An administrator discovers that CPU utilization of a FortiGate-200F is high and determines that no traffic is being accelerated by hardware.
Why is no traffic being accelerated by hardware?
Refer to the exhibits.
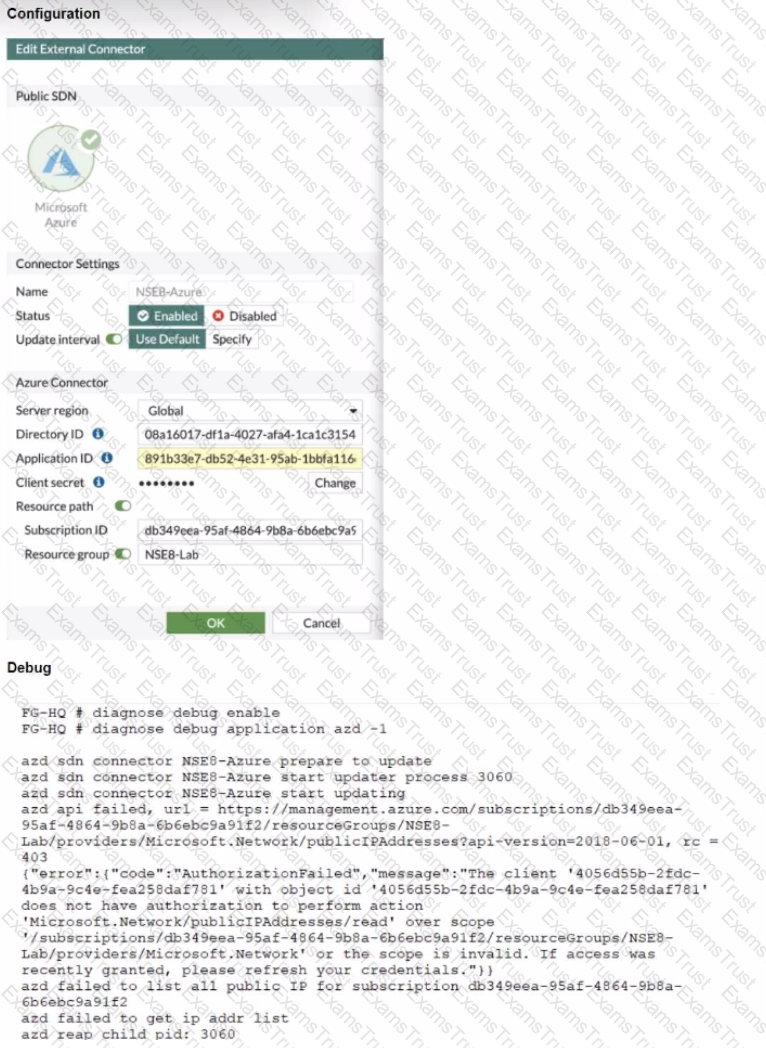
The exhibits show the configuration and debug output from a FortiGate Public SDN Connector.
What is a possible reason for this dynamic address object to be empty?
Refer to the exhibit.
FortiManager is configured with the Jinja Script under CLI Templates shown in the exhibit.
Which two statements correctly describe the expected behavior when running this template? (Choose two.)
Refer to the exhibit.
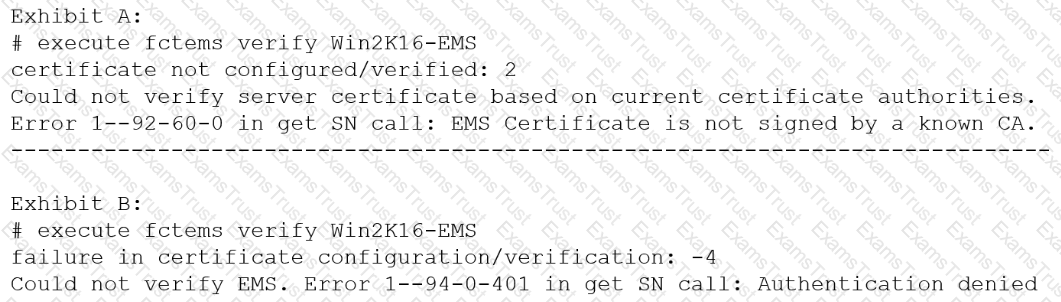
The exhibit shows two error messages from a FortiGate root Security Fabric device when you try to configure a new connection to a FortiClient EMS Server.
Referring to the exhibit, which two actions will fix these errors? (Choose two.)
Refer to the exhibit.
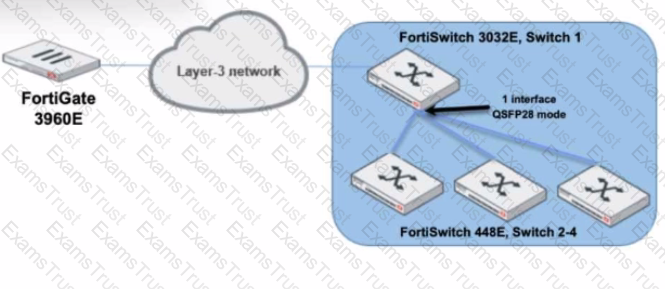
You are managing a FortiSwitch 3032E that is managed by FortiLink on a FortiGate 3960E. The 3032E is heavily utilized and there is only one port free.
The requirement is to add an additional three FortiSwitch 448E devices with 10Gbps SFP+ connectivity directly to the 3032E. The plan is to use split port (phy-mode) with QSFP28 mode to connect the new 448E switches.
In this scenario, which statement about the switch deployment is correct?
Refer to the exhibits.
