When site categories are disabled in FortiClient webfilter and antivirus (malicious websites), which feature can be used to protect the endpoint from malicious web access?
Refer to the exhibit.
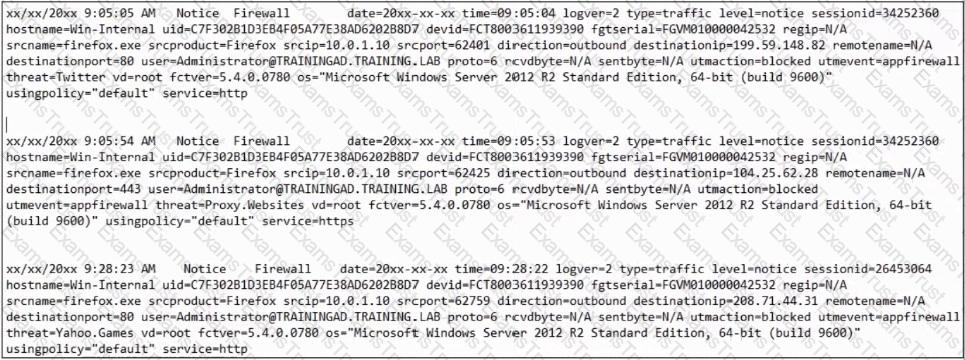
Based on the FortiClient logs shown in the exhibit which application is blocked by the application firewall?
An administrator deploys a FortiClient installation through the Microsoft AD group policy After installation is complete all the custom configuration is missing.
What could have caused this problem?
An administrator installs FortiClient on Windows Server.
What is the default behavior of real-time protection control?
Which component or device shares device status information through ZTNA telemetry?
Refer to the exhibit.
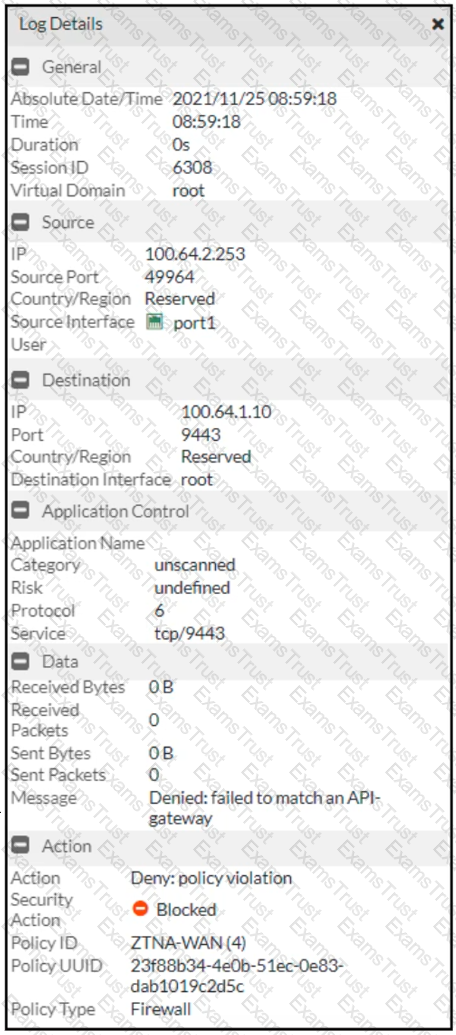
Which shows the output of the ZTNA traffic log on FortiGate.
What can you conclude from the log message?
Which three types of antivirus scans are available on FortiClient? (Choose three )
An administrator has a requirement to add user authentication to the ZTNA access for remote or off-fabric users Which FortiGate feature is required m addition to ZTNA?
Refer to the exhibits.
