What are three attributes that APBR queries from the application system cache module. (Choose Three)
Exhibit:
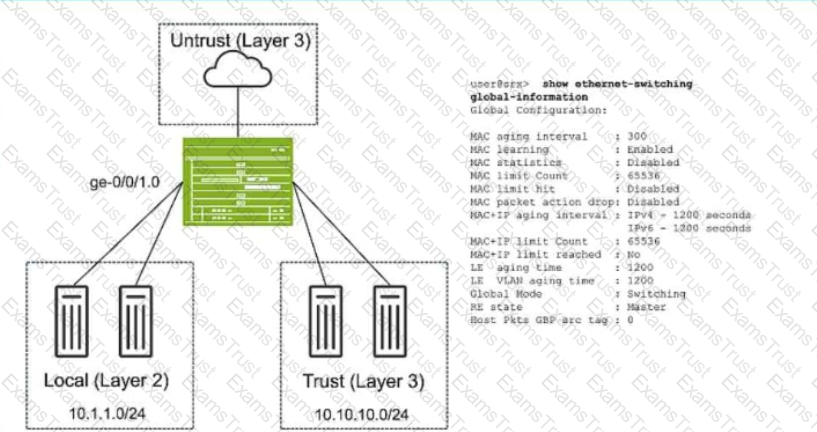
Referring to the exhibit, which two statements are true? (Choose two.)
Exhibit:
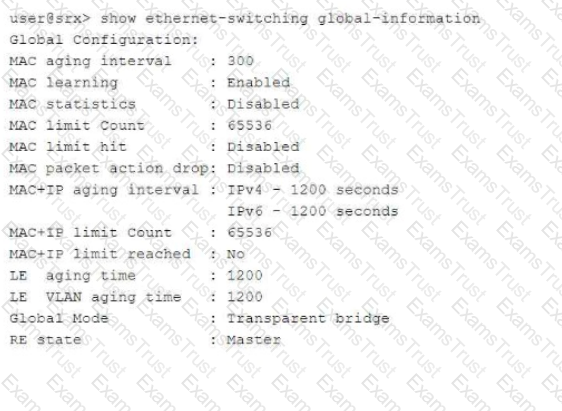
Referring to the exhibit, which two statements are correct? (Choose two.)
Exhibit:

The Ipsec VPN does not establish when the peer initiates, but it does establish when the SRX
series device initiates. Referring to the exhibit, what will solve this problem?
You are asked to configure tenant systems.
Which two statements are true in this scenario? (Choose two.)
You want to enable transparent mode on your SRX series device.
In this scenario, which three actions should you perform? (Choose three.)
You are configuring an interconnect logical system that is configured as a VPLS switch to allow two logical systems to communicate.
Which two parameters are required when configuring the logical tunnel interfaces? (Choose two.)
You are asked to create multiple virtual routers using a single SRX Series device. You must ensure that each virtual router maintains a unique copy of the routing protocol daemon (RPD) process.
Which solution will accomplish this task?
Exhibit:
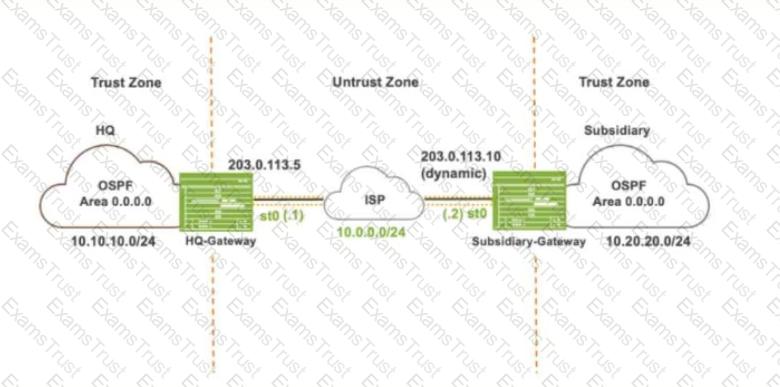
Referring to the exhibit, which IKE mode will be configured on the HQ-Gateway and Subsidiary-Gateway?
You are asked to select a product offered by Juniper Networks that can collect and assimilate data from all probes and determine the optimal links for different applications to maximize the full potential of AppQoE.
Which product provides this capability?
Exhibit:
Which two statements are correct about the output shown in the exhibit. (Choose Two)
Which two statements describe the behavior of logical systems? (Choose two.)
