You are adding more spoke VPCs to an existing hub and spoke topology Your goal is to finish this task in the minimum amount of time without making errors.
Which Amazon AWS services must you subscribe to accomplish your goal?
Refer to the exhibit.
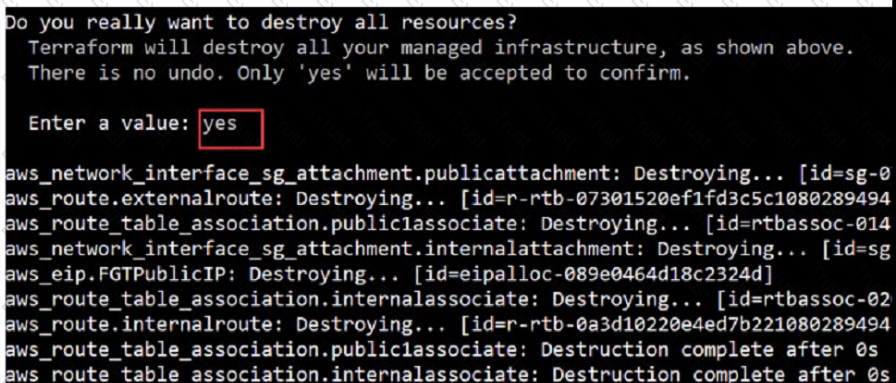
What would be the impact of confirming to delete all the resources in Terraform?
You are tasked with deploying a FortiGate HA solution in Amazon Web Services (AWS) using Terraform What are two steps you must take to complete this deployment? (Choose two.)
You are asked to find a solution to replace the existing VPC peering topology to have a higher bandwidth connection from Amazon Web Services (AWS) to the on-premises data center Which two solutions will satisfy the requirement? (Choose two.)
Refer to the exhibit
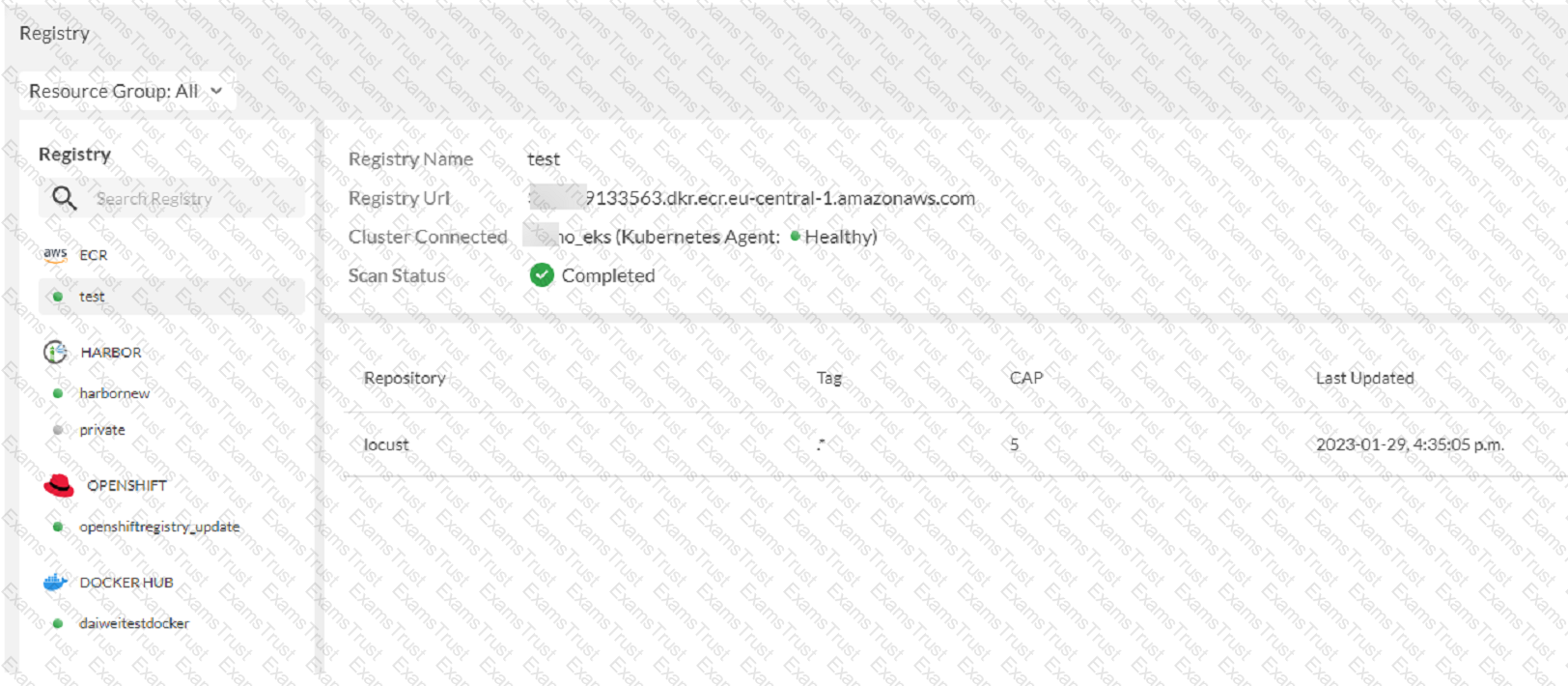
The exhibit shows the results of a FortiCNP registry scan
Which two statements are correct? (Choose two )
What are three important steps required to get Terraform ready using Microsoft Azure Cloud Shell? (Choose three.)