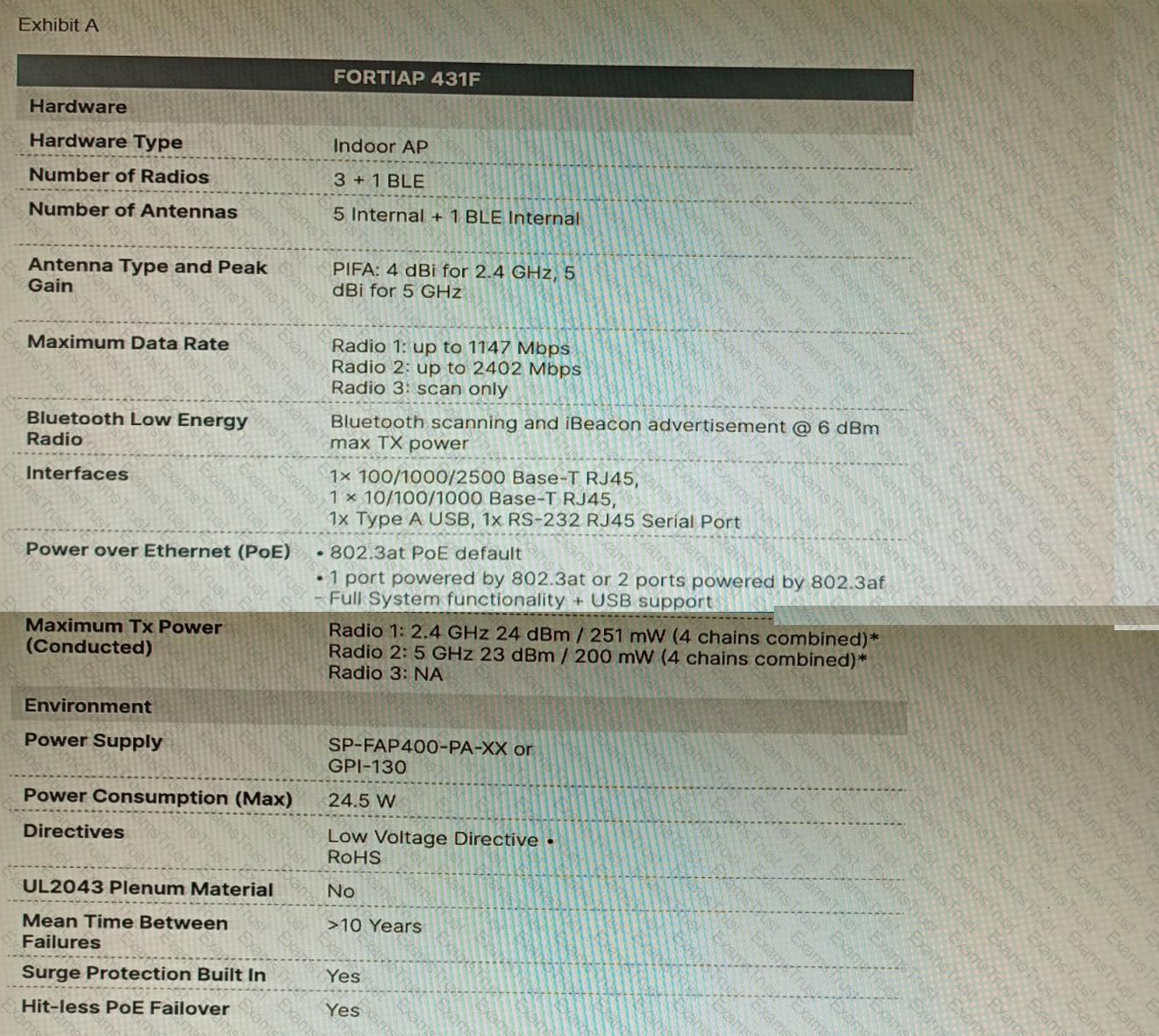
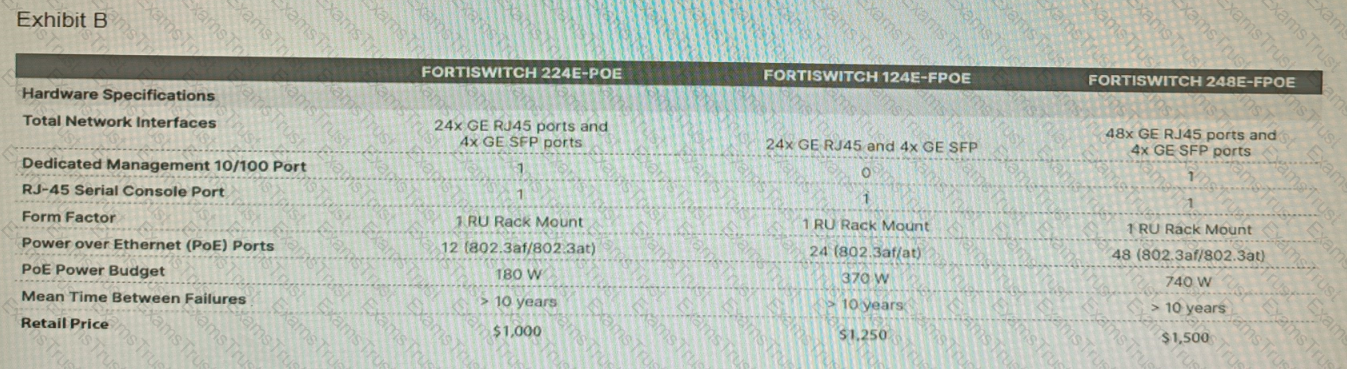
A customer wants to deploy 12 FortiAP 431F devices on high density conference center, but they do not currently have any PoE switches to connect them to. They want to be able to run them at full power while having network redundancy
From the FortiSwitch models and sample retail prices shown in the exhibit, which build of materials would have the lowest cost, while fulfilling the customer's requirements?
