A company is implementing HPE Aruba Networking Wireless IDS/IPS (WIDS/WIPS) on its AOS-10 APs, which are managed in HPE Aruba Networking Central.
What is one requirement for enabling detection of rogue APs?
A company needs you to integrate HPE Aruba Networking ClearPass Policy Manager (CPPM) with HPE Aruba Networking ClearPass Device Insight (CPDI).
What is one task you should do to prepare?
You are setting up HPE Aruba Networking SSE to detect threats as remote users browse the internet.
What is part of this process?
Refer to the exhibit:
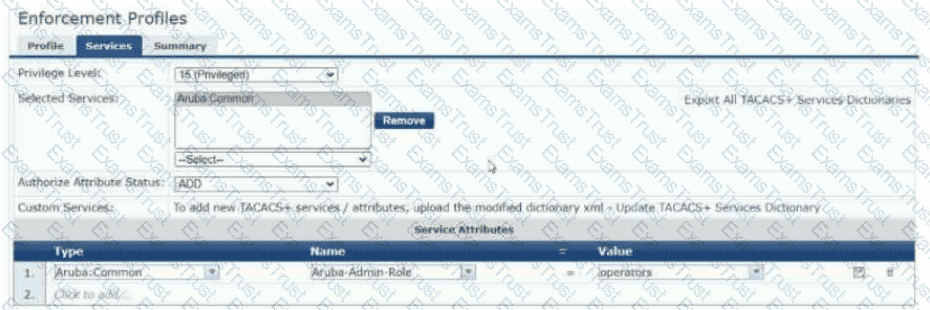
The exhibit shows the TACACS+ enforcement profile that HPE Aruba Networking ClearPass Policy Manager (CPPM) assigns to a manager. When this manager logs into an AOS-CX switch, what does the switch do?
As part of setting up an HPE Aruba Networking ClearPass Onboard solution for wireless clients, you created Network Settings, a Configuration Profile, and a Provisioning Settings object in ClearPass Onboard. You also ran the ClearPass Onboard Service Only Template on ClearPass Policy Manager (CPPM).
You now need to ensure that only domain users are authenticated and allowed to log into the ClearPass Onboard portal.
Which component should you edit?
What is one use case for implementing user-based tunneling (UBT) on AOS-CX switches?
You need to create a rule in an HPE Aruba Networking ClearPass Policy Manager (CPPM) role mapping policy that references a ClearPass Device Insight Tag. Which Type (namespace) should you specify for the rule?
A company has AOS-CX switches and HPE Aruba Networking ClearPass Policy Manager (CPPM). The company wants switches to implement 802.1X
authentication to CPPM and download user roles.
What is one task that you must complete on the switches to support this use case?
What is one benefit of integrating HPE Aruba Networking ClearPass Policy Manager (CPPM) with third-party solutions such as Mobility Device Management (MDM) and firewalls?
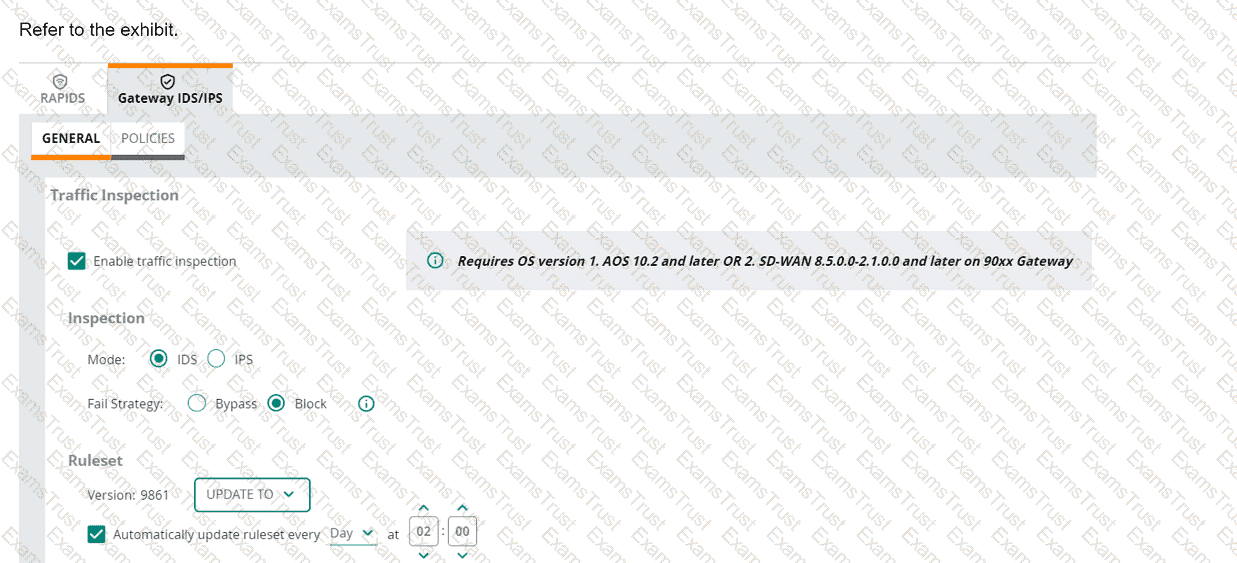
(Note that the HPE Aruba Networking Central interface shown here might look slightly different from what you see in your HPE Aruba Networking Central
interface as versions change; however, similar concepts continue to apply.)
