What is the purpose of the Filesystem Hierarchy Standard?
It is a security model used to ensure files are organized according to their permissions and accessibility.
It provides unified tools to create, maintain and manage multiple filesystems in a common way.
It defines a common internal structure of inodes for all compliant filesystems.
Itis a distribution neutral description of locations of files and directories.
The Filesystem Hierarchy Standard is a distribution neutral description of locations of files and directories. According to the first result, it is a reference describing the conventions used for the layout of Unix-like systems. It is maintained by the Linux Foundation and the latest version is 3.0
Which of the following is the device file name for the second partition on the only SCSI drive?
/dev/hda1
/dev/sda2
/dev/sd0a2
/dev/sd1p2
The correct device file name for the second partition on the only SCSI drive is /dev/sda2. This is because SCSI drives use the naming scheme sdX, where X is a letter starting from a for the first drive, b for the second drive, and so on. The partitions on each drive are numbered from 1 to the maximum number of partitions supported by the drive. Therefore, the first partition on the first SCSI drive is /dev/sda1, the second partition on the first SCSI drive is /dev/sda2, the first partition on the second SCSI drive is /dev/sdb1, and so on. The other options are incorrect because they do not follow the SCSI naming scheme. Option A is wrong because it uses the naming scheme for IDE drives, which is hdX. Option C is wrong because it uses the naming scheme for BSD drives, which is sdXaY, where X is a number and Y is a letter. Option D is wrong because it uses the naming scheme for Solaris drives, which is sdXpY, where X is a number and Y is a number. References:
[LPI Linux Essentials - 2.1 Using Devices, Linux Filesystems, Filesystem Hierarchy Standard]
[LPI Linux Essentials - 2.2 Mounting, Unmounting Filesystems]
[LPI Linux Essentials - 2.3 Disk Partitions]
Device file - ArchWiki
What is the Linux drive naming scheme? - Ask Ubuntu
Which of the following are modes of the vi editor? (Choose two.)
edit mode
insert mode
change mode
review mode
command mode
The modes of the vi editor that are correct are insert mode and command mode. The vi editor is a modal editor, which means that it has different modes for different operations. The insert mode allows the user to insert text into the file. The command mode allows the user to execute commands, such as saving, quitting, moving the cursor, searching, replacing, and so on. The user can switch between the modes by pressing certain keys, such as Esc, i, a, o, and others. The edit mode, change mode, and review mode are not valid modes of the vi editor. References: LPI Exam 101 Detailed Objectives, Topic 103: GNU and Unix Commands, Weight: 25, Objective 103.8: Use vi to create and edit files, vi editor
When using regular expressions, which of the following characters match the beginning of a line?
^
?
*
+
$
When using regular expressions, the ^ character matches the beginning of a line. For example, ^Hello will match any line that starts with Hello. The ? character matches zero or one occurrence of the preceding character or group. For example, colou?r will match both color and colour. The * character matches zero or more occurrences of the preceding character or group. For example, ab*c will match ac, abc, abbc, abbbc, and so on. The + character matches one or more occurrences of the preceding character or group. For example, ab+c will match abc, abbc, abbbc, and so on, but not ac. The charactermatchestheendofaline.Forexample,World will match any line that ends with World. References: [LPI Exam 101 Detailed Objectives], Topic 103: GNU and Unix Commands, Weight: 25, Objective 103.7: Use regular expressions with the standard Linux utilities, Regular Expressions
Which file in /proc describes the IRQs that are used by various kernel drivers? (Specify the file name only without any path.)
interrupts
How many fields are in a syntactically correct line of /etc/fstab?
3
4
5
6
7
A syntactically correct line of /etc/fstab must have six fields, separated by whitespaces or tabs. The fields are as follows:
The device file, UUID or label or other means of locating the partition or data source.
The mount point, which is the directory where the device is/will be mounted.
The file system type, which specifies the type of the file system.
The mount options, which are a comma-separated list of options that control how the file system is mounted and accessed.
The dump flag, which is a number that indicates whether the file system should be backed up by the dump utility. This is an outdated method and should not be used.
The fsck order, which is a number that indicates the order in which the file system should be checked by the fsck utility at boot time. A value of 0 means no check, a value of 1 means the root file system, and a value of 2 or higher means other file systems.
For example, a line of /etc/fstab could look like this:
UUID=80b496fa-ce2d-4dcf-9afc-bcaa731a67f1 /mnt/example ext4 defaults 0 2
This means that the file system with the UUID 80b496fa-ce2d-4dcf-9afc-bcaa731a67f1 is mounted on /mnt/example, has the type ext4, uses the default mount options, is not backed up by dump, and is checked by fsck after the root file system.
Which of the following command lines creates or, in case it already exists, overwrites a file called data with the output of ls?
ls 3> data
ls >& data
ls > data
ls >> data
The command line that will create or, in case it already exists, overwrite a file called data with the output of ls is ls > data. The > character is a redirection operator that redirects the standard output (STDOUT) of a command to a file. If the file does not exist, it will be created. If the file already exists, it will be overwritten. The 3> character is not a valid redirection operator. The >& character is a redirection operator that redirects both standard output (STDOUT) and standard error (STDERR) of a command to a file. The >> character is a redirection operator that appends the standard output (STDOUT) of a command to a file, without overwriting the existing file contents. References: LPI Exam 101 Detailed Objectives, Topic 103: GNU and Unix Commands, Weight: 25, Objective 103.3: Perform basic file management, Redirection
Which of the following commands can be used to display the inode number of a given file?
inode
ls
ln
cp
The command ls can be used to display the inode number of a given file by using the -i option. The inode number is a unique identifier for each file in a Linux file system. It contains information about the file’s attributes, such as size, permissions, ownership, timestamps, and location on the disk12. For example, ls -i file.txt will show the inode number of the file file.txt in the current directory. The command inode does not exist in Linux. The command ln can be used to create links to files, but not to display their inode numbers. The command cp can be used to copy files, but not to display their inode numbers3. References: 1: What is an Inode in Linux? 2: Understanding Linux File System Inodes 3: Linux Commands Cheat Sheet
Which of the following commands is used to change metadata and options for ext3 filesystems?
mod3fs
tune3fs
mod2fs
tune2fs
dump2fs
The tune2fs command is used to change metadata and options for ext2, ext3, and ext4 filesystems. The tune2fs command can adjust various parameters such as the maximum mount count, the check interval, the reserved blocks percentage, the volume label, and the UUID. The tune2fs command can also enable or disable some filesystem features, such as the journal, the dir_index, the acl, and the user_xattr. The tune2fs command requires the device name or the UUID of the filesystem as an argument, and one or more options to specify the changes to be made. For example, to change the volume label of an ext3 filesystem on /dev/sda1 to “data”, use the following command:
tune2fs -L data /dev/sda1
The other options are not valid commands or options. The mod3fs and mod2fs commands do not exist on a standard Linux system. The tune3fs command is a synonym for tune2fs, but it is not commonly used. The dump2fs command is used to display the superblock and blocks group information for ext2, ext3, and ext4 filesystems, but it does not change any parameters or options. References:
tune2fs - adjust tunable filesystem parameters on ext2/ext3/ext4 …
Chapter 5. The Ext3 File System - Red Hat Customer Portal
Chapter 37. Getting started with an ext3 file system - Red Hat Customer …
In order to display all currently mounted filesystems, which of the following commands could be used? (Choose TWO correct answers.)
cat /proc/self/mounts
free
mount
lsmounts
cat /proc/filesystems
The correct commands to display all currently mounted filesystems are cat /proc/self/mounts and mount. The cat /proc/self/mounts command reads the contents of the /proc/self/mounts file, which is a symbolic link to /proc/mounts. This file contains information about all the filesystems that are currently mounted on the system, as reported by the kernel. The mount command without any arguments shows all the mounted filesystems, as recorded by the mount and umount commands. The other options are incorrect because they do not display the mounted filesystems. The free command shows the amount of free and used memory in the system. The lsmounts command is not a standard Linux command. The cat /proc/filesystems command shows the filesystem types that are supported by the kernel. References:
[LPI Linux Essentials - 2.2 Mounting, Unmounting Filesystems]
How to get the complete and exact list of mounted filesystems in Linux? - Unix & Linux Stack Exchange
4 Commands to List Mounted File Systems in Linux - Linux Shell Tips
How To Show Mounted Devices In Linux Operating System
How to Check if a Filesystem is Mounted in Linux?
When planning a partition scheme, which of the following directories could be considered for separate partitions? (Choose three.)
/etc
/home
/var
/lib
/opt
When planning a partition scheme, it is advisable to consider creating separate partitions for some directories that may contain large amounts of data, have different backup or security requirements, or benefit from being on different filesystems. Some of the common directories that could be considered for separate partitions are:
/home: This directory contains the personal files and settings of the users. Creating a separate partition for /home can make it easier to backup, restore, or upgrade the system without affecting the user data. It can also improve security by allowing different mount options such as noexec or nosuid. Additionally, it can help to prevent the system from becoming unusable if the users fill up their disk space with personal files123.
/var: This directory contains variable data such as logs, caches, spool files, databases, and web server content. Creating a separate partition for /var can prevent the system from crashing or becoming unresponsive if the /var partition fills up due to excessive logging or caching. It can also improve performance by allowing different filesystem options such as noatime or nodiratime. Furthermore, it can enhance security by isolating the data that may be modified by external sources such as web applications or mail servers124.
/opt: This directory contains optional software packages that are not part of the standard distribution. Creating a separate partition for /opt can make it easier to manage, backup, or remove these packages without affecting the rest of the system. It can also allow different filesystem types or features that may be required by some of the software installed in /opt125.
Other directories that could be considered for separate partitions are /boot, /tmp, /usr, and /srv, depending on the system requirements and preferences12 . References:
Linux Partitioning Recommendations | Average Linux User
Linux Disk Partitioning Schemes - Land of Linux
C.3. Recommended Partitioning Scheme - Debian
Which SysV init configuration file is commonly used to set the default run level? (Specify the full name of the file, including path.)
/etc/inittab
The /etc/inittab file is a plain text file that contains information about the initialization process of the system. It defines the default run level, the available run levels, and the actions to be taken when entering or leaving a run level. The default run level is the mode of operation that the system starts up into, and it determines which services and processes are running. The default run level is specified by a line similar to the following in the /etc/inittab file:
id:5:initdefault:
The number after the first colon indicates the default run level, which can range from 0 to 6. The meaning of each run level is:
0 — Halt
1 — Single-user text mode
2 — Not used (user-definable)
3 — Full multi-user text mode
4 — Not used (user-definable)
5 — Full multi-user graphical mode (with an X-based login screen)
6 — Reboot
To change the default run level, edit the /etc/inittab file as root and change the number to the desired run level. For example, to change the default run level to 3, use the following command:
sudo nano /etc/inittab
And change the line to:
id:3:initdefault:
Then save and exit the file. The changes will take effect on the next reboot.
Pressing the Ctrl-C combination on the keyboard while a command is executing in the foreground sends which of the following signal codes?