Refer to the exhibit showing the history logs from a FortiMail device.
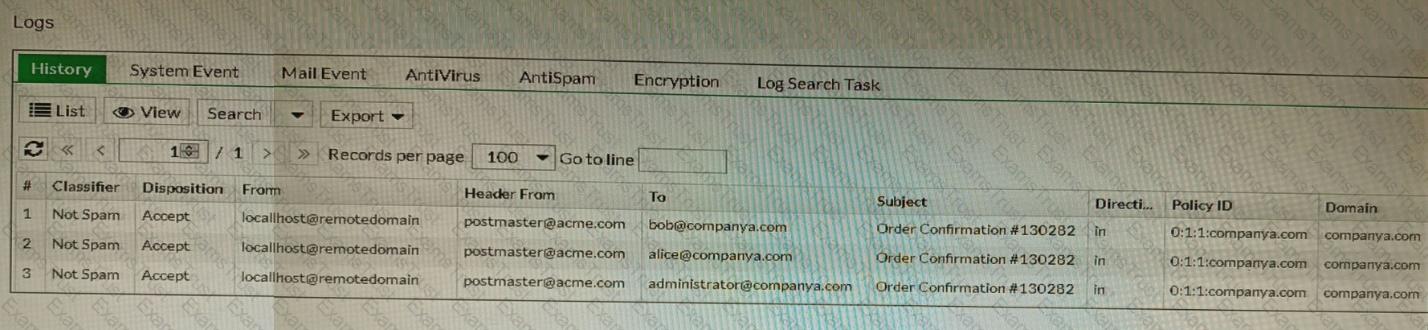
Which FortiMail email security feature can an administrator enable to treat these emails as spam?
You deployed a fully loaded FG-7121F in the data center and enabled sslvpn-load-balance. Based on the behavior of this feature which statement is correct?
Refer to the exhibits.
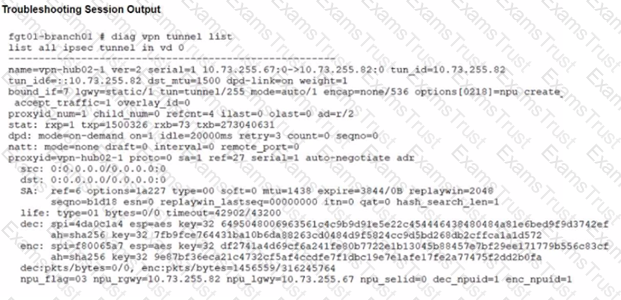
A customer is trying to restore a VPN connection configured on a FortiGate. Exhibits show output during a troubleshooting session when the VPN was working and the current baseline VPN configuration.
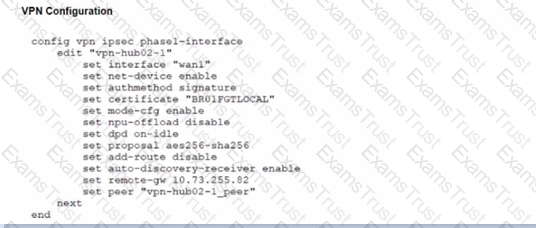
Which configuration parameters will restore VPN connectivity based on the diagnostic output?
Refer to the exhibit of a FortiNAC configuration.
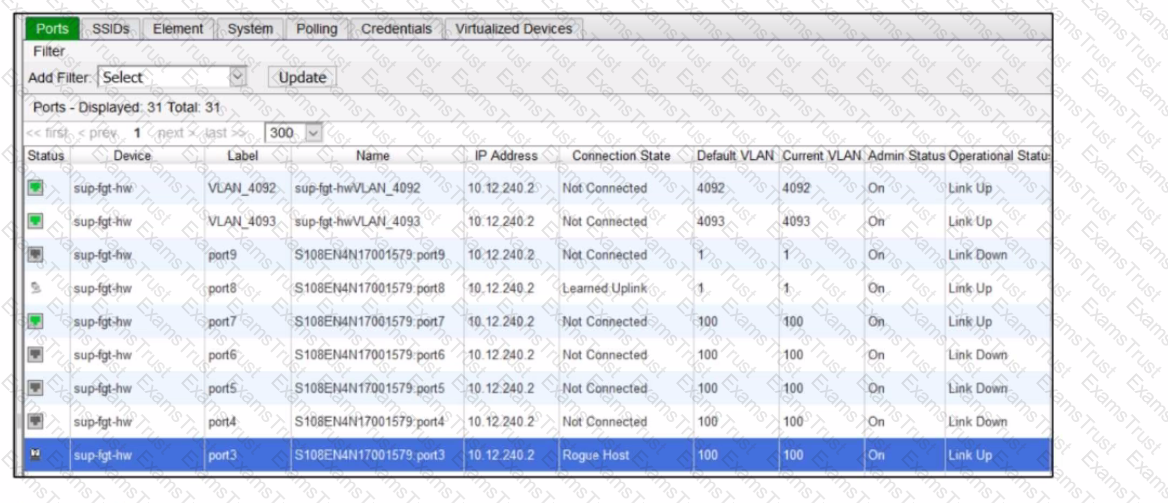
In this scenario, which two statements are correct? (Choose two.)
A customer would like to improve the performance of a FortiGate VM running in an Azure D4s_v3 instance, but they already purchased a BYOL VM04 license.
Which two actions will improve performance the most without making a FortiGate license change? (Choose two.)
Refer to the exhibit.
