Which aspects of information security will be caused by unauthorized access? (multiple choice)
The network-based intrusion detection system is mainly used to monitor the information of the critical path of the network in real time, listen to all packets on the network, collect data, and divide
Analyze the suspicious object, which of the following options are its main features? (multiple choices)
What are the typical technologies of anti-virus engines (multiple choice)
For the description of the Anti DDOS system, which of the following options is correct? C
The whitelist rule of the firewall anti-virus module is configured as ("*example*, which of the following matching methods is used in this configuration?
When configuring the terminal visits, we put some equipment configured exception equipment ,which of the following statements are true about the exception equipment?
With regard to APT attacks, the attacker often lurks for a long time and launches a formal attack on the enterprise at the key point of the incident.
Generally, APT attacks can be summarized into four stages:
1. Collecting Information & Intrusion
2. Long-term lurking & mining
3. Data breach
4. Remote control and penetration
Regarding the order of these four stages, which of the following options is correct?
Which of the following is the correct configuration idea for the anti-virus strategy?
1. Load the feature library
2. Configure security policy and reference AV Profile
3. Apply and activate the license
4. Configure AV Profile
5. Submit
Regarding Huawei's anti-virus technology, which of the following statements is wrong?
Regarding the enhanced mode in HTTP Flood source authentication, which of the following descriptions are correct? Multiple choices
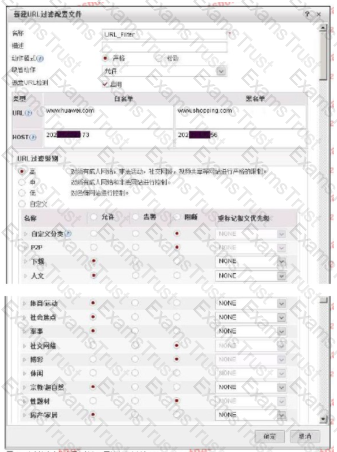
The following figure shows the configuration of the URL filtering configuration file. Regarding the configuration, which of the following statements is correct?
Which of the following options belong to the upgrade method of the anti-virus signature database of Huawei USG6000 products? (multiple choice)
The analysis and processing capabilities of traditional firewalls at the application layer are weak, and they cannot correctly analyze malicious codes that are mixed in the flow of allowed application teaching: many Attacks or malicious behaviors often use the firewall's open application data flow to cause damage, causing application layer threats to penetrate the firewall
A True
B. False
When a virus is detected in an email, which of the following is not the corresponding action for detection?
Under the CLI command, which of the following commands can be used to view the AV engine and virus database version?
Regarding the description of intrusion detection technology, which of the following statements is correct?
Fage attack means that the original address and target address of TOP are both set to the IP address of a certain victim. This behavior will cause the victim to report to it.
SYN-ACK message is sent from the address, and this address sends back an ACK message and creates an empty connection, which causes the system resource board to occupy or target
The host crashed.
Which of the following protocols can be used to construct attack messages for special control message attacks? (multiple choice)
A ICMP protocol
B. UDP protocol
C. CIP protocol
D. FTP protocol
IPS is an intelligent intrusion detection and defense product. It can not only detect the occurrence of intrusions, but also can respond in real time through certain response methods.
Stop the occurrence and development of intrusions, and protect the information system from substantial attacks in real time. According to the description of PS, the following items are wrong?
Regarding the processing process of file overwhelming, which of the following statements is correct?
When the device recognizes a keyword during content filtering detection, which response actions can the device perform? (multiple choice)
Regarding intrusion detection I defense equipment, which of the following statements are correct? (multiple choice)
An enterprise administrator configures a Web reputation website in the form of a domain name, and configures the domain name as abc; example. com. .
Which of the following is the entry that the firewall will match when looking up the website URL?
The most common form of child-like attack is to send a large number of seemingly legitimate packets to the target host through Flood, which ultimately leads to network bandwidth.
Or the equipment resources are exhausted. Which of the following options is not included in traffic attack packets?
When a data file hits the whitelist of the firewall's anti-virus module, the firewall will no longer perform virus detection on the file.
Which of the following are the control items of HTTP behavior?) (multiple choice)
Which of the following options are common reasons for IPS detection failure? (multiple choices)
Which of the following options describes the IntelliSense engine IAE incorrectly?
For special message attacks, which of the following option descriptions is correct?
A Special control packet attack is a potential attack and does not have direct destructive behavior
B. The attacker probes the network structure by sending special control messages to launch a real attack.
C. Special control message attacks do not have the ability to detect the network structure. Only scanning attacks can detect the network.
D. Special control message items can only use ICMP to construct attack messages.