Click the Exhibit button.
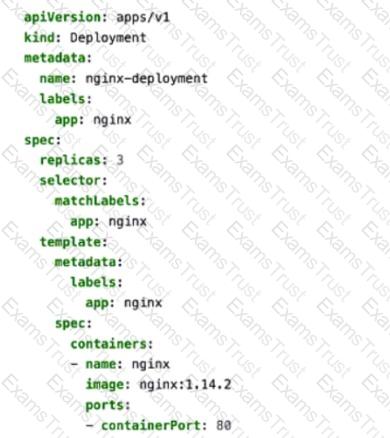
You apply the manifest file shown in the exhibit.
Which two statements are correct in this scenario? (Choose two.)
The created pods are receiving traffic on port 80.
This manifest is used to create a deployment.
This manifest is used to create a deploymentConfig.
Four pods are created as a result of applying this manifest.
The provided YAML manifest defines a Kubernetes Deployment object that creates and manages a set of pods running the NGINX web server. Let’s analyze each statement in detail:
A. The created pods are receiving traffic on port 80.
Correct:
The containerPort: 80 field in the manifest specifies that the NGINX container listens on port 80 for incoming traffic.
While this does not expose the pods externally, it ensures that the application inside the pod (NGINX) is configured to receive traffic on port 80.
B. This manifest is used to create a deployment.
Correct:
The kind: Deployment field explicitly indicates that this manifest is used to create a Kubernetes Deployment .
Deployments are used to manage the desired state of pods, including scaling, rolling updates, and self-healing.
C. This manifest is used to create a deploymentConfig.
Incorrect:
deploymentConfig is a concept specific to OpenShift, not standard Kubernetes. In OpenShift, deploymentConfig provides additional features like triggers and lifecycle hooks, but this manifest uses the standard Kubernetes Deployment object.
D. Four pods are created as a result of applying this manifest.
Incorrect:
The replicas: 3 field in the manifest specifies that the Deployment will create three replicas of the NGINX pod. Therefore, only three pods are created, not four.
Why These Statements?
Traffic on Port 80:
The containerPort: 80 field ensures that the NGINX application inside the pod listens on port 80. This is critical for the application to function as a web server.
Deployment Object:
The kind: Deployment field confirms that this manifest creates a Kubernetes Deployment, which manages the lifecycle of the pods.
Replica Count:
The replicas: 3 field explicitly states that three pods will be created. Any assumption of four pods is incorrect.
Additional Context:
Kubernetes Deployments:Deployments are one of the most common Kubernetes objects used to manage stateless applications. They ensure that the desired number of pod replicas is always running and can handle updates or rollbacks seamlessly.
Ports in Kubernetes:The containerPort field in the pod specification defines the port on which thecontainerized application listens. However, to expose the pods externally, a Kubernetes Service (e.g., NodePort, LoadBalancer) must be created.
JNCIA Cloud References:
The JNCIA-Cloud certification covers Kubernetes concepts, including Deployments, Pods, and networking. Understanding how Deployments work and how ports are configured is essential for managing containerized applications in cloud environments.
For example, Juniper Contrail integrates with Kubernetes to provide advanced networking and security features for Deployments like the one described in the exhibit.
Which two statements about containers are true? (Choose two.)
Containers contain executables, libraries, configuration files, and an operating system.
Containers package the entire runtime environment of an application, including its dependencies.
Containers can only run on a system with a Type 2 hypervisor.
Containers share the use of the underlying system’s kernel.
Containers are a lightweight form of virtualization that enable the deployment of applications in isolated environments. Let’s analyze each statement:
A. Containers contain executables, libraries, configuration files, and an operating system.
Incorrect: Containers do not include a full operating system. Instead, they share the host system's kernel and only include the application and its dependencies (e.g., libraries, binaries, and configuration files).
B. Containers package the entire runtime environment of an application, including its dependencies.
Correct: Containers bundle the application code, runtime, libraries, and configuration files into a single package. This ensures consistency across different environments and eliminates issues caused by differences in dependencies.
C. Containers can only run on a system with a Type 2 hypervisor.
Incorrect: Containers do not require a hypervisor. They run directly on the host operating system and share the kernel. Hypervisors (Type 1 or Type 2) are used for virtual machines, not containers.
D. Containers share the use of the underlying system’s kernel.
Correct: Containers leverage the host operating system's kernel, which allows them to be lightweight and efficient. Each container has its own isolated user space but shares the kernel with other containers.