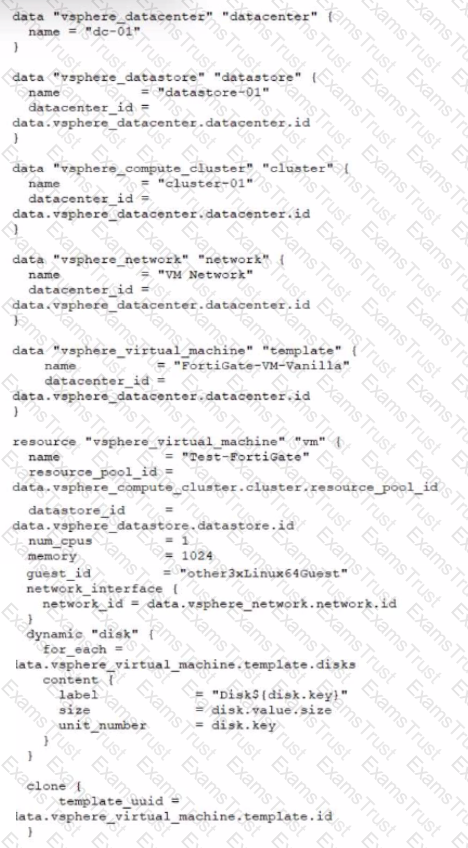
A customer wants to automate the creation and configuration of FortiGate VM instances in a VMware vCenter environment using Terraform. They have the creation part working with the code shown in the exhibit.
Which code snippet will allow Terraform to automatically connect to a newly deployed FortiGate if its IP was dynamically assigned by VMware NSX-T?
A FortiGate is configured to perform outbound firewall authentication with Azure AD as a SAML IdP.
What are two valid interactions that occur when the client attempts to access the internet? (Choose two.)
Refer to the exhibit.
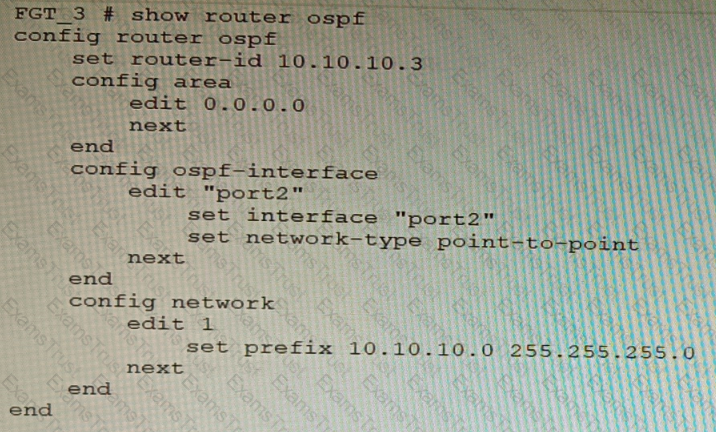
You are operating an internal network with multiple OSPF routers on the same LAN segment. FGT_3 needs to be added to the OSPF network and has the configuration shown in the exhibit. FGT_3 is not establishing any OSPF connection.
What needs to be changed to the configuration to make sure FGT_3 will establish OSPF neighbors without affecting the DR/BDR election?
A)
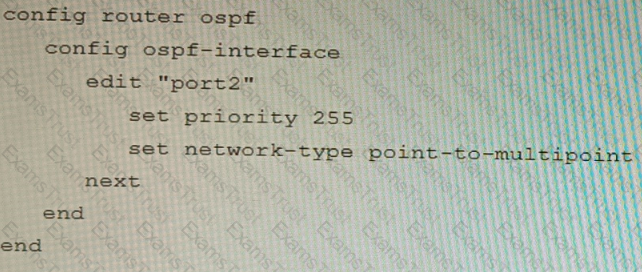
B)
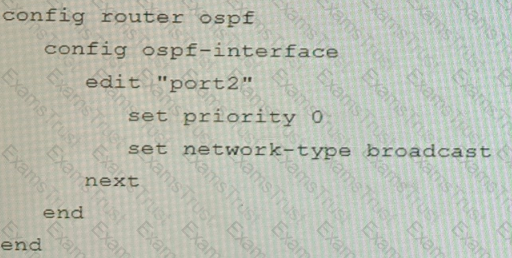
C)
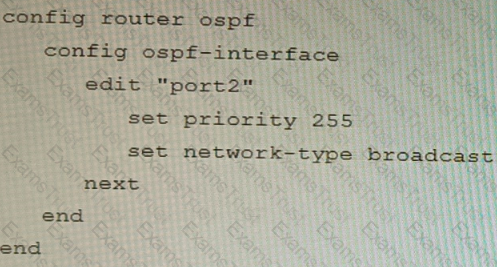
D)
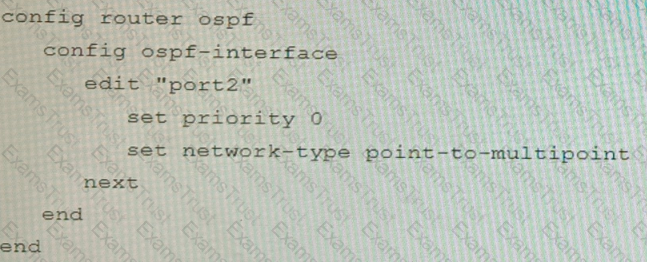
Refer to the exhibit containing the configuration snippets from the FortiGate. Customer requirements:
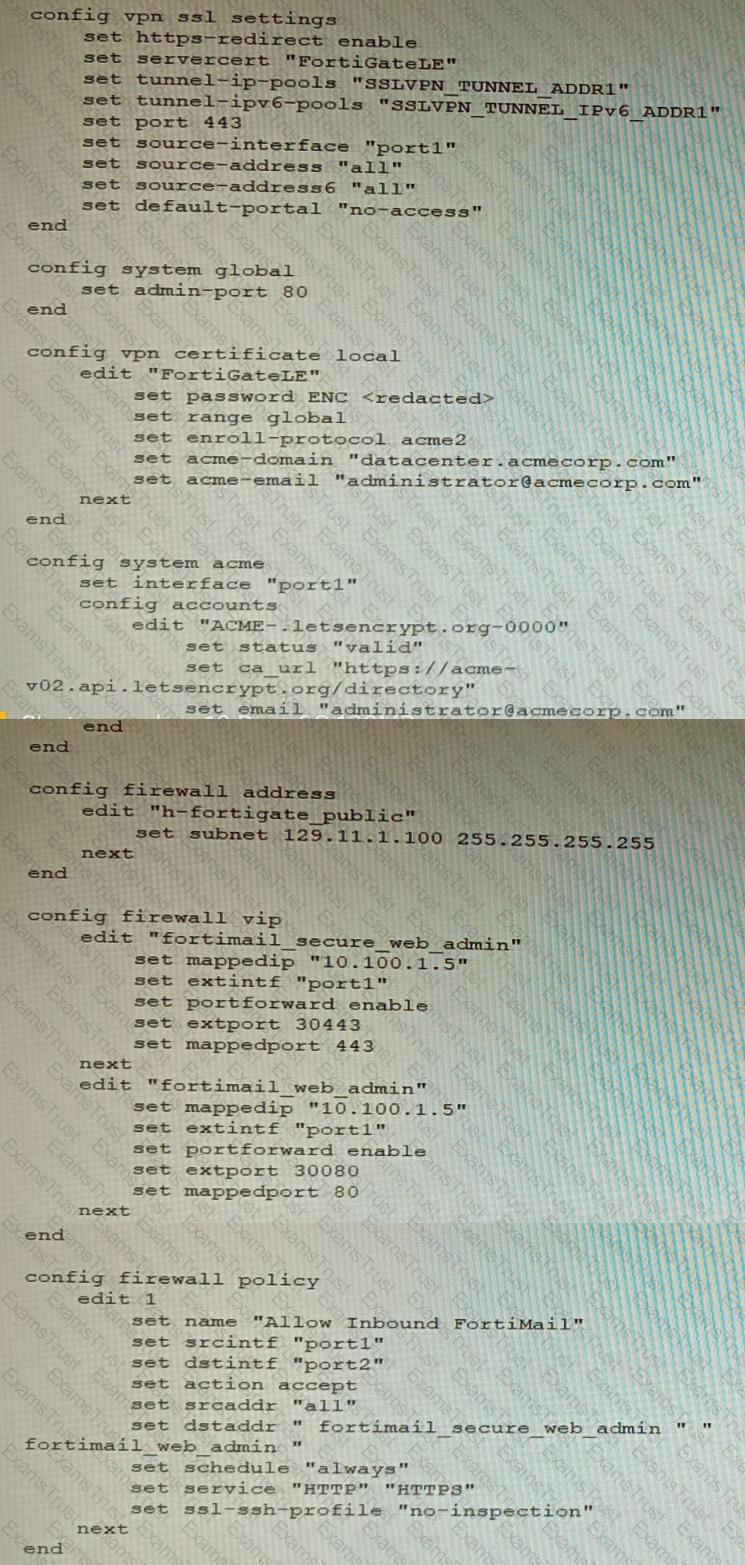
