Which three common breach points can be found in a typical OT environment? (Choose three.)
When device profiling rules are enabled, which devices connected on the network are evaluated by the device profiling rules?
Which three criteria can a FortiGate device use to look for a matching firewall policy to process traffic? (Choose three.)
Refer to the exhibit.
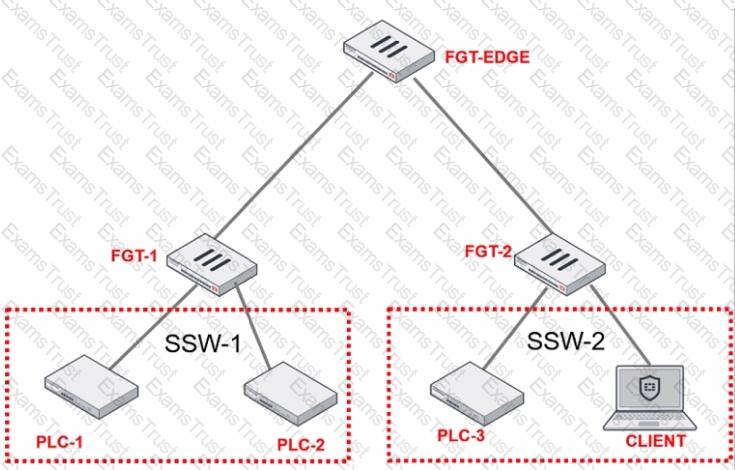
PLC-3 and CLIENT can send traffic to PLC-1 and PLC-2. FGT-2 has only one software switch (SSW-1) connecting both PLC-3 and CLIENT. PLC-3 and CLIENT cannot send traffic to each other.
Which two statements about the traffic between PCL-1 and PLC-2 are true? (Choose two.)
Refer to the exhibits.
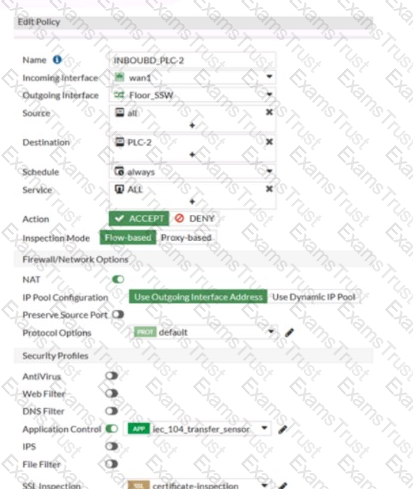
Which statement is true about the traffic passing through to PLC-2?
As an OT administrator, it is important to understand how industrial protocols work in an OT network.
Which communication method is used by the Modbus protocol?
An administrator wants to use FortiSoC and SOAR features on a FortiAnalyzer device to detect and block any unauthorized access to FortiGate devices in an OT network.
Which two statements about FortiSoC and SOAR features on FortiAnalyzer are true? (Choose two.)
Refer to the exhibit.

Which statement about the interfaces shown in the exhibit is true?
Refer to the exhibit.
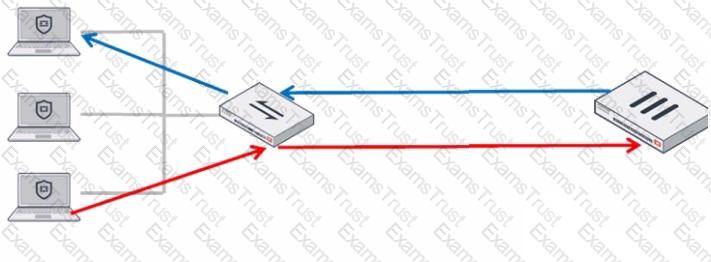
In order for a FortiGate device to act as router on a stick, what configuration must an OT network architect implement on FortiGate to achieve inter-VLAN routing?
Refer to the exhibit, which shows a non-protected OT environment.
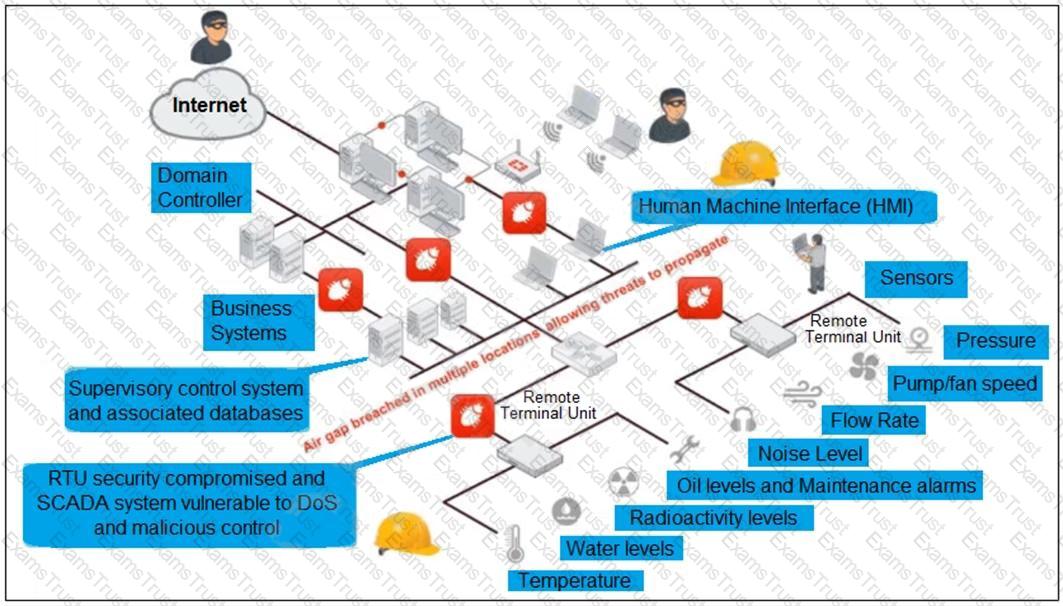
An administrator needs to implement proper protection on the OT network.
Which three steps should an administrator take to protect the OT network? (Choose three.)
What can be assigned using network access control policies?
How can you achieve remote access and internet availability in an OT network?
Which two statements are true when you deploy FortiGate as an offline IDS? (Choose two.)
An OT administrator is defining an incident notification policy using FortiSIEM and would like to configure the system with a notification policy. If an incident occurs, the administrator would like to be able to intervene and block an IP address or disable a user in Active Directory from FortiSIEM.
Which step must the administrator take to achieve this task?
Refer to the exhibit.
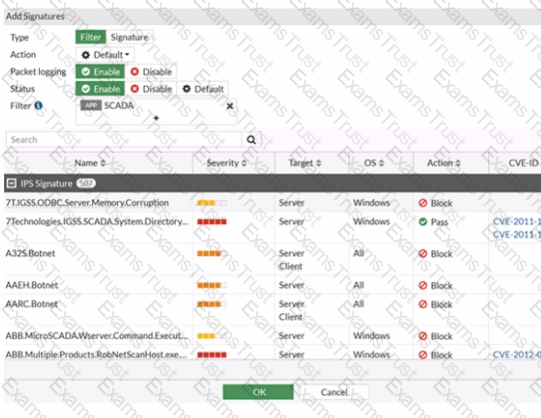
The IPS profile is added on all of the security policies on FortiGate.
For an OT network, which statement of the IPS profile is true?
What triggers Layer 2 polling of infrastructure devices connected in the network?
Refer to the exhibits.

Which statement about some of the generated report elements from FortiAnalyzer is true?
Which statement is correct about processing matched rogue devices by FortiNAC?