An administrator decides to use the Use managed identity option on the FortiGate SDN connector with Microsoft Azure However, the SDN connector is failing on the connection What must the administrator do to correct this issue?
Refer to the exhibit.
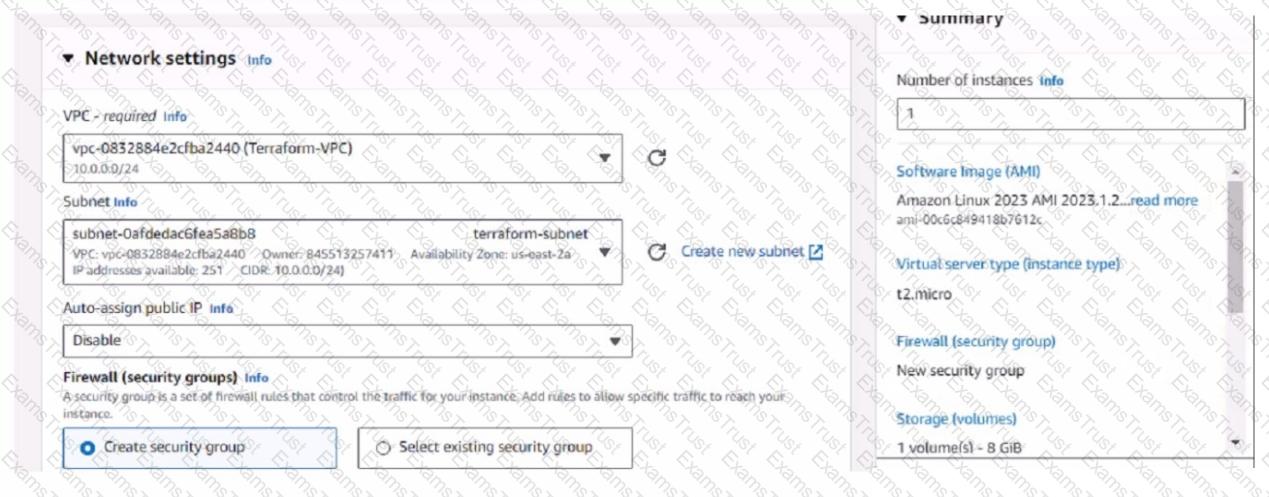
You have deployed a Linux EC2 instance in Amazon Web Services (AWS) with the settings shown on the exhibit
What next step must the administrator take to access this instance from the internet?
Which two statements are true about Transit Gateway Connect peers in anlPv4 BGP configuration'? (Choose two.)
Refer to the exhibit.
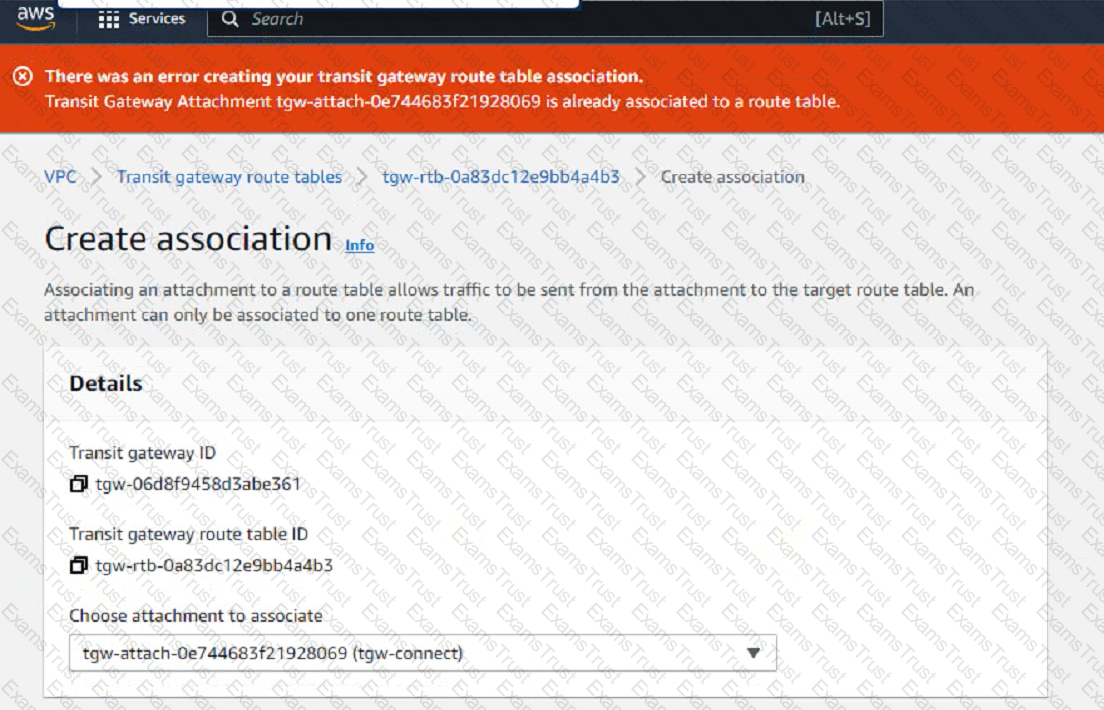
You are configuring a second route table on a Transit Gateway to accommodate east-west traffic inspection between two VPCs_ However, you are getting an error during the transit gateway route table association With the Connect attachment.