• SSLVPN Portal must be accessible on standard HTTPS port (TCP/443)
• Public IP address (129.11.1.100) is assigned to portl
• Datacenter.acmecorp.com resolves to the public IP address assigned to portl
The customer has a Let's Encrypt certificate that is going to expire soon and it reports that subsequent attempts to renew that certificate are failing.
Reviewing the requirement and the exhibit, which configuration change below will resolve this issue?
A)
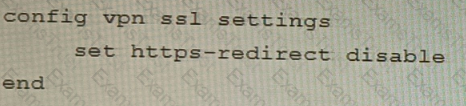
B)

C)
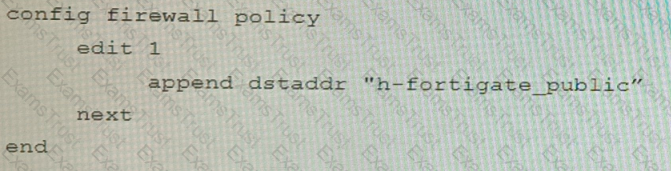
D)

Refer to The exhibit, which shows a topology diagram.
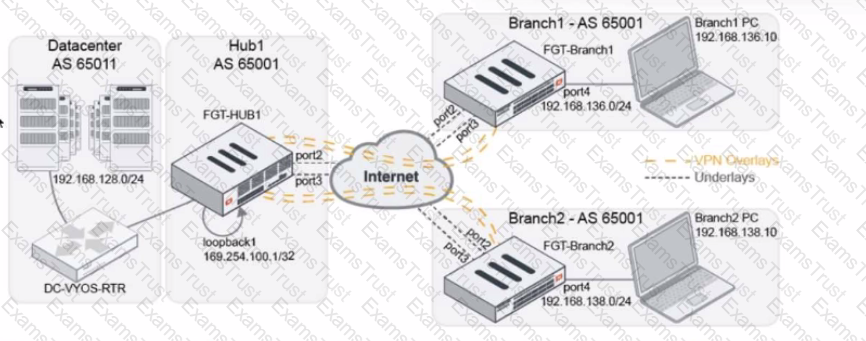
A customer wants to use SD-WAN for traffic generated from the data center towards Branches. SD-WAN on HUB should follow the underlay condition on each Branch and the solution should be scalable for hundreds of Branches.
Which SD WAN-Rules strategy should be used?
A customer with a FortiDDoS 200F protecting their fibre optic internet connection from incoming traffic sees that all the traffic was dropped by the device even though they were not under a DoS attack. The traffic flow was restored after it was rebooted using the GUI. Which two options will prevent this situation in the future? (Choose two)
You must configure an environment with dual-homed servers connected to a pair of FortiSwitch units using an MCLAG.