Why These Statements?
Runtime Environment Packaging: Containers ensure portability and consistency by packaging everything an application needs to run.
Kernel Sharing: By sharing the host kernel, containers consume fewer resources compared to virtual machines, which require separate operating systems.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding containerization technologies, including Docker and Kubernetes. Containers are a fundamental component of modern cloud-native architectures.
For example, Juniper Contrail integrates with Kubernetes to manage containerized workloads, leveraging the lightweight and portable nature of containers.
You want to view pods with their IP addresses in OpenShift.
Which command would you use to accomplish this task?
oc qet pods -o vaml
oc get pods -o wide
oc qet all
oc get pods
OpenShift provides various commands to view and manage pods. Let’s analyze each option:
A. oc qet pods -o vaml
Incorrect:
The command contains a typo (qetinstead ofget) and an invalid output format (vaml). The correct format would beyaml, but this command does not display pod IP addresses.
B. oc get pods -o wide
Correct:
Theoc get pods -o widecommand displays detailed information about pods, including their names, statuses, andIP addresses. The-o wideflag extends the output to include additional details like pod IPs and node assignments.
C. oc qet all
Incorrect:
The command contains a typo (qetinstead ofget). Even if corrected,oc get alllists all resources (e.g., pods, services, deployments) but does not display pod IP addresses.
D. oc get pods
Incorrect:
Theoc get podscommand lists pods with basic information such as name, status, and restart count. It does not include pod IP addresses unless the-o wideflag is used.
Why oc get pods -o wide?
Detailed Output:The-o wideflag provides extended information, including pod IP addresses, which is essential for troubleshooting and network configuration.
Ease of Use:This command is simple and effective for viewing pod details in OpenShift.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding OpenShift CLI commands and their outputs. Knowing how to retrieve detailed pod information is essential for managing and troubleshooting OpenShift environments.
For example, Juniper Contrail integrates with OpenShift to provide advanced networking features, relying on accurate pod IP information for traffic routing and segmentation.
Which container runtime engine is used by default in OpenShift?
containerd
cri-o
Docker
runC
OpenShift uses a container runtime engine to manage and run containers within its Kubernetes-based environment. Let’s analyze each option:
A. containerd
Incorrect:
Whilecontainerdis a popular container runtime used in Kubernetes environments, it is not the default runtime for OpenShift. OpenShift uses a runtime specifically optimized for Kubernetes workloads.
B. cri-o
Correct:
CRI-Ois the default container runtime engine for OpenShift. It is a lightweight, Kubernetes-native runtime that implements the Container Runtime Interface (CRI) and is optimized for running containers in Kubernetes environments.
C. Docker
Incorrect:
Docker was historically used as a container runtime in earlier versions of Kubernetes and OpenShift. However, OpenShift has transitioned to CRI-O as its default runtime, as Docker's architecture is not directly aligned with Kubernetes' requirements.
D. runC
Incorrect:
runCis a low-level container runtime that executes containers. While it is used internally by higher-level runtimes likecontainerdandcri-o, it is not used directly as the runtime engine in OpenShift.
Why CRI-O?
Kubernetes-Native Design:CRI-O is purpose-built for Kubernetes, ensuring compatibility and performance.
Lightweight and Secure:CRI-O provides a minimalistic runtime that focuses on running containers efficiently and securely.
JNCIA Cloud References:
The JNCIA-Cloud certification covers container runtimes as part of its curriculum on container orchestration platforms. Understanding the role of CRI-O in OpenShift is essential for managing containerized workloads effectively.
For example, Juniper Contrail integrates with OpenShift to provide advanced networking features, leveraging CRI-O for container execution.
What are two available installation methods for an OpenShift cluster? (Choose two.)
installer-provisioned infrastructure
kubeadm
user-provisioned infrastructure
kubespray
OpenShift provides multiple methods for installing and deploying clusters, depending on the level of control and automation desired. Let’s analyze each option:
A. installer-provisioned infrastructure
Correct:
Installer-provisioned infrastructure (IPI)is an automated installation method where the OpenShift installer provisions and configures the underlying infrastructure (e.g., virtual machines, networking) using cloud provider APIs or bare-metal platforms. This method simplifies deployment by handling most of the setup automatically.
B. kubeadm
Incorrect:
kubeadmis a tool used to bootstrap Kubernetes clusters manually. While it is widely used for Kubernetes installations, it is not specific to OpenShift and is not an official installation method for OpenShift clusters.
