Exhibit
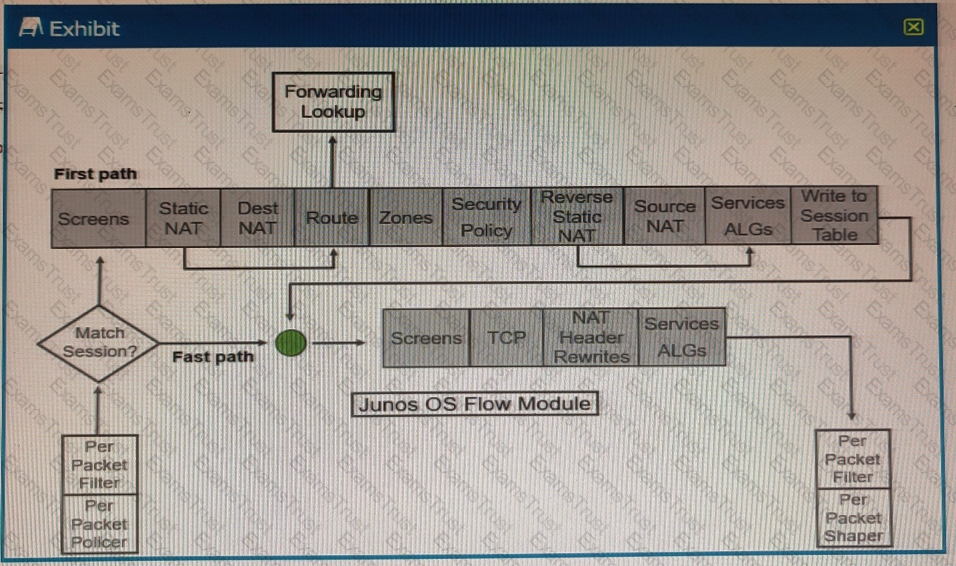
Referring to the SRX Series flow module diagram shown in the exhibit, where is application security processed?
You are asked to determine how much traffic a popular gaming application is generating on your network.
Which action will you perform to accomplish this task?
Which two statements are correct about security policy changes when using the policy rematch feature? (Choose two.)
Which two statements are correct about a reth LAG? (Choose two.)
Click the Exhibit button.
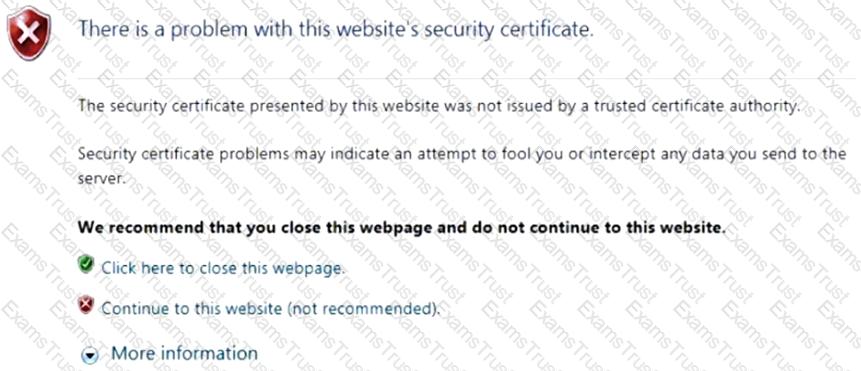
You have implemented SSL client protection proxy. Employees are receiving the error shown in the exhibit.
How do you solve this problem?
Regarding static attack object groups, which two statements are true? (Choose two.)
You need to deploy an SRX Series device in your virtual environment.
In this scenario, what are two benefits of using a CSRX? (Choose two.)
Which two statements about SRX chassis clustering are correct? (Choose two.)
Which two statements are true about application identification? (Choose two.)
Which two statements are correct about SSL proxy server protection? (Choose two.)
Which two statements are true about Juniper ATP Cloud? (Choose two.)