An HPE Aruba Networking 9x00 gateway is part of an HPE Aruba Networking Central group that has the settings shown in the exhibit. What would cause the
gateway to drop traffic as part of its IDPS settings?
You are setting up an HPE Aruba Networking VIA solution for a company. You have already created a VPN pool with IP addresses for the remote clients. During
tests, however, the clients do not receive IP addresses from that pool.
What is one setting to check?
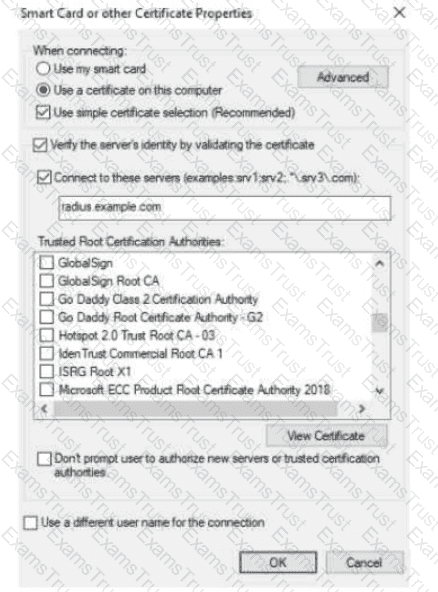
The exhibit shows the 802.1X-related settings for Windows domain clients. What should admins change to make the settings follow best security practices?

You have downloaded a packet capture that you generated on HPE Aruba Networking Central. When you open the capture in Wireshark, you see the output shown in the
exhibit.
What should you do in Wireshark so that you can better interpret the packets?
Which issue can an HPE Aruba Networking Secure Web Gateway (SWG) solution help customers address?
You have run an Active Endpoint Security Report on HPE Aruba Networking ClearPass. The report indicates that hundreds of endpoints have MAC addresses but
no known IP addresses.
What is one step for addressing this issue?
A company wants you to create a custom device fingerprint on CPPM with rules for profiling a group of specialized devices. What is one requirement?
A company wants HPE Aruba Networking ClearPass Policy Manager (CPPM) to periodically poll Microsoft Endpoint Manager (formerly Intune) for attributes about its managed clients.
What should you do on ClearPass to permit this integration?
A company has a variety of HPE Aruba Networking solutions, including an HPE Aruba Networking infrastructure and HPE Aruba Networking ClearPass Policy Manager (CPPM). The company passes traffic from the corporate LAN destined to the data center through a third-party SRX firewall. The company would like to further protect itself from internal threats. What is one solution that you can recommend?
You are establishing a cluster of HPE Aruba Networking ClearPass servers. (Assume that they are running version 6.9.).
For which type of certificate is it recommended to install a CA-signed certificate on the Subscriber before it joins the cluster?
A company has HPE Aruba Networking infrastructure devices. The devices authenticate clients to HPE Aruba Networking ClearPass Policy Manager (CPPM). You want CPPM to track information about clients, such as their IP addresses and their network bandwidth utilization. What should you set up on the network infrastructure devices to help that happen?
A company wants to implement Virtual Network based Tunneling (VNBT) on a particular group of users and assign those users to an overlay network with VNI
3000.
Assume that an AOS-CX switch is already set up to:
. Implement 802.1X to HPE Aruba Networking ClearPass Policy Manager (CPPM)
. Participate in an EVPN VXLAN solution that includes VNI 3000
Which setting should you configure in the users' AOS-CX role to apply VNBT to them when they connect?
You manage AOS-10 APs with HPE Aruba Networking Central. A role is configured on these APs with these rules (in order):
Allow UDP on port 67 to any destination
Allow any to network 10.1.4.0/23
Deny any to network 10.1.0.0/18 + log
Deny any to network 10.0.0.0/8
Allow any to any destination
You add this new rule immediately before rule 4:
Deny SSH to network 10.1.0.0/21 + denylist
After this change, what happens when a client assigned to this role sends SSH traffic to 10.1.7.12?
A company is implementing a client-to-site VPN based on tunnel-mode IPsec.
Which devices are responsible for the IPsec encapsulation?
Your company wants to implement Tunneled EAP (TEAP).
