You are logged in as a local admin on a Windows 7 system and you need to launch the Computer Management Console from command line.
Which command would you use?
> NMAP -sn 192.168.11.200-215
The NMAP command above performs which of the following?
Which of the following is the least-likely physical characteristic to be used in biometric control that supports a large company?
Which of the following is the successor of SSL?
Jesse receives an email with an attachment labeled “Court_Notice_21206.zip”. Inside the zip file is a file named “Court_Notice_21206.docx.exe” disguised as a word document. Upon execution, a window appears stating, “This word document is corrupt.” In the background, the file copies itself to Jesse APPDATA\local directory and begins to beacon to a C2 server to download additional malicious binaries.
What type of malware has Jesse encountered?
You are tasked to perform a penetration test. While you are performing information gathering, you find an employee list in Google. You find the receptionist's email, and you send her an email changing the source email to her boss's email( boss@company ). In this email, you ask for a pdf with information. She reads your email and sends back a pdf with links. You exchange the pdf links with your malicious links (these links contain malware) and send back the modified pdf, saying that the links don't work. She reads your email, opens the links, and her machine gets infected. You now have access to the company network.
What testing method did you use?
The purpose of a __________ is to deny network access to local area networks and other information assets by unauthorized wireless devices.
When you are testing a web application, it is very useful to employ a proxy tool to save every request and response. You can manually test every request and analyze the response to find vulnerabilities. You can test parameter and headers manually to get more precise results than if using web vulnerability scanners.
What proxy tool will help you find web vulnerabilities?
You've gained physical access to a Windows 2008 R2 server which has an accessible disc drive. When you attempt to boot the server and log in, you are unable to guess the password. In your tool kit you have an Ubuntu 9.10 Linux LiveCD. Which Linux based tool has the ability to change any user's password or to activate disabled Windows accounts?
Which of the following statements is TRUE?
This tool is an 802.11 WEP and WPA-PSK keys cracking program that can recover keys once enough data packets have been captured. It implements the standard FMS attack along with some optimizations like KoreK attacks, as well as the PTW attack, thus making the attack much faster compared to other WEP cracking tools.
Which of the following tools is being described?
As a Certified Ethical Hacker, you were contracted by a private firm to conduct an external security assessment through penetration testing.
What document describes the specifics of the testing, the associated violations, and essentially protects both the organization's interest and your liabilities as a tester?
You have successfully compromised a machine on the network and found a server that is alive on the same network. You tried to ping it but you didn't get any response back.
What is happening?
Which of the following is the structure designed to verify and authenticate the identity of individuals within the enterprise taking part in a data exchange?
Which of the following is a design pattern based on distinct pieces of software providing application functionality as services to other applications?
How does the Address Resolution Protocol (ARP) work?
A distributed port scan operates by:
You’ve just gained root access to a Centos 6 server after days of trying. What tool should you use to maintain access?
One of the Forbes 500 companies has been subjected to a large scale attack. You are one of the shortlisted pen testers that they may hire. During the interview with the CIO, he emphasized that he wants to totally eliminate all risks. What is one of the first things you should do when hired?
Destination unreachable administratively prohibited messages can inform the hacker to what?
What is the best Nmap command to use when you want to list all devices in the same network quickly after you successfully identified a server whose IP address is 10.10.0.5?
Why would an attacker want to perform a scan on port 137?
A company recently hired your team of Ethical Hackers to test the security of their network systems. The company wants to have the attack be as realistic as possible. They did not provide any information besides the name of their company. What phase of security testing would your team jump in right away?