1(SIGHUP)
2(SIGINT)
3(SIGQUIT)
9(SIGKILL)
15(SIGTERM)
The command line that will create or, in case it already exists, overwrite a file called data with the output of ls is ls > data. The > character is a redirection operator that redirects the standard output (STDOUT) of a command to a file. If the file does not exist, it will be created. If the file already exists, it will be overwritten. The 3> character is not a valid redirection operator. The >& character is a redirection operator that redirects both standard output (STDOUT) and standard error (STDERR) of a command to a file. The >> character is a redirection operator that appends the standard output (STDOUT) of a command to a file, without overwriting the existing file contents. References: LPI Exam 101 Detailed Objectives, Topic 103: GNU and Unix Commands, Weight: 25, Objective 103.3: Perform basic file management, Redirection
Which of the following Linux filesystems preallocates a fixed number of inodes at the filesystem's make/creation time and does NOT generate them as needed? (Choose TWO correct answers.)
ext3
JFS
ext2
XFS
procfs
The ext3 and ext2 filesystems preallocate a fixed number of inodes at the filesystem’s make/creation time and do not generate them as needed. This means that the number of inodes in these filesystems is determined by the size of the partition and the inode ratio, which is usually 16 KB per inode. The inode ratio can be specified when creating the filesystem with the mke2fs command. The number of inodes in these filesystems cannot be changed dynamically, unless the filesystem is reformatted. This can lead to inode exhaustion, which occurs when all the available inodes are used up, even if there is still free disk space. To avoid this problem, it is advisable to estimate the number of files and directories that will be stored on the filesystem and adjust the inode ratio accordingly. The other options are incorrect because they do not preallocate a fixed number of inodes at the filesystem’s make/creation time. The JFS and XFS filesystems use dynamic inode allocation, which means that they create inodes as needed, depending on the file and directory creation. The procfs filesystem is a virtual filesystem that does not store any data on the disk, but provides information about the processes and the kernel. Therefore, it does not have any inodes.
For more information on how inodes work and how to manage them, you can refer to the following articles:
Inodes in Linux: limit, usage and helpful commands | Stackscale
filesystems - What is an inode? - Unix & Linux Stack Exchange
Allocation Methods | Linux.org
Which of the following commands changes all occurrences of the word “bob” in file data to “Bob” and prints the result to standard output?
sed‘/bob/Bob’ data
sed‘s/bob/Bob/g’ data
sed‘s/bob/Bob/’ data
sed‘/bob/Bob/’ data
sed‘s/bob,Bob/’ data
The sed command is used to perform various text processing tasks on a file or a stream. The s command is used to substitute a pattern with a replacement. The g flag is used to replace all occurrences of the pattern in a line. The / character is used to separate the pattern, the replacement, and the flags. Therefore, the command sed‘s/bob/Bob/g’ data will change all occurrences of the word “bob” in file data to “Bob” and print the result to standard output. The other commands are incorrect because they either use the wrong syntax or do not replace all occurrences of the word “bob”. References:
LPI 101-500 Exam Objectives, Topic 103.7, Weight 4
LPI Learning Materials, Chapter 3.7, Basic Scripting
Web Search Results, 1
What command changes the nice level of a running process? (Specify ONLY the command without any path or parameters)
renice
The renice command changes the nice level of a running process. The nice level is a value that affects the scheduling priority of a process. A lower nice level means a higher priority and a higher nice level means a lower priority. The renice command requires the process ID (PID) of the target process and the new nice level as arguments. For example, renice -n 10 1234 will change the nice level of the process with PID 1234 to 10. References: LPI Exam 101 Detailed Objectives, Topic 103: GNU and Unix Commands, Weight: 25, Objective 103.3: Perform basic file management, renice command
Which permissions and ownership should the file /etc/passwd have?
-rw-------1 rootroot531 Jun 5 22:45 /etc/passwd
-rw-r--r--1 rootroot531 Jun 5 22:45 /etc/passwd
-rw-r--r--1 11531 Jun 5 22:45 /etc/passwd
-rw-------1 11531 Jun 5 22:45 /etc/passwd
The correct permissions and ownership for the file /etc/passwd are:
B. -rw-r–r-- 1 root root 531 Jun 5 22:45 /etc/passwd
The /etc/passwd file is a plain text-based database that contains information for all user accounts on the system. It is owned by root and has 644 permissions. The file can only be modified by root or users with sudo privileges and readable by all system users. The permissions and ownership of the file are important for the security and functionality of the system. The permissions and ownership of the file can be viewed by using the ls -l command. For example:
ls -l /etc/passwd
The output of the command will show the following information:
-rw-r–r-- 1 root root 531 Jun 5 22:45 /etc/passwd
The first column shows the permissions of the file, which are composed of 10 characters. The first character indicates the file type, which is - for regular files. The next nine characters indicate the permissions for the user (owner), the group, and the others, respectively. Each set of three characters indicates the read ®, write (w), and execute (x) permissions. A dash (-) means no permission. In this case, the permissions are:
rw- for the user, which means the user can read and write the file, but not execute it.
r-- for the group, which means the group can only read the file, but not write or execute it.
r-- for the others, which means the others can only read the file, but not write or execute it.
The second and third columns show the owner and the group of the file, which are both root. The root user is the superuser or the administrator of the system, who has full access and control over the system. The root group is the primary group of the root user, which usually has no other members.
The fourth column shows the size of the file in bytes, which is 531 in this case. The fifth and sixth columns show the date and time of the last modification of the file, which are Jun 5 22:45 in this case. The last column shows the name of the file, which is /etc/passwd in this case.
The other options are not correct because:
A. -rw------- 1 root root 531 Jun 5 22:45 /etc/passwd: This option has the wrong permissions for the file. The permissions are 600, which means only the user (root) can read and write the file, and the group and the others have no permissions at all. This would prevent the system users from reading the file, which would cause problems for the login process and other utilities that rely on the file.
C. -rw-r–r-- 1 1 531 Jun 5 22:45 /etc/passwd: This option has the wrong owner and group for the file. The owner and group are both 1, which is the numeric ID of the user and group. However, the numeric ID of the root user and group is 0, not 1. The user and group with the numeric ID of 1 are usually bin, which is a system user and group that own some system binaries and directories. The bin user and group should not own the /etc/passwd file, as this would compromise the security and functionality of the system.
D. -rw------- 1 1 531 Jun 5 22:45 /etc/passwd: This option has both the wrong permissions and the wrong owner and group for the file. The permissions are 600, which means only the user can read and write the file, and the owner and group are both 1, which is the numeric ID of the bin user and group. This would prevent the system users from reading the file, and give the bin user and group full access to the file, which would cause problems for the security and functionality of the system.
What does the command grub-install /dev/sda do?
GRUB creates partitions on the device/dev/sdato be used with Linux.
GRUB sets the default BIOS boot device to/dev/sda.
GRUB installs all required files and configures the boot loader on device/dev/sda.
GRUB recompiles the Linux Kernel and installs it on the Master Boot Record of device/dev/sda.
The grub-install command is used to install the GRUB boot loader on a device, such as a hard disk or a floppy disk. The command takes one argument, which is the device name where the boot loader should be installed. The command copies the GRUB files from the /boot/grub directory to the device and writes the boot code to the Master Boot Record (MBR) or the boot sector of the device. The command also creates a device map file in /boot/grub/device.map, which maps the BIOS device names to the Linux device names. The grub-install command is useful for setting up a dual-boot system or for repairing a broken GRUB installation. The command can also take various options to customize the installation, such as --boot-directory, --efi-directory, --removable, --force-lba, and --no-floppy. References:
GNU GRUB Manual 2.06: Installing GRUB using grub-install
grub-install Command Options – The Geek Diary
Which of the following commands is used to update the list of available packages when using dpkg based package management?
apt-get update
apt-get upgrade
apt-cache update
apt-get refresh
apt-cache upgrade
The command that is used to update the list of available packages when using dpkg based package management is apt-get update12. The apt-get command is a high-level tool that works with dpkg and provides a user-friendly interface for managing packages3. The apt-get update command is used to synchronize the package index files from the sources specified in the /etc/apt/sources.list file12. This command does not install or upgrade any packages, but only downloads the information about the latest versions and dependencies of the packages12. The apt-get update command is usually run before the apt-get upgrade or apt-get install commands, which are used to upgrade or install packages respectively12.
The other options in the question are not correct because:
B. apt-get upgrade: This command is used to upgrade the installed packages to the latest versions, not to update the list of available packages12.
C. apt-cache update: There is no such command in Linux. The apt-cache command is used to query and display information about the packages, not to update them4.
D. apt-get refresh: There is no such command in Linux. The closest command is apt-get update, which is the correct answer.
E. apt-cache upgrade: There is no such command in Linux. The closest command is apt-get upgrade, which is not the correct answer.
Typically, which top level system directory is used for files and data that change regularly while the system is running and are to be kept between reboots? (Specify only the top level directory)
/var
/var/,
Var
var/
The top-level system directory that is used for files and data that change regularly while the system is running and are to be kept between reboots is /var. The /var directory contains variable data that changes in size as the system runs. For instance, log files, mail directories, databases, and printing spools are stored in /var. These files and data are not temporary and need to be preserved across system reboots. The /var directory is one of the few directories that are recommended to be on a separate partition, according to the Filesystem Hierarchy Standard (FHS)1. This is because the /var directory can grow unpredictably and fill up the / partition, which can cause system instability or failure. By having /var on a separate partition, we can limit the amount of disk space that can be used by variable data and prevent users from affecting the / partition. The /var directory is also a common target for malicious attacks, so having it on a separate partition can improve the security and isolation of the system. References:
Filesystem Hierarchy Standard
Which of the following commands overwrites the bootloader located on /dev/sda without overwriting the partition table or any data following it?
dd if=/dev/zero of=/dev/sda bs=512
dd if=/dev/zero of=/dev/sda bs=512 count=1
dd if=/dev/zero of=/dev/sda bs=440 count=1
dd if=/dev/zero of=/dev/sda bs=440
The dd command is used to copy data from one device or file to another, with optional parameters to specify the block size (bs), the number of blocks to copy (count), and other options. The bootloader is typically located in the first 440 bytes of the disk, which is the Master Boot Record (MBR) area. The MBR also contains the partition table, which starts at byte 446 and occupies 64 bytes. Therefore, to overwrite the bootloader without affecting the partition table or any data following it, the command should copy 440 bytes from /dev/zero (a special device that provides null bytes) to /dev/sda (the disk device) and stop after one block. This is achieved by the command: dd if=/dev/zero of=/dev/sda bs=440 count=1 References:
LPI Exam 101 Detailed Objectives, section 1.101.3
dd man page
Master Boot Record
Which file should be edited to select the network locations from which Debian installation package files are loaded?
/etc/dpkg/dpkg.cfg
/etc/apt/apt.conf
/etc/apt/apt.conf.d
/etc/apt/sources.list
/etc/dpkg/dselect.cfg
The /etc/apt/sources.list file is the main configuration file for the Advanced Package Tool (apt), which is used to manage Debian installation package files. This file contains a list of repositories, or sources, from which apt can download and install packages. Each repository is specified by a line that has the following format:
type uri suite [component1] [component2] […]
Where:
type is the access method, such as http, ftp, file, etc.
uri is the Uniform Resource Identifier (URI) of the repository, such as
suite is the distribution code name or archive name, such as stable, testing, unstable, etc.
component is an optional section of the repository, such as main, contrib, non-free, etc.
For example, a typical sources.list file for Debian stable could look like this:
deb stable main contrib non-free deb-src stable main contrib non-free
deb stable/updates main contrib non-free deb-src stable/updates main contrib non-free
deb stable-updates main contrib non-free deb-src stable-updates main contrib non-free
The first two lines specify the main repository for Debian stable, with both binary (deb) and source (deb-src) packages. The next two lines specify the security updates repository for Debian stable, which contains important security fixes. The last two lines specify the stable-updates repository, which contains packages that have been updated after the release of Debian stable.
By editing the /etc/apt/sources.list file, one can select the network locations from which Debian installation package files are loaded. However, it is recommended to use a graphical or command-line tool, such as aptitude or synaptic, to manage the sources.list file, as they can handle the syntax and avoid errors.
Which of the following is correct when talking about mount points?
Every existing directory can be used as a mount point.
Only empty directories can be used as a mount point.
Directories need to have the SetUID flag set to be used as a mount point.
Files within a directory are deleted when the directory is used as a mount point.
The correct answer when talking about mount points is that every existing directory can be used as a mount point. A mount point is a directory in the Linux file-system where a file system, partition, or storage device can be attached and accessed1. To create a mount point, you need root privileges. Mounting means making the contents of the attached file system, partition, or storage device available in the mount point directory1.
The other options are incorrect for the following reasons:
Only empty directories can be used as a mount point. This is not true, as any directory can be used as a mount point, regardless of whether it contains files or not. However, if the directory is not empty, the files inside it will be hidden by the mounted file system until it is unmounted2. Therefore, it is recommended to use empty directories as mount points to avoid confusion and data loss2.