How can you set up HPE Aruba Networking ClearPass Policy Manager (CPPM) to enforce certificated-based authentication for clients using TEAP?
A company uses HPE Aruba Networking ClearPass Policy Manager (CPPM) as a TACACS+ server to authenticate managers on its AOS-CX switches. The company wants CPPM to control which commands managers are allowed to enter.
Which service must you add to the managers' TACACS+ enforcement profile?
A company has HPE Aruba Networking APs and AOS-CX switches, as well as HPE Aruba Networking ClearPass. The company wants CPPM to have HTTP User-
Agent strings to use in profiling devices.
What can you do to support these requirements?
The following firewall role is configured on HPE Aruba Networking Central-managed APs:
wlan access-rule employees
index 3
rule any any match 17 67 67 permit
rule any any match any 53 53 permit
rule 10 5 5.0 255.255 255.0 match any any any deny
rule 10.5 0.0 255.255 0.0 match 6 80 80 permit
rule 10.5 0.0 255.255.0.0 match 6 443 443 permit
rule 10.5.0.0 255.255.0.0 match any any any deny
rule any any match any any any permit
A client has authenticated and been assigned to the employees role. The client has IP address 10.2.2.2. Which correctly describes behavior in this policy?
Refer to Exhibit:
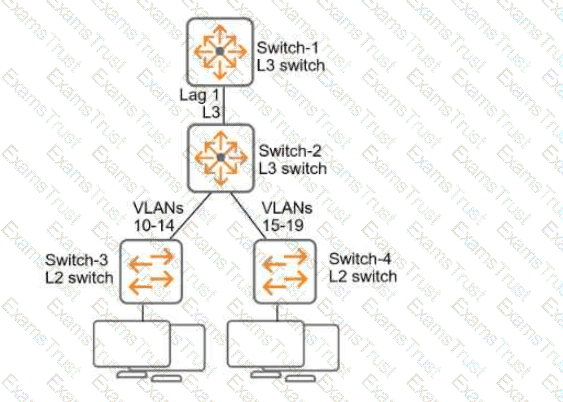
All of the switches in the exhibit are AOS-CX switches.
What is the preferred configuration on Switch-2 for preventing rogue OSPF routers in this network?
You are using OpenSSL to obtain a certificate signed by a Certification Authority (CA). You have entered this command:
openssl req -new -out file1.pem -newkey rsa:3072 -keyout file2.pem
Enter PEM pass phrase: **********
Verifying - Enter PEM pass phrase: **********
Country Name (2 letter code) [AU]:US
State or Province Name (full name) [Some-State]:California
Locality Name (eg, city) []:Sunnyvale
Organization Name (eg, company) [Internet Widgits Pty Ltd]:example.com
Organizational Unit Name (eg, section) []:Infrastructure
Common Name (e.g. server FQDN or YOUR name) []:radius.example.com
What is one guideline for continuing to obtain a certificate?
A company has wired VolP phones, which transmit tagged traffic and connect to AOS-CX switches. The company wants to tunnel the phones' traffic to an HPE
Aruba Networking gateway for applying security policies.
What is part of the correct configuration on the AOS-CX switches?
Refer to the exhibit.
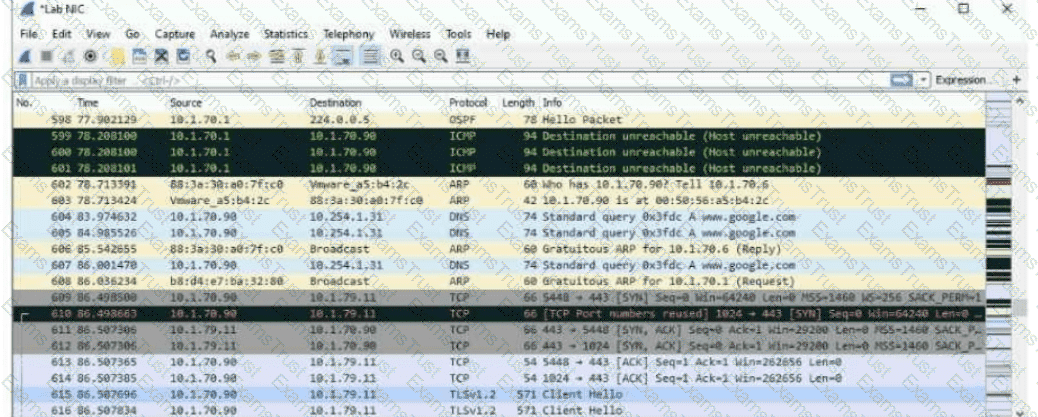
The exhibit shows a saved packet capture, which you have opened in Wireshark. You want to focus on the complete conversation between 10.1.70.90 and 10.1.79.11 that uses source port 5448.
What is a simple way to do this in Wireshark?