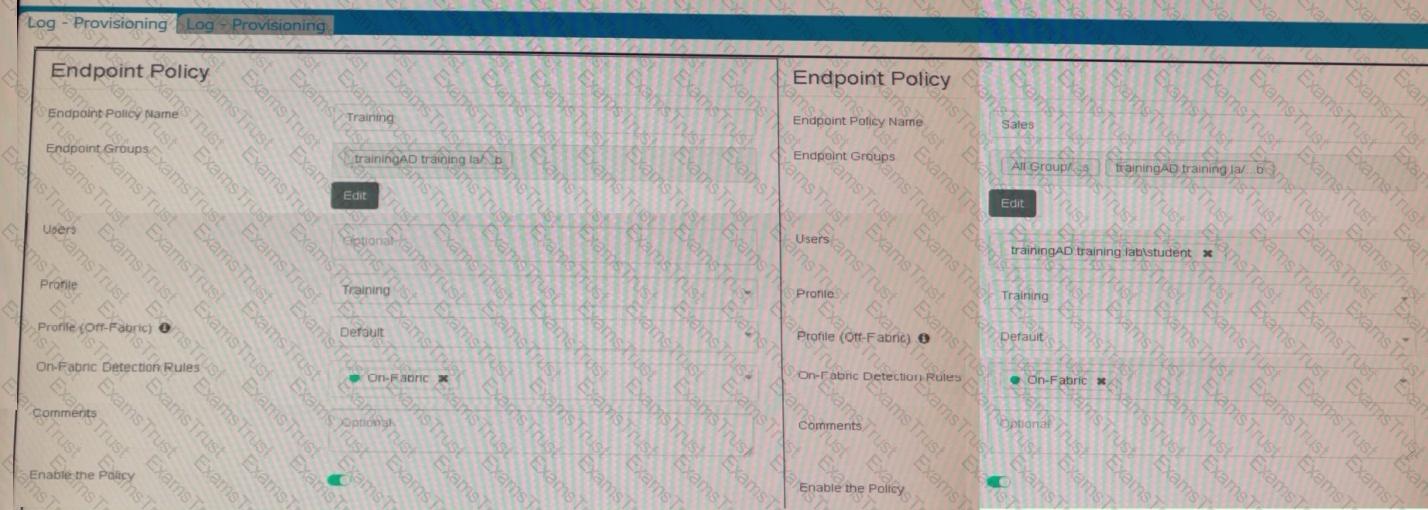
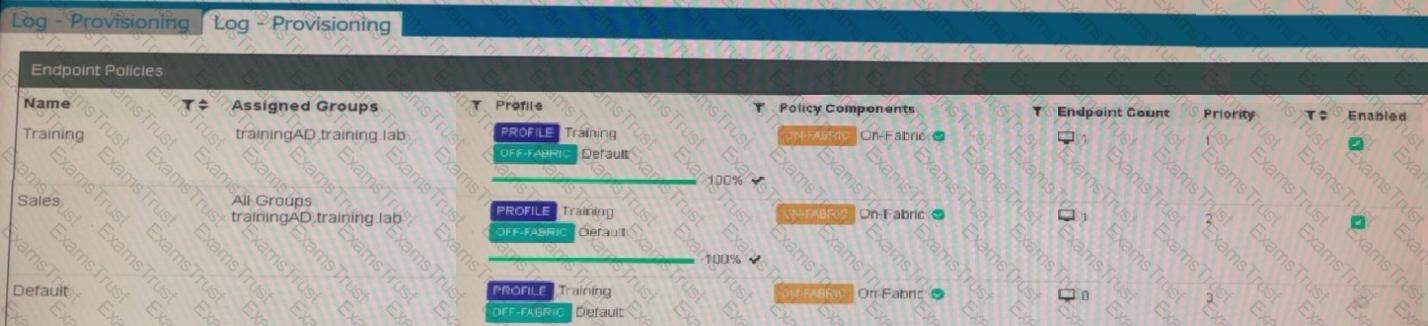
Which shows the configuration of endpoint policies.
Based on the configuration, what will happen when someone logs in with the user account student on an endpoint in the trainingAD domain?
Refer to the exhibit.
