Which system group will force at-risk hosts into the quarantine network, based on point of connection?
What causes a host's state to change to "at risk"?
Refer to the exhibit.
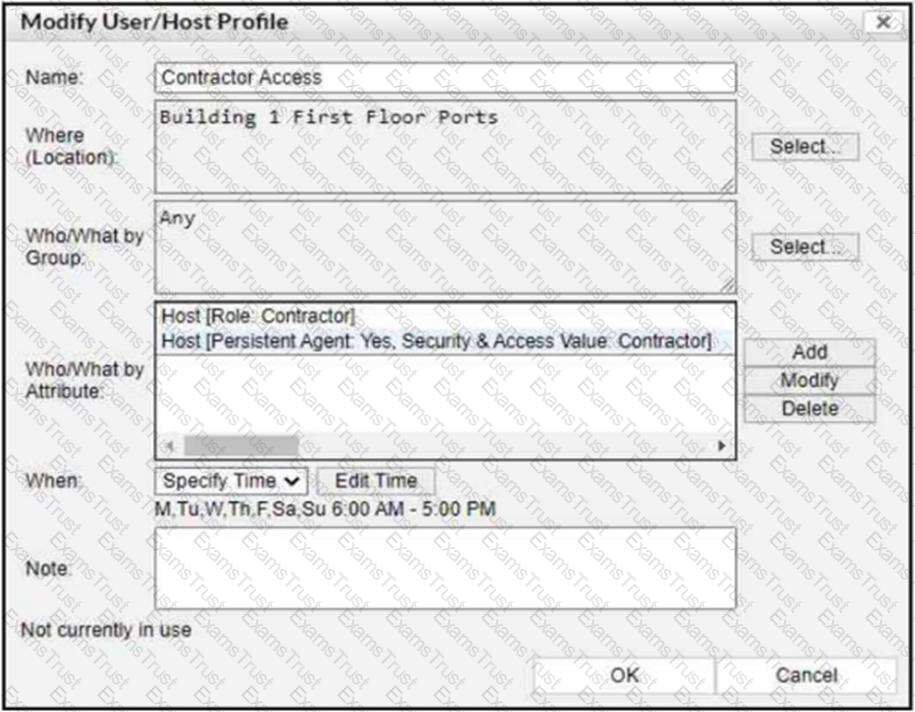
If a host is connected to a port in the Building 1 First Floor Ports group, what must also be true to match this user/host profile?
How are logical networks assigned to endpoints?
Where do you look to determine which network access policy, if any is being applied to a particular host?
View the command and output shown in the exhibit.
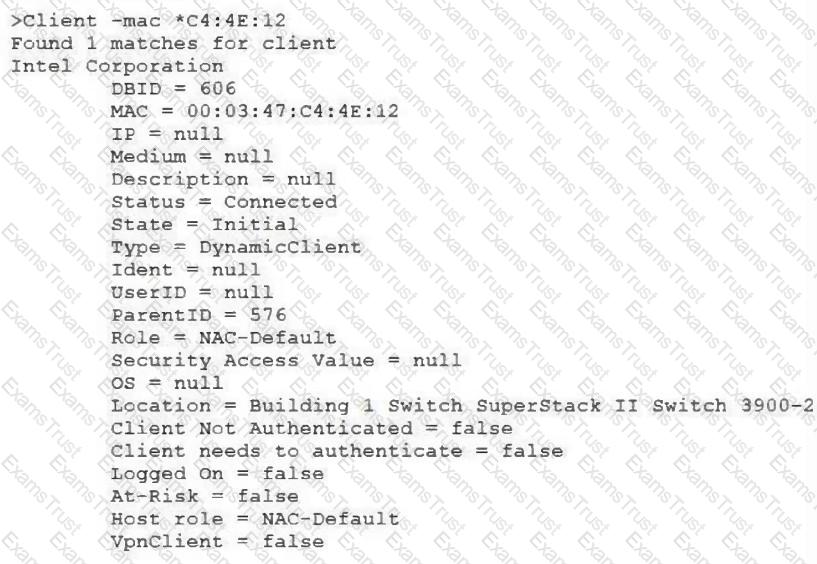
What is the current state of this host?
Which two policy types can be created on a FortiNAC Control Manager? (Choose two.)
