSL VPN in web mode?
Refer to the exhibit.
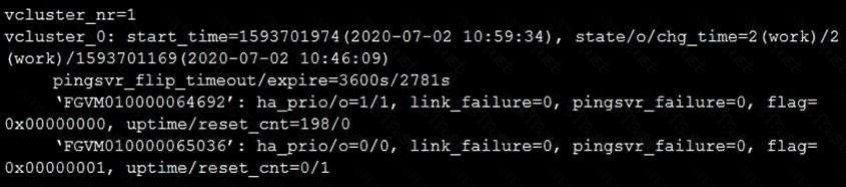
The exhibit displays the output of the CLI command: diagnose sys ha dump-by vcluster.
Which two statements are true? (Choose two.)
44
Which statement about the policy ID number of a firewall policy is true?
Which two statements are correct regarding FortiGate FSSO agentless polling mode? (Choose two.)
Refer to the exhibit.
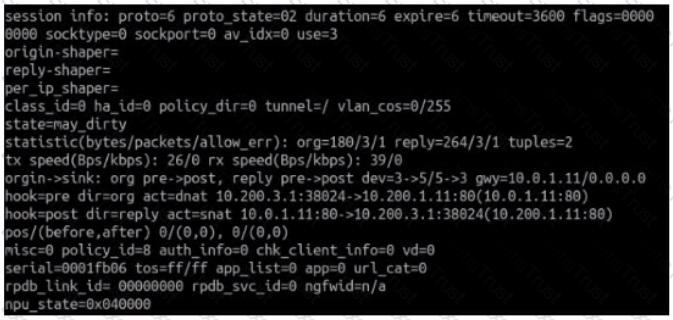
Which contains a session diagnostic output. Which statement is true about the session diagnostic output?
33
Which of statement is true about SSL VPN web mode?
Refer to the exhibit.
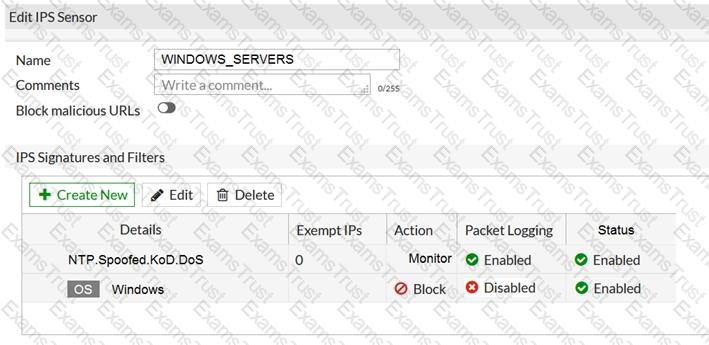
The exhibit shows the IPS sensor configuration.
If traffic matches this IPS sensor, which two actions is the sensor expected to take? (Choose two.)
An administrator wants to configure timeouts for users. Regardless of the userTMs behavior, the timer should start as soon as the user authenticates and expire after the configured value.
Which timeout option should be configured on FortiGate?
An administrator must disable RPF check to investigate an issue.
Which method is best suited to disable RPF without affecting features like antivirus and intrusion prevention system?
Which statement correctly describes NetAPI polling mode for the FSSO collector agent?
Which statement about video filtering on FortiGate is true?
An organization requires remote users to send external application data running on their PCs and access FTP resources through an SSL/TLS connection.
Which FortiGate configuration can achieve this goal?
Which statements best describe auto discovery VPN (ADVPN). (Choose two.)
A network administrator has enabled full SSL inspection and web filtering on FortiGate. When visiting any HTTPS websites, the browser reports certificate warning errors. When visiting HTTP websites, the browser does not report errors.
What is the reason for the certificate warning errors?
85
Which statement regarding the firewall policy authentication timeout is true?
20
Which two statements are true about the RPF check? (Choose two.)
Refer to the exhibit.
The exhibit shows the output of a diagnose command.