C. user-provisioned infrastructure
Correct:
User-provisioned infrastructure (UPI)is a manual installation method where users prepare and configure the infrastructure (e.g., virtual machines, load balancers, DNS) before deploying OpenShift. This method provides greater flexibility and control over the environment but requires more effort from the user.
D. kubespray
Incorrect:
Kubesprayis an open-source tool used to deploy Kubernetes clusters on various infrastructures. Likekubeadm, it is not specific to OpenShift and is not an official installation method for OpenShift clusters.
Why These Methods?
Installer-Provisioned Infrastructure (IPI):Automates the entire installation process, making it ideal for users who want a quick and hassle-free deployment.
User-Provisioned Infrastructure (UPI):Allows advanced users to customize the infrastructure and tailor the deployment to their specific needs.
JNCIA Cloud References:
The JNCIA-Cloud certification covers OpenShift installation methods as part of its curriculum on container orchestration platforms. Understanding the differences between IPI and UPI is essential for deploying OpenShift clusters effectively.
For example, Juniper Contrail integrates with OpenShift to provide advanced networking features, regardless of whether the cluster is deployed using IPI or UPI.
Which two statements are correct about the Kubernetes networking model? (Choose two.)
Pods are allowed to communicate if they are only in the default namespaces.
Pods are not allowed to communicate if they are in different namespaces.
Full communication between pods is allowed across nodes without requiring NAT.
Each pod has its own IP address in a flat, shared networking namespace.
Kubernetes networking is designed to provide seamless communication between pods, regardless of their location in the cluster. Let’s analyze each statement:
A. Pods are allowed to communicate if they are only in the default namespaces.
Incorrect:Pods can communicate with each other regardless of the namespace they belong to. Namespaces are used for logical grouping and isolation but do not restrict inter-pod communication.
B. Pods are not allowed to communicate if they are in different namespaces.
Incorrect:Pods in different namespaces can communicate with each other as long as there are no network policies restricting such communication. Namespaces do not inherently block communication.
C. Full communication between pods is allowed across nodes without requiring NAT.
Correct:Kubernetes networking is designed so that pods can communicate directly with each other across nodes without Network Address Translation (NAT). Each pod has a unique IP address, and the underlying network ensures direct communication.
D. Each pod has its own IP address in a flat, shared networking namespace.
Correct:In Kubernetes, each pod is assigned a unique IP address in a flat network space. This allows pods to communicate with each other as if they were on the same network, regardless of the node they are running on.
Why These Statements?
Flat Networking Model:Kubernetes uses a flat networking model where each pod gets its own IP address, simplifying communication and eliminating the need for NAT.
Cross-Node Communication:The design ensures that pods can communicate seamlessly across nodes, enabling scalable and distributed applications.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes Kubernetes networking concepts, including pod-to-pod communication and the flat networking model. Understanding these principles is essential for designing and managing Kubernetes clusters.
For example, Juniper Contrail provides advanced networking features for Kubernetes, ensuring efficient and secure pod communication across nodes.
What is the name of the Docker container runtime?
docker_cli
containerd
dockerd
cri-o
Docker is a popular containerization platform that relies on a container runtime to manage the lifecycle of containers. The container runtime is responsible for tasks such as creating, starting, stopping, and managing containers. Let’s analyze each option:
A. docker_cli
Incorrect: The Docker CLI (Command Line Interface) is a tool used to interact with the Docker daemon (dockerd). It is not a container runtime but rather a user interface for managing Docker containers.
B. containerd
Correct: containerd is the default container runtime used by Docker. It is a lightweight, industry-standard runtime that handles low-level container management tasks, such as image transfer, container execution, and lifecycle management. Docker delegates these tasks to containerd through the Docker daemon.
C. dockerd
Incorrect: dockerd is the Docker daemon, which manages Docker objects such as images, containers, networks, and volumes. While dockerd interacts with the container runtime, it is not the runtime itself.
D. cri-o
Incorrect: cri-o is an alternative container runtime designed specifically for Kubernetes. It implements the Kubernetes Container Runtime Interface (CRI) and is not used by Docker.
Why containerd?
Industry Standard: containerd is a widely adopted container runtime that adheres to the Open Container Initiative (OCI) standards.