Your customer needs embedded security in an EVPN-VXLAN solution.
What are two benefits of adding an SRX Series device in this scenario? (Choose two.)
You are deploying IPsec VPNs to securely connect several enterprise sites with ospf for dynamic
routing. Some of these sites are secured by third-party devices not running Junos.
Which two statements are true for this deployment? (Choose two.)
Which role does an SRX Series device play in a DS-Lite deployment?
A customer wants to be able to initiate a return connection to an internal host from a specific
Server.
Which NAT feature would you use in this scenario?
The SRX series device is performing static NAT. you want to ensure that host A can reach the
internal webserver using domain name.
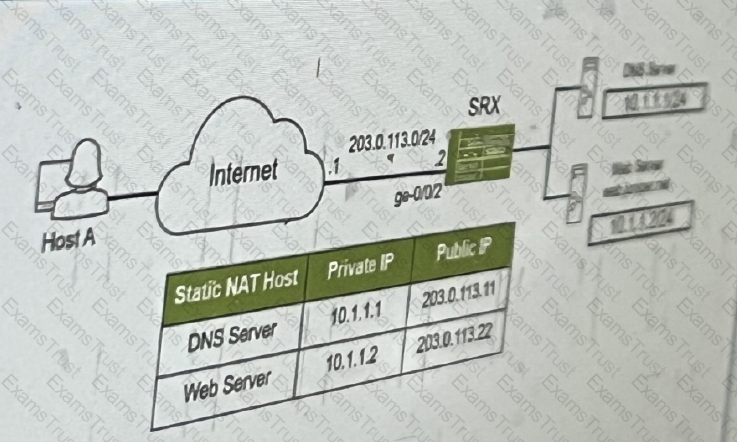
Referring to the exhibit, which two Junos features are required to accomplish this task? (Choose two.)
You need to set up source NAT so that external hosts can initiate connections to an internal device, but only if a connection to the device was first initiated by the internal device.