Directories need to have the SetUID flag set to be used as a mount point. This is not true, as the SetUID flag is a special permission that allows a file to be executed with the privileges of its owner, regardless of who runs it3. This flag has nothing to do with mounting file systems, and it is not required for a directory to be used as a mount point4.
Files within a directory are deleted when the directory is used as a mount point. This is not true, as the files within a directory are not deleted when the directory is used as a mount point. They are only hidden by the mounted file system until it is unmounted2. The files are still present on the disk and can be recovered by unmounting the file system or using another mount point to access them2.
In which directory must definition files be placed to add additional repositories to yum?
/etc/yum.repos.d
/etc/yum.repos.d/
yum.repos.d
yum.repos.d/
B
The /etc/yum.repos.d/ directory contains configuration files for additional yum repositories. Each file in this directory should end with .repo and contain information about one or more repositories. The yum command will read all the files in this directory and use them as sources for software packages. The format of the .repo files is similar to the /etc/yum.conf file, which contains the main configuration options for yum. Each .repo file can have one or more sections, each starting with [repository] where repository is a unique identifier for the repository. The section can have various options, such as name, baseurl, enabled, gpgcheck, etc. For example, a .repo file for the EPEL repository could look like this:
[epel] name=Extra Packages for Enterprise Linux 7 - $basearch enabled=1 gpgcheck=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-EPEL-7
Which RPM command will output the name of the package which supplied the file /etc/exports?
rpm -F /etc/exports
rpm -qf /etc/exports
rpm -Kl /etc/exports
rpm -qp /etc/exports
rpm -qi/etc/exports
The RPM command that will output the name of the package which supplied the file /etc/exports is rpm -qf /etc/exports. This command will query the RPM database and find the package that owns or provides the file /etc/exports1. The output will show the package name, version, release, and architecture. For example:

The other options are incorrect for the following reasons:
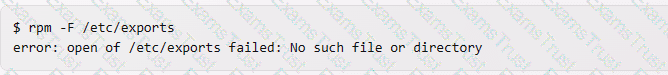
rpm -F /etc/exports. This command will try to freshen or upgrade the package that contains the file /etc/exports, if it is already installed2. This command will not output the package name, but rather install the latest version of the package from a specified source. For example:
rpm -Kl /etc/exports. This command is not valid, as RPM does not have a -Kl option. The -K option is used to verify the signatures of the RPM package files, not the installed files3. The -l option is used to list the files in a package, not to query the package name. For example:

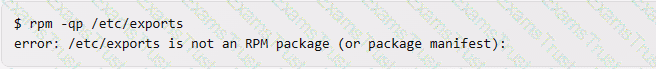
rpm -qp /etc/exports. This command will try to query the package information of the file /etc/exports, as if it was an RPM package file. This command will not output the package name, but rather an error message, as /etc/exports is not a valid RPM package file. For example:
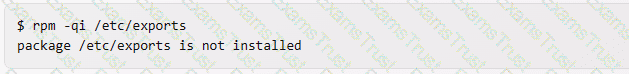
rpm -qi /etc/exports. This command will try to query the information of the package /etc/exports, as if it was an installed package name. This command will not output the package name, but rather an error message, as /etc/exports is not a valid package name. For example:
An administrator has issued the following command:
grub-install --root-directory=/custom-grub /dev/sda
In which directory will new configuration files be found? (Provide the full directory path only without the filename)
/custom-grub/boot/grub/
/custom-grub/boot/grub
The command grub-install is used to install GRUB on a device or a partition. The option --root-directory specifies the directory where GRUB images are put. The default is /boot/grub. The argument /dev/sda specifies the device where GRUB is installed, usually the Master Boot Record (MBR) of the disk. Therefore, the command grub-install --root-directory=/custom-grub /dev/sda will install GRUB on the MBR of /dev/sda and put the GRUB images under the directory /custom-grub/boot/grub. This means that the new configuration files, such as grub.cfg, will be found in the directory /custom-grub/boot/grub. References:
GNU GRUB Manual 2.06: Installing GRUB using grub-install
Installing GRUB using grub-install - GNU GRUB Manual 0.97
Which command will disable swapping on a device? (Specify ONLY the command without any path or parameters.)
Swapoff
/sbin/swapoff
A
The swapoff command is used to disable swapping on a device or a file. It takes the path of the device or file as an argument, or -a to disable all swaps. Disabling swap can improve the performance of the system if there is enough physical memory, or it can be necessary if the swap size needs to be changed. However, disabling swap can also cause problems if the system runs out of memory and has no swap space to use. References:
How to Disable Swap in Linux - Linux Handbook
How to Permanently Disable Swap in Linux? - GeeksforGeeks
LPI Linux Essentials - 1.1 Operating System Basics
Which option to the yum command will update the entire system? (Specify ONLY the option name without any additional parameters.)
update
upgrade
update/upgrade
The yum command is a tool for managing software packages on Red Hat Enterprise Linux and other RPM-based systems. The yum update option will update the entire system by checking the versions of the installed packages and installing the latest available versions from the repositories. The yum upgrade option will do the same, but it will also remove any obsolete packages that are no longer needed by the system. Both options will prompt the user to confirm before proceeding with the update or upgrade process. References:
Yum Command Cheat Sheet for Red Hat Enterprise Linux
"yum update" Explained for Beginners!
How to Install Updates on CentOS 7
Which option to the yum command will update the entire system?
Which of the following commands lists the dependencies of a given dpkg package?
apt-cache depends-onpackage
apt-cache dependencies package
apt-cache depends package
apt-cache requires package
The apt-cache command is used to query the APT cache for information about packages. The depends option shows a listing of each dependency a package has and all the possible other packages that can fulfill that dependency. For example, apt-cache depends ubuntu-restricted-extras will show the dependencies of the ubuntu-restricted-extras package. The other options are not valid for the apt-cache command. References:
How to Check Dependencies of a Package in Ubuntu/Debian-based Linux Distributions
Check DEB package dependencies on Ubuntu / Debian
What is the difference between the --remove and the --purge action with the dpkg command?
--remove removes the program, --purge also removes the config files
--remove only removes the program, --purge only removes the config files
--remove removes a package, --purge also removes all packages dependent on it
--remove removes only the package file itself, --purge removes all files related to the package
The dpkg command is a tool to install, build, remove and manage Debian packages. The option --remove is used to remove an installed package, but it does not remove the configuration files that may have been modified by the user. The option --purge is used to remove an installed package and also delete its configuration files. This can be useful if the user wants to completely uninstall a package and start from scratch if it is reinstalled later. The syntax is: dpkg --remove package or dpkg --purge package. For example, dpkg --remove nginx will remove the nginx web server package, but it will leave the configuration files in /etc/nginxdpkg --purge nginx will remove the nginx package and also delete the configuration files in /etc/nginx1. The other options are not correct because:
–remove only removes the program, --purge only removes the config files: This is false, because --purge also removes the program, not just the config files.
–remove removes a package, --purge also removes all packages dependent on it: This is false, because --purge does not remove any other packages, only the specified one. To remove a package and its dependencies, the apt-get command can be used with the option --auto-remove2.
–remove removes only the package file itself, --purge removes all files related to the package: This is false, because --remove also removes the files that are installed by the package, not just the package file itself. --purge only removes the configuration files that are not removed by --remove. References:
dpkg(1) — dpkg — Debian buster — Debian Manpages
How to remove a package and its dependencies with dpkg? - Ask Ubuntu
Which of the following options is used in a GRUB Legacy configuration file to define the amount of time that the GRUB menu will be shown to the user?
hidemenu
splash
timeout
showmenu
The timeout option in a GRUB Legacy configuration file is used to define the amount of time (in seconds) that the GRUB menu will be shown to the user before booting the default entry. The timeout option is usually located in the /boot/grub/menu.lst file. For example, timeout 10 will display the GRUB menu for 10 seconds. To disable the timeout and wait for user input indefinitely, the value of timeout can be set to -1. To boot immediately without displaying the menu, the value of timeout can be set to 0. The other options are not valid for the GRUB Legacy configuration file. References:
GRUB Legacy - ArchWiki
How do I set the grub timeout and the grub default boot entry?
How to Remove the Timeout From GRUB Menu
Which of the following apt-get commands will install the newest versions of all currently installed packages without removing any packages or installing new packages that are not already installed?
auto-update
upgrade
dist-upgrade
install
update
The apt-get command upgrade will install the newest versions of all currently installed packages without removing any packages or installing new packages that are not already installed. It will only upgrade packages that can be upgraded without changing the dependencies1. The syntax is: apt-get upgrade. For example, apt-get upgrade nginx will update the nginx package to the latest version available in the repositories, if there is one2. The other options are not correct because:
auto-update is not a valid apt-get command.
dist-upgrade will also install new packages or remove existing packages if that is required to resolve a package conflict1. It is more aggressive than upgrade and may change the system in unexpected ways3.
install will install new packages or upgrade existing packages to the specified version1. It may also install or remove dependencies as needed4.
update will only resynchronize the package index files from the sources, but it will not install or upgrade any packages1. References:
apt-get(8) — apt — Debian buster — Debian Manpages
How to Update Nginx on Ubuntu 18.04 | Linuxize
What is “dist-upgrade” and why does it upgrade more than “upgrade”? - Ask Ubuntu
How to Install Specific Version of Package using apt-get - TecAdmin
What is the name of the main configuration file for GNU GRUB? (Specify the file name only without any path.)
menu.lst
grub.conf
grub.cfg
C
The main configuration file for GNU GRUB is grub.cfg, which is usually located in /boot/grub/ or /boot/grub2/ depending on the distribution. This file contains the menu entries for the boot loader, each with a title, a kernel image, an initrd image, and optional parameters. The grub.cfg file is not meant to be edited manually, as it is generated by the grub-mkconfig command, which reads the settings from /etc/default/grub and the scripts in /etc/grub.d/. The /etc/default/grub file contains the global options for GRUB, such as the default menu entry, the timeout, the theme, etc. The /etc/grub.d/ directory contains executable scripts that are run by grub-mkconfig to generate the menu entries for each operating system or kernel found on the system. For example, the script 10_linux generates the entries for the Linux kernels installed by the package manager, while the script 30_os-prober generates the entries for other operating systems detected on the system, such as Windows. To make changes to the GRUB configuration, one should edit the /etc/default/grub file and/or the scripts in /etc/grub.d/, and then run grub-mkconfig -o /boot/grub/grub.cfg to update the grub.cfg file. References:
2, 102.2 Install a boot manager
4, 102.2 Install a boot manager
man grub-mkconfig
Which function key is used to start Safe Mode in Windows NT?
F10
F8
F6
Windows NT does not support Safe Mode
The function key that is used to start Safe Mode in Windows NT is none of the above, because Windows NT does not support Safe Mode. Safe Mode is a diagnostic mode of Windows that starts the system with minimal drivers and services, allowing the user to troubleshoot problems and restore the system to a normal state1. Safe Mode was introduced in Windows 95 and later versions, but not in Windows NT 4.0 and earlier2.
The other options are incorrect for the following reasons:
F10. This function key is used to access the Recovery Console in Windows XP, which is a command-line interface that allows the user to perform various administrative tasks, such as repairing the boot sector, restoring the registry, or copying files3. The Recovery Console is not the same as Safe Mode, and it is not available in Windows NT.
F8. This function key is used to access the Advanced Boot Options menu in Windows Vista and later versions, which allows the user to choose from various boot modes, including Safe Mode, Last Known Good Configuration, Debugging Mode, and others4. In Windows NT, pressing F8 during startup only displays a simple menu with three options: Normal, VGA mode, and Boot Logging5. None of these options are equivalent to Safe Mode.
F6. This function key is used to load additional drivers during the installation of Windows, such as SCSI or RAID drivers, from a floppy disk or a USB flash drive6. This function key has nothing to do with Safe Mode, and it is not relevant after the installation is completed.
