Your organization has recently implemented Netskope Private Access. During an investigation, your security team has asked you to provide a list of all hosts including domains and IP addresses that a user accessed through Netskope Private Access for the past seven days.
Which two locations in the Netskope Web UI would allow you to obtain and export the requested data? (Choose two.)
You are required to provide an additional pop-up warning to users before allowing them to proceed to Web applications categorized as "low" or "poor" by Netskope's Cloud Confidence Index. Which action would allow you to accomplish this task?
You want to set up a Netskope API connection to Box.
What two actions must be completed to enable this connection? (Choose two.)
A customer changes CCI scoring from the default objective score to another score. In this scenario, what would be a valid reason for making this change?
Your company asks you to obtain a detailed list of all events from the last 24 hours for a specific user. In this scenario, what are two methods to accomplish this task? (Choose two.)
Click the Exhibit button.
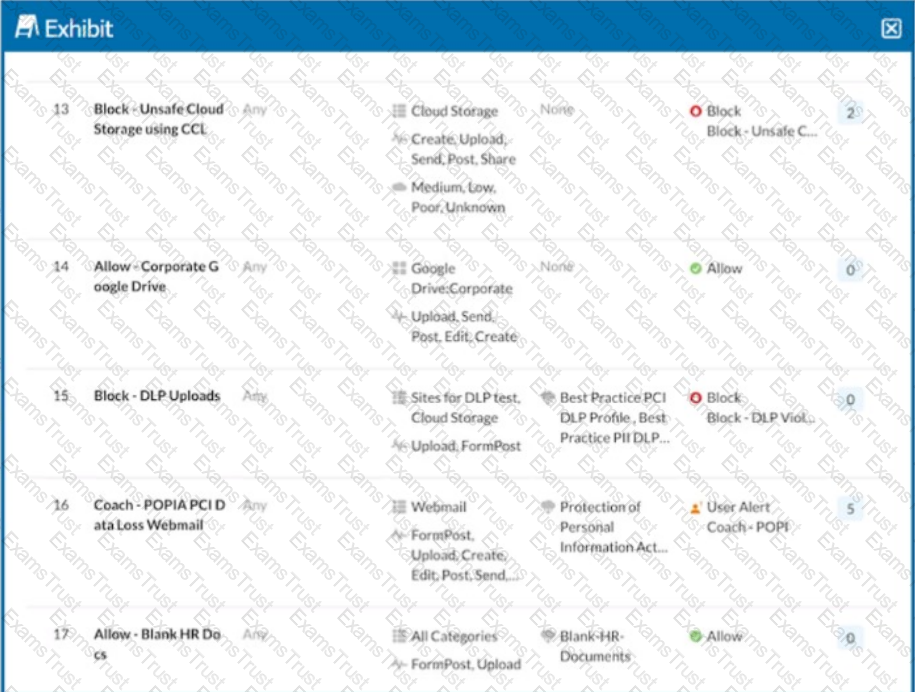
A user is uploading a file containing PCI-DSS data to the corporate Google Drive instance. You notice that the upload is not blocked by the policy shown in the exhibit. Which statement is correct in this scenario?
Your organization has implemented Netskope Private Access (NPA) for all users. Users from the European region are reporting that they are unable to access many of their applications. You suspect that the publishers for the European data center may be disconnected and you want to verify the Publishers' status.
Which two methods describe how you would accomplish this task? (Choose two.)
How do you protect your data at rest intellectual property (IP), such as source code or product designs, stored in Microsoft 365 SharePoint?
You are required to restrict cloud users from uploading data to any risky cloud storage service as defined by the Cloud Confidence Index. In the Netskope platform, which two policy elements would enable you to implement this control? (Choose two)
You need to provide a quick view under the Skope IT Applications page showing only risky shadow IT cloud applications being used.
In this scenario, which two filter combinations would you use to accomplish this task? (Choose two.)
A customer wants to detect misconfigurations in their AWS cloud instances.
In this scenario, which Netskope feature would you recommend to the customer?
Users are connecting to sanctioned cloud applications from public computers, such as from a hotel business center.
Which traffic steering method would work in this scenario?
Which two use cases would be considered examples of Shadow IT within an organization? (Choose two.)