Multicast traffic is expected in this environment, and you should ensure unnecessary traffic is pruned from links that do not have a multicast listener.
In which two ways must you configure the igmps-f lood-traffic and igmps-flood-report settings? (Choose two.)
Refer to the exhibit.
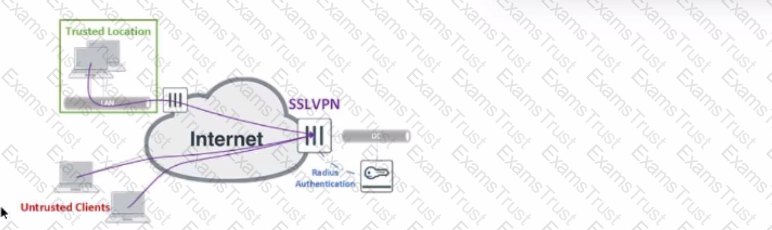
The exhibit shows the topology a customer wants to implement using a flexible authentication scheme. Users connecting from trusted remote locations are authenticated using only their username/password when connecting to the SSLVPN FortiGate in the data center.
When connecting from the Untrusted Clients, users must authenticate using 2-factor authentication.
In this scenario, which RADIUS attribute can be used as a RADIUS policy selector on the FortiAuthenticator to accomplish this goal?
Refer to the exhibit.
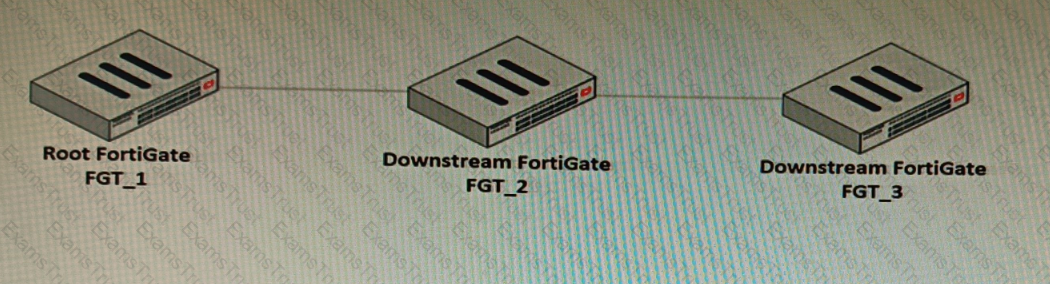
You have deployed a security fabric with three FortiGate devices as shown in the exhibit. FGT_2 has the following configuration:
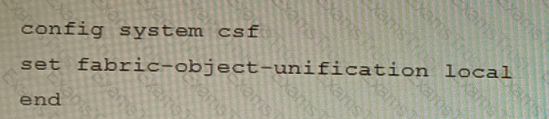
FGT_1 and FGT_3 are configured with the default setting. Which statement is true for the synchronization of fabric-objects?
Refer to the exhibit showing a FortiView monitor screen.
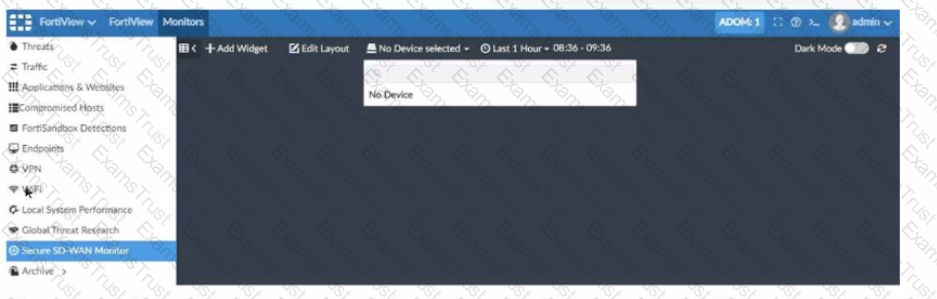
After a Secure SD-WAN implementation a customer reports that in FortiAnalyzer under FortiView Secure SD-WAN Monitor there is No Device for selection.
What can cause this issue?
SD-WAN is configured on a FortiGate. You notice that when one of the internet links has high latency the time to resolve names using DNS from FortiGate is very high.
You must ensure that the FortiGate DNS resolution times are as low as possible with the least amount of work.
What should you configure?
Refer to the exhibits.
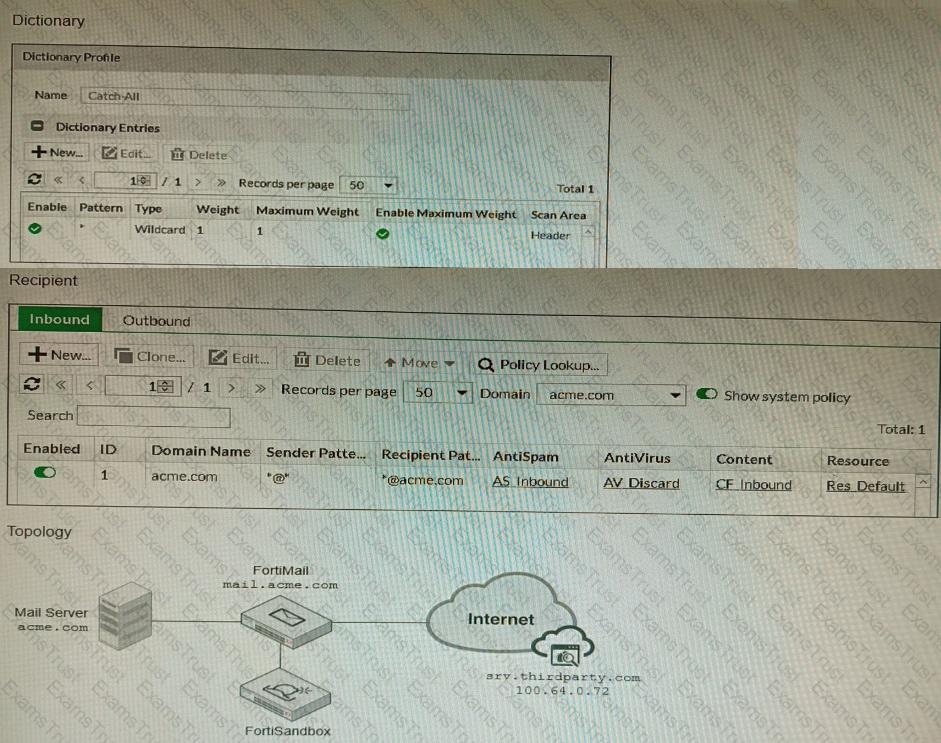
The exhibits show a FortiMail network topology, Inbound configuration settings, and a Dictionary Profile.