Integration with Docker: Docker uses containerd as its default runtime, making it the correct answer in this context.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding containerization technologies and their components. Docker and its runtime (containerd) are foundational tools in modern cloud environments, enabling lightweight, portable, and scalable application deployment.
For example, Juniper Contrail integrates with container orchestration platforms like Kubernetes, which often use containerd as the underlying runtime. Understanding container runtimes is essential for managing containerized workloads in cloud environments.
You must install a basic Kubernetes cluster.
Which tool would you use in this situation?
kubeadm
kubectl apply
kubectl create
dashboard
To install a basic Kubernetes cluster, you need a tool that simplifies the process of bootstrapping and configuring the cluster. Let’s analyze each option:
A. kubeadm
Correct:
kubeadmis a command-line tool specifically designed to bootstrap a Kubernetes cluster. It automates the process of setting up the control plane and worker nodes, making it the most suitable choice for installing a basic Kubernetes cluster.
B. kubectl apply
Incorrect:
kubectl applyis used to deploy resources (e.g., pods, services) into an existing Kubernetes cluster by applying YAML or JSON manifests. It does not bootstrap or install a new cluster.
C. kubectl create
Incorrect:
kubectl createis another Kubernetes CLI command used to create resources in an existing cluster. Likekubectl apply, it does not handle cluster installation.
D. dashboard
Incorrect:
The Kubernetesdashboardis a web-based UI for managing and monitoring a Kubernetes cluster. It requires an already-installed cluster and cannot be used to install one.
Why kubeadm?
Cluster Bootstrapping: kubeadmprovides a simple and standardized way to initialize a Kubernetes cluster, including setting up the control plane and joining worker nodes.
Flexibility:While it creates a basic cluster, it allows for customization and integration with additional tools like CNI plugins.
JNCIA Cloud References:
The JNCIA-Cloud certification covers Kubernetes installation methods, includingkubeadm. Understanding how to usekubeadmis essential for deploying and managing Kubernetes clusters effectively.
For example, Juniper Contrail integrates with Kubernetes clusters created usingkubeadmto provide advanced networking and security features.
Which method is used to extend virtual networks between physical locations?
encapsulations
encryption
clustering
load-balancing
To extend virtual networks between physical locations, a mechanism is needed to transport network traffic across different sites while maintaining isolation and connectivity. Let’s analyze each option:
A. encapsulations
Correct: Encapsulation is the process of wrapping network packets in additional headers to create tunnels. Protocols like VXLAN, GRE, and MPLS are commonly used to extend virtual networks between physical locations by encapsulating traffic and transporting it over the underlay network.
B. encryption
Incorrect: Encryption secures data during transmission but does not inherently extend virtual networks. While encryption can be used alongside encapsulation for secure communication, it is not the primary method for extending networks.
C. clustering
Incorrect: Clustering refers to grouping multiple servers or devices to work together as a single system. It is unrelated to extending virtual networks between physical locations.
D. load-balancing
Incorrect: Load balancing distributes traffic across multiple servers or paths to optimize performance. While important for scalability, it does not extend virtual networks.
Why Encapsulation?
Tunneling Mechanism: Encapsulation protocols like VXLAN and GRE create overlay networks that span multiple physical locations, enabling seamless communication between virtual networks.
Isolation and Scalability: Encapsulation ensures that virtual networks remain isolated and scalable, even when extended across geographically dispersed sites.
JNCIA Cloud References:
The JNCIA-Cloud certification covers overlay networking and encapsulation as part of its curriculum on cloud architectures. Understanding how encapsulation works is essential for designing and managing distributed virtual networks.
For example, Juniper Contrail uses encapsulation protocols like VXLAN to extend virtual networks across data centers, ensuring consistent connectivity and isolation.
You are asked to provision a bare-metal server using OpenStack.
Which service is required to satisfy this requirement?
Ironic
Zun
Trove
Magnum
OpenStack is an open-source cloud computing platform that provides various services for managing compute, storage, and networking resources. To provision abare-metal serverin OpenStack, theIronicservice is required. Let’s analyze each option:
A. Ironic
Correct:OpenStack Ironic is a bare-metal provisioning service that allows you to manage and provision physical servers as if they were virtual machines. It automates tasks such as hardware discovery, configuration, and deployment of operating systems on bare-metal servers.
B. Zun
Incorrect:OpenStack Zun is a container service that manages the lifecycle of containers. It is unrelated to bare-metal provisioning.
C. Trove
Incorrect:OpenStack Trove is a Database as a Service (DBaaS) solution that provides managed database instances. It does not handle bare-metal provisioning.