Which two statements are correct about DLP Incidents in the Netskope platform? (Choose two.)
A company is attempting to steer traffic to Netskope using GRE tunnels. They notice that after the initial configuration, users cannot access external websites from their browsers.
What are three probable causes for this issue? (Choose three.)
What are two use cases for Netskope's DLP solution? (Choose two.)
According to Netskope. what are two preferred methods to report a URL miscategorization? (Choose two.)
You just deployed the Netskope client in Web mode and several users mention that their messenger application is no longer working. Although you have a specific real-time policy that allows this application, upon further investigation you discover that it is using proprietary encryption. You need to permit access to all the users and maintain some visibility.
In this scenario, which configuration change would accomplish this task?
What are two CASB inline interception use cases? (Choose two.)
You are deploying TLS support for real-time Web and SaaS transactions. What are two secure implementation methods in this scenario? (Choose two.)
What are two reasons why legacy solutions, such as on-premises firewalls and proxies, fail to secure the data and data access compared to Netskope Secure Web Gateway? (Choose two.)
API-enabled Protection traffic is sent to which Netskope component?
Click the Exhibit button.
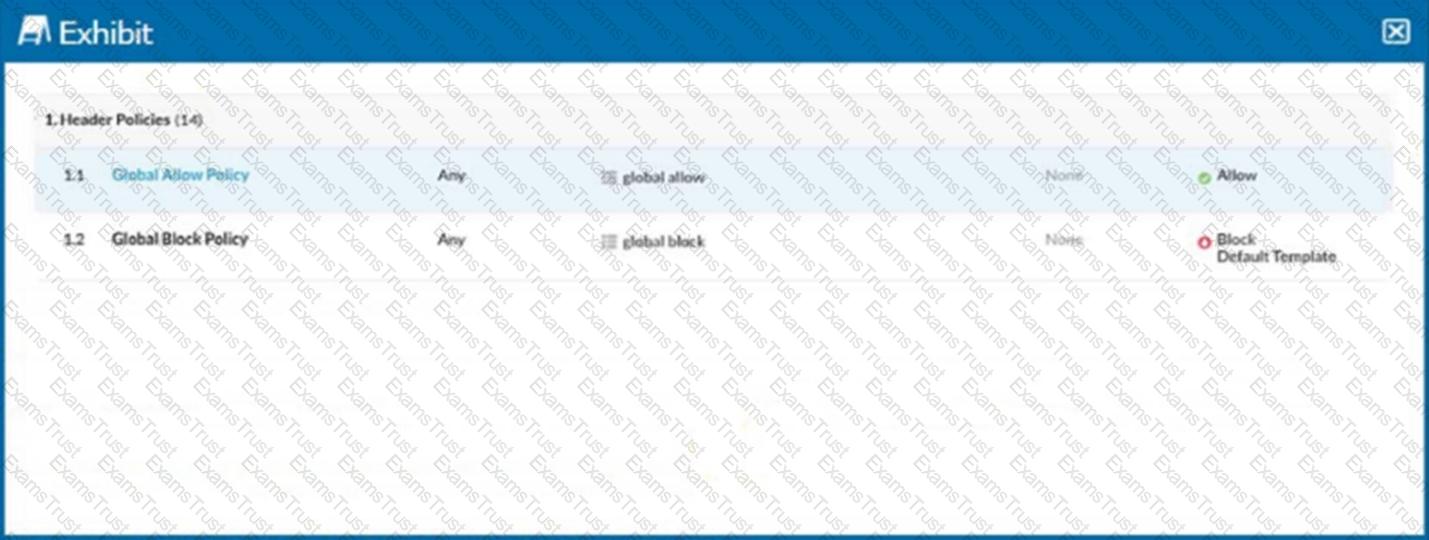
Referring to the exhibit, you have a user reporting that a blocked website is needed for legitimate business reasons. Upon review, you determine that the user has been blocked by the Global Block policy. You need to create an exception forthat domain. You create a custom URL list that includes the domain.
In this scenario, which two actions would allow this access? (Choose two.)
In which two scenarios would you use SD-WAN technology? (Choose two.)
You want to use an out-of-band API connection into your sanctioned Microsoft 365 OneDrive for Business application to find sensitive content, enforce near real-time policy controls, and quarantine malware.