You have initiated an active operating system fingerprinting attempt with nmap against a target system:
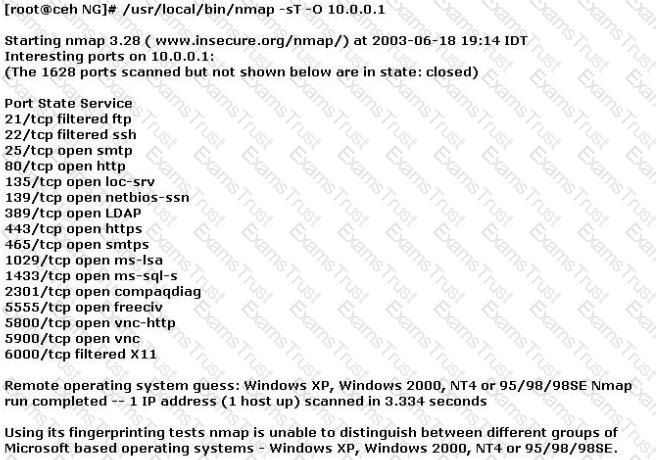
What operating system is the target host running based on the open ports shown above?
Jack was attempting to fingerprint all machines in the network using the following Nmap syntax:
invictus@victim_server:~$ nmap -T4 -0 10.10.0.0/24
TCP/IP fingerprinting (for OS scan) xxxxxxx xxxxxx xxxxxxxxx. QUITTING!
Obviously, it is not going through. What is the issue here?
As an Ethical Hacker you are capturing traffic from your customer network with Wireshark and you need to find and verify just SMTP traffic. What command in Wireshark will help you to find this kind of traffic?
SNMP is a protocol used to query hosts, servers, and devices about performance or health status data. This protocol has long been used by hackers to gather great amount of information about remote hosts. Which of the following features makes this possible? (Choose two.)
What are two things that are possible when scanning UDP ports? (Choose two.)
Which Type of scan sends a packets with no flags set?
The practical realities facing organizations today make risk response strategies essential. Which of the following is NOT one of the five basic responses to risk?
If you are to determine the attack surface of an organization, which of the following is the BEST thing to do?
Shellshock had the potential for an unauthorized user to gain access to a server. It affected many internet-facing services, which OS did it not directly affect?
International Organization for Standardization (ISO) standard 27002 provides guidance for compliance by outlining
An attacker has captured a target file that is encrypted with public key cryptography. Which of the attacks below is likely to be used to crack the target file?
Which cipher encrypts the plain text digit (bit or byte) one by one?
Which of the following is optimized for confidential communications, such as bidirectional voice and video?
Which of the following network attacks takes advantage of weaknesses in the fragment reassembly functionality of the TCP/IP protocol stack?
SOAP services use which technology to format information?
Which of the following processes of PKI (Public Key Infrastructure) ensures that a trust relationship exists and that a certificate is still valid for specific operations?
Which of the following network attacks relies on sending an abnormally large packet size that exceeds TCP/IP specifications?
The intrusion detection system at a software development company suddenly generates multiple alerts regarding attacks against the company's external webserver, VPN concentrator, and DNS servers. What should the security team do to determine which alerts to check first?
If a tester is attempting to ping a target that exists but receives no response or a response that states the destination is unreachable, ICMP may be disabled and the network may be using TCP. Which other option could the tester use to get a response from a host using TCP?
Which of the following descriptions is true about a static NAT?
Which of the following guidelines or standards is associated with the credit card industry?
Which of the following defines the role of a root Certificate Authority (CA) in a Public Key Infrastructure (PKI)?
Which initial procedure should an ethical hacker perform after being brought into an organization?
Which Open Web Application Security Project (OWASP) implements a web application full of known vulnerabilities?
The Open Web Application Security Project (OWASP) testing methodology addresses the need to secure web applications by providing which one of the following services?
What is the purpose of DNS AAAA record?
This is an attack that takes advantage of a web site vulnerability in which the site displays content that includes un-sanitized user-provided data.

What is this attack?
Which of the following tools are used for enumeration? (Choose three.)
Why would you consider sending an email to an address that you know does not exist within the company you are performing a Penetration Test for?
What port number is used by LDAP protocol?
Peter, a Network Administrator, has come to you looking for advice on a tool that would help him perform SNMP enquires over the network.
Which of these tools would do the SNMP enumeration he is looking for? Select the best answers.