D. Magnum
Incorrect:OpenStack Magnum is a container orchestration service that supports Kubernetes, Docker Swarm, and other container orchestration engines. It is focused on containerized workloads, not bare-metal servers.
Why Ironic?
Purpose-Built for Bare-Metal:Ironic is specifically designed to provision and manage bare-metal servers, making it the correct choice for this requirement.
Automation:Ironic automates the entire bare-metal provisioning process, including hardware discovery, configuration, and OS deployment.
JNCIA Cloud References:
The JNCIA-Cloud certification covers OpenStack as part of its cloud infrastructure curriculum. Understanding OpenStack services like Ironic is essential for managing bare-metal and virtualized environments in cloud deployments.
For example, Juniper Contrail integrates with OpenStack to provide networking and security for both virtualized and bare-metal workloads. Proficiency with OpenStack services ensures efficient management of diverse cloud resources.
Which cloud service model provides access to networking, storage, servers, and virtualization in a cloud environment?
Platform as a Service (PaaS)
Software as a Service (SaaS)
Infrastructure as a Service (IaaS)
Database as a Service (DaaS)
Cloud service models define how services are delivered and managed in a cloud environment. The three primary models are:
Infrastructure as a Service (IaaS): Provides virtualized computing resources such as servers, storage, networking, and virtualization over the internet. Customers manage their own operating systems, applications, and data, while the cloud provider manages the underlying infrastructure.
Platform as a Service (PaaS): Provides a platform for developers to build, deploy, and manage applications without worrying about the underlying infrastructure. Examples include Google App Engine and Microsoft Azure App Services.
Software as a Service (SaaS): Delivers fully functional applications over the internet, eliminating the need for users to install or maintain software locally. Examples include Salesforce CRM, Google Workspace, and Microsoft Office 365.
Database as a Service (DaaS): A specialized subset of PaaS that provides managed database services.
In this question, the focus is on access to networking, storage, servers, and virtualization , which are the core components of IaaS . IaaS allows customers to rent infrastructure on-demand and build their own environments without investing in physical hardware.
Why IaaS?
Flexibility: Customers have full control over the operating systems, applications, and configurations.
Scalability: Resources can be scaled up or down based on demand.
Cost Efficiency: Pay-as-you-go pricing eliminates upfront hardware costs.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding the different cloud service models and their use cases. IaaS is particularly relevant for organizations that want to leverage cloud infrastructure while maintaining control over their applications and data.
For example, Juniper Contrail integrates with IaaS platforms like OpenStack to provide advanced networking and security features for virtualized environments.
Which term identifies to which network a virtual machine interface is connected?
virtual network ID
machine access control (MAC)
Virtual Extensible LAN
virtual tunnel endpoint (VTEP)
In cloud environments, virtual machines (VMs) connect to virtual networks to enable communication. Identifying the network to which a VM interface is connected is essential for proper configuration and isolation. Let’s analyze each option:
A. virtual network ID
Correct:Thevirtual network IDuniquely identifies the virtual network to which a VM interface is connected. This ID is used to logically group VMs and ensure they can communicate within the same network while maintaining isolation from other networks.
B. machine access control (MAC)
Incorrect:The MAC address is a hardware identifier for a network interface card (NIC). While it is unique to each interface, it does not identify the network to which the VM is connected.
C. Virtual Extensible LAN (VXLAN)
Incorrect:VXLAN is a tunneling protocol used to create overlay networks in cloud environments. While VXLAN encapsulates traffic, it does not directly identify the network to which a VM interface is connected.
D. virtual tunnel endpoint (VTEP)
Incorrect:A VTEP is a component of overlay networks (e.g., VXLAN) that encapsulates and decapsulates traffic. It is used to establish tunnels but does not identify the virtual network itself.
Why Virtual Network ID?
Logical Isolation:The virtual network ID ensures that VMs are logically grouped into isolated networks, enabling secure and efficient communication.
Scalability:Virtual networks allow cloud environments to scale by supporting multiple isolated networks within the same infrastructure.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding virtual networking concepts, including virtual networks and their identifiers. Virtual network IDs are fundamental to cloud architectures, enabling multi-tenancy and network segmentation.
For example, Juniper Contrail uses virtual network IDs to manage connectivity and isolation for VMs in cloud environments. Proper configuration of virtual networks ensures seamless communication and security.
