What are two capabilities of Microsoft Defender for Endpoint? Each correct selection presents a complete solution.
NOTE: Each correct selection is worth one point.
What is the purpose of Azure Active Directory (Azure AD) Password Protection?
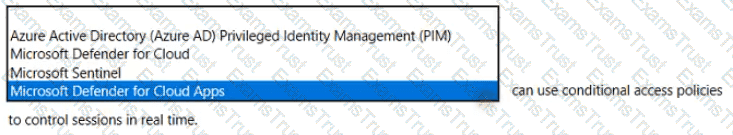
Select the answer that correctly completes the sentence.
Which two types of resources can be protected by using Azure Firewall? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
What can you use to ensure that all the users in a specific group must use multi-factor authentication (MFA) to sign in to Azure AD?
Select the answer that correctly completes the sentence.

What can you use to provide threat detection for Azure SQL Managed Instance?
Which Microsoft 365 compliance center feature can you use to identify all the documents on a Microsoft SharePoint Online site that contain a specific key word?
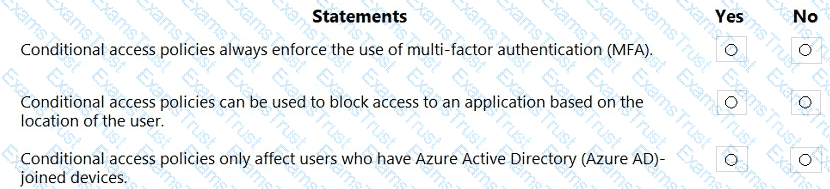
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

Select the answer that correctly completes the sentence.

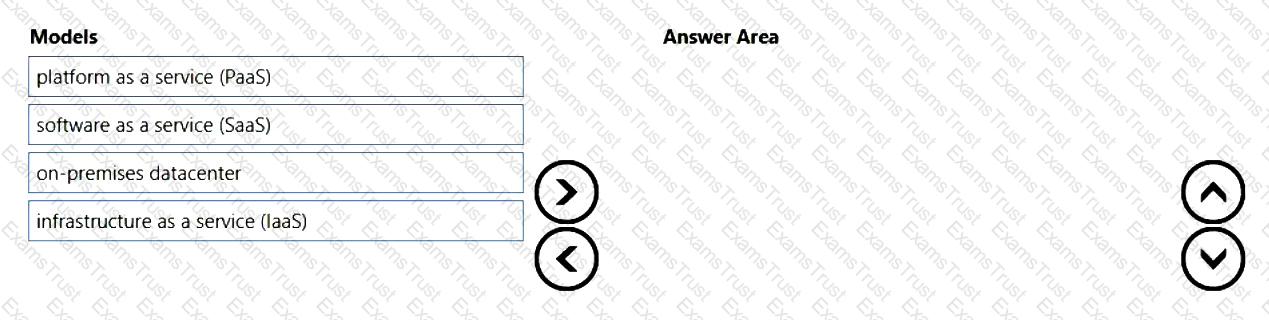
You need to identify which cloud service models place the most responsibility on the customer in a shared responsibility model.
in which order should you list the service models from the most customer responsibility (on the top) to the least customer responsibility (on the bottom)? To answer, move all models from the list of models to the answer area and arrange them in the correct order.
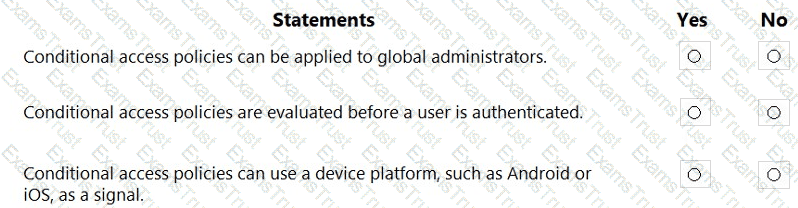
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
Select the answer that correctly completes the sentence.
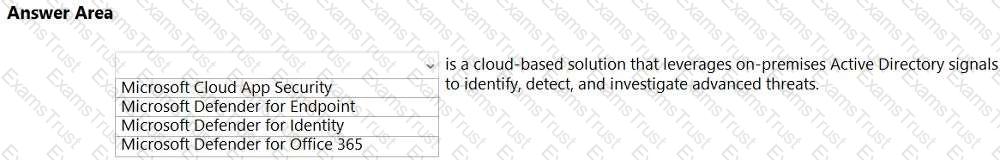
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Which Azure Active Directory (Azure AD) feature can you use to evaluate group membership and automatically remove users that no longer require membership in a group?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have an Azure subscription.
You need to implement approval-based time-bound role activation.
What should you use?
Which solution performs security assessments and automatically generates alerts when a vulnerability is found?
What can you use to provision Azure resources across multiple subscriptions in a consistent manner?
What should you use in the Microsoft Defender portal to view security trends and track the protection status of identities?
When you enable Azure AD Multi-Factor Authentication (MFA), how many factors are required for authentication?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You need to connect to an Azure virtual machine by using Azure Bastion. What should you use?
What Microsoft Purview feature can use machine learning algorithms to detect and automatically protect sensitive items?
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.
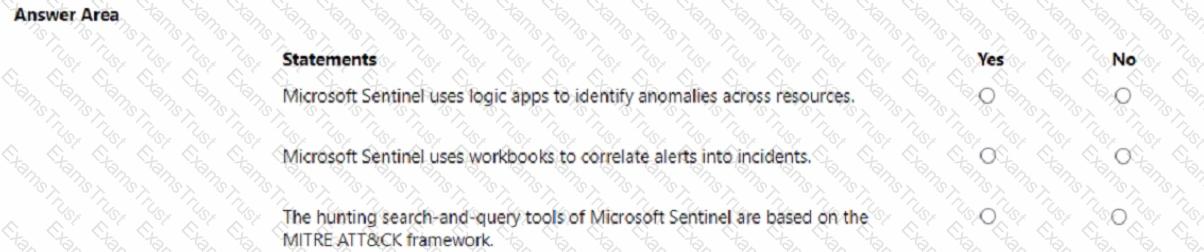
Which three authentication methods can be used by Azure Multi-Factor Authentication (MFA)? Each correct answer presents a complete solution. NOTE: Each correct selection is worth one point.
Select the answer that correctly completes the sentence.