Which type of NAT solution provides this functionality?
Which two statements are true when setting up an SRX Series device to operate in mixed mode? (Choose two.)
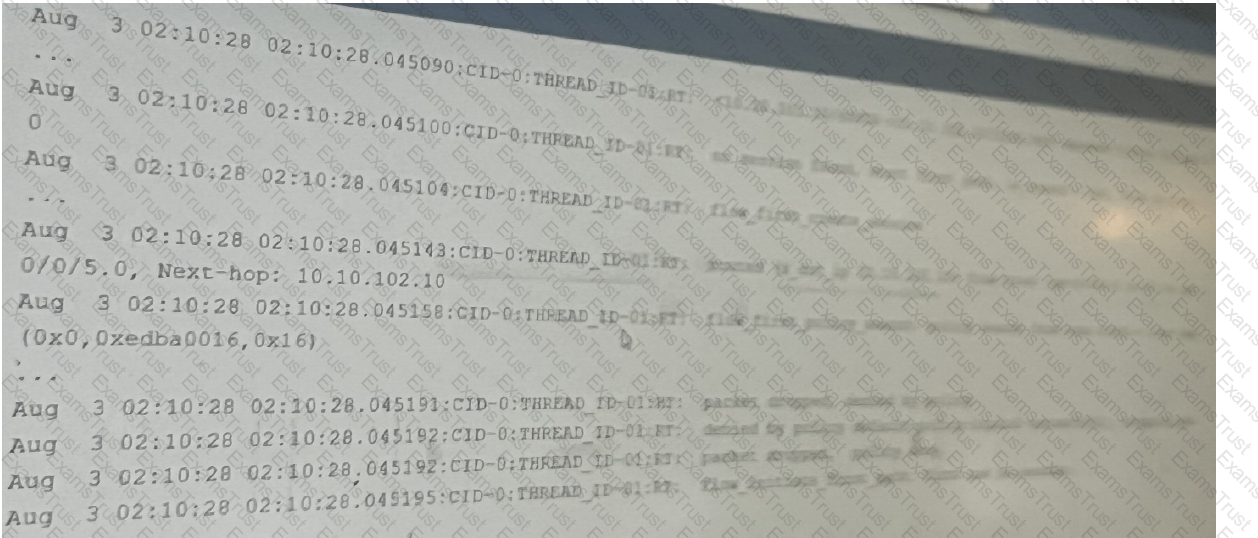
Exhibit:
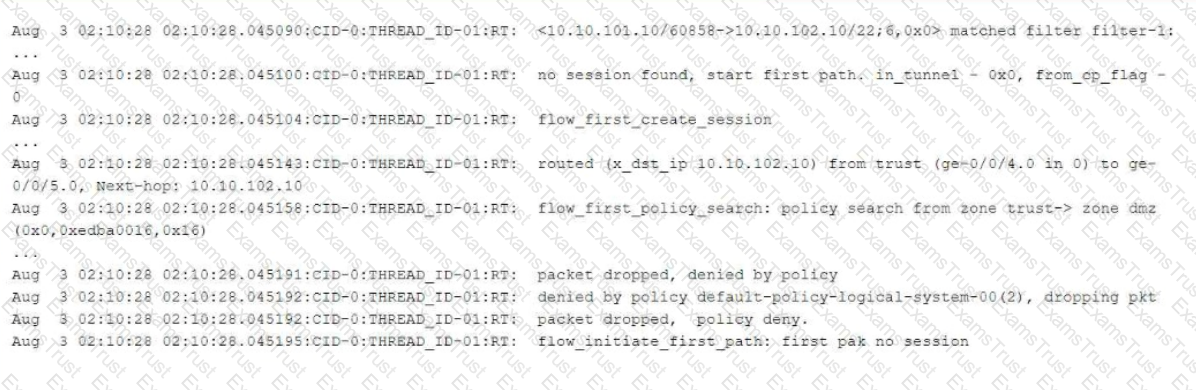
Referring to the flow logs exhibit, which two statements are correct? (Choose two.)
Click the Exhibit button.
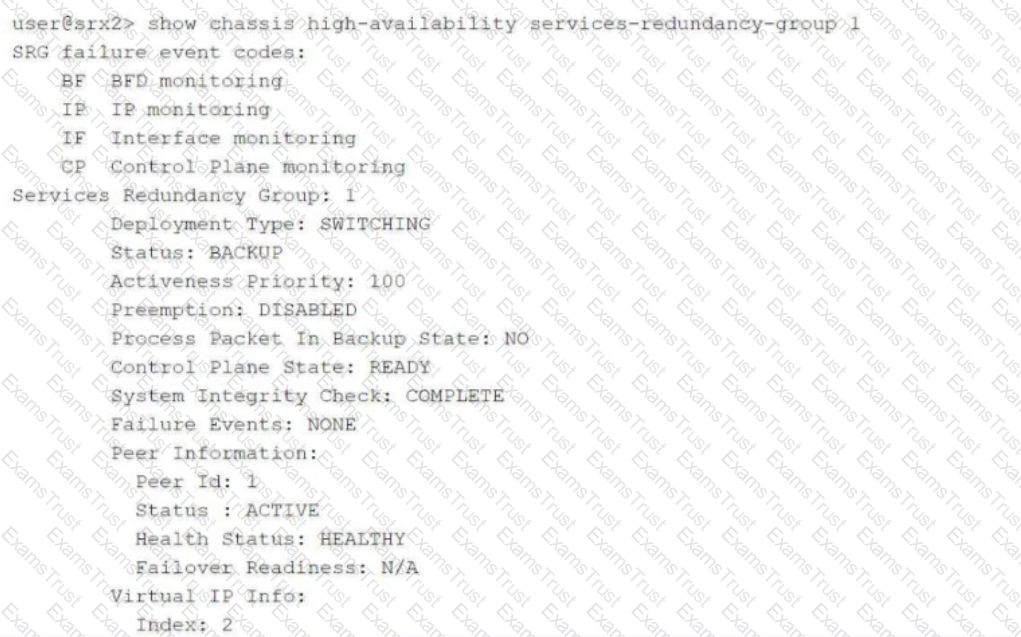
Referring to the exhibit, which two statements are correct? (Choose two.)
You configure two Ethernet interfaces on your SRX Series device as Layer 2 interfaces and add them to the same VLAN. The SRX is using the default L2-learning setting. You do not add the interfaces to a security zone.
Which two statements are true in this scenario? (Choose two.)
You want to bypass IDP for traffic destined to social media sites using APBR, but it is not working and IDP is dropping the session.
What are two reasons for this problem? (Choose two.)
You want to configure the SRX Series device to map two peer interfaces together and ensure that there is no switching or routing lookup to forward traffic.