When using rpm --verify to check files created during the installation of RPM packages, which of the following information is taken into consideration? (Choose THREE correct answers.)
Timestamps
MD5 checksums
Inodes
File sizes
GnuPG signatures
When using rpm --verify to check files created during the installation of RPM packages, the following information is taken into consideration:
Timestamps. RPM compares the modification time of the installed files with the original time stored in the RPM database. If the file has been modified after installation, the timestamp will differ and RPM will report it with an M flag1.
MD5 checksums. RPM calculates the MD5 checksum of the installed files and compares it with the original checksum stored in the RPM database. If the file has been altered in any way, the checksum will differ and RPM will report it with an 5 flag1.
File sizes. RPM compares the size of the installed files with the original size stored in the RPM database. If the file has been truncated or appended, the size will differ and RPM will report it with an S flag1.
RPM does not take into consideration the following information:
Inodes. RPM does not check the inode number of the installed files, as it is not a reliable indicator of file identity. The inode number can change if the file is moved, copied, or restored from a backup2.
GnuPG signatures. RPM does not verify the GnuPG signatures of the installed files, as they are not part of the RPM package format. The GnuPG signatures are used to verify the authenticity and integrity of the RPM package files before installation, not after3.
To prevent users from being able to fill up the / partition, the ____________ directory should be on a separate partition if possible because it is world writeable.
/tmp
tmp
The /tmp directory should be on a separate partition if possible because it is world writable. This means that any user can create, modify, or delete files and directories in /tmp. This can pose a risk of filling up the / partition, which can cause system instability or failure. By having /tmp on a separate partition, we can limit the amount of disk space that can be used by temporary files and prevent users from affecting the / partition. The /tmp directory is also a common target for malicious attacks, so having it on a separate partition can improve the security and isolation of the system. The /tmp directory is one of the few directories that are world writable by default, according to the Filesystem Hierarchy Standard (FHS)1. The other directories that are usually world writable are /var/tmp and /var/lock, which are also used for temporary or lock files. However, these directories are not as frequently used or as large as /tmp, so they are less likely to fill up the / partition. The /tmp directory also has the sticky bit set, which means that only the owner of a file or directory can delete or rename it2. This prevents users from deleting or modifying other users’ files in /tmp. However, this does not prevent users from creating new files or directories in /tmp, which can still consume disk space and resources. Therefore, it is advisable to have /tmp on a separate partition if possible. References:
Filesystem Hierarchy Standard
Sticky bit - Wikipedia
Which of the following commands will send output from the program myapp to both standard output (stdout) and the file file1.log?
cat < myapp | cat > file1.log
myapp 0>&1 | cat > file1.log
myapp | cat > file1.log
myapp | tee file1.log
tee myapp file1.log
The tee command reads from standard input and writes to both standard output and one or more files1. Therefore, the command myapp | tee file1.log will send the output of the program myapp to both the terminal and the file file1.log. The other commands will either fail to write to both standard output and file, or write the wrong output. For example, the command cat < myapp | cat > file1.log will try to read the file myapp as input and write it to the file file1.log, but it will not display anything on the terminal. The command myapp 0>&1 | cat > file1.log will redirect the standard input of myapp to its standard output, and then pipe it to the file file1.log, but it will not display anything on the terminal. The command myapp | cat > file1.log will pipe the output of myapp to the file file1.log, but it will not display anything on the terminal. The command tee myapp file1.log will try to read from standard input and write to both the file myapp and the file file1.log, but it will not execute the program myapp. References:
[LPI Linux Essentials - 1.3 Basic Editing]
[LPI Linux Essentials - 1.4 I/O Redirection]
[LPI Linux Essentials - 1.5 Manage Simple Partitions and Filesystems]
From a Bash shell, which of the following commands directly executes the instruction from the file /usr/local/bin/runme.sh without starting a subshell? (Please select TWO answers.)
source /usr/local/bin/runme.sh
. /usr/local/bin/runme.sh
/bin/bash /usr/local/bin/runme.sh
/usr/local/bin/runme.sh
run /usr/local/bin/runme.sh
The commands that directly execute the instruction from the file /usr/local/bin/runme.sh without starting a subshell are source /usr/local/bin/runme.sh and . /usr/local/bin/runme.sh. These commands use the source or dot builtins, which read and execute commands from the given file in the current shell environment. This means that any changes made by the file, such as setting variables, defining functions, or changing directories, will affect the current shell. This is different from running the file as a script, which will create a new shell process and execute the commands in a separate environment. The source or dot commands are useful for loading configuration files, such as ~/.bashrc or /etc/profile, or for running scripts that modify the current state of the shell.
The other commands are incorrect for the following reasons:
C. /bin/bash /usr/local/bin/runme.sh: This command will run the file as a script using the /bin/bash interpreter. This will create a new shell process and execute the commands in a separate environment. Any changes made by the file will not affect the current shell.
D. /usr/local/bin/runme.sh: This command will also run the file as a script, but using the interpreter specified by the shebang line (#!) at the beginning of the file. If the file does not have a shebang line, it will use the default shell interpreter, which may or may not be /bin/bash. This will also create a new shell process and execute the commands in a separate environment. Any changes made by the file will not affect the current shell.
E. run /usr/local/bin/runme.sh: This command is not valid, as there is no builtin or external command called run. This will produce an error message.
Which of the following commands moves and resumes in the background the last stopped shell job?
run
bg
fg
back
The bg command is used to move and resume in the background the last stopped shell job. A stopped job is a process that has been suspended by using Ctrl+Z or the kill -STOP command. The bg command will resume the execution of the stopped job and allow it to run in the background, without blocking the current shell. The bg command can also take a job number as an argument, which can be obtained by using the jobs command. For example, if the last stopped job is 1+ Stopped sleep 500, then the following command will move and resume it in the background:
bg %1
The output will be:
1+ sleep 500 &
The fg command is used to move and resume in the foreground the last stopped or backgrounded job. The run and back commands are not valid commands in Linux. References:
[LPI Exam 101 Detailed Objectives], Topic 103: GNU and Unix Commands, Objective 103.5: Create, monitor and kill processes, Weight: 4, Key Knowledge Areas: Use of jobs, fg and bg commands.
Linux Commands: jobs, bg, and fg, Topic: The bg Command.
: 6
The /etc/_______ file lists currently mounted devices.
mtab
The /etc/mtab file is a system-generated file that lists all the currently mounted devices and their mount options. It is updated automatically by the mount and umount commands. It can be used to check which devices are mounted and where, as well as their filesystem type and mount options. The /etc/mtab file has the same format as the /etc/fstab file, which is a user-edited file that lists the devices that should be mounted at boot time or on demand. References:
LPIC-1 Exam 101 Objectives, Topic 101: System Architecture, 101.1 Determine and configure hardware settings, Key Knowledge Areas, The following is a partial list of the used files, terms and utilities: /etc/mtab
LPIC-1 101-500 Exam Prep, Section 1: System Architecture, Lesson 1.1: Determine and Configure Hardware Settings, Video: 1.1.4 Mounting and Unmounting Filesystems, Transcript: The /etc/mtab file is a system-generated file that lists all the currently mounted devices and their mount options.
Which of the following commands will reduce all consecutive spaces down to a single space?
tr '\s' ' ' < a.txt > b.txt
tr -c ' ' < a.txt > b.txt
tr -d ' ' < a.txt > b.txt
tr -r ' ' '\n' < a.txt > b.txt
tr -s ' ' < a.txt > b.txt
The command that will reduce all consecutive spaces down to a single space is tr -s ’ ’ < a.txt > b.txt. This command uses the following options and syntax:
-s: Squeezes repeated characters listed in the first set with single occurrence.
’ ': Specifies a space character as the first set.
< a.txt: Redirects the input from a file named a.txt.
b.txt: Redirects the output to a file named b.txt.
The output of this command will be a new file called b.txt that contains the same text as a.txt, except that any sequence of multiple spaces will be replaced by a single space. For example, if the file a.txt contains the following text:
This is a text file with multiple spaces.
The file b.txt will contain the following text:
This is a text file with multiple spaces.
The other commands are incorrect for the following reasons:
A. tr ‘\s’ ’ ’ < a.txt > b.txt: This command will replace every whitespace character (\s) with a space character, which will not reduce the number of spaces, but rather convert tabs and newlines into spaces.
B. tr -c ’ ’ < a.txt > b.txt: This command will complement the first set, meaning that it will apply the operation to all characters that are not spaces. This will not affect the spaces at all, but rather squeeze all other characters.
C. tr -d ’ ’ < a.txt > b.txt: This command will delete all spaces from the input, which will not reduce them to a single space, but rather remove them completely.
D. tr -r ’ ’ ‘\n’ < a.txt > b.txt: This command will replace all spaces with newlines, which will not reduce the spaces, but rather create a new line for each word.
What is the output of the following command?
echo "Hello World" | tr -d aieou
Hello World
eoo
Hll Wrld
eoo Hll Wrld
The tr command is used to translate or delete characters from a given input. The -d option specifies that the characters in the second argument should be deleted from the input. In this case, the second argument is aieou, which are the vowels in the English alphabet. Therefore, the tr command will delete any vowel from the input, which is Hello World. The output will be the input without any vowels, which is Hll Wrld. References:
[LPI Exam 101 Detailed Objectives], Topic 103: GNU and Unix Commands, Objective 103.7: Perform basic file management, Weight: 4, Key Knowledge Areas: Use of tr to perform basic text transformations.
[LPI Linux Essentials Certification All-in-One Exam Guide], Chapter 5: Working with Files, Page 165, Using the tr Command.
In compliance with the FHS, in which of the directories are man pages found?
/usr/share/man
/opt/man
/usr/doc/
/var/pkg/man
/var/man
According to the Filesystem Hierarchy Standard (FHS), the directory /usr/share/man contains manual pages for user commands, system calls, library functions, and other documentation1. The other directories are either non-standard, deprecated, or used for different purposes. For example, /opt/man is used for manual pages for add-on application software packages1, /usr/doc/ is an old location for documentation files that is no longer used2, /var/pkg/man and /var/man are not defined by the FHS. References:
[LPI Linux Essentials - 1.6 Basic File Editing]
[LPI Linux Essentials - 1.7 Personalize and/or Localize Your Linux System]
[LPI Linux Essentials - 1.8 Basic Security and File Permissions]
In a nested directory structure, which find command line option would be used to restrict the command to searching down a particular number of subdirectories?
-dirmax
-maxdepth
-maxlevels
-n
-s
The find command is used to search for files and directories that match certain criteria. The option -maxdepth can be used to restrict the command to searching down a particular number of subdirectories. The argument to -maxdepth is a positive integer that specifies the maximum depth of the directory tree to be searched. For example, -maxdepth 0 means only the current directory, -maxdepth 1 means the current directory and its direct subdirectories, and so on1. The option -maxdepth should be placed before any other expressions, as it affects the behavior of the whole command2. For example, to find all the files with the extension .txt in the current directory and its direct subdirectories, the command would be:
find . -maxdepth 1 -type f -name “*.txt”
The other options are not correct because:
A. -dirmax is not a valid find option.
C. -maxlevels is not a valid find option.
D. -depth is a valid find option, but it does not restrict the command to searching down a particular number of subdirectories. It only changes the order of the search, so that the files and directories are processed in depth-first order, meaning that the contents of a directory are processed before the directory itself1. References:
find(1) — Linux manual page
How to use find command to search for multiple extensions - Unix & Linux Stack Exchange
Which command is used in a Linux environment to create a new directory? (Specify ONLY the command without any path or parameters.)
mkdir
/usr/bin/mkdir
A
The mkdir command is used in a Linux environment to create a new directory. The mkdir command takes one or more arguments that specify the name and path of the directory to be created. For example, mkdir foo will create a directory named foo in the current working directory, while mkdir /home/bar will create a directory named bar in the /home directory. The mkdir command can also create multiple directories at once by using the -p option, which creates any missing parent directories along the path. For example, mkdir -p /tmp/a/b/c will create the directories /tmp, /tmp/a, /tmp/a/b and /tmp/a/b/c if they do not exist already. References:
LPIC-1 Exam 101 Objectives, Topic 103: GNU and Unix Commands, 103.3 Perform basic file management
LPIC-1 Linux Administrator 101-500 Exam FAQ, LPIC-1 Exam 101 Objectives, GNU and Unix Commands (Total Weight: 25)
Which of the following commands displays the contents of a gzip compressed tar archive?
gzip archive.tgz | tar xvf -
tar ztf archive.tgz
gzip -d archive.tgz | tar tvf -
tar cf archive.tgz
The command that displays the contents of a gzip compressed tar archive is tar ztf archive.tgz. This command uses the following options:
-z: Tells tar to read or write archives through gzip, allowing it to work on compressed files directly. -t: Lists the contents of an archive without extracting it. -f archive.tgz: Specifies the name of the archive file.