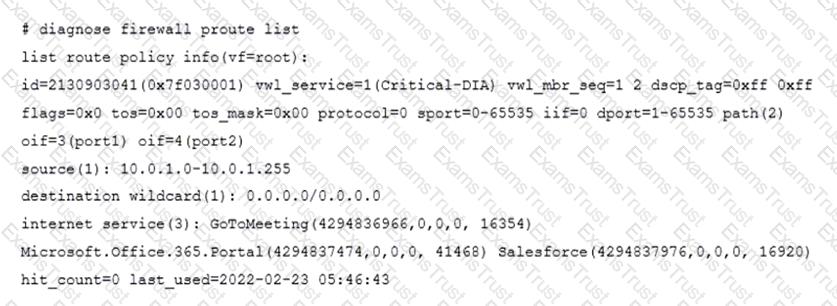
What does the output reveal about the policy route?
What is the limitation of using a URL list and application control on the same firewall policy, in NGFW policy-based mode?
99
An administrator needs to configure VPN user access for multiple sites using the same soft FortiToken. Each site has a FortiGate VPN gateway. What must an administrator do to achieve this objective?
What are two benefits of flow-based inspection compared to proxy-based inspection? (Choose two.)
Why does FortiGate Keep TCP sessions in the session table for several seconds, even after both sides (client and server) have terminated the session?
An administrator does not want to report the logon events of service accounts to FortiGate. What setting on the collector agent is required to achieve this?
Refer to the exhibit.
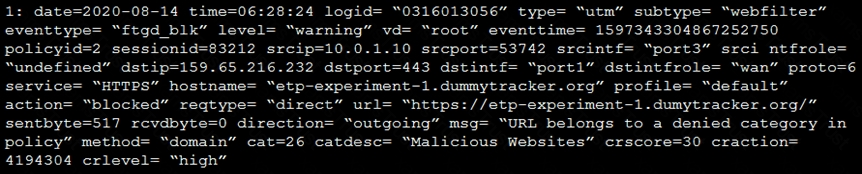
Based on the raw log, which two statements are correct? (Choose two.)
An administrator configures outgoing interface any in a firewall policy.
What is the result of the policy list view?
Which of the following SD-WAN load balancing method use interface weight value to distribute traffic? (Choose two.)
13
Which two inspection modes can you use to configure a firewall policy on a profile-based next-generation firewall (NGFW)? (Choose two.)
Refer to the exhibits.
Exhibit A shows a topology for a FortiGate HA cluster that performs proxy-based inspection on traffic. Exhibit B shows the HA configuration and the partial output of the get system ha status command.
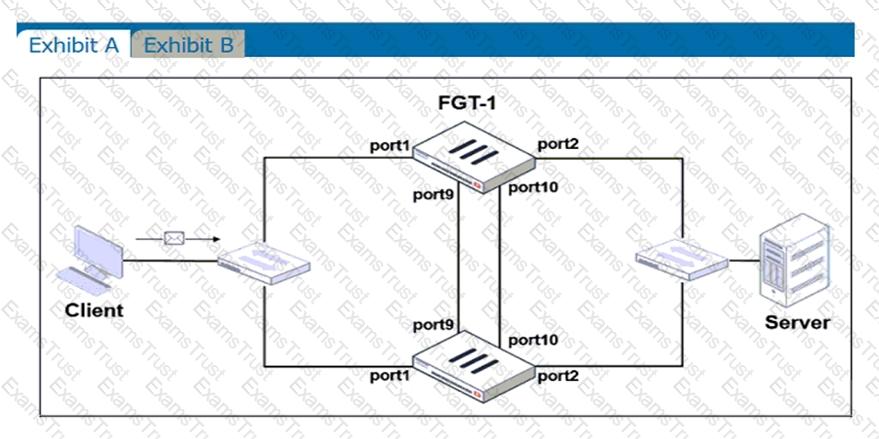
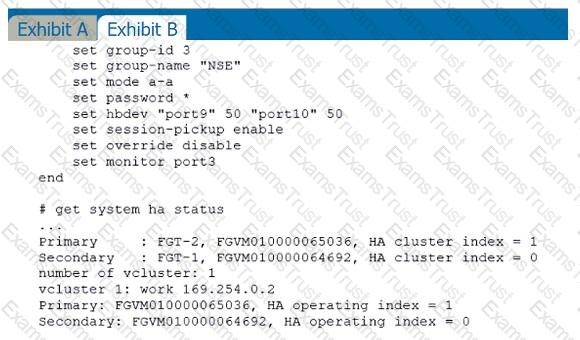
Based on the exhibits, which two statements about the traffic passing through the cluster are true? (Choose two.)
