Refer to the exhibit.
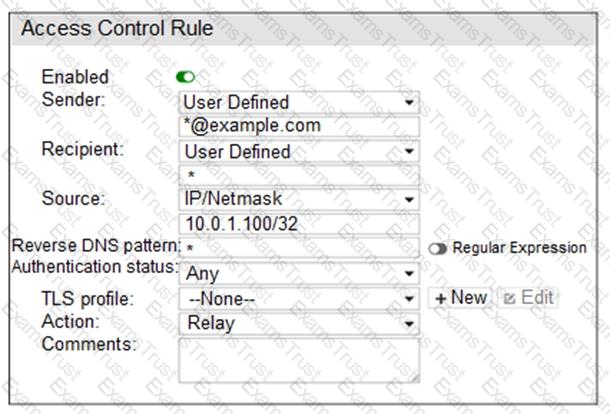
Which two statements about the access receive rule are true? (Choose two.)
Refer to the exhibit.
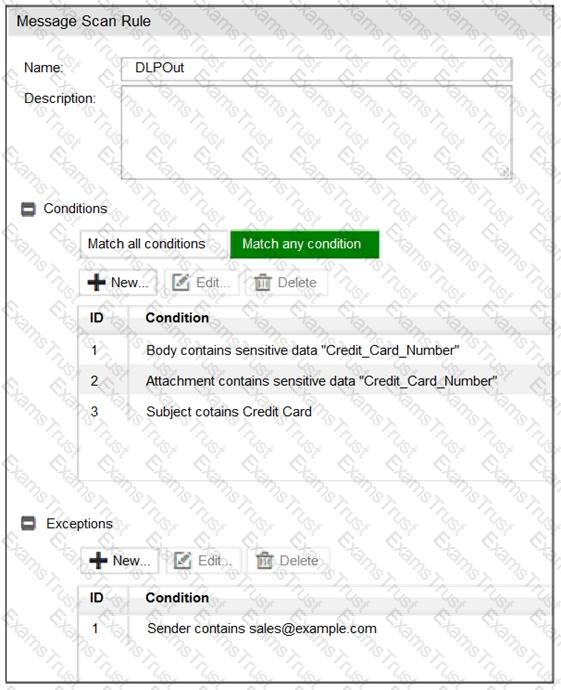
Which two message types will trigger this DLP scan rule? (Choose two.)
Which statement about how impersonation analysis identifies spoofed email addresses is correct?
FortiMail is configured with the protected domain example.com.
Which two envelope addresses will require an access receive rule, to relay for unauthenticated senders? (Choose two.)
Examine the FortMail mail server settings shown in the exhibit; then answer the question below.
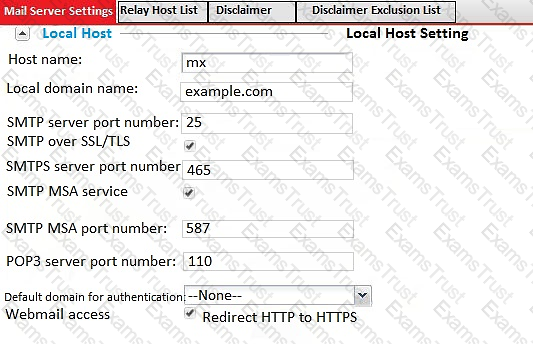
Which of the following statements are true? (Choose two.)
Examine the nslookup output shown in the exhibit; then answer the question below.
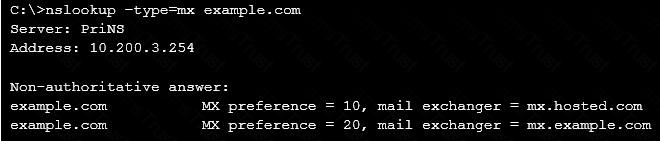
Identify which of the following statements is true regarding the example.com domain’s MTAs. (Choose two.)
Examine the FortiMail antivirus action profile shown in the exhibit; then answer the question below.
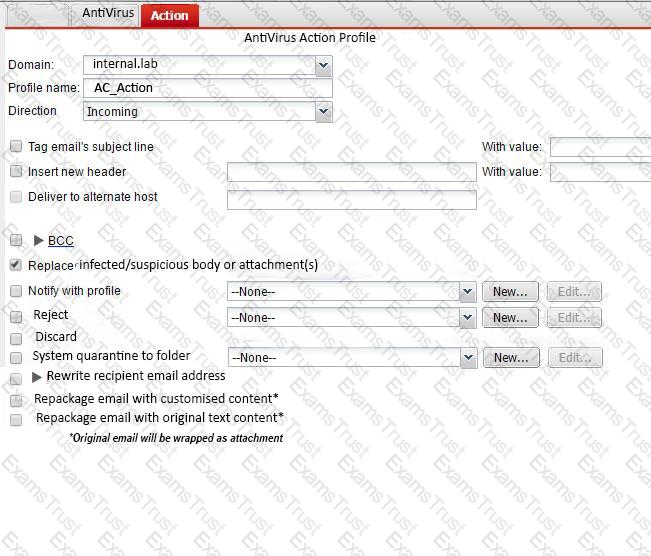
What is the expected outcome if FortiMail applies this action profile to an email? (Choose two.)
Examine the FortiMail active-passive cluster shown in the exhibit; then answer the question below.
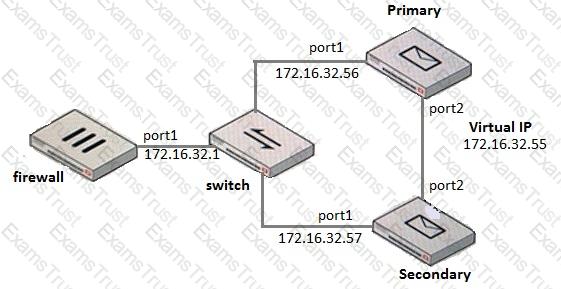
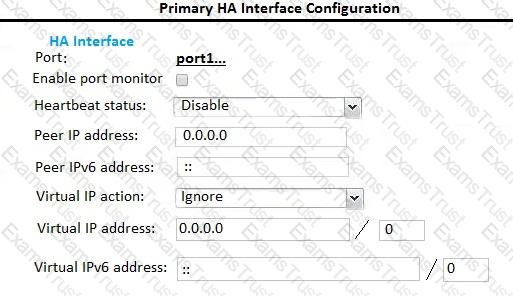
Which of the following parameters are recommended for the Primary FortiMail’s HA interface configuration? (Choose three.)