Where do you look to determine which network access policy, if any is being applied to a particular host?
What method of communication does FortiNAC use to control VPN host access on FortiGate?
Which agent can receive and display messages from FortiNAC to the end user?
Which three are components of a security rule? (Choose three.)
Where are logical network values defined?
What would occur if both an unknown (rogue) device and a known (trusted) device simultaneously appeared on a port that is a member of the Forced Registration port group?
Which two of the following are required for endpoint compliance monitors? (Choose two.)
Which devices would be evaluated by device profiling rules?
When FortiNAC is managing VPN clients connecting through FortiGate. why must the clients run a FortiNAC agent?
During the on-boarding process through the captive portal, what are two reasons why a host that successfully registered would remain stuck in the Registration VLAN? (Choose two.)
How are logical networks assigned to endpoints?
An administrator is configuring FortiNAC to manage FortiGate VPN users. As part of the configuration, the administrator must configure a few FortiGate firewall policies.
What is the purpose of the FortiGate firewall policy that applies to unauthorized VPN clients?
How does FortiGate update FortiNAC about VPN session information?
Which two methods can be used to gather a list of installed applications and application details from a host? (Choose two.)
Refer to the exhibit, and then answer the question below.
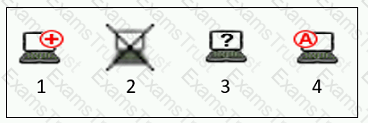
Which host is rogue?
In which view would you find who made modifications to a Group?
Refer to the exhibit.
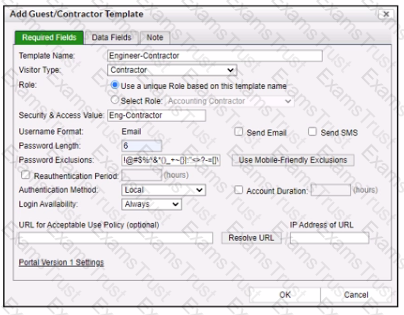
When a contractor account is created using this template, what value will be set in the accounts Rote field?