Which two statements are true about the FGCP protocol? (Choose two.)
106
Which two actions can you perform only from the root FortiGate in a Security Fabric? (Choose two.)
84
Which certificate value can FortiGate use to determine the relationship between the issuer and the certificate?
An administrator configures FortiGuard servers as DNS servers on FortiGate using default settings.
What is true about the DNS connection to a FortiGuard server?
Refer to the exhibit.
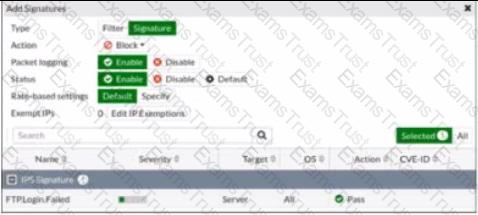
Review the Intrusion Prevention System (IPS) profile signature settings. Which statement is correct in adding the FTP.Login.Failed signature to the IPS sensor profile?
Refer to the exhibit.
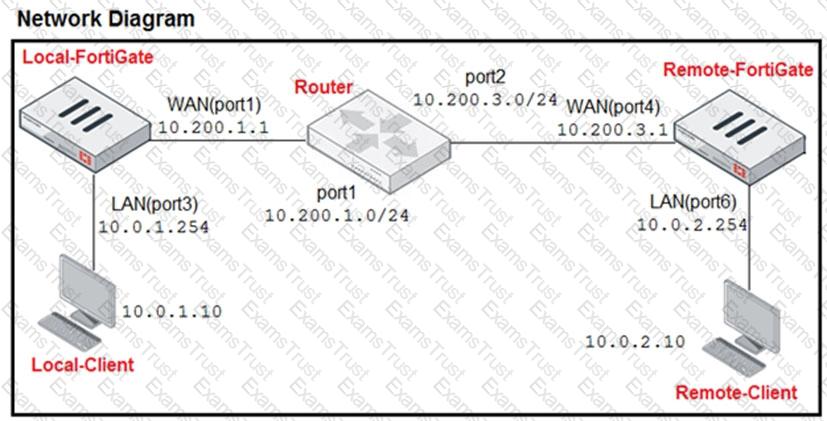
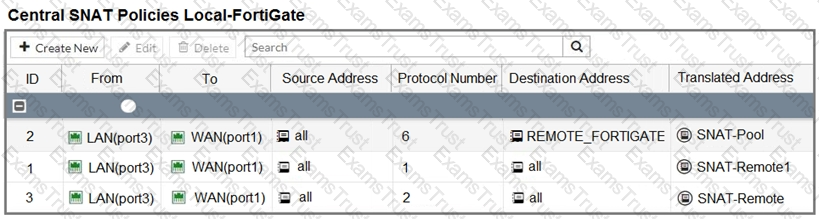
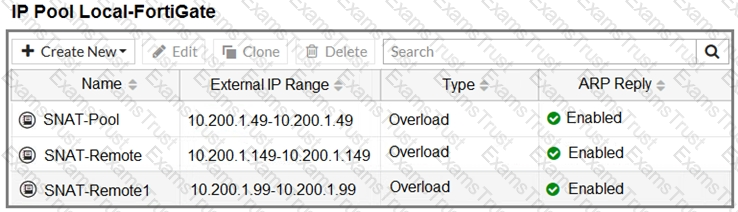
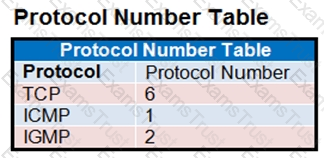
The exhibit contains a network diagram, central SNAT policy, and IP pool configuration.