John is an incident handler at a financial institution. His steps in a recent incident are not up to the standards of the company. John frequently forgets some steps and procedures while handling responses as they are very stressful to perform. Which of the following actions should John take to overcome this problem with the least administrative effort?
Within the context of Computer Security, which of the following statements describes Social Engineering best?
Every company needs a formal written document which spells out to employees precisely what they are allowed to use the company's systems for, what is prohibited, and what will happen to them if they break the rules. Two printed copies of the policy should be given to every employee as soon as possible after they join the organization. The employee should be asked to sign one copy, which should be safely filed by the company. No one should be allowed to use the company's computer systems until they have signed the policy in acceptance of its terms.
What is this document called?
Bob is acknowledged as a hacker of repute and is popular among visitors of "underground" sites.
Bob is willing to share his knowledge with those who are willing to learn, and many have expressed their interest in learning from him. However, this knowledge has a risk associated with it, as it can be used for malevolent attacks as well.
In this context, what would be the most effective method to bridge the knowledge gap between the "black" hats or crackers and the "white" hats or computer security professionals? (Choose the test answer.)
What hacking attack is challenge/response authentication used to prevent?
An LDAP directory can be used to store information similar to a SQL database. LDAP uses a _____ database structure instead of SQL’s _____ structure. Because of this, LDAP has difficulty representing many-to-one relationships.
Matthew, a black hat, has managed to open a meterpreter session to one of the kiosk machines in Evil Corp’s lobby. He checks his current SID, which is S-1-5-21-1223352397-1872883824-861252104-501. What needs to happen before Matthew has full administrator access?
What is GINA?
As a securing consultant, what are some of the things you would recommend to a company to ensure DNS security?
Let's imagine three companies (A, B and C), all competing in a challenging global environment. Company A and B are working together in developing a product that will generate a major competitive advantage for them. Company A has a secure DNS server while company B has a DNS server vulnerable to spoofing. With a spoofing attack on the DNS server of company B, company C gains access to outgoing e-mails from company B. How do you prevent DNS spoofing?
Which of the following open source tools would be the best choice to scan a network for potential targets?
Which of the following describes the characteristics of a Boot Sector Virus?
Bluetooth uses which digital modulation technique to exchange information between paired devices?
A hacker was able to sniff packets on a company's wireless network. The following information was discovered:
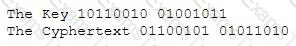
Using the Exlcusive OR, what was the original message?
ICMP ping and ping sweeps are used to check for active systems and to check
A company has five different subnets: 192.168.1.0, 192.168.2.0, 192.168.3.0, 192.168.4.0 and 192.168.5.0. How can NMAP be used to scan these adjacent Class C networks?
Which of the following is a hardware requirement that either an IDS/IPS system or a proxy server must have in order to properly function?
What is the main reason the use of a stored biometric is vulnerable to an attack?
What is the most secure way to mitigate the theft of corporate information from a laptop that was left in a hotel room?
Which of the following identifies the three modes in which Snort can be configured to run?
Which property ensures that a hash function will not produce the same hashed value for two different messages?
Which tool can be used to silently copy files from USB devices?
At a Windows Server command prompt, which command could be used to list the running services?
A penetration tester is hired to do a risk assessment of a company's DMZ. The rules of engagement states that the penetration test be done from an external IP address with no prior knowledge of the internal IT systems. What kind of test is being performed?
A hacker is attempting to use nslookup to query Domain Name Service (DNS). The hacker uses the nslookup interactive mode for the search. Which command should the hacker type into the command shell to request the appropriate records?
Which solution can be used to emulate computer services, such as mail and ftp, and to capture information related to logins or actions?
Alice encrypts her data using her public key PK and stores the encrypted data in the cloud. Which of the following attack scenarios will compromise the privacy of her data?
Company XYZ has asked you to assess the security of their perimeter email gateway. From your office in New York, you craft a specially formatted email message and send it across the Internet to an employee of Company XYZ. The employee of Company XYZ is aware of your test.