Which action Should you take to fulfill your requirement?
A Network security administrator is searching for a solution to secure traffic going in and out of the container infrastructure.
In which two ways can Fortinet container security help secure container infrastructure? (Choose two.)
You are automating configuration changes on one of the FortiGate VMS using Linux Red Hat Ansible.
How does Linux Red Hat Ansible connect to FortiGate to make the configuration change?
You must allow an SSH traffic rule in an Amazon Web Services (AWS) network access list (NACL) to allow SSH traffic to travel to a subnet for temporary testing purposes. When you review the current inbound network ACL rules, you notice that rule number 5 demes SSH and telnet traffic to the subnet
What can you do to allow SSH traffic?
What is the main advantage of using SD-WAN Transit Gateway Connect over traditional SD-WAN?
Refer to the exhibit

You deployed an HA active-passive FortiGate VM in Microsoft Azure.
Which two statements regarding this particular deployment are true? (Choose two.)
Refer to the exhibit
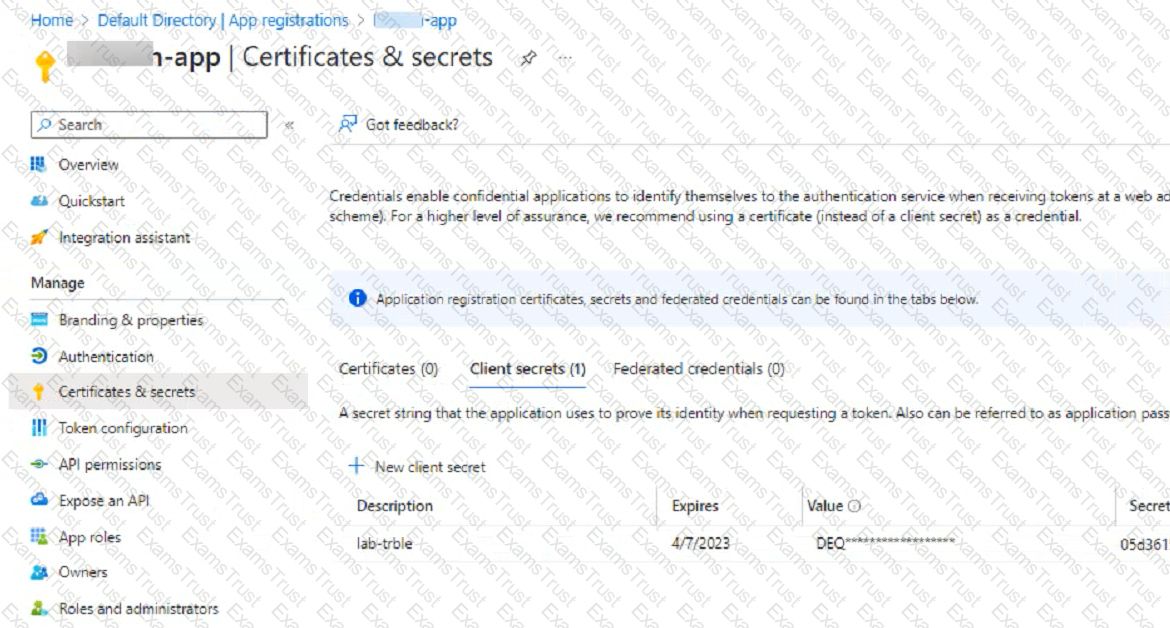
An administrator is trying to deploy a FortiGate VM in Microsoft Azure using Terraform However, during the configuration, the Azure client secret is no longer visible in the Azure portal.
How would the administrator obtain the Azure
client secret to configure on Terratorm?
In an SD-WAN TGW Connect topology, which three initial steps are mandatory when routing traffic from a spoke VPC to a security VPC through a Transit Gateway? (Choose three.)