The WAN (port1) interface has the IP address 10.200. 1. 1/24.
The LAN (port3) interface has the IP address 10.0. 1.254/24.
A firewall policy is configured to allow to destinations from LAN (port3) to WAN (port1).
Central NAT is enabled, so NAT settings from matching Central SNAT policies will be applied.
Which IP address will be used to source NAT the traffic, if the user on Local-Client (10.0. 1. 10) pings the IP address of Remote-FortiGate (10.200.3. 1)?
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 fails to come up. The administrator has also re-entered the pre-shared key on both FortiGate devices to make sure they match.
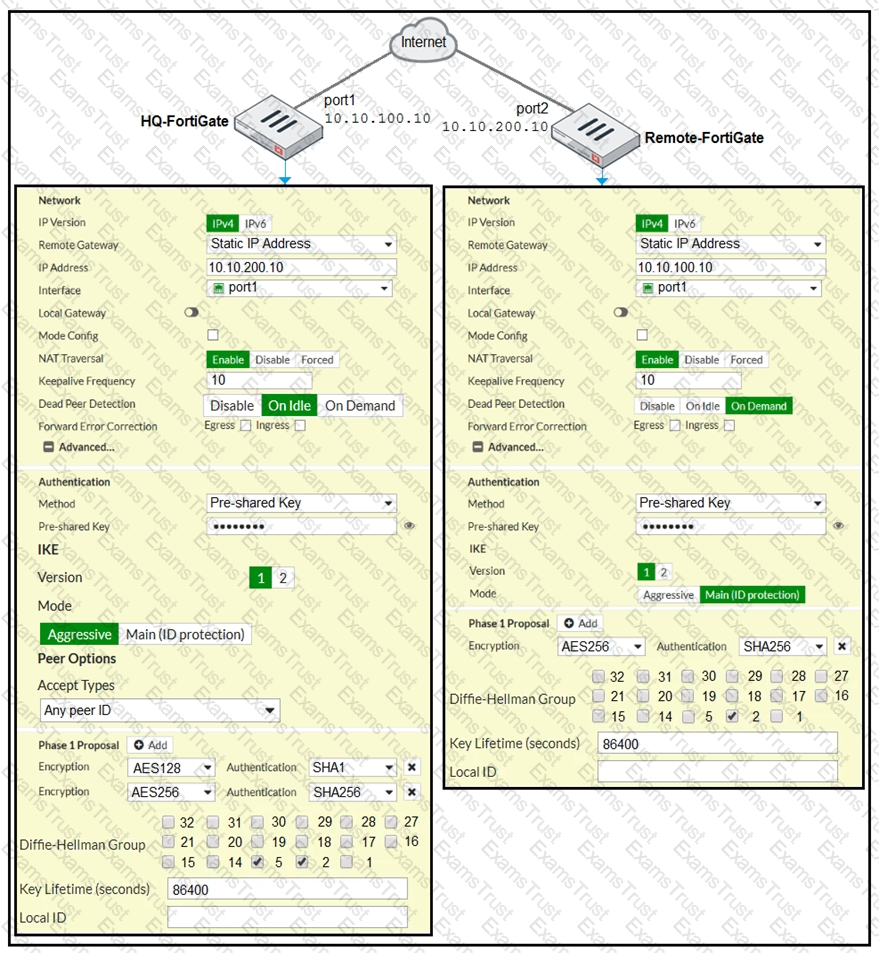
Based on the phase 1 configuration and the diagram shown in the exhibit, which two configuration changes will bring phase 1 up? (Choose two.)
30
A team manager has decided that, while some members of the team need access to a particular website, the majority of the team does not Which configuration option is the most effective way to support this request?
FortiGate is operating in NAT mode and is configured with two virtual LAN (VLAN) subinterfaces added to the same physical interface.