In this scenario, which primary function in the Netskope platform would you use to connect your application to Netskope?
You added a new private app definition and created a Real-time Protection policy to allow access for all users. You have a user who reports that they are unable to access the application but all other applications work fine.
Which statement correctly describes how to troubleshoot this issue using the Netskope Web UI?
Which three status indicators does the NPA Troubleshooter Tool provide when run? (Choose three)
What are two supported ways to provision users to your customer's Netskope tenant? (Choose two.)
Which two statements describe a website categorized as a domain generated algorithm (DGA)? (Choose two.)
Click the Exhibit button.
Referring to the exhibit, which statement accurately describes the difference between Source IP (Egress) and Source IP (User) address?
You are asked to review files affected by malware in your organization. In this scenario, which two actions are possible and would be accessible from the Netskope UI -> Incidents --> Malware? (Choose two)
You have an issue with the Netskope client connecting to the tenant.
In this scenario, what are two ways to collect the logs from the client machine? (Choose two.)
Exhibit
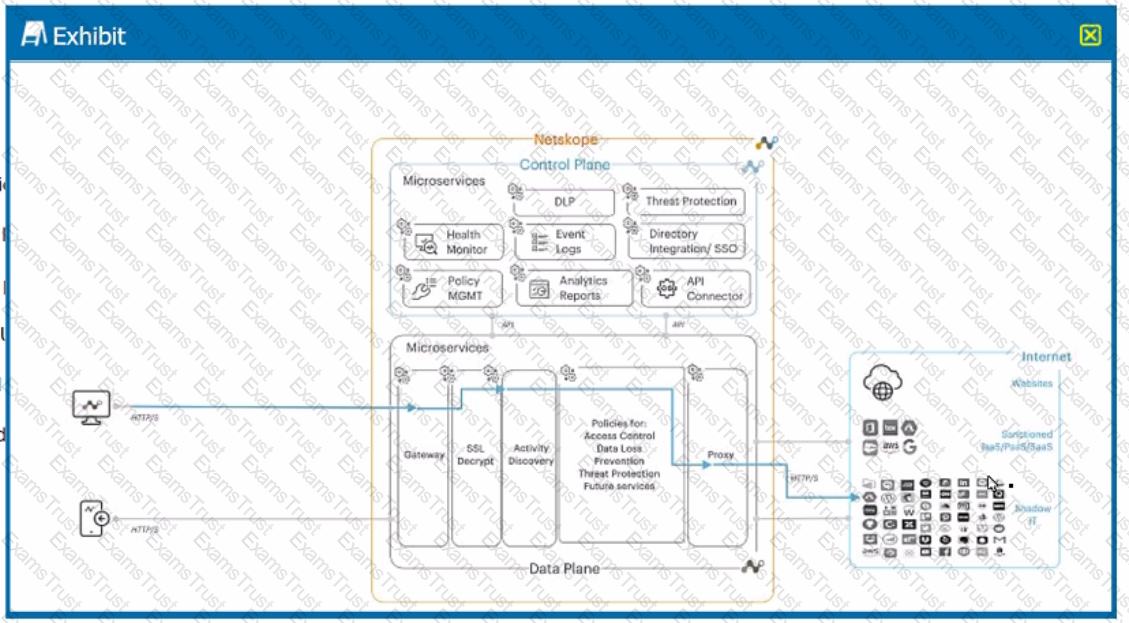
A user is connected to a cloud application through Netskope's proxy.
In this scenario, what information is available at Skope IT? (Choose three.)
Which three technologies describe the primary cloud service models as defined by the National Institute of Standards and Technology (NIST)? (Choose three.)
You want to enable Netskope to gain visibility into your users' cloud application activities in an inline mode.
In this scenario, which two deployment methods would match your inline use case? (Choose two.)
When designing an architecture with Netskope Private Access, which element guarantees connectivity between the Netskope cloud and the private application?
You are creating a real-time policy for cloud applications.
In addition to users, groups, and organizational units, which two source criteria would support this scenario? (Choose two.)
You are required to create a policy that will notify and allow users to log into their personal Google Drive instance.
Which two policy components must be configured to enforce this use case? (Choose two.)