Which feature on the SRX Series device is used to accomplish this task?
Click the Exhibit button.
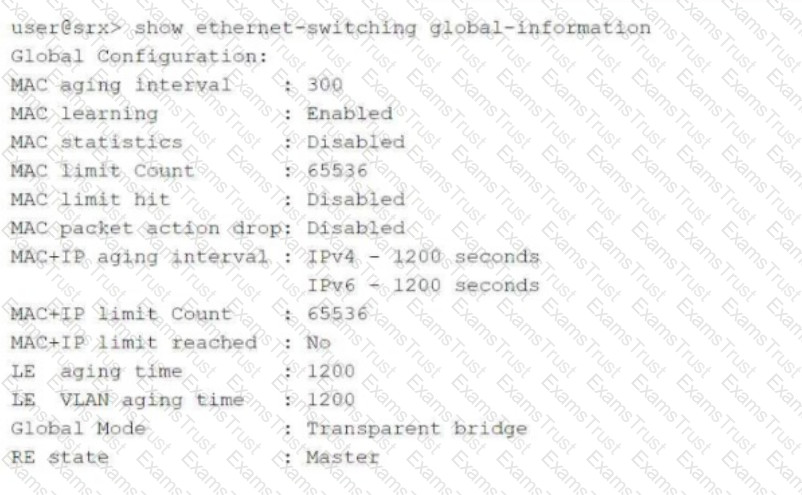
Referring to the exhibit, which two statements are correct? (Choose two.)
Click the Exhibit button.
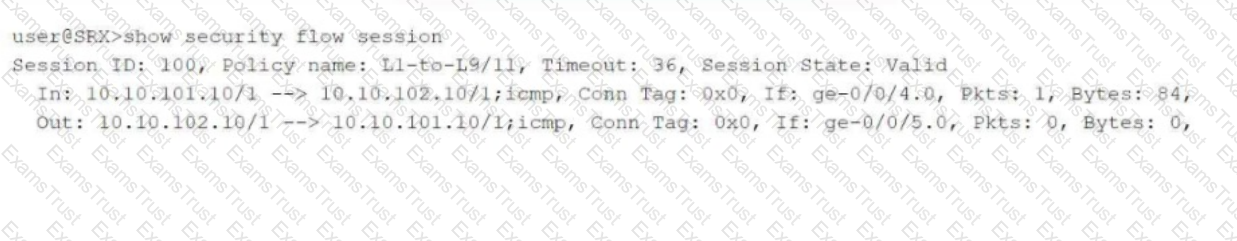
Referring to the exhibit, which two statements are true? (Choose two.)
Exhibit:
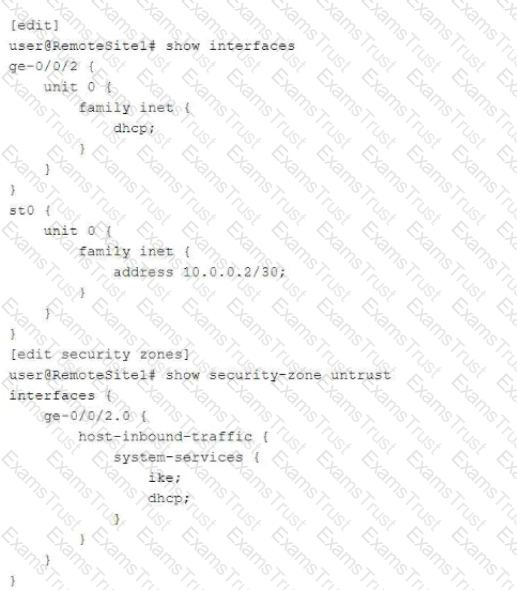
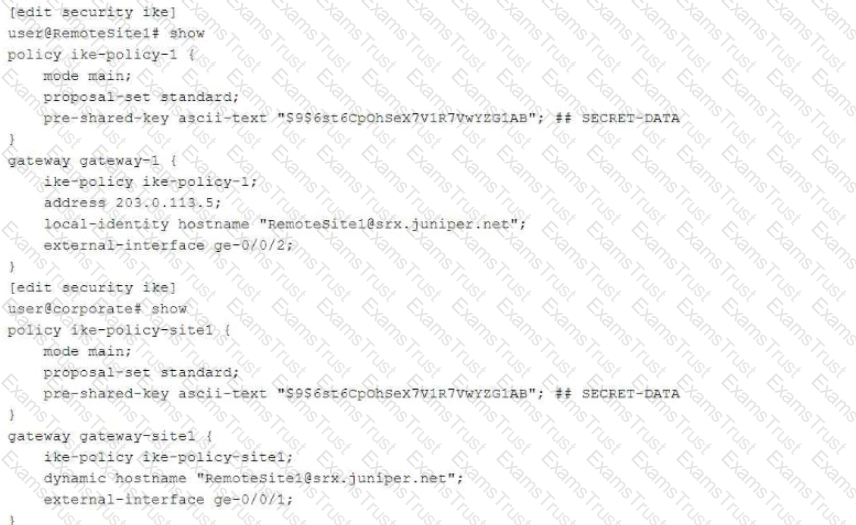
You are troubleshooting a new IPsec VPN that is configured between your corporate office and the RemoteSite1 SRX Series device. The VPN is not currently establishing. The RemoteSite1 device is being assigned an IP address on its gateway interface using DHCP.