In this scenario, what are two requirements for the VLAN ID? (Choose two.)
Which two types of traffic are managed only by the management VDOM? (Choose two.)
27
Which feature in the Security Fabric takes one or more actions based on event triggers?
87
Which of the following are valid actions for FortiGuard category based filter in a web filter profile ui proxy-based inspection mode? (Choose two.)
Which two protocols are used to enable administrator access of a FortiGate device? (Choose two.)
Refer to the exhibits.
Exhibit A shows a network diagram. Exhibit B shows the firewall policy configuration and a VIP object configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
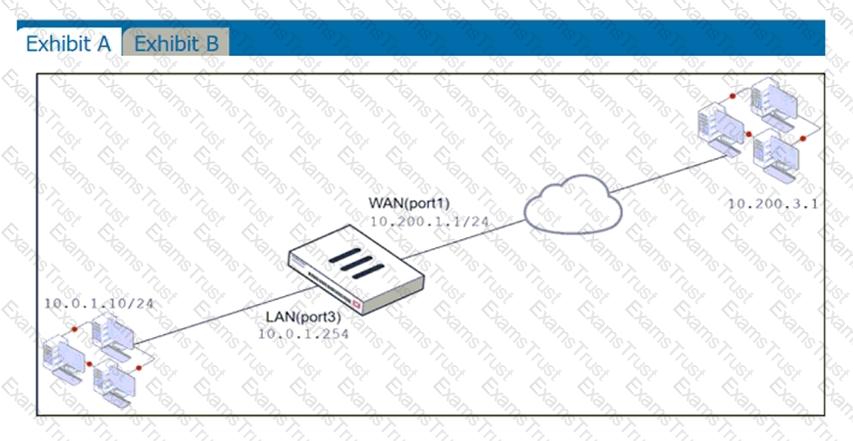
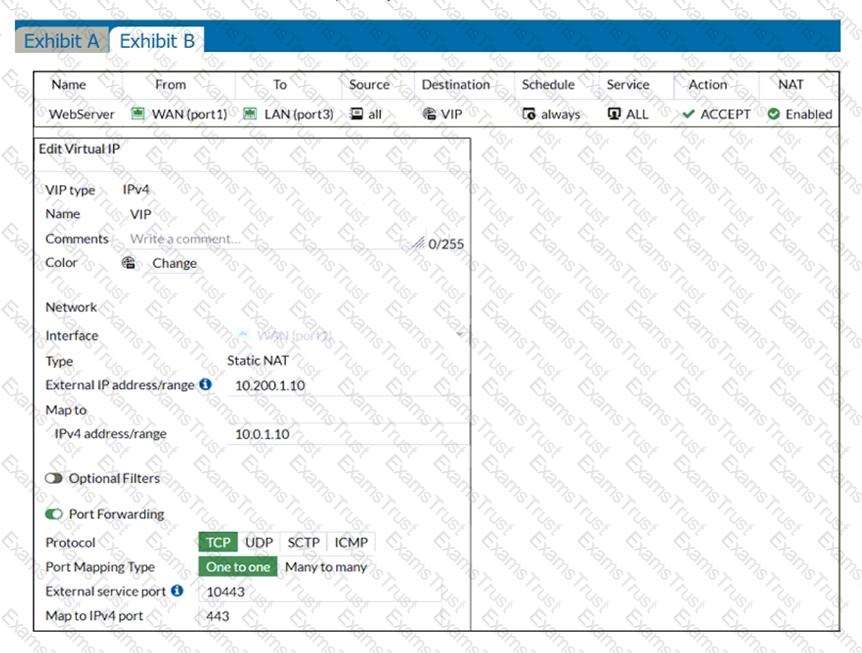
If the host 10.200.3.1 sends a TCP SYN packet on port 10443 to 10.200.1.10, what will the source address, destination address, and destination port of the packet be, after FortiGate forwards the packet to the destination?
Refer to the exhibit showing a debug flow output.