Which two CPU flags indicate virtualization? (Choose two.)
lvm
vmx
xvm
kvm
CPU flags indicate hardware support for specific features, including virtualization. Let’s analyze each option:
A. lvm
Incorrect: LVM (Logical Volume Manager) is a storage management technology used in Linux systems. It is unrelated to CPU virtualization.
B. vmx
Correct: The vmx flag indicates Intel Virtualization Technology (VT-x), which provides hardware-assisted virtualization capabilities. This feature is essential for running hypervisors like VMware ESXi, KVM, and Hyper-V.
C. xvm
Incorrect: xvm is not a recognized CPU flag for virtualization. It may be a misinterpretation or typo.
D. kvm
Correct: The kvm flag indicates Kernel-based Virtual Machine (KVM) support, which is a Linux kernel module that leverages hardware virtualization extensions (e.g., Intel VT-x orAMD-V) to run virtual machines. While kvm itself is not a CPU flag, it relies on hardware virtualization features like vmx (Intel) or svm (AMD).
Why These Answers?
Hardware Virtualization Support: Both vmx (Intel VT-x) and kvm (Linux virtualization) are directly related to CPU virtualization. These flags enable efficient execution of virtual machines by offloading tasks to the CPU.
JNCIA Cloud References:
The JNCIA-Cloud certification emphasizes understanding virtualization technologies, including hardware-assisted virtualization. Recognizing CPU flags like vmx and kvm is crucial for deploying and troubleshooting virtualized environments.
For example, Juniper Contrail integrates with hypervisors like KVM to manage virtualized workloads in cloud environments. Ensuring hardware virtualization support is a prerequisite for deploying such solutions.
You are asked to support an application in your cluster that uses a non-IP protocol.
In this scenario, which type of virtual network should you create to support this application?
a Layer 3 virtual network
a Layer 2 virtual network
an Ethernet VPN (EVPN) Type 5 virtual network
a virtual network router connected to the virtual network
In cloud environments, virtual networks are used to support applications that may rely on different protocols for communication. Let’s analyze each option:
A. a Layer 3 virtual network
Incorrect:A Layer 3 virtual network operates at the IP level and is designed for routing traffic between subnets or networks. It is not suitable for applications that use non-IP protocols (e.g., Ethernet-based protocols).
B. a Layer 2 virtual network
Correct:A Layer 2 virtual network operates at the data link layer (Layer 2) and supports non-IP protocols by forwarding traffic based on MAC addresses. This makes it ideal for applications that rely on protocols like Ethernet, MPLS, or other Layer 2 technologies.
C. an Ethernet VPN (EVPN) Type 5 virtual network
Incorrect:EVPN Type 5 is a Layer 3 overlay technology used for inter-subnet routing in EVPN environments. It is not designed to support non-IP protocols.
D. a virtual network router connected to the virtual network
Incorrect:A virtual network router is used to route traffic between different subnets or networks. It operates at Layer 3 and is not suitable for applications using non-IP protocols.
Why Layer 2 Virtual Network?
Support for Non-IP Protocols:Layer 2 virtual networks forward traffic based on MAC addresses, making them compatible with non-IP protocols.
Flexibility:They can support a wide range of applications, including those that rely on Ethernet or other Layer 2 technologies.
JNCIA Cloud References:
The JNCIA-Cloud certification covers virtual networking concepts, including Layer 2 and Layer 3 networks. Understanding the differences between these layers is essential for designing networks that meet application requirements.
For example, Juniper Contrail supports Layer 2 virtual networks to enable seamless communication for applications using non-IP protocols.
Which Linux protection ring is the least privileged?
0
1
2
3
In Linux systems, the concept of protection rings is used to define levels of privilege for executing processes and accessing system resources. These rings are part of the CPU's architecture and provide a mechanism for enforcing security boundaries between different parts of the operating system and user applications. There are typically four rings in the x86 architecture, numbered from 0 to 3:
Ring 0 (Most Privileged):This is the highest level of privilege, reserved for the kernel and critical system functions. The operating system kernel operates in this ring because it needs unrestricted access to hardware resources and control over the entire system.
Ring 1 and Ring 2:These intermediate rings are rarely used in modern operating systems. They can be utilized for device drivers or other specialized purposes, but most operating systems, including Linux, do not use these rings extensively.