Which two of the following are required for endpoint compliance monitors? (Choose two.)
In a wireless integration, what method does FortiNAC use to obtain connecting MAC address information?
Which agent can receive and display messages from FortiNAC to the end user?
Refer to the exhibit.
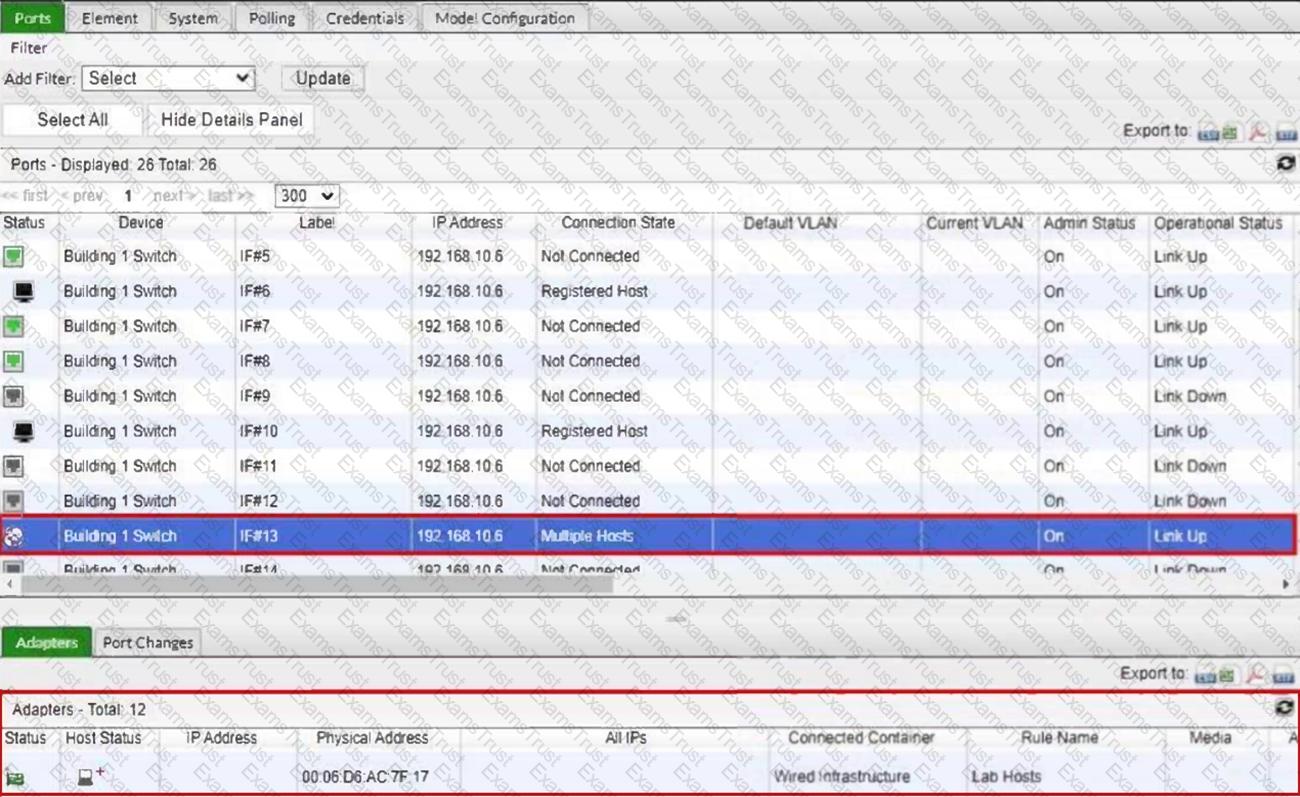
What would happen if the highlighted port with connected hosts was placed in both the Forced Registration and Forced Remediation port groups?
View the command and output.
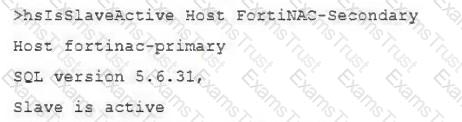
What is the state of database replication?
With enforcement for network access policies and at-risk hosts enabled, what will happen if a host matches a network access policy and has a state of "at risk"?
An administrator wants the Host At Risk event to generate an alarm. What is used to achieve this result?