Which two system monitoring reports are available on the System Monitoring widget?
(Choose two.)
A security analyst has reported unauthorized access to System Configuration. You must review the user's current level of access, and then restrict their access according to your organization's requirements. As part of your auditing process, which two actions should you perform? (Choose two.)
What are two different services that you can configure for monitoring system and cluster health statuses on FortiSOAR?
(Choose two.)
Which two statements about appliance users are true? (Choose two.)
Refer to the exhibit.
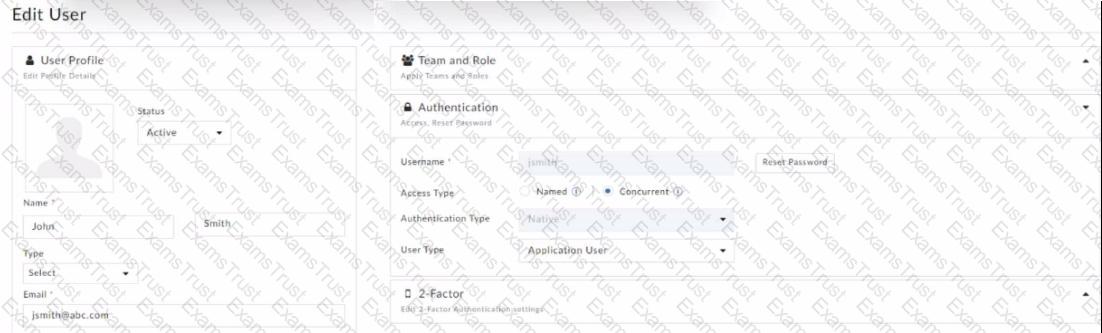
Which statement correctly describes the user's login behavior?
Which three roles are defined as SAML roles?
(Choose three.)
WhichSMS vendor does FortiSOAR support for two-factor authentication?
What are two features of the FortiSOAR perpetual trial license? (Choose two.).
Refer to the exhibit.
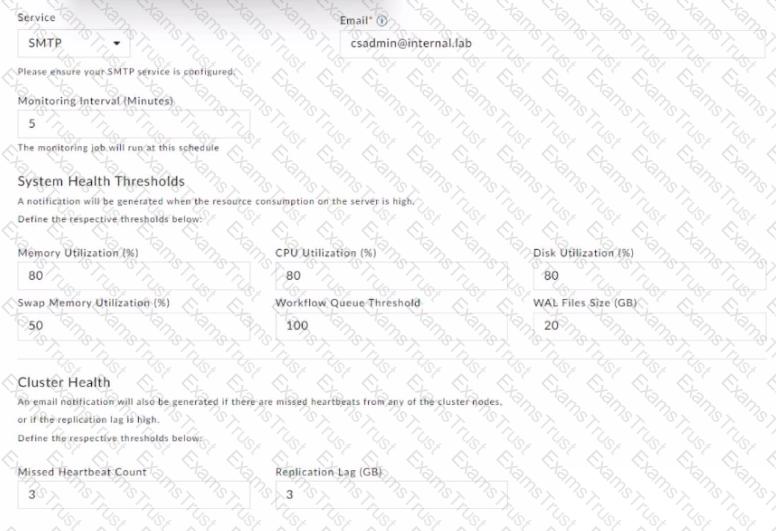
How long after the syops-ha service goes down will the heartbeat missed notification be sent to the administrator?
What are two system-level logs that can be purged using application configuration? (Choose two.)
Which three actions can be performed from within the war room? (Choose three)