Exhibit
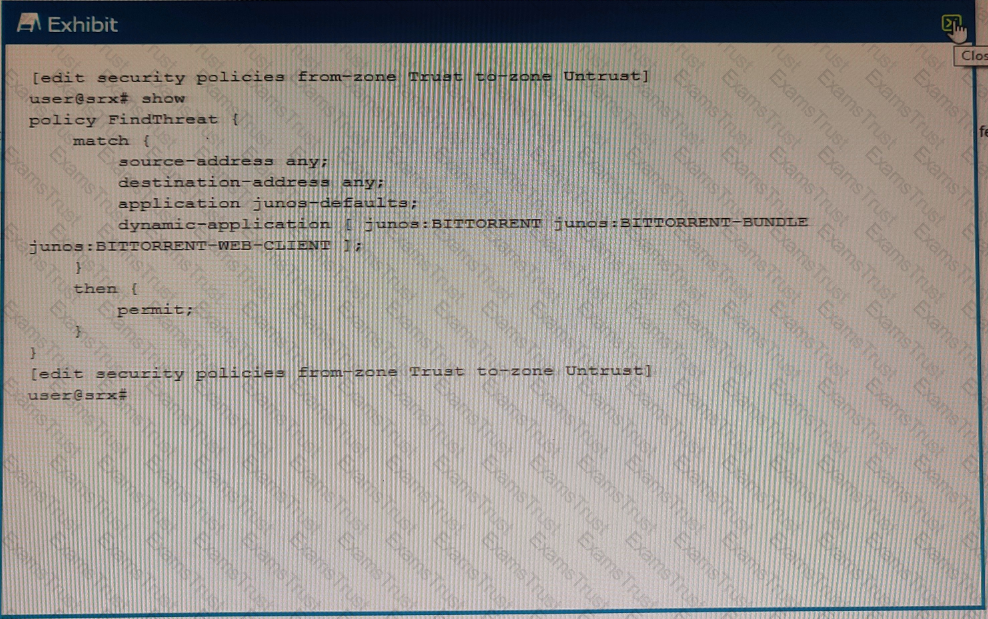
You are asked to track BitTorrent traffic on your network. You need to automatically add the workstations to the High_Risk_Workstations feed and the servers to the BitTorrent_Servers feed automatically to help mitigate future threats.
Which two commands would add this functionality to the FindThreat policy? (Choose two.)
A)

B)

C)

D)

Which two functions does Juniper ATP Cloud perform to reduce delays in the inspection of files? (Choose two.)
After JSA receives external events and flows, which two steps occur? (Choose two.)
Exhibit
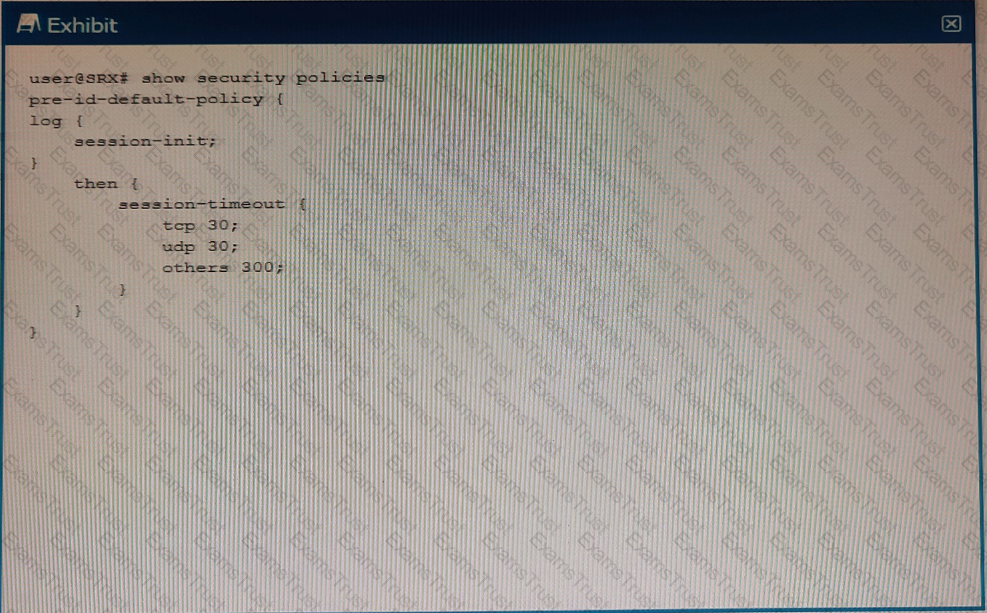
Which two statements are correct about the configuration shown in the exhibit? (Choose two.)
You want to use IPS signatures to monitor traffic.
Which module in the AppSecure suite will help in this task?
What are two requirements for enabling AppQoE? (Choose two.)
On an SRX Series firewall, what are two ways that Encrypted Traffic Insights assess the threat of the traffic? (Choose two.)