Which action will solve this problem?
You are asked to see if your persistent NAT binding table is exhausted.
Which show command would you use to accomplish this task?
You want to use a security profile to limit the system resources allocated to user logical systems.
In this scenario, which two statements are true? (Choose two.)
Exhibit:
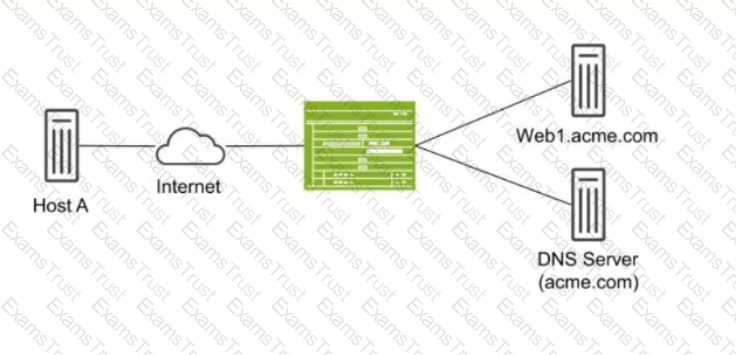
Host A shown in the exhibit is attempting to reach the Web1 webserver, but the connection is failing. Troubleshooting reveals that when Host A attempts to resolve the domain name of the server (web.acme.com), the request is resolved to the private address of the server rather than its public IP.
Which feature would you configure on the SRX Series device to solve this issue?
Which encapsulation type must be configured on the lt-0/0/0 logical units for an interconnect
logical systems VPLS switch?
Which two statements are true about the procedures the Junos security device uses when handling traffic destined for the device itself? (Choose two.)
The exhibit shows part of the flow session logs.
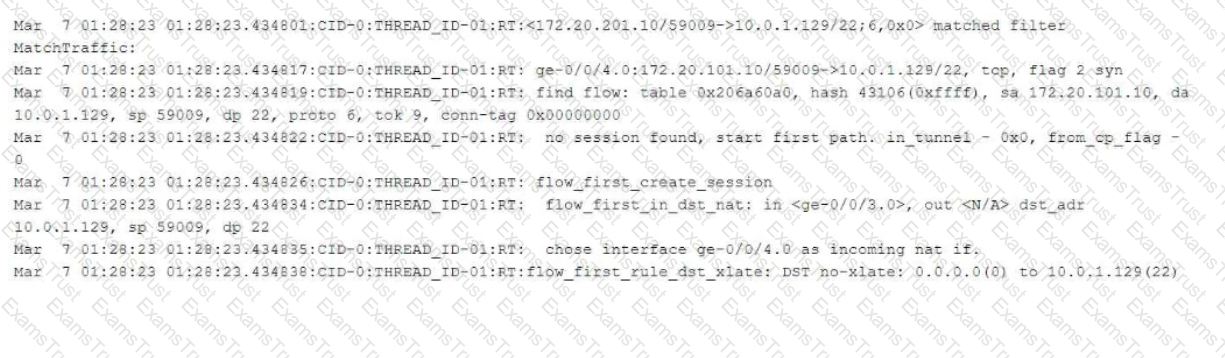
Which two statements are true in this scenario? (Choose two.)
Which two statements are correct about the ICL in an active/active mode multinode HA environment? (Choose two.)