The output of this command will show the names of the files and directories stored in the archive, one per line. For example, if the archive contains three files named file1, file2, and file3, the output will be:
file1 file2 file3
The other commands are incorrect for the following reasons:
gzip archive.tgz | tar xvf -: This command will decompress the archive using gzip and pipe it to tar, which will extract the files to the current directory. The - option tells tar to read the archive from the standard input. This command does not display the contents of the archive, but rather extracts them.
gzip -d archive.tgz | tar tvf -: This command is similar to the previous one, except that it uses the -d option for gzip to decompress the archive instead of compressing it, and the -t option for tar to list the contents instead of extracting them. However, this command is redundant and inefficient, as tar can handle compressed archives directly with the -z option. Also, the -d option for gzip will delete the original archive file after decompression, which may not be desirable.
tar cf archive.tgz: This command will create a new archive named archive.tgz from the files and directories given as arguments. However, this command does not use the -z option, so the archive will not be compressed with gzip. Also, this command does not display the contents of the archive, but rather creates it.
Which of the following explanations are valid reasons to run a command in the background of your shell?
The command does not need to execute immediately.
The command has to run immediately but the user needs to log out.
The system is being shut down and the command needs to restart execution immediately after the reboot.
The command can run at a lower priority than normal commands run on the command line.
Running a command in the background of your shell means that the command will execute asynchronously, without blocking the shell prompt or waiting for user input. This can be useful for commands that take a long time to complete, or that do not require user interaction. One of the valid reasons to run a command in the background is when the command has to run immediately but the user needs to log out. For example, if the user wants to start a backup process that will take several hours, but also wants to close the terminal session and log out from the system, they can run the backup command in the background by appending an ampersand (&) to the command line. This way, the backup command will continue to run even after the user logs out, and the user can check the status or output of the command later. The other options are either incorrect or not applicable. Running a command in the background does not affect the execution priority of the command, which is determined by the nice value and the scheduler. Running a command in the background does not delay the execution of the command, which will start as soon as possible. Running a command in the background does not guarantee that the command will survive a system shutdown or reboot, unless the command is configured to do so with a service manager or a startup script. References:
LPIC-1 Exam 101 Objectives, Topic 103: GNU and Unix Commands, 103.1 Work on the command line
LPIC-1 Linux Administrator 101-500 Exam FAQ, LPIC-1 Exam 101 Objectives, GNU and Unix Commands (Total Weight: 25)
Which of the following statements is correct regarding the command foo 1> bar?
The stdout from the command foo is appended to the file bar.
The stdout from the command foo overwrites the file bar.
The command foo receives its stdin from the file bar.
The command foo receives its stdin from the stdout of the command bar.
The stderr from the command foo is saved to the file bar.
The command foo 1> bar redirects the standard output (stdout) from the command foo to the file bar, overwriting the existing contents of the file. The number 1 before the redirection operator > indicates the file descriptor of the stdout stream, which is 1 by default. The redirection operator > means that the output of the command is written to the file, replacing any previous data in the file. The file name after the redirection operator is the destination of the output. For example, if the command foo prints “Hello world” to the stdout, and the file bar contains “Goodbye world”, the command foo 1> bar will write “Hello world” to the file bar, erasing “Goodbye world”. The other options are not correct because:
A. The stdout from the command foo is appended to the file bar: This is not what 1> does, because it overwrites the file, not appends to it. To append the output to the file, the operator >> should be used instead of >.
C. The command foo receives its stdin from the file bar: This is not what 1> does, because it redirects the output, not the input. To redirect the input from the file, the operator < should be used instead of >.
D. The command foo receives its stdin from the stdout of the command bar: This is not what 1> does, because it redirects the output to a file, not to another command. To redirect the output to another command, the operator | (pipe) should be used instead of >.
E. The stderr from the command foo is saved to the file bar: This is not what 1> does, because it redirects the stdout, not the stderr. To redirect the stderr, the file descriptor 2 should be used instead of 1.
What does the? symbol within regular expressions represent?
Match the preceding qualifier one or more times.
Match the preceding qualifier zero or more times.
Match the preceding qualifier zero or one times.
Match a literal? character.
The ? symbol within regular expressions represents an optional match of the preceding qualifier. A qualifier is a character or a group of characters that can be repeated a certain number of times, such as , +, ?, {n}, {n,}, or {n,m}. The ? symbol means that the qualifier can occur zero or one times, but not more. For example, the regular expression colou?r matches both “color” and “colour”, but not “colouur” or “colr”. The ? symbol can also be used to make other qualifiers lazy, meaning that they will match the smallest possible number of characters, instead of the largest (greedy). For example, the regular expression a.?b matches the shortest string that starts with “a” and ends with “b”, such as “ab” or “a-b”, but not “a-b-c”. References:
[LPI Exam 101 Detailed Objectives], Topic 103: GNU and Unix Commands, Objective 103.7: Perform basic file management, Weight: 4, Key Knowledge Areas: Use of egrep to search for extended regular expressions in text output.
[Regular expression syntax cheat sheet], Topic: Quantifiers.
Which of the following commands prints a list of usernames (first column) and their primary group (fourth column) from the /etc/passwd file?
fmt -f 1,4 /etc/passwd
split -c 1,4 /etc/passwd
cut -d : -f 1,4 /etc/passwd
paste -f 1,4 /etc/passwd
The cut command is used to extract selected fields from each line of a file. The -d option specifies the delimiter that separates the fields, and the -f option specifies the fields to print. The /etc/passwd file contains information about the users on the system, and each field is separated by a colon (:). Therefore, cut -d : -f 1,4 /etc/passwd will print the first and fourth fields of each line, which are the username and the primary group ID respectively. The other commands are either invalid or do not perform the desired task. The fmt command is used to reformat paragraphs of text, but it does not have a -f option. The split command is used to split a file into smaller files, but it does not have a -c option. The paste command is used to merge lines of files, but it does not have a -f option. References:
LPIC-1 Exam 101 Objectives, Topic 103: GNU and Unix Commands, 103.3 Perform basic file management
LPIC-1 Linux Administrator 101-500 Exam FAQ, LPIC-1 Exam 101 Objectives, GNU and Unix Commands (Total Weight: 25)
What happens after issuing the command vi without any additional parameters?
vi starts and loads the last file used andmoves the cursor to the position where vi was when it last exited.
vi starts and requires the user to explicitly either create a new or load an existing file.
vi exits with an error message as it cannot be invoked without a file name to operate on.
vi starts in command mode and opens a new empty file.
vi starts and opens a new file which is filled with the content of the vi buffer if the buffer contains text.
The vi command is a text editor that operates in two modes: command mode and insert mode. Command mode is used to enter commands to manipulate the text, such as saving, quitting, copying, pasting, etc. Insert mode is used to enter text into the file. When the vi command is invoked without any additional parameters, it starts in command mode and opens a new empty file. To enter text, the user has to press i to switch to insert mode. To return to command mode, the user has to press Esc. To save and quit, the user has to enter :wq in command mode. The other options are either incorrect or not applicable. The vi command does not load the last file used or the content of the vi buffer by default. It also does not require the user to explicitly create or load a file. It does not exit with an error message unless there is a problem with the terminal or the system. References:
LPIC-1 Exam 101 Objectives, Topic 103: GNU and Unix Commands, 103.7 Use and edit text files
LPIC-1 Linux Administrator 101-500 Exam FAQ, LPIC-1 Exam 101 Objectives, GNU and Unix Commands (Total Weight: 25)
What does the + symbol mean in the following grep regular expression:
grep '^d[aei]\+d$' /usr/share/dict/words
Match the preceding character set ([aei]) one or more times.
Match the preceding character set ([aei]) zero or more times.
Match the preceding character set ([aei]) zero or one times.
Match a literal + symbol.
The + symbol in a grep regular expression means to match the preceding character or character set one or more times. In other words, it means to repeat the previous element at least once. For example, the regular expression ^d[aei]\+d$ will match any word that starts and ends with d and has one or more of the letters a, e or i in between. Some examples of words that match this pattern are dead, deed, died, daiid, etc. The other options are either incorrect or not applicable. The * symbol means to match the preceding character or character set zero or more times. The ? symbol means to match the preceding character or character set zero or one times. The \+ symbol means to match a literal + symbol, not a repetition modifier. References:
LPIC-1 Exam 101 Objectives, Topic 103: GNU and Unix Commands, 103.3 Perform basic file management
LPIC-1 Linux Administrator 101-500 Exam FAQ, LPIC-1 Exam 101 Objectives, GNU and Unix Commands (Total Weight: 25)
Which character, added to the end of a command, runs that command in the background as a child process of the current shell?
!
+
&
%
#
The character that, added to the end of a command, runs that command in the background as a child process of the current shell is the ampersand symbol (&). This means that the command will not block the shell and the user can enter other commands while the background command is running. The background command will also not receive any input from the keyboard or the terminal. The shell will print the job number and the process ID of the background command, and the user can use the jobs command to list the status of all background jobs in the current shell session. To bring a background job to the foreground, the user can use the fg command with the job number or the process ID. To terminate a background job, the user can use the kill command with the process ID.
The other characters are not valid or relevant for running a command in the background. The exclamation mark (!) is used to access the command history or to negate a condition. The plus sign (+) is used for arithmetic operations or to append text. The percent sign (%) is used for arithmetic operations or to refer to a job number. The hash sign (#) is used for comments or to specify a hexadecimal number.
In the vi editor, how can commands such as moving the cursor or copying lines into the buffer be issued multiple times or applied to multiple rows?
By using the command: repeat followed by the number and the command.
By specifying the number right in front of a command such as 4l or 2yj.
By selecting all affected lines using the shift and cursor keys before applying the command.
By issuing a command such as: set repetition=4 which repeats every subsequent command 4 times.
In the vi editor, one of the ways to issue commands multiple times or apply them to multiple rows is to specify the number right in front of a command. This will repeat the command as many times as the number indicates. For example, the command 4l will move the cursor four characters to the right, and the command 2yj will copy two lines from the current line to the buffer. This method can be used for most of the vi commands that operate on single characters, words, lines, or blocks of text. Another way to issue commands multiple times or apply them to multiple rows is to use the . (dot) command, which repeats the last command. For example, after deleting a line with dd, pressing . will delete another line. However, this method is less precise and efficient than specifying the number before the command. References:
Basic vi commands (cheat sheet), Topic: Moving within a File (Navigation).
Vi Editor with Commands in Linux/Unix Tutorial, Topic: VI Editing commands.
Given the following routing table:
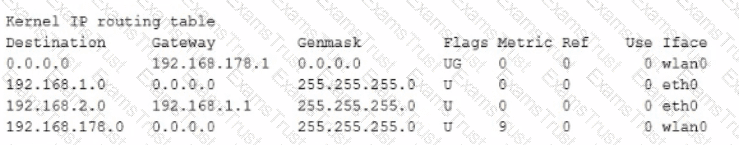
How would an outgoing packet to the destination 192 168 2 150 be handled?