You are required to integrate a third-party's host service (srv.thirdparty.com) into the e-mail processing path.
All inbound e-mails must be processed by FortiMail antispam and antivirus with FortiSandbox integration. If the email is clean, FortiMail must forward it to the third-party service, which will send the email back to FortiMail for final delivery, FortiMail must not scan the e-mail again.
Which three configuration tasks must be performed to meet these requirements? (Choose three.)
You must analyze an event that happened at 20:37 UTC. One log relevant to the event is extracted from FortiGate logs:
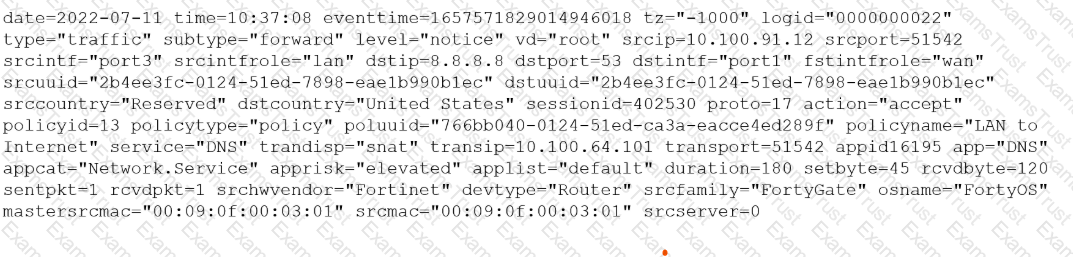
The devices and the administrator are all located in different time zones Daylight savings time (DST) is disabled
• The FortiGate is at GMT-1000.
• The FortiAnalyzer is at GMT-0800
• Your browser local time zone is at GMT-03.00
You want to review this log on FortiAnalyzer GUI, what time should you use as a filter?
Refer to the exhibits.

During the implementation of a Fortinet Security Fabric configuration, CLI commands were issued in the order shown in the exhibit. On the next day, the local admin for FGTC issues the following command:
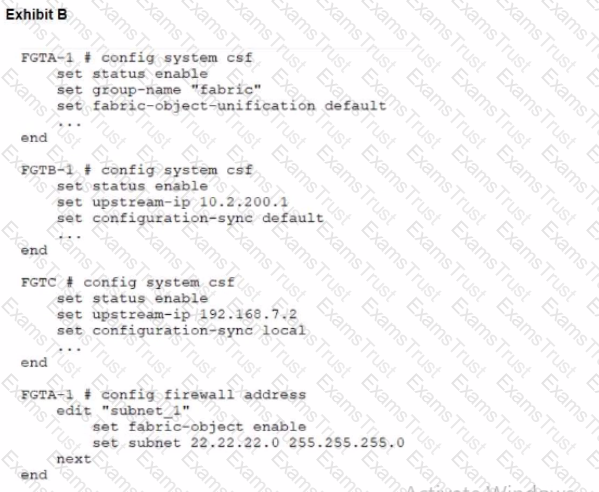
FGTC # config system csf
set configuration-sync default
end
In this scenario, which outcome is true regarding the "subnet_1" firewall address object on FGTC?
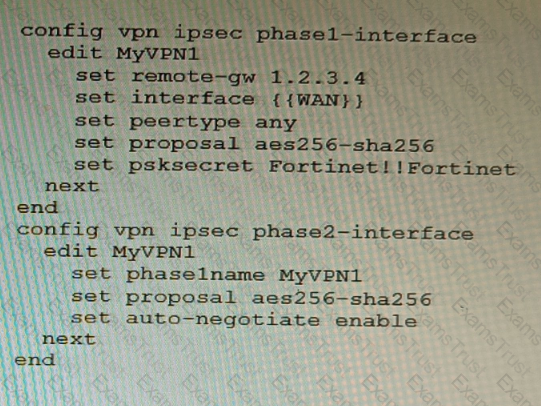
You have configured a Site-to-Site IPsec VPN tunnel between a FortiGate and a third-party device but notice that one of the error counters on the tunnel interface keeps increasing.
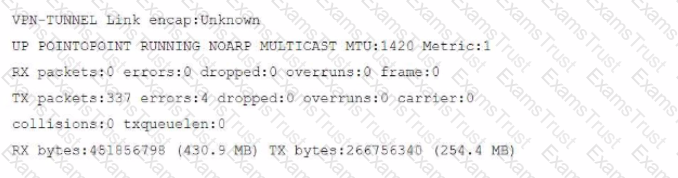
Which two configuration options can resolve this problem? (Choose two.)
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1).