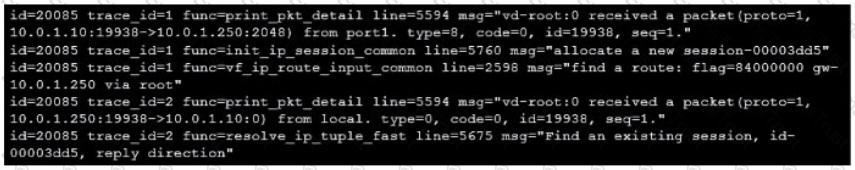
Which two statements about the debug flow output are correct? (Choose two.)
Refer to the exhibits.
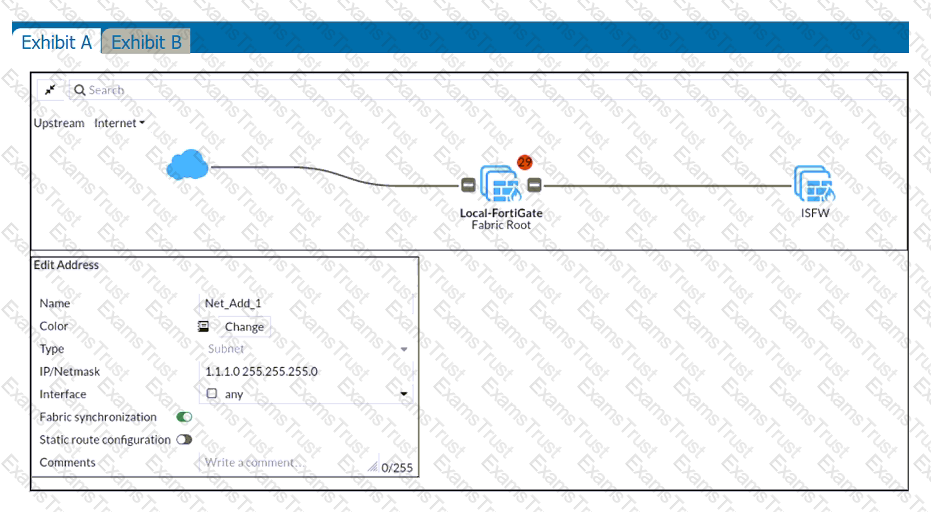
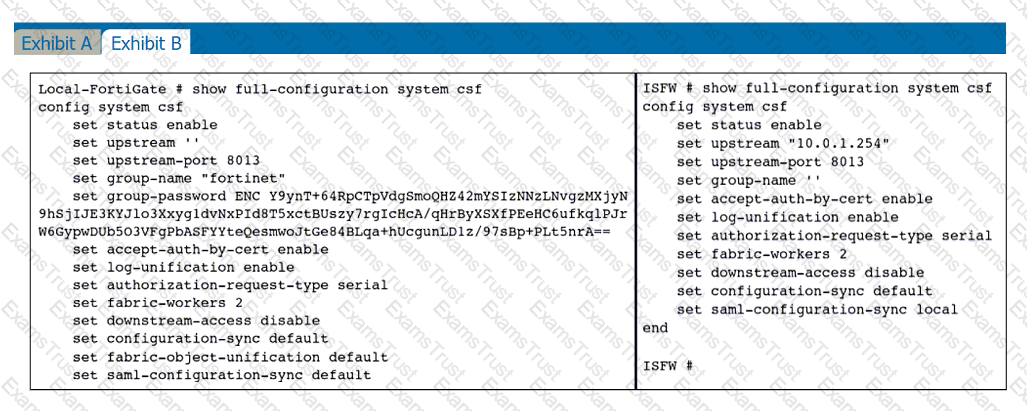
An administrator creates a new address object on the root FortiGate (Local-FortiGate) in the security fabric. After synchronization, this object is not available on the downstream FortiGate (ISFW).
What must the administrator do to synchronize the address object?
55
In which two ways can RPF checking be disabled? (Choose two )
Which three statements explain a flow-based antivirus profile? (Choose three.)