It would be passed to the default router 192 168 178 1 onwIan0.
It would be directly transmitted on the device eth0
It would be passed to the default router 255 255 255 0 on eth0
It would be passed to the router 192 168.1.1 oneth0
It would be directly transmitted on the device wlan0.
If neither cron. allow nor cron. deny exist in /etc/, which of the following is true?
Without additional configuration, all users may create user specific crontabs
Without additional configuration, only root may create user specific crontabs
The cron daemon will refuse to start and report missing files in the system's logfile
When a user creates a user specific crontab the system administrator must approve it explicitly
The default settings of /etc/crond.conf define whether or not user specific crontabs are generally allowed or not.
Which character in the password field of /etc/passwd is used to indicate that the encrypted password is stored in /etc/shadow?
*
-
$
#
x
What is true regarding UEFI firmware? (Choose two.)
It can read and interpret partition tables
It can use and read certain file systems
It stores its entire configuration on the /boot/ partition
It is stored in a special area within the GPT metadata
It is loaded from a fixed boot disk position
UEFI firmware is a software program that provides the interface between the hardware and the operating system on a computer. UEFI stands for Unified Extensible Firmware Interface and it is a replacement for the traditional BIOS (Basic Input/Output System). UEFI firmware has several advantages over BIOS, such as faster boot times, better security, larger disk support, and graphical user interface. Some of the features of UEFI firmware are12:
It can use and read certain file systems: UEFI firmware can access files on partitions formatted with FAT12, FAT16, or FAT32 file systems. This allows UEFI to load boot loaders, kernels, and configuration files from these partitions without relying on the legacy MBR (Master Boot Record) or boot sector code. UEFI firmware can also support other file systems, such as NTFS or ext4, with additional drivers.
It is loaded from a fixed boot disk position: UEFI firmware is stored in a ROM chip on the motherboard, but it also requires a special partition on the boot disk to store additional files and drivers. This partition is called the EFI System Partition (ESP) and it is usually the first partition on the disk. The ESP must have a specific GUID (Globally Unique Identifier) and must be formatted with a FAT file system. The UEFI firmware will look for the ESP on the boot disk and load the files from there.
The other options are false or irrelevant. UEFI firmware does not read and interpret partition tables, it relies on the operating system to do that. UEFI firmware does not store its entire configuration on the /boot/ partition, it stores some of its settings in the NVRAM (Non-Volatile Random Access Memory) on the motherboard and some of its files on the ESP. UEFI firmware is not stored in a special area within the GPT (GUID Partition Table) metadata, it is stored in a ROM chip and an ESP. GPT is a partitioning scheme that supports larger disks and more partitions than the legacy MBR scheme. References:
Linux Essentials - Linux Professional Institute Certification Programs1
Exam 101 Objectives - Linux Professional Institute2
How to Boot and Install Linux on a UEFI PC With Secure Boot3
How to Access UEFI Settings From Linux - It’s FOSS4
UEFI firmware updates for linux-surface - GitHub5
What is true about NetworkManager on a Linux system that uses its distnbution's mechanisms to configure network interfaces? (Choose TWO correct answers )
NetworkManager reconfigures all network interfaces to use DHCP unless they are specifically managed by NetworkManager
NetworkManager must be explicitly enabled for each interface it should manage
NetworkManager by default does not change interfaces which are already configured
NetworkManager disables all interfaces which were not configured by NetworkManager
NetworkManager can be configured to use the distribution's network interface configuration
Consider the following directory:
drwxrwxr-x 2 root sales 4096 Jan 1 15:21 sales
Which command ensures new files created within the directory sales are owned by the group sales? (Choose two.)
chmod g+s sales
setpol –R newgroup=sales sales
chgrp –p sales sales
chown --persistent *.sales sales
chmod 2775 sales
The command chmod g+s sales sets the setgid bit on the directory sales, which means that any new file or subdirectory created within sales will inherit the group ownership of the directory. The command chmod 2775 sales does the same thing, but also sets the permissions of the directory to rwxrwxr-x, which means that the owner, group, and others can read, write, and execute files in the directory. Both commands ensure that new files created within the directory sales are owned by the group sales. The other commands are either invalid or do not affect the group ownership of new files. References:
Linux Essentials - Linux Professional Institute Certification Programs1
Exam 101 Objectives - Linux Professional Institute
Which of the following files, located in a user’s home directory, contains the Bash history?
.bashrc_history
.bash_histfile
.history
.bash_history
.history_bash
The correct answer is D, .bash_history. This file, located in a user’s home directory, contains the Bash history, which is a list of commands that the user has entered in the Bash shell. The syntax of the file is:
~/.bash_history
The ~ symbol represents the user’s home directory, which is usually /home/username. The / symbol is a directory separator that separates the components of a path. The . symbol at the beginning of the file name indicates that the file is hidden, which means that it is not normally displayed by the ls command or the file manager, unless the -a option or the show hidden files option is used. The bash_history is the name of the file that stores the Bash history.
The Bash history is maintained by the Bash shell while it is running, and it is written to the .bash_history file when the shell exits or when the history -a or -w options are used. The history command can be used to display, manipulate, or search the Bash history. The HISTFILE variable can be used to change the name or location of the .bash_history file. The HISTSIZE and HISTFILESIZE variables can be used to change the number of commands that are stored in the Bash history and the .bash_history file, respectively.
The other files are incorrect for the following reasons:
A, .bashrc_history: This file does not exist by default, and it is not used to store the Bash history. The .bashrc file is a configuration file that is executed by the Bash shell when it starts in interactive mode. It can contain commands, aliases, functions, variables, or other settings that affect the behavior of the shell. However, it is not used to store the history of the commands that the user has entered.
B, .bash_histfile: This file does not exist by default, and it is not used to store the Bash history. The .bash_histfile file is not a standard file name, and it is not recognized by the Bash shell. The Bash shell uses the .bash_history file to store the history of the commands that the user has entered, unless the HISTFILE variable is changed to a different file name.
C, .history: This file does not exist by default, and it is not used to store the Bash history. The .history file is not a standard file name, and it is not recognized by the Bash shell. The Bash shell uses the .bash_history file to store the history of the commands that the user has entered, unless the HISTFILE variable is changed to a different file name.
E, .history_bash: This file does not exist by default, and it is not used to store the Bash history. The .history_bash file is not a standard file name, and it is not recognized by the Bash shell. The Bash shell uses the .bash_history file to store the history of the commands that the user has entered, unless the HISTFILE variable is changed to a different file name.
What does the term Braille Display refer to?
A standardized high contract graphical theme for desktop applications
A Linux desktop environment similar to KDE and GNOME
A legacy display technology superseded by LCD
A physical representation of characters using small dots
A standard file format for data exchange, similar to XML
When redirecting the output of find to the xargs command, what option to find is useful if the filenames contain spaces?
–rep-space
-printnul
-nospace
–ignore-space
–print0
This option to the find command is useful if the filenames contain spaces when redirecting the output of find to the xargs command. The syntax of the option is:
find [where to start searching from] [expression determines what to find] -print0
The -print0 option tells the find command to print the full file name on the standard output, followed by a null character (ASCII code 0) instead of the newline character. This allows file names that contain spaces or other special characters to be correctly interpreted by the xargs command, which can use the -0 option to read items from the standard input that are terminated by a null character. The syntax of the xargs command with the -0 option is:
xargs -0 [command]
The -0 option tells the xargs command to expect the items from the standard input to be separated by a null character, and to execute the command using the items as arguments.
Therefore, the command find … -print0 | xargs -0 … will search for files and directories using the find command, print the results with a null character as the separator, pipe the output to the xargs command, which will read the items with a null character as the separator, and execute another command using the items as arguments. This will avoid any problems with filenames that contain spaces or other special characters.
The other options are incorrect for the following reasons:
A, -rep-space: This option does not exist in the find command. There is no option to replace spaces in the filenames with another character in the find command. The command will report an error and exit.
B, -printnul: This option does not exist in the find command. There is a similar option, -print0, which prints the filenames with a null character as the separator, but -printnul is not a valid option. The command will report an error and exit.
C, -nospace: This option does not exist in the find command. There is no option to ignore spaces in the filenames in the find command. The command will report an error and exit.
D, -ignore-space: This option does not exist in the find command. There is no option to ignore spaces in the filenames in the find command. The command will report an error and exit.
Which of the following commands changes all CR-LF line breaks in the text file userlist.txt to Linux standard LF line breaks and stores the result in newlist.txt?
tr –d ‘\r’ < userlist.txt > newlist.txt
tr –c ‘\n\r’ ‘’
tr ‘\r\n’ ‘’
tr ‘\r’ ‘\n’ userlist.txt newlist.txt
tr –s ‘/^M/^J/’ userlist.txt newlist.txt
The correct answer is A, tr -d ‘\r’ < userlist.txt > newlist.txt. This command will use the tr utility to delete the carriage return characters (\r) from the userlist.txt file and redirect the output to the newlist.txt file. The tr utility is used to translate, delete, or squeeze characters from the standard input and write the result to the standard output. The syntax of the tr command is:
tr [options] set1 [set2]
The options can modify the behavior of the tr command, such as complementing, squeezing, or truncating the sets of characters. The set1 and set2 are strings of characters that specify the translation to be performed. The characters in set1 are replaced by the corresponding characters in set2. If set2 is omitted, the characters in set1 are deleted.
The -d option tells tr to delete the characters in set1 from the output. The \r character is a special escape sequence that represents the carriage return character, which is used in Windows systems to mark the end of a line, along with the line feed character (\n). The < and > symbols are redirection operators that redirect the input and output of a command to a file or device. The < symbol redirects the standard input of a command from a file, while the > symbol redirects the standard output of a command to a file, overwriting any existing content.
Therefore, the command tr -d ‘\r’ < userlist.txt > newlist.txt will read each character from the userlist.txt file, delete any carriage return characters, and write the output to the newlist.txt file. This will effectively change all CR-LF line breaks (\r\n) in the userlist.txt file to Linux standard LF line breaks (\n) and store the result in newlist.txt.
The other commands are incorrect for the following reasons:
B, tr -c ‘\n\r’ ‘’
C, tr ‘\r\n’ ‘’
D, tr ‘\r’ ‘\n’ userlist.txt newlist.txt: This command will not work as expected, because it has several errors. First, the set1 and set2 in this command are ‘\r’ and ‘\n’, which means that tr will replace the carriage return characters with the line feed characters, not delete them. Second, the redirection operators are missing, which means that tr will not read the input from the userlist.txt file or write the output to the newlist.txt file, but instead it will expect the input from the standard input and write the output to the standard output. Third, the userlist.txt and newlist.txt are treated as additional arguments that will cause an error. Therefore, the command tr ‘\r’ ‘\n’ userlist.txt newlist.txt will replace all the carriage return characters with the line feed characters from the standard input and write the output to the standard output, and report an error for the extra arguments.
E, tr -s ‘/M/J/’ userlist.txt newlist.txt: This command will not work as expected, because it has several errors. First, the -s option tells tr to squeeze the repeated characters in set1 with a single occurrence, not delete them. Second, the set1 in this command is ‘/M/J/’, which is not a valid escape sequence for the carriage return and the line feed characters. The correct escape sequences are ‘\r’ and ‘\n’, respectively. Third, the redirection operators are missing, which means that tr will not read the input from the userlist.txt file or write the output to the newlist.txt file, but instead it will expect the input from the standard input and write the output to the standard output. Fourth, the userlist.txt and newlist.txt are treated as additional arguments that will cause an error. Therefore, the command tr -s ‘/M/J/’ userlist.txt newlist.txt will squeeze the repeated occurrences of the characters /, ^, M, and J from the standard input and write the output to the standard output, and report an error for the extra arguments.