A company uses both HPE Aruba Networking ClearPass Policy Manager (CPPM) and HPE Aruba Networking ClearPass Device Insight (CPDI).
What is one way integrating the two solutions can help the company implement Zero Trust Security?
Refer to Exhibit.
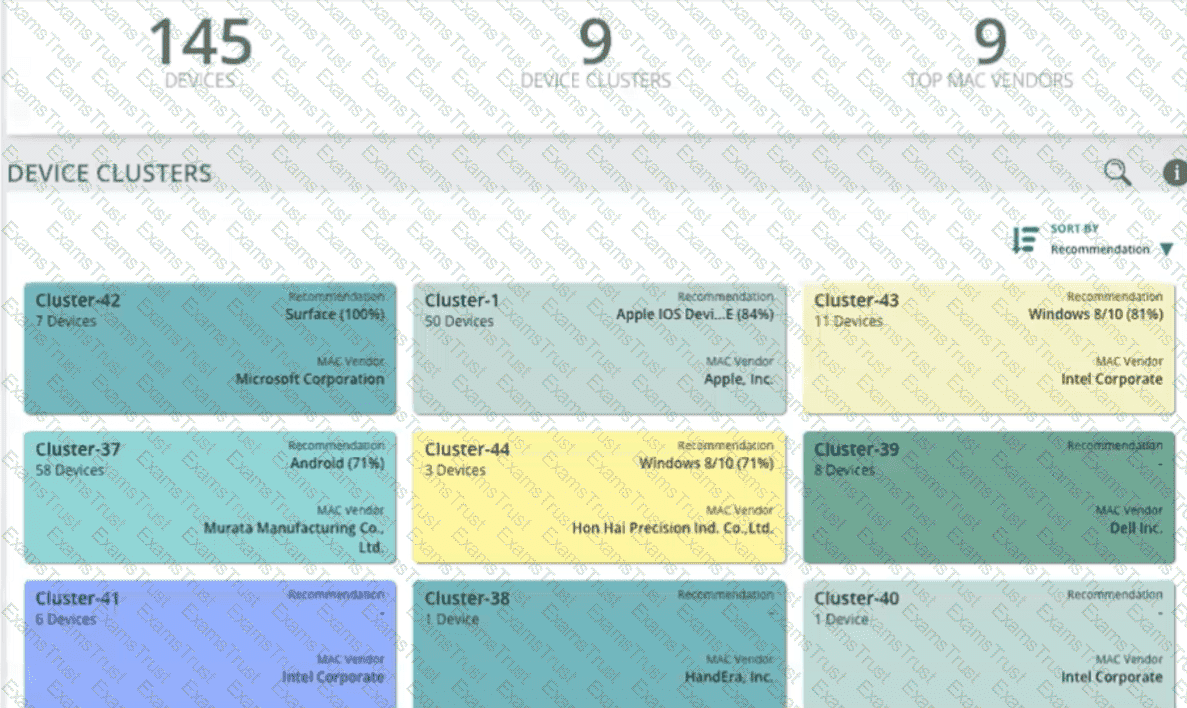
A company is using HPE Aruba Networking ClearPass Device Insight (CPDI) (the standalone application). In the CPDI interface, you go to the Generic Devices
page and see the view shown in the exhibit.
What correctly describes what you see?
A company already uses HPE Aruba Networking ClearPass Policy Manager (CPPM) as the RADIUS server for authenticating wireless clients with 802.1X. Now you are setting up 802.1X on AOS-CX switches to authenticate many of those same clients on wired connections. You decide to copy CPPM's wireless 802.1X service and then edit it with a new name and enforcement policy. What else must you change for authentication to work properly?
A company wants to use HPE Aruba Networking ClearPass Policy Manager (CPPM) to profile Linux devices. You have decided to schedule a subnet scan of the devices' subnets. Which additional step should you complete before scheduling the scan?
A company has AOS-CX switches at the access layer, managed by HPE Aruba Networking Central. You have identified suspicious activity on a wired client. You want to analyze the client's traffic with Wireshark, which you have on your management station.
What should you do?
You are establishing a cluster of HPE Aruba Networking ClearPass servers. (Assume that they are running version 6.9.).
For which type of certificate it is recommended to install a CA-signed certificate on the Subscriber before it joins the cluster?
What is one use case that companies can fulfill using HPE Aruba Networking ClearPass Policy Manager’s (CPPM’s) Device Profiler?
A company wants you to integrate HPE Aruba Networking ClearPass Policy Manager (CPPM) with HPE Aruba Networking ClearPass Device Insight (CPDI).
What is one aspect of the integration that you should explain?
A company uses both HPE Aruba Networking ClearPass Policy Manager (CPPM) and HPE Aruba Networking ClearPass Device Insight (CPDI). What is one way integrating the two solutions can help the company implement Zero Trust Security?