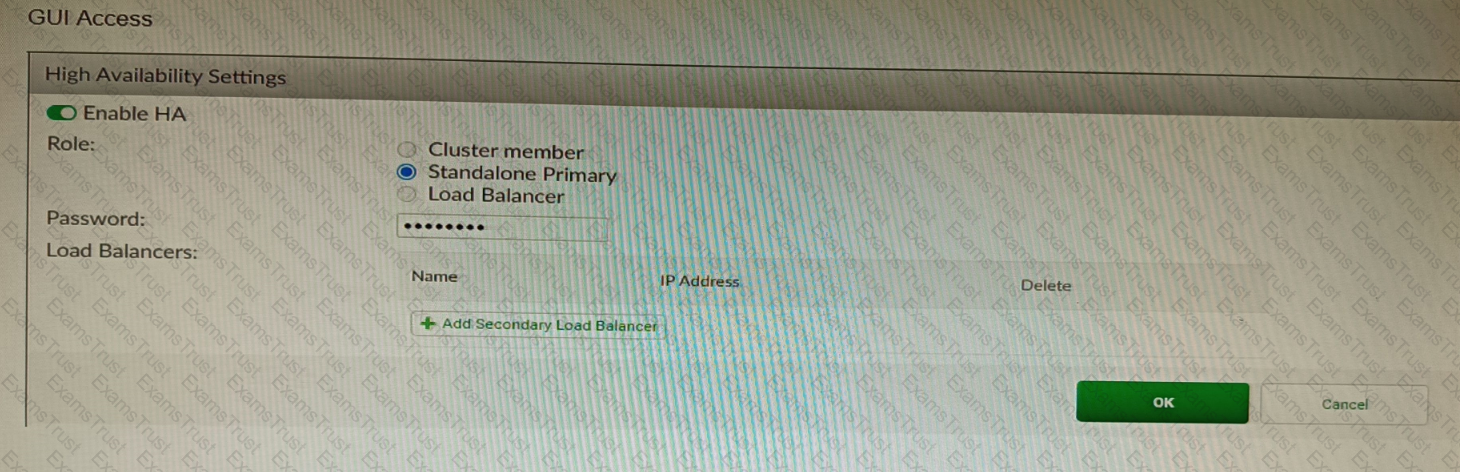
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?
A retail customer with a FortiADC HA cluster load balancing five webservers in L7 Full NAT mode is receiving reports of users not able to access their website during a sale event. But for clients that were able to connect, the website works fine.
CPU usage on the FortiADC and the web servers is low, application and database servers are still able to handle more traffic, and the bandwidth utilization is under 30%.
Which two options can resolve this situation? (Choose two.)
Refer to the CLI output:
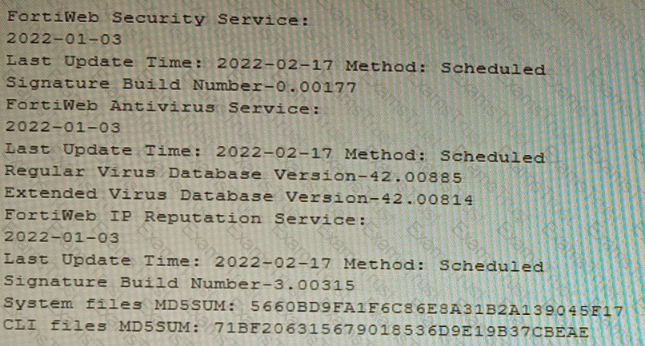
Given the information shown in the output, which two statements are correct? (Choose two.)
You are running a diagnose command continuously as traffic flows through a platform with NP6 and you obtain the following output:
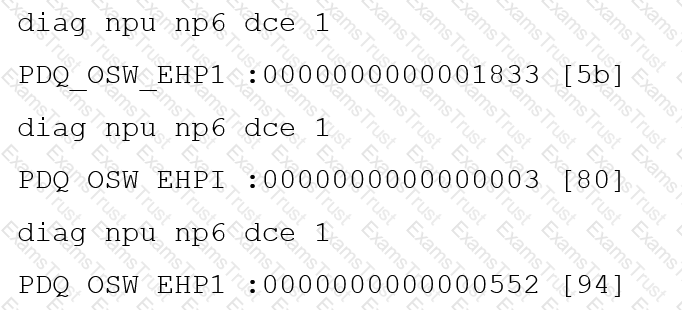
Given the information shown in the output, which two statements are true? (Choose two.)
Refer to the exhibits.
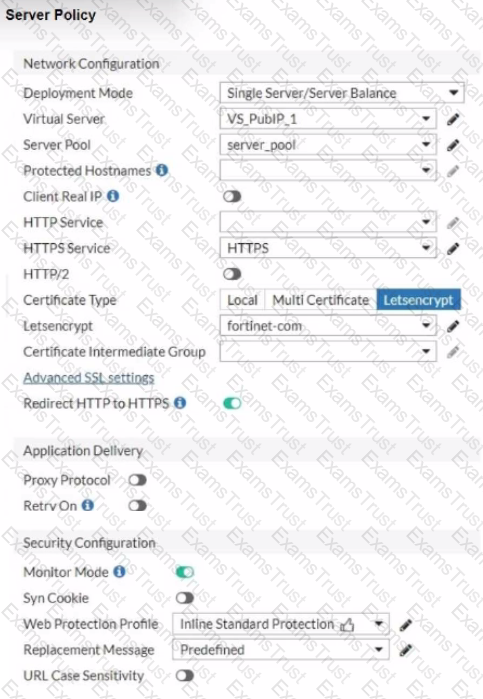
You are configuring a Let's Encrypt certificate to enable SSL protection to your website. When FortiWeb tries to retrieve the certificate, you receive a certificate status failed, as shown below.

Based on the Server Policy settings shown in the exhibit, which two configuration changes will resolve this issue? (Choose two.)