Which of the following commands list all files and directories within the /tmp/ directory and its subdirectories which are owned by the user root? (Choose two.)
find /tmp –user root -print
find –path /tmp –uid root
find /tmp –uid root -print
find /tmp –user root
find –path /tmp –user root -print
The find command can be used to search for files and directories that match certain criteria, such as ownership, permissions, size, type, name, etc. The syntax of the find command is:
find [options] [path...] [expression]
The options can modify the behavior of the find command, such as how to handle symbolic links, how to optimize the search, or how to enable debugging. The path argument specifies the starting point of the search, which can be one or more directories. The expression argument consists of one or more tests, actions, and operators that are applied to each file or directory that is found.
The -user test matches files or directories that are owned by a given user. The user can be specified by name or by numeric user ID (UID). The -print action prints the full file name of the matching file or directory on the standard output, followed by a newline. If no action is specified, -print is assumed by default.
Therefore, to list all files and directories within the /tmp/ directory and its subdirectories which are owned by the user root, we can use either of the following commands:
find /tmp -user root -print
find /tmp -user root
Both commands will search recursively from the /tmp/ directory and print the full file names of the files or directories that are owned by the user root. The -print action is optional in this case, since it is the default action.
The other commands are incorrect for the following reasons:
find -path /tmp -uid root : The -path test matches files or directories whose full file name matches the given pattern. This command will not search recursively from the /tmp/ directory, but only match files or directories whose name is exactly /tmp. The -uid test is equivalent to the -user test, but it requires a numeric UID instead of a user name. This command will not match any files or directories, unless there is a file or directory named /tmp that is owned by the user with UID root (which is usually 0).
find -path /tmp -user root -print : This command has the same problem as the previous one. It will not search recursively from the /tmp/ directory, but only match files or directories whose name is exactly /tmp and are owned by the user root. This command will not match any files or directories, unless there is a file or directory named /tmp that is owned by the user root.
find /tmp -uid root -print : This command will search recursively from the /tmp/ directory, but it will use the -uid test instead of the -user test. The -uid test requires a numeric UID instead of a user name. This command will match files or directories that are owned by the user with UID root (which is usually 0), but it will not match files or directories that are owned by other users who have the same user name as root (such as root2 or root3).
Which ol the following fields can be found in the /etc/group file? (Choose TWO correct answers.)
The home directory of the group
The list of users that belong to the group
The name of the group
The default group ACL
The description of the group
If an alias Is exists, which of the following commands updates the ai as to point to dig contmfl nd is -1 instead of the alias's current target?
set ls-'ls -1"
alias ls=,ls -1'
alias --force ls='ls -1*
alias --update Is ls='ls -1'
realias Is-'Is -1'
Which of the following commands displays the output of the foo command on the screen and also writes it to a file called /tmp/foodata?
foo | less /tmp/foodata
foo | cp /tmp/foodata
foo > /tmp/foodata
foo | tee /tmp/foodata
foo > stdout >> /tmp/foodata
This command will display the output of the foo command on the screen and also write it to a file called /tmp/foodata. The syntax of the command is:
foo | tee [options] [file]
The foo command is any command that produces some output. The | symbol is a pipe operator that redirects the standard output of one command to the standard input of another command. The tee command reads from the standard input and writes to both the standard output and one or more files. The options can modify the behavior of the tee command, such as appending to the file instead of overwriting it, or ignoring interrupt signals. The file is the name of the file to which the output is written. If no file is given, the tee command will only write to the standard output.
Therefore, the command foo | tee /tmp/foodata will run the foo command, pipe its output to the tee command, which will display the output on the screen and write it to the file /tmp/foodata.
The other commands are incorrect for the following reasons:
A, foo | less /tmp/foodata: This command will not write the output of the foo command to a file, but it will display the output of the foo command on the screen in a pager. The less command is a program that allows the user to view and scroll through a file or the output of a command. The syntax of the command is:
foo | less [options] [file]
The foo command is any command that produces some output. The | symbol is a pipe operator that redirects the standard output of one command to the standard input of another command. The less command reads from the standard input or a file and displays it on the screen in a pager. The options can modify the behavior of the less command, such as setting the number of lines per screen, or searching for a pattern. The file is the name of the file to be viewed. If no file is given, the less command will read from the standard input.
Therefore, the command foo | less /tmp/foodata will run the foo command, pipe its output to the less command, which will display the output on the screen in a pager. However, the /tmp/foodata argument will be ignored by the less command, because it will read from the standard input instead of the file. The command will not write anything to the file /tmp/foodata.
B, foo | cp /tmp/foodata: This command will not work as expected, because it has several errors. First, the cp command is not a valid command to write the output of a command to a file. The cp command is used to copy files or directories from one location to another. The syntax of the command is:
cp [options] source destination
The options can modify the behavior of the cp command, such as preserving the attributes of the files, or creating backups of the existing files. The source is the name of the file or directory to be copied. The destination is the name of the file or directory where the source is copied to.
Second, the pipe operator is not a valid way to redirect the output of a command to the cp command. The pipe operator redirects the standard output of one command to the standard input of another command. However, the cp command does not read from the standard input, but from the source argument. Therefore, the command foo | cp /tmp/foodata will run the foo command, pipe its output to the cp command, which will ignore the standard input and report an error for missing the destination argument. The command will not write anything to the file /tmp/foodata.
C, foo > /tmp/foodata: This command will not display the output of the foo command on the screen, but it will write it to a file called /tmp/foodata. The > symbol is a redirection operator that redirects the standard output of a command to a file or device, overwriting any existing content. The syntax of the command is:
foo > file
The foo command is any command that produces some output. The > symbol redirects the standard output of the foo command to the file. The file is the name of the file to which the output is written.
Therefore, the command foo > /tmp/foodata will run the foo command, redirect its output to the file /tmp/foodata, and overwrite any previous content. The command will not display anything on the screen.
E, foo > stdout >> /tmp/foodata: This command will not work as expected, because it has several errors. First, the stdout argument is not a valid file name or device name. The stdout is an abbreviation for the standard output, which is a stream that a program uses to write its output. However, the stdout is not a file or device that can be used as a destination for the redirection operator. Second, the >> symbol is a redirection operator that redirects the standard output of a command to a file or device, appending to any existing content. The syntax of the command is:
foo >> file
The foo command is any command that produces some output. The >> symbol redirects the standard output of the foo command to the file. The file is the name of the file to which the output is appended.
Therefore, the command foo > stdout >> /tmp/foodata will run the foo command, redirect its output to the stdout argument, which will cause an error, and then redirect its output again to the file /tmp/foodata, which will append the output to the file. The command will not display anything on the screen.
Which umask value ensures that new directories can be read, written and listed by their owning user, read and listed by their owning group and are not accessible at all for everyone else?
0750
0027
0036
7640
0029
The umask value is a four-digit octal number that determines the default permissions for new files and directories created by a user. The umask value specifies the permissions that are not granted to the user, group, and others. The permissions are represented by three bits for each category, where 1 means execute, 2 means write, and 4 means read. The sum of these values indicates the combination of permissions. For example, 7 means read, write, and execute; 6 means read and write; 5 means read and execute; 4 means read only; 3 means write and execute; 2 means write only; 1 means execute only; and 0 means no permission.
The umask value is subtracted from the maximum permissions for files and directories, which are 666 and 777, respectively. The maximum permissions are then converted to binary and bitwise ANDed with the bitwise complement of the umask value. The result is the default permissions for the new files and directories. For example, if the umask value is 0027, the default permissions for a new file are:
666 - 027 = 639 639 in octal = 110 011 001 in binary 027 in octal = 000 010 111 in binary Bitwise complement of 027 = 111 101 000 in binary 110 011 001 AND 111 101 000 = 110 001 000 in binary 110 001 000 in binary = 608 in octal 608 in octal = rw- — —
The default permissions for a new directory are:
777 - 027 = 750 750 in octal = 111 101 000 in binary 027 in octal = 000 010 111 in binary Bitwise complement of 027 = 111 101 000 in binary 111 101 000 AND 111 101 000 = 111 101 000 in binary 111 101 000 in binary = 750 in octal 750 in octal = rwx r-x —
Therefore, the umask value of 0027 ensures that new files can be read and written by their owning user, and are not accessible at all for everyone else. New directories can be read, written and listed by their owning user, read and listed by their owning group, and are not accessible at all for everyone else.
Which of the following vi commands deletes two lines, the current and the following line?
d2
2d
2dd
dd2
de12
The correct answer is C, 2dd. This command will delete two lines, the current and the following line, in vi editor. The syntax of the command is:
[number]dd
The number specifies how many lines to delete, starting from the current line. The dd command deletes the lines and puts them in a buffer, which can be pasted later with the p command. If no number is given, the command will delete only the current line.
The other commands are incorrect for the following reasons:
A, d2: This command will delete two characters, not two lines. The syntax of the command is:
d[motion]
The motion specifies how many characters to delete, starting from the current cursor position. The 2 motion means two characters to the right. The d command deletes the characters and puts them in a buffer, which can be pasted later with the p command.
B, 2d: This command is incomplete and will not work. The d command requires a motion argument to specify how many characters to delete. The 2 argument is only a number, not a motion. The command will wait for another keystroke to complete the motion.
D, dd2: This command will delete the current line and then move the cursor two lines down. The syntax of the command is:
dd[number]
The dd command deletes the current line and puts it in a buffer, which can be pasted later with the p command. The number specifies how many lines to move the cursor down, after deleting the current line. If no number is given, the command will move the cursor to the next line.
E, de12: This command will delete from the current cursor position to the end of the word, and then move the cursor to the 12th line. The syntax of the command is:
d[motion][number]
The d command deletes the characters specified by the motion and puts them in a buffer, which can be pasted later with the p command. The e motion means the end of the word. The number specifies the line number to move the cursor to, after deleting the characters.
What is true about the file .profile in a user's home directory?
It must be executable
It must call the binary of the login shell
It must use a valid shell script syntax
It must start with a shebang
It must be readable for its owner only
What information related to a user account is modified using the chage command?
Default ownership for new files
Group membership
Set of commands available to the user
Password expiry information
Default permissions for new files
What of the following statements are true regarding /dev/ when using udev? (Choose TWO correct answers.)
Entries for all possible devices get created on boot even if those devices are not connected.
Additional rules for udev can be created by adding them to /etc/udev/rules.d/.
When using udev, it is not possible to create block orcharacter devices in /dev/ using mknod.
The /dev/ directory is a filesystem of type tmpfs and is mounted by udev during system startup.
The content of /dev/ is stored in /etc/udev/dev and is restored during system startup.
udev is a device manager that dynamically creates and removes device nodes in the /dev/ directory. It also handles device events, such as adding, removing, or changing the attributes of devices. udev uses rules to match devices and assign properties, permissions, names, symlinks, and other actions. The rules are stored in files under /lib/udev/rules.d/ and /etc/udev/rules.d/. The latter directory can be used to create additional or override existing rules. The /dev/ directory is not a regular directory on the root filesystem, but a virtual filesystem of type tmpfs that is mounted by udev during system startup. tmpfs is a filesystem that resides in memory and can grow and shrink dynamically. The content of /dev/ is not stored in /etc/udev/dev, but is created by udev based on the rules and the available devices. udev does not prevent the creation of block or character devices in /dev/ using mknod, but it may overwrite or remove them if they conflict with the rules or the device events. References: LPI Linux Essentials - 1.101.2, LPI Linux Administrator - 102.4
Which file in the /proc filesystem lists parameters passed from the bootloader to the kernel? (Specify the file name only without any path.)
cmdline
The file in the /proc filesystem that lists the parameters passed from the bootloader to the kernel is /proc/cmdline. This file contains a single line of text that shows the command line arguments that were used to boot the kernel. These arguments can include various options, such as the root device, the init process, the console device, and more. The /proc/cmdline file is read-only and cannot be modified at runtime. The parameters in this file are determined by the bootloader configuration, such as GRUB or LILO, and can be changed by editing the corresponding files12.