In the Microsoft Cloud Adoption Framework for Azure, which two phases are addressed before the Ready phase? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No. NOTE: Each correct selection is worth one point.

completes the sentence.

What can you use to view the Microsoft Secure Score for Devices?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Select the answer that correctly completes the sentence.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statement, select Yes if the statement is true Otherwise, select No.
NOTE: Each connect selection a worth one point.

Which three tasks can be performed by using Azure Active Directory (Azure AD) Identity Protection? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Select the answer that correctly completes the sentence.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Select the answer that correctly completes the sentence.

Select the answer that correctly completes the sentence.

What are three uses of Microsoft Cloud App Security? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

To which three locations can a data loss prevention (DLP) policy be applied? Each correct answer presents a complete solution.
NOTE: Each correct answer is worth one point.
Select the answer that correctly completes the sentence.
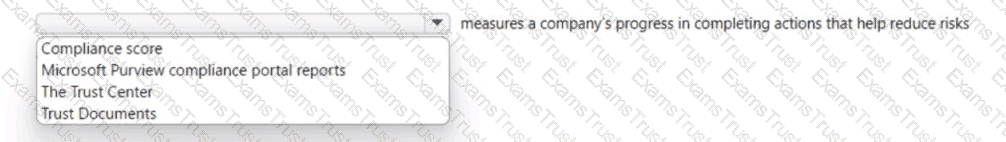
Select the answer that correctly completes the sentence.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Select the answer that correctly completes the sentence.

Select the answer that correctly completes the sentence.
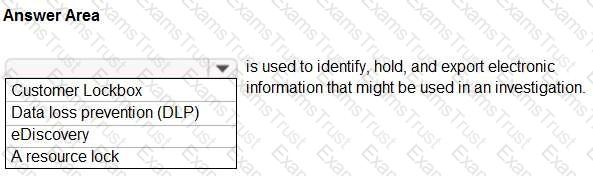
Select the answer that correctly completes the sentence.

Which Microsoft Purview data classification type supports the use of regular expressions?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Which three authentication methods can Microsoft Entra users use to reset their password? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
What can you use to provision Azure resources across multiple subscriptions in a consistent manner?
Which three statements accurately describe the guiding principles of Zero Trust? Each correct answer presents a complete solution.
NOTE: Each correct selection is worth one point.
Select the answer that correctly completes the sentence.

Select the answer that correctly completes the sentence.

For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You plan to implement a security strategy and place multiple layers of defense throughout a network infrastructure.
Which security methodology does this represent?
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

Match the types of Conditional Access signals to the appropriate definitions.
To answer, drag the appropriate Conditional Access signal type from the column on the left to its definition on the right. Each signal type may be used once, more than once, or not at all.
NOTE: Each correct match is worth one point.
