Which of the following files can the sandbox detect? (multiple choice)
Anti-DDoS defense system includes: management center, detection center and cleaning center.
What are the typical technologies of anti-virus engines (multiple choice)
Portal At the time of certification, pass Web After the browser enters the account password for authentication, it prompts"Authenticating.."The status lasts for a long time before it shows that the authentication is successful. Which of the following reasons may cause this phenomenon?
Analysis is the core function of intrusion detection. The analysis and processing process of intrusion detection can be divided into three phases; build an analyzer to perform analysis on actual field data.
Which of the analysis, feedback and refinement is the function included in the first two stages?
Which of the following is the default port number of Portal authentication service?
Regarding the file source set in the software management, which of the following descriptions is correct?
UDP is a connectionless protocol. UDP Flood attacks that change sources and ports will cause performance degradation of network devices that rely on session forwarding.
Even the session table is exhausted, causing the network to be paralyzed. Which of the following options is not a preventive measure for UDP Flood attacks?
Which of the following options belong to the keyword matching mode? (multiple choice)
When configuring the antivirus software policy, if you set"The required antivirus software violation level is not installed or running"for"generally"And check"out Now serious violation of the rules prohibits access to the network"Options. When the user uses Any office Certify, The certification is passed, but the result of the security check Can the user access the network when the virus software is not turned on?
After an enterprise deployed antivirus software, it was discovered that virus infections still occurred on a large scale. In addition to the limitations of the product's own technology, the reason for the problem is weak personal terminal security protection, which is also an important factor.
Using Agile Controller-Campus for visitor management, users can obtain the account they applied for in a variety of ways, but which of the following are not included A way?
When the license of Huawei USG6000 product expires, the RBL function will be unavailable, and users can only use the local black and white list to filter junk mail.
155955cc-666171a2-20fac832-0c042c0435
Regarding the sequence of file filtering technology processing flow, which of the following is correct?
(1) The security policy is applied as permit
(2) Protocol decoding
(3) File type recognition
(4) Application recognition
(5) File filtering
Regarding traditional firewalls, which of the following statements are correct? (multiple choice)
Which of the following threats cannot be detected by IPS?
Huawei NIP6000 products provide carrier-class high-reliability mechanisms from multiple levels to ensure the stable operation of equipment.
Which of the following options belong to the network reliability? (multiple choice)
Which of the following are typical intrusions? "Multiple choice)
View on the switch Agile Controller-Campus The policy issued by the server is as follows:
For this strategy, which of the following options are correct? (Multiple choice)
Portal authentication on the Agile Controller-Campus has been configured and is correct.
Configure the following commands on the access control switch:
[S5720] authentication free-rule 1 destination ip 10.1.31.78 mask 255.255. 255.255
Which of the following options are correct? (multiple choice)
Regarding the trigger mechanism of 802.1X authentication, which of the following descriptions is correct? (multiple choice)
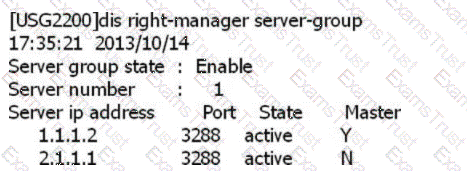
SACG query right-manager information as follows, which options are correct? (Select 2 answers)
Which of the following options is Agile Controller-Campus middle SC The main function of the component?
Deployed by an enterprise network managerAgile Controller-Campus withSACG Later;Identity authentication is successful but cannot access the post-authentication domain, This phenomenon may be caused by any reason? (Multiple choice)
In a centralized networking, the database, SM server, SC server, and AE server are all centrally installed in the corporate headquarters. This networking method is suitable. It is used for enterprises with a wide geographical distribution of users and a large number of users.
When the device recognizes a keyword during content filtering detection, which response actions can the device perform? (multiple choice)
Location refers to the end user's use AC-Campus The terminal environment when accessing the controlled network office. Which of the following options is correct for the description of the place?
Identity authentication determines whether to allow access by identifying the identity of the access device or user.
In a WLAN network, when the AP is in monitoring mode, what kind of packets does the AP use to determine the device type?
SACG Inquire right-manager The information is as follows, which options are correct? (Multiple choice)
Huawei USG6000 products can scan and process certain file transfer protocols for viruses, but which of the following protocols is not included?
In the deployment of Huawei NIP6000 products, only port mirroring can be used for streaming replication.
Which of the following options belong to a third-party server account? (Multiple choice)
In the following options, which of the two attacks use similar attack methods, they will generate a large number of useless response packets, occupying network bandwidth,
Consume equipment resources?
An account can belong to multiple roles, that is, a user may hold multiple positions.
Which of the following options are correct for the configuration description of the management center ATIC? (multiple choice)
Buffer overflows, Trojan horses, and backdoor attacks are all attacks at the application layer.
Attacks on the Web can be divided into three types of attacks on the client, server, or communication channel.
Which of the following options is not a feature of Trojan horses?
The administrator issues notices to users in the form of announcements, such as the latest software and patch installation notices. Which of the following options of the announcement is incorrect?
Which of the following options is not a feature of big data technology?
In the Agile Controller-Campus admission control technology framework, regarding the description of RADIUS, which of the following options is correct?
Which way can NAC Agent upgrade package be deployed?
Which of the following cybersecurity threats exist only in WLAN In the network?
In the scenario of SACG linkage in bypass mode, only the traffic initiated by the terminal user will pass through the firewall, and the server will return to the terminal in use.
The traffic does not need to go through the firewall y. For the firewall, it belongs to the scenario of inconsistent traffic back and forth paths, this needs to turn off the session state check function.
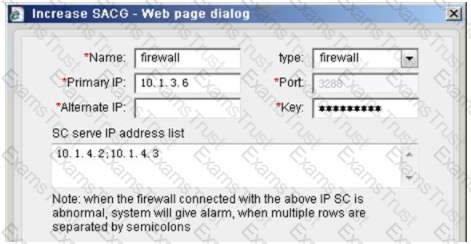
The following is a hardware SACG increase firewall configuration, which statement below is true?
Place refers to the terminal environment when end-user use strategy management center access to
controlled network office, which options are correct about place? (Choose 2 answers)
Which of the following options is for Portal The statement of the gateway access process is correct?
Regarding the processing process of file overwhelming, which of the following statements is correct?
For the convenience of visitors, different authentication and master pages can be distributed for different visitors. When configuring the push page strategy, different matching conditions need to be defined, so which of the following options can be used as the limited matching conditions? (Multiple choice)
How to check whether the SM and SC silverware start normally after installing the Agile Controller-Campus) (multiple delivery)
In the Agile Controller-Campus admission control scenario, regarding the role description of the RADIUS server I client, which of the following is positive True?
The security management system is only optional, and anti-virus software or anti-hacking technology can be a good defense against network threats.
Cloud sandbox refers to deploying the sandbox in the cloud and providing remote detection services for tenants. The process includes:
1. Report suspicious files
2. Retrospective attack
3. Firewall linkage defense
4. Prosecution in the cloud sandbox
For the ordering of the process, which of the following options is correct?
The administrator has defined two key words that need to be recognized on the firewall: the weight of the keyword x is 2, and the weight of the key y is 3: defined
The alarm interval value from the content is 5, and the blocking threshold value is 10. If the device detects that there is a secondary key space x in the webpage created by the user, the two keywords are
Y; Regarding the weight value and monthly household visits to Heshun Street, is the following statement correct?