You are having some trouble with a disk partition and you need to do maintenance on this partition but your users home directories are on it and several are logged in. Which command would disconnect the users and allow you to safely execute maintenance tasks?
telinit 1
shutdown -r now
killall -9 inetd
/bin/netstop --maint
/etc/rc.d/init.d/network stop
The command that would disconnect the users and allow you to safely execute maintenance tasks on a disk partition is telinit 112. The telinit command is used to change the runlevel of the system, which is a mode of operation that defines what processes and services are running3. The runlevel 1, also known as single-user mode, is a mode that allows only the root user to log in, and disables all network services and graphical interfaces4. This mode is useful for performing system maintenance and recovery tasks, such as repairing a disk partition5.
The other options in the question are not correct because:
B. shutdown -r now: This command would reboot the system immediately, without disconnecting the users gracefully or allowing you to do any maintenance tasks.
C. killall -9 inetd: This command would kill the inetd process, which is a daemon that manages network services. This would not disconnect the users who are already logged in, and it would not stop other processes that might interfere with the maintenance tasks.
D. /bin/netstop --maint: There is no such command in Linux.
E. /etc/rc.d/init.d/network stop: This command would stop the network service, which would disconnect the users who are logged in remotely, but not the ones who are logged in locally. It would also not stop other processes that might interfere with the maintenance tasks.
Which of the following options for the kernel's command line changes the systemd boot target to rescue.target instead of the default target?
systemd.target=rescue.target
systemd.runlevel=rescue.target
systemd.service=rescue.target
systemd.default=rescue.target
systemd.unit=rescue.target
Which command will display messages from the kernel that were output during the normal boot sequence?
dmesg
The command dmesg will display messages from the kernel that were output during the normal boot sequence. The dmesg command reads the kernel ring buffer, which is a data structure that stores the most recent messages generated by the kernel. The dmesg command can also be used to display messages from the kernel that were output after the boot sequence, such as hardware events, driver messages, or system errors. The dmesg command has various options to filter, format, or save the output. For example, dmesg -T will display human-readable timestamps for each message, and dmesg -w will display the messages in real time as they occur. References:
1: How to view all boot messages in Linux after booting? - Super User
2: dmesg(1) - Linux manual page
3: Kernel ring buffer - Wikipedia
Which command displays the contents of the Kernel Ring Buffer on the command line? (Provide only the command name without any options or path information)
dmesg,
The command that displays the contents of the Kernel Ring Buffer on the command line is dmesg12. The dmesg command is a Linux utility that displays kernel-related messages retrieved from the kernel ring buffer12. The ring buffer stores information about hardware, device driver initialization, and messages from kernel modules that take place during system startup12. The dmesg command is invaluable when troubleshooting hardware-related errors, warnings, and for diagnosing device failure2.
The dmesg command can be used with various options to control the output format, filter the messages by facility or level, clear the ring buffer, or follow the new messages in real time123. For example, the following command displays the last 10 messages from the kernel ring buffer:
$ dmesg | tail -10
The following command displays the messages from the kernel ring buffer in a human-readable format with colored output:
$ dmesg -H --color
The following command displays the messages from the kernel ring buffer that have the facility kern and the level emerg:
$ dmesg -f kern -l emerg
The following command clears the ring buffer:
$ dmesg --clear
The following command keeps dmesg running and waiting for new messages:
$ dmesg -w
Which of the following kernel parameters instructs the kernel to suppress most boot messages?
silent
verbose=0
nomesg
quiet
The quiet kernel parameter instructs the kernel to suppress most boot messages, except for critical errors12. The quiet parameter can be added to the GRUB_CMDLINE_LINUX_DEFAULT variable in the /etc/default/grub file and then run sudo update-grub to apply the changes3. The quiet parameter can also be used in combination with other parameters, such as splash, to enable a graphical boot screen4.
The other options in the question are not valid or do not have the same functionality as the quiet parameter:
silent: There is no such kernel parameter in Linux.
verbose=0: This parameter is used to set the verbosity level of the kernel messages, but it does not suppress them completely. The valid values for this parameter are from 0 (quiet) to 7 (debug)5.
nomesg: This parameter is used to disable all kernel messages on the console, including the emergency ones. This parameter is not recommended for normal use, as it can hide critical errors and prevent troubleshooting.
What information can the lspci command display about the system hardware? (Choose THREE correct answers.)
Device IRQ settings
PCI bus speed
System battery type
Device vendor identification
Ethernet MAC address
The lspci command can display information about the system hardware, such as:
Device IRQ settings1: The lspci command can show the interrupt request (IRQ) number assigned to each device by using the -v option. The IRQ number indicates how the device communicates with the CPU.
PCI bus speed2: The lspci command can show the speed of the PCI bus by using the -vv option. The speed is expressed in megahertz (MHz) or gigahertz (GHz) and indicates how fast the data can be transferred between the device and the bus.
Device vendor identification3: The lspci command can show the name and identification number of the device vendor by using the -n or -nn option. The vendor identification helps to identify the manufacturer and model of the device.
Which of the following commands brings a system running SysV init into a state in which it is safe to perform maintenance tasks? (Choose TWO correct answers.)
shutdown -R 1 now
shutdown -single now
init 1
telinit 1
runlevel 1
The commands init 1 and telinit 1 both bring a system running SysV init into a state in which it is safe to perform maintenance tasks. This state is also known as single-user mode or runlevel 1, where only the root user can log in and no network services are running. The command shutdown -R 1 now is incorrect, because it reboots the system instead of entering single-user mode. The command shutdown -single now is invalid, because the -single option does not exist for the shutdown command. The command runlevel 1 is also invalid, because runlevel is a command that displays the current and previous runlevels, not a command that changes the runlevel. References:
1: SysVinit - ArchWiki
2: Linux: How to write a System V init script to start, stop, and restart my own application or service - nixCraft
3: sysvinit - Gentoo wiki
The USB device filesystem can be found under /proc/______/usb/. (Please fill in the blank with the single word only)
bus
The USB device filesystem can be found under /proc/bus/usb/1. This is a virtual filesystem that provides information about the USB devices and buses connected to the system12. It contains files and directories that correspond to the USB host controllers, hubs, and devices12. For example, the following output shows the contents of /proc/bus/usb/ on a system with one USB host controller and two USB devices:
The directories 001 and 002 represent the USB buses, and each contain files that represent the USB devices on that bus. The file devices contains a summary of all the USB devices and their configurations. The file drivers contains a list of the USB drivers and the devices they are bound to12.
The /proc/bus/usb/ filesystem is deprecated and should not be used anymore3. It has been replaced by the /sys/bus/usb/ filesystem, which is a sysfs mount that provides more detailed and structured information about the USB devices and buses3 .
What is the first program that is usually started, at boot time, by the Linux kernel when using SysV init?
/lib/init.so
/sbin/init
/etc/rc.d/rcinit
/proc/sys/kernel/init
/boot/init
The first program that is usually started, at boot time, by the Linux kernel when using SysV init is /sbin/init. This program is responsible for reading the /etc/inittab file and executing the appropriate scripts and programs for each runlevel. The other options are not valid programs that are started by the kernel. /lib/init.so is a shared library that is used by some init programs, but not by SysV init. /etc/rc.d/rcinit is a script that is run by init, not by the kernel. /proc/sys/kernel/init is a kernel parameter that can be used to specify a different init program, but the default value is /sbin/init. /boot/init is not a standard location for an init program, and it is unlikely that the kernel would find it there. References:
1: SysVinit - ArchWiki
2: Linux: How to write a System V init script to start, stop, and restart my own application or service - nixCraft
3: sysvinit - Gentoo wiki
The message "Hard Disk Error" is displayed on the screen during Stage 1 of the GRUB boot process. What does this indicate?
The kernel was unable to execute /bin/init
The next Stage cannot be read from the hard disk because GRUB was unable to determine the size and geometry of the disk
One or more of the filesystems on the hard disk has errors and a filesystem check should be run
The BIOS was unable to read the necessary data from the Master Boot Record to begin the boot process
The GRUB boot process consists of three stages1:
Stage 1: This stage is located in the Master Boot Record (MBR) of the first hard disk or the boot sector of a partition. Its main function is to load either Stage 1.5 or Stage 22.
Stage 1.5: This stage is located in the first 30 KB of hard disk immediately following the MBR or in the boot sector of a partition. It contains the code to access the file system that contains the GRUB configuration file. Its main function is to load Stage 22.
Stage 2: This stage is located in an ordinary file system, usually in the /boot/grub directory. It contains the code to display the GRUB menu and to load the kernel and initrd images. It can also load additional modules to support other file systems or features2.
The message “Hard Disk Error” is displayed on the screen during Stage 1 of the GRUB boot process. This indicates that the next Stage (either Stage 1.5 or Stage 2) cannot be read from the hard disk because GRUB was unable to determine the size and geometry of the disk3. This could occur because the BIOS translated geometry has been changed by the user or the disk is moved to another machine or controller after installation, or GRUB was not installed using itself (if it was, the Stage 2 version of this error would have been seen during that process and it would not have completed the install)3.
The other options in the question are not correct because:
A. The kernel was unable to execute /bin/init: This error would occur in Stage 2, after the kernel and initrd images are loaded, not in Stage 14.
C. One or more of the filesystems on the hard disk has errors and a filesystem check should be run: This error would also occur in Stage 2, when GRUB tries to access the file system that contains the GRUB configuration file, not in Stage 15.
D. The BIOS was unable to read the necessary data from the Master Boot Record to begin the boot process: This error would prevent GRUB from starting at all, not in Stage 16.
Which of the following commands reboots the system when using SysV init? (Choose TWO correct answers.)
shutdown -r now
shutdown -r "rebooting"
telinit 6
telinit 0
shutdown -k now "rebooting"
The shutdown command is used to bring the system down in a safe and controlled way. It can take various options and arguments, such as the time of shutdown, the message to broadcast to users, the halt or reboot mode, etc. The option -r instructs the shutdown command to reboot the system after shutting down. The argument now means to shut down immediately. Therefore, shutdown -r now will reboot the system without delay. The telinit command is used to change the run level of the system. It takes a single argument that specifies the new run level. The run level 6 is reserved for rebooting the system. Therefore, telinit 6 will also reboot the system. The other options are either incorrect or irrelevant. shutdown -r “rebooting” will also reboot the system, but with a delay of one minute and a message to the users. telinit 0 will halt the system, not reboot it. shutdown -k now “rebooting” will only send a warning message to the users, but not actually shut down or reboot the system. References: LPI Linux Essentials - 1.101.2, LPI Linux Administrator - 101.3
During a system boot cycle, what is the program that is run after the BIOS completes its tasks?
The bootloader
The inetd program
The init program
The kernel
The program that is run after the BIOS completes its tasks is the bootloader12. The bootloader is a small program that loads the operating system into memory and executes it. The bootloader can be located in the Master Boot Record (MBR) of the first hard disk or the boot sector of a partition for BIOS systems, or in an .efi file on the EFI System Partition for UEFI systems12. The bootloader can also display a menu to allow the user to choose from different operating systems or kernel versions to boot12.
The other options in the question are not correct because:
B. The inetd program: This is a program that listens for incoming network connections and launches the appropriate service for them. It is not involved in the boot process3.
C. The init program: This is a program that is executed by the kernel as the first user-space process. It is responsible for starting and managing other processes and services. It is not run by the BIOS.
D. The kernel: This is the core of the operating system that controls everything in the system. It is loaded and executed by the bootloader, not by the BIOS.
Which of the following information is stored within the BIOS? (Choose TWO correct answers.)
Boot device order
Linux kernel version
Timezone
Hardware configuration
The system's hostname
The BIOS (Basic Input/Output System) is a firmware that is stored in a ROM chip on the motherboard and is responsible for initializing the hardware and loading the bootloader. The BIOS has a setup utility that allows the user to configure various settings, such as the boot device order, the hardware configuration, the system date and time, the security options, etc. The BIOS does not store information about the Linux kernel version, the time zone, or the system’s hostname, as these are part of the operating system and are not relevant for the BIOS. References: LPI Linux Essentials - 1.101.1, LPI Linux Administrator - 102.1
Copyright © 2014-2026 Examstrust. All Rights Reserved