Ring 3 (Least Privileged):This is the least privileged ring, where user-level applications run. Applications running in Ring 3 have limited access to system resources and must request services from the kernel (which runs in Ring 0) via system calls. This ensures that untrusted or malicious code cannot directly interfere with the core system operations.
Why Ring 3 is the Least Privileged:
Isolation:User applications are isolated from the core system functions to prevent accidental or intentional damage to the system.
Security:By restricting access to hardware and sensitive system resources, the risk of vulnerabilities or exploits is minimized.
Stability:Running applications in Ring 3 ensures that even if an application crashes or behaves unexpectedly, it does not destabilize the entire system.
JNCIA Cloud References:
The Juniper Networks Certified Associate - Cloud (JNCIA-Cloud) curriculum emphasizes understanding virtualization, cloud architectures, and the underlying technologies that support them. While the JNCIA-Cloud certification focuses more on Juniper-specific technologies like Contrail, it also covers foundational concepts such as virtualization, Linux, and cloud infrastructure.
In the context of virtualization and cloud environments, understanding the role of protection rings is important because:
Hypervisors often run in Ring 0 to manage virtual machines (VMs).
VMs themselves run in a less privileged ring (e.g., Ring 3) to ensure isolation between the guest operating systems and the host system.
For example, in a virtualized environment like Juniper Contrail, the hypervisor (e.g., KVM) manages the execution of VMs. The hypervisor operates in Ring 0, while the guest OS and applications within the VM operate in Ring 3. This separation ensures that the VMs are securely isolated from each other and from the host system.
Thus, the least privileged Linux protection ring isRing 3, where user applications execute with restricted access to system resources.
Which two statements describe a multitenant cloud? (Choose two.)
Tenants are aware of other tenants using their shared resources.
Servers, network, and storage are separated per tenant.
The entities of each tenant are isolated from one another.
Multiple customers of a cloud vendor have access to their own dedicated hardware.
Amultitenant cloudis a cloud architecture where multiple customers (tenants) share the same physical infrastructure or platform while maintaining logical isolation. Let’s analyze each statement:
A. Tenants are aware of other tenants using their shared resources.
Incorrect:In a multitenant cloud, tenants are logically isolated from one another. While they may share underlying physical resources (e.g., servers, storage), they are unaware of other tenants and cannot access their data or applications. This isolation ensures security and privacy.
B. Servers, network, and storage are separated per tenant.
Incorrect:In a multitenant cloud, resources such as servers, network, and storage are shared among tenants. The separation is logical, not physical. For example, virtualization technologies like hypervisors and software-defined networking (SDN) are used to create isolated environments for each tenant.
C. The entities of each tenant are isolated from one another.
Correct:Logical isolation is a fundamental characteristic of multitenancy. Each tenant’s data, applications, and configurations are isolated to prevent unauthorized access or interference. Technologies like virtual private clouds (VPCs) and network segmentation ensure this isolation.
D. Multiple customers of a cloud vendor have access to their own dedicated hardware.
Correct:While multitenancy typically involves shared resources, some cloud vendors offer dedicated hardware options for customers with strict compliance or performance requirements. For example, AWS offers "Dedicated Instances" or "Dedicated Hosts," which provide dedicated physical servers for specific tenants within a multitenant environment.
JNCIA Cloud References:
The Juniper Networks Certified Associate - Cloud (JNCIA-Cloud) curriculum discusses multitenancy as a key feature of cloud computing. Multitenancy enables efficient resource utilization and cost savings by allowing multiple tenants to share infrastructure while maintaining isolation.
For example, Juniper Contrail supports multitenancy by providing features like VPCs, network overlays, and tenant isolation. These capabilities ensure that each tenant has a secure and independent environment within a shared infrastructure.
Which statement about software-defined networking is true?
It must manage networks through the use of containers and repositories.
It manages networks by separating the data forwarding plane from the control plane.
It applies security policies individually to each separate node.
It manages networks by merging the data forwarding plane with the control plane.
Software-Defined Networking (SDN) is a revolutionary approach to network management that separates the control plane from the data (forwarding) plane. Let’s analyze each option:
A. It must manage networks through the use of containers and repositories.
Incorrect:While containers and repositories are important in cloud-native environments, they are not a requirement for SDN. SDN focuses on programmability and centralized control, not containerization.
B. It manages networks by separating the data forwarding plane from the control plane.
Correct:SDN separates the control plane (decision-making) from the data forwarding plane (packet forwarding). This separation enables centralized control, programmability, and dynamic network management.
