In a defense-in-depth strategy, what is the purpose of role-based access control?
Available Choices (select all choices that are correct)
In an IACS system, a typical security conduit consists of which of the following assets?
Available Choices (select all choices that are correct)
Which type of cryptographic algorithms requires more than one key?
Available Choices (select all choices that are correct)
What is the purpose of ISO/IEC 15408 (Common Criteria)?
Available Choices (select all choices that are correct)
Why is OPC Classic considered firewall unfriendly?
Available Choices (select all choices that are correct)
Within the National Institute of Standards and Technoloqv Cybersecuritv Framework v1.0 (NIST CSF), what is the status of the ISA 62443 standards?
Available Choices (select all choices that are correct)
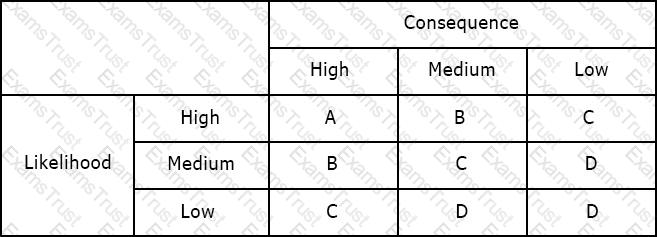
Using the risk matrix below, what is the risk of a medium likelihood event with high consequence?
Which of the following is an element of security policy, organization, and awareness?
Available Choices (select all choices that are correct)
How many security levels are in the ISASecure certification program?
Available Choices (select all choices that are correct)
Which of the following are the critical variables related to access control?
Available Choices (select all choices that are correct)
Which analysis method is MOST frequently used as an input to a security risk assessment?
Available Choices (select all choices that are correct)
Which of the ISA 62443 standards focuses on the process of developing secure products?
Available Choices (select all choices that are correct)
Who must be included in a training and security awareness program?
Available Choices (select all choices that are correct)
Which is a commonly used protocol for managing secure data transmission on the Internet?
Available Choices (select all choices that are correct)
Which of the following is an example of separation of duties as a part of system development and maintenance?
Available Choices (select all choices that are correct)
Which of the following is a recommended default rule for IACS firewalls?
Available Choices (select all choices that are correct)
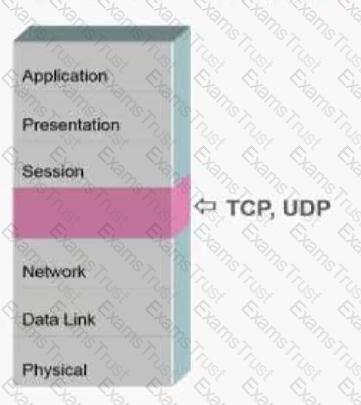
At Layer 4 of the Open Systems Interconnection (OSI) model, what identifies the application that will handle a packet inside a host?
Available Choices (select all choices that are correct)
What are the three main components of the ISASecure Integrated Threat Analysis (ITA) Program?
Available Choices (select all choices that are correct)
What do packet filter firewalls examine?
Available Choices (select all choices that are correct)
Which of the following ISA-99 (IEC 62443) Reference Model levels is named correctly?
Available Choices (select all choices that are correct)
Which is the implementation of PROFIBUS over Ethernet for non-safety-related communications?
Available Choices (select all choices that are correct)
Which organization manages the ISASecure conformance certification program?
Available Choices (select all choices that are correct)
What is the name of the protocol that implements serial Modbus over Ethernet?
Available Choices (select all choices that are correct)
Which communications system covers a large geographic area?
Available Choices (select all choices that are correct)
Which is the PRIMARY reason why Modbus over Ethernet is easy to manaqe in a firewall?
Available Choices (select all choices that are correct)
What is the name of the missing layer in the Open Systems Interconnection (OSI) model shown below?