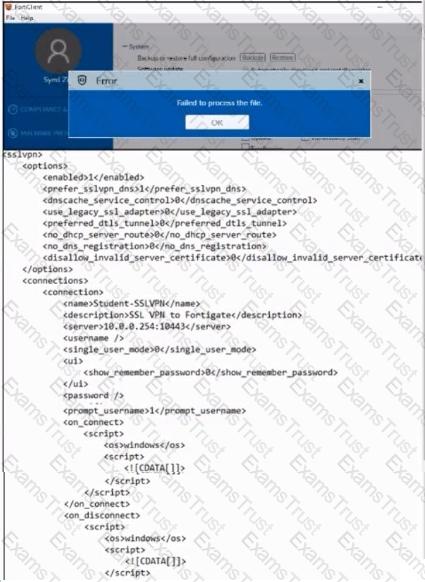
An administrator has restored the modified XML configuration file to FortiClient and sees the error shown in the exhibit.
Based on the XML settings shown in the exhibit, what must the administrator do to resolve the issue with the XML configuration file?
An administrator is required to maintain a software vulnerability on the endpoints, without showing the feature on the FortiClient dashboard. What must the administrator do to achieve this requirement?
Refer to the exhibit.
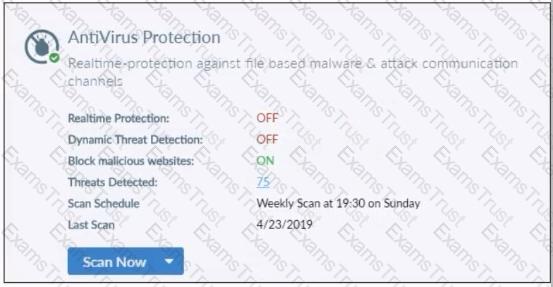
Based on the settings shown in the exhibit what action will FortiClient take when it detects that a user is trying to download an infected file?
Refer to the exhibit, which shows the Zero Trust Tagging Rule Set configuration.
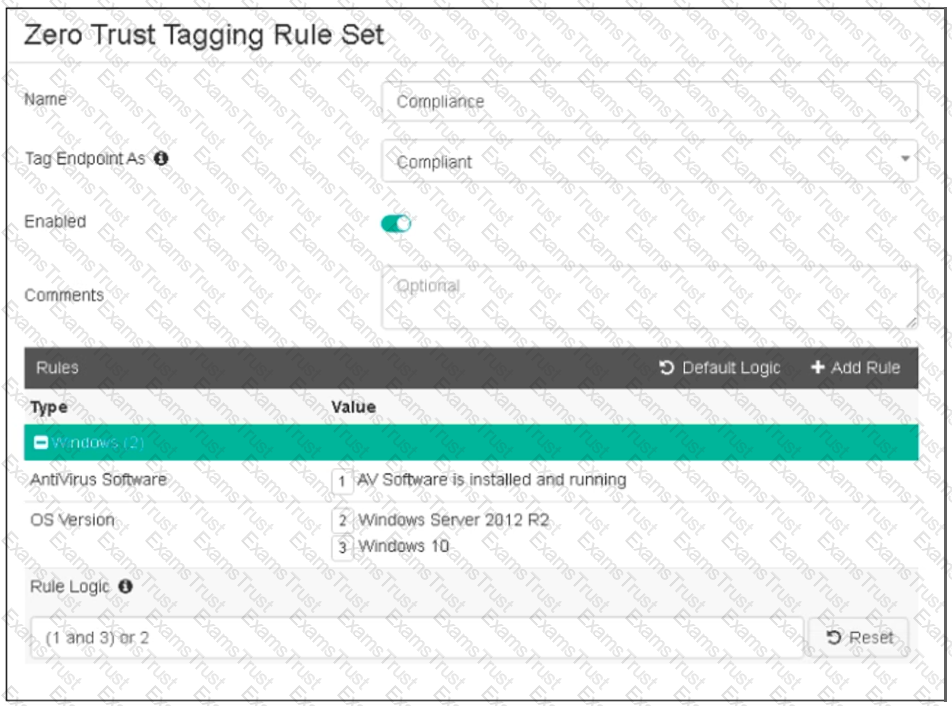
Which two statements about the rule set are true? (Choose two.)
A FortiClient EMS administrator has enabled the compliance rule for the sales department. Which Fortinet device will enforce compliance with dynamic access control?