C. It applies security policies individually to each separate node.
Incorrect:SDN applies security policies centrally through the SDN controller, not individually to each node. Centralized policy enforcement is one of the key advantages of SDN.
D. It manages networks by merging the data forwarding plane with the control plane.
Incorrect:Merging the forwarding and control planes contradicts the fundamental principle of SDN. The separation of these planes is what enables SDN’s flexibility and programmability.
Why This Answer?
Separation of Planes:By decoupling the control plane from the forwarding plane, SDN enables centralized control over network devices. This architecture simplifies network management, improves scalability, and supports automation.
JNCIA Cloud References:
The JNCIA-Cloud certification covers SDN as a core concept in cloud networking. Understanding the separation of the control and forwarding planes is essential for designing and managing modern cloud environments.
For example, Juniper Contrail serves as an SDN controller, centralizing control over network devices and enabling advanced features like network automation and segmentation.
You want to limit the memory, CPU, and network utilization of a set of processes running on a Linux host.
Which Linux feature would you configure in this scenario?
You want to limit the memory, CPU, and network utilization of a set of processes running on a Linux host.
Which Linux feature would you configure in this scenario?
virtual routing and forwarding instances
network namespaces
control groups
slicing
Linux provides several features to manage system resources and isolate processes. Let’s analyze each option:
A. virtual routing and forwarding instances
Incorrect:Virtual Routing and Forwarding (VRF) is a networking feature used to create multiple routing tables on a single router or host. It is unrelated to limiting memory, CPU, or network utilization for processes.
B. network namespaces
Incorrect:Network namespaces are used to isolate network resources (e.g., interfaces, routing tables) for processes. While they can help with network isolation, they do not directly limit memory or CPU usage.
C. control groups
Correct: Control Groups (cgroups)are a Linux kernel feature that allows you to limit, account for, and isolate the resource usage (CPU, memory, disk I/O, network) of a set of processes. cgroups are commonly used in containerization technologies like Docker and Kubernetes to enforce resource limits.
D. slicing
Incorrect:"Slicing" is not a recognized Linux feature for resource management. This term may refer to dividing resources in other contexts but is not relevant here.
Why Control Groups?
Resource Management:cgroups provide fine-grained control over memory, CPU, and network utilization, ensuring that processes do not exceed their allocated resources.
Containerization Foundation:cgroups are a core technology behind container runtimes likecontainerdand orchestration platforms like Kubernetes.
JNCIA Cloud References:
The JNCIA-Cloud certification covers Linux features like cgroups as part of its containerization curriculum. Understanding cgroups is essential for managing resource allocation in cloud environments.
For example, Juniper Contrail integrates with Kubernetes to manage containerized workloads, leveraging cgroups to enforce resource limits.
When considering OpenShift and Kubernetes, what are two unique resources of OpenShift? (Choose two.)
routes
build
ingress
services
OpenShift extends Kubernetes by introducing additional resources and abstractions to simplify application development and deployment. Let’s analyze each option:
A. routes
Correct:
Routesare unique to OpenShift and provide a way to expose services externally by mapping a hostname to a service. They are built on top of Kubernetes Ingress but offer additional features like TLS termination and wildcard support.
B. build
Correct:
Buildsare unique to OpenShift and represent the process of transforming source code into container images. OpenShift provides build configurations and strategies (e.g., Docker, S2I) to automate this process, which is not natively available in Kubernetes.
C. ingress
Incorrect:
Ingressis a standard Kubernetes resource used to manage external access to services. While OpenShift uses Ingress as the foundation for its Routes, Ingress itself is not unique to OpenShift.
D. services
Incorrect:
Servicesare a core Kubernetes resource used to expose applications internally within the cluster. They are not unique to OpenShift.
Why These Resources?
Routes:Extend Kubernetes Ingress to provide advanced external access capabilities, such as custom domain mappings and TLS termination.
Builds:Simplify the process of building container images directly within the OpenShift platform, enabling streamlined CI/CD workflows.
JNCIA Cloud References:
The JNCIA-Cloud certification covers OpenShift's unique resources as part of its curriculum on container orchestration platforms. Understanding the differences between OpenShift and Kubernetes resources is essential for leveraging OpenShift's full capabilities.
For example, Juniper Contrail integrates with OpenShift to provide advanced networking features, ensuring secure and efficient traffic routing for Routes and Builds.
Copyright © 2014-2025 Examstrust. All Rights Reserved