Exhibit
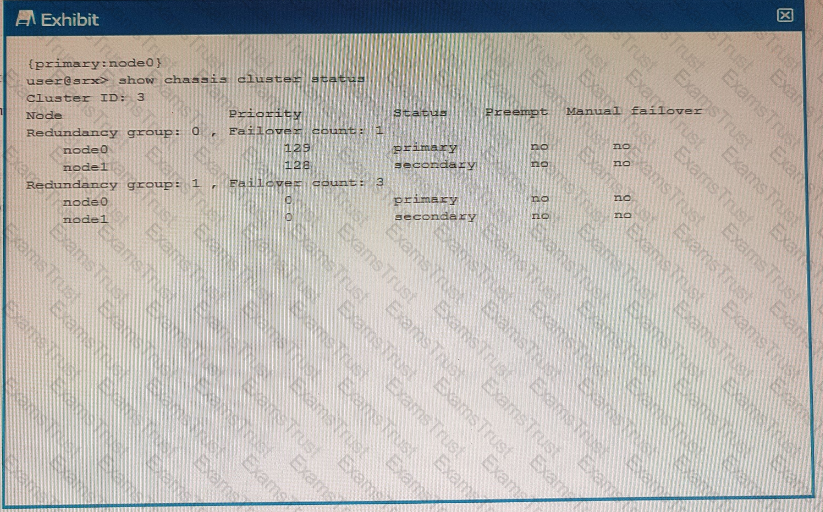
Using the information from the exhibit, which statement is correct?
You are asked to block malicious applications regardless of the port number being used.
In this scenario, which two application security features should be used? (Choose two.)
You are configuring logging for a security policy.
In this scenario, in which two situations would log entries be generated? (Choose two.)
You are asked to implement IPS on your SRX Series device.
In this scenario, which two tasks must be completed before a configuration will work? (Choose two.)
Your manager asks you to provide firewall and NAT services in a private cloud.
Which two solutions will fulfill the minimum requirements for this deployment? (Choose two.)
You want to be alerted if the wrong password is used more than three times on a single device within five minutes.
Which Juniper Networks solution will accomplish this task?
What information does encrypted traffic insights (ETI) use to notify SRX Series devices about known malware sites?
You administer a JSA host and want to include a rule that sets a threshold for excessive firewall denies and sends an SNMP trap after receiving related syslog messages from an SRX Series firewall.
Which JSA rule type satisfies this requirement?
Which two statements are correct about Juniper ATP Cloud? (Choose two.)
Exhibit
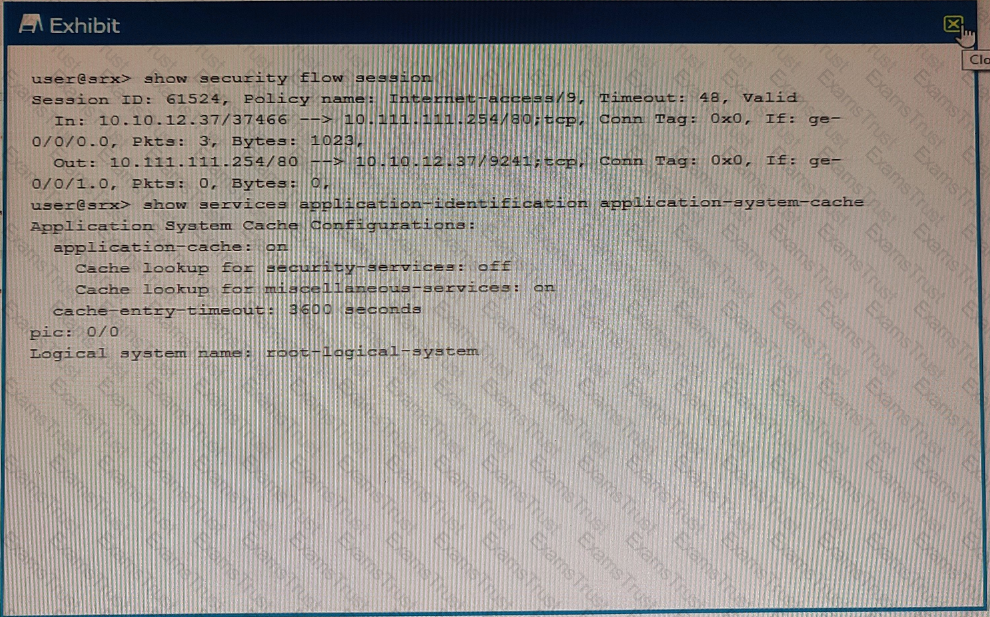
Referring to the exhibit which statement is true?