Your email message looks like this:
From: jim_miller@companyxyz.com
To: michelle_saunders@companyxyz.com
Subject: Test message
Date: 4/3/2017 14:37
The employee of Company XYZ receives your email message. This proves that Company XYZ's email gateway doesn't prevent what?
Email is transmitted across the Internet using the Simple Mail Transport Protocol. SMTP does not encrypt email, leaving the information in the message vulnerable to being read by an unauthorized person. SMTP can upgrade a connection between two mail servers to use TLS. Email transmitted by SMTP over TLS is encrypted. What is the name of the command used by SMTP to transmit email over TLS?
If an attacker uses the command SELECT*FROM user WHERE name = ‘x’ AND userid IS NULL; --‘; which type of SQL injection attack is the attacker performing?
Which Nmap option would you use if you were not concerned about being detected and wanted to perform a very fast scan?
The collection of potentially actionable, overt, and publicly available information is known as
When tuning security alerts, what is the best approach?
Which of the following is considered as one of the most reliable forms of TCP scanning?
Code injection is a form of attack in which a malicious user:
What would you enter, if you wanted to perform a stealth scan using Nmap?
A hacker named Jack is trying to compromise a bank’s computer system. He needs to know the operating system of that computer to launch further attacks.
What process would help him?
Nedved is an IT Security Manager of a bank in his country. One day. he found out that there is a security breach to his company's email server based on analysis of a suspicious connection from the email server to an unknown IP Address.
What is the first thing that Nedved needs to do before contacting the incident response team?
Which of the following Bluetooth hacking techniques does an attacker use to send messages to users without the recipient’s consent, similar to email spamming?
Your business has decided to add credit card numbers to the data it backs up to tape. Which of the
following represents the best practice your business should observe?
Which of the following steps for risk assessment methodology refers to vulnerability identification?
You are the Network Admin, and you get a compliant that some of the websites are no longer accessible. You try to ping the servers and find them to be reachable. Then you type the IP address and then you try on the browser, and find it to be accessible. But they are not accessible when you try using the URL.
What may be the problem?
What mechanism in Windows prevents a user from accidentally executing a potentially malicious batch (.bat) or PowerShell (.ps1) script?
_________ is a set of extensions to DNS that provide to DNS clients (resolvers) origin authentication of DNS data to reduce the threat of DNS poisoning, spoofing, and similar attacks types.
The "white box testing" methodology enforces what kind of restriction?
The security concept of "separation of duties" is most similar to the operation of which type of security device?
An attacker with access to the inside network of a small company launches a successful STP manipulation attack. What will he do next?
Bob learned that his username and password for a popular game has been compromised. He contacts the company and resets all the information. The company suggests he use two-factor authentication, which option below offers that?
The network in ABC company is using the network address 192.168.1.64 with mask 255.255.255.192. In the network the servers are in the addresses 192.168.1.122, 192.168.1.123 and 192.168.1.124.
An attacker is trying to find those servers but he cannot see them in his scanning. The command he is using is:
nmap 192.168.1.64/28.
Why he cannot see the servers?
A penetration test was done at a company. After the test, a report was written and given to the company's IT authorities. A section from the report is shown below:
According to the section from the report, which of the following choice is true?
Which of the following is a protocol specifically designed for transporting event messages?
Attempting an injection attack on a web server based on responses to True/False questions is called which of the following?
Which Intrusion Detection System is best applicable for large environments where critical assets on the network need extra security and is ideal for observing sensitive network segments?
A company's Web development team has become aware of a certain type of security vulnerability in their Web software. To mitigate the possibility of this vulnerability being exploited, the team wants to modify the software requirements to disallow users from entering HTML as input into their Web application.
What kind of Web application vulnerability likely exists in their software?
A company's security policy states that all Web browsers must automatically delete their HTTP browser cookies upon terminating. What sort of security breach is this policy attempting to mitigate?
To determine if a software program properly handles a wide range of invalid input, a form of automated testing can be used to randomly generate invalid input in an attempt to crash the program.
What term is commonly used when referring to this type of testing?