Review the exhibit.
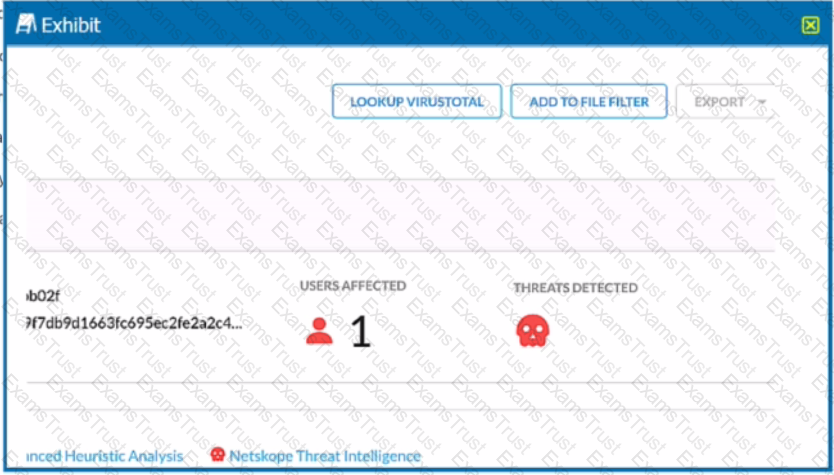
You are at the Malware Incident page. A virus was detected by the Netskope Heuristics Engine. Your security team has confirmed that the virus was a test data file You want to allow the security team to use this file
Referring to the exhibit, which two statements are correct? (Choose two.)
A company allows their users to access OneDrive on their managed laptops. It is against corporate policy to upload any documents to their personal OneDrive. The company needs to enforce this policy to protect their customer’s sensitive data.
What are two ways to enforce this policy? (Choose two.)
You want to prevent a document stored in Google Drive from being shared externally with a public link. What would you configure in Netskope to satisfy this requirement?
You have created a specific Skope IT application events query and want to have the query automatically run and display the results every time you log into your tenant.
Which two statements are correct in this scenario? (Choose two.)
Your organization has a homegrown cloud application. You are required to monitor the activities that users perform on this cloud application such as logins, views, and downloaded files. Unfortunately, it seems Netskope is unable to detect these activities by default.
How would you accomplish this goal?
You want to provide malware protection for all cloud storage applications.
In this scenario, which action would accomplish this task?
Your company wants to deploy Netskope using a tunnel because you have a mixture of device operating systems. You also do not want to enable encryption because you want to maximize bandwidth.
Your company needs to keep quarantined files that have been triggered by a DLP policy. In this scenario, which statement Is true?
Netskope is being used as a secure Web gateway. Your organization's URL list changes frequently. In this scenario, what makes It possible for a mass update of the URL list in the Netskope platform?
Your company has Microsoft Azure ADFS set up as the Identity Provider (idP). You need to deploy the Netskope client to all company users on Windows laptops without user intervention.
In this scenario, which two deployment options would you use? (Choose two.)
An engineering firm is using Netskope DLP to identify and block sensitive documents, including schematics and drawings. Lately, they have identified that when these documents are blocked, certain employees may be taking screenshots and uploading them. They want to block any screenshots from being uploaded.
Which feature would you use to satisfy this requirement?
The risk team at your company has determined that traffic from the sales team to a custom Web application should not be inspected by Netskope. All other traffic to the Web application should continue to be inspected. In this scenario, how would you accomplish this task?
Your company asks you to use Netskope to integrate with Endpoint Detection and Response (EDR) vendors such as CrowdStrike. In this scenario, what is a requirement for a successful Integration and sharing of threat data?
You are testing policies using the DLP predefined identifier "Card Numbers (Major Networks; all)." No DLP policy hits are observed.
You are implementing tenant access security and governance controls for privileged users. You want to start with controls that are natively available within the Netskope Cloud Security Platform and do not require external or third-party integration.
Which three access controls would you use in this scenario? (Choose three.)
Your learn is asked to Investigate which of the Netskope DLP policies are creating the most incidents. In this scenario, which two statements are true? (Choose two.)
Which statement describes how Netskope's REST API, v1 and v2, handles authentication?
Your customer is using a virtual desktop infrastructure (VDI) for their support engineers. Multiple users will be logging into the same device, and they want to detect activities for each user.
You are using Skope IT to analyze and correlate a security incident. You are seeing too many events generated by API policies. You want to filter for logs generated by the Netskope client only.
Your company wants to know if there has been any unusual user activity. In the UI, you go to Skope IT -> Alerts.
Which two types of alerts would you filter to find this information? (Choose two.)
Netskope support advised you to enable DTLS for belter performance. You added firewall rules to allow UDP port 443 traffic. These settings are part of which configuration element when enabled in the Netskope tenant?
Which statement describes a requirement for deploying a Netskope Private Application (NPA) Publisher?
Your customer is migrating all of their applications over to Microsoft 365 and Azure. They have good practices and policies in place (or their inline traffic, but they want to continuously detect reconfigurations and enforce compliance standards.
Which two solutions would satisfy their requirements? (Choose two.)
You have deployed a development Web server on a public hosting service using self-signed SSL certificates. After some troubleshooting, you determined that when the Netskope client is enabled, you are unable to access the Web server over SSL. The default Netskope tenant steering configuration is in place.
In this scenario, which two settings are causing this behavior? (Choose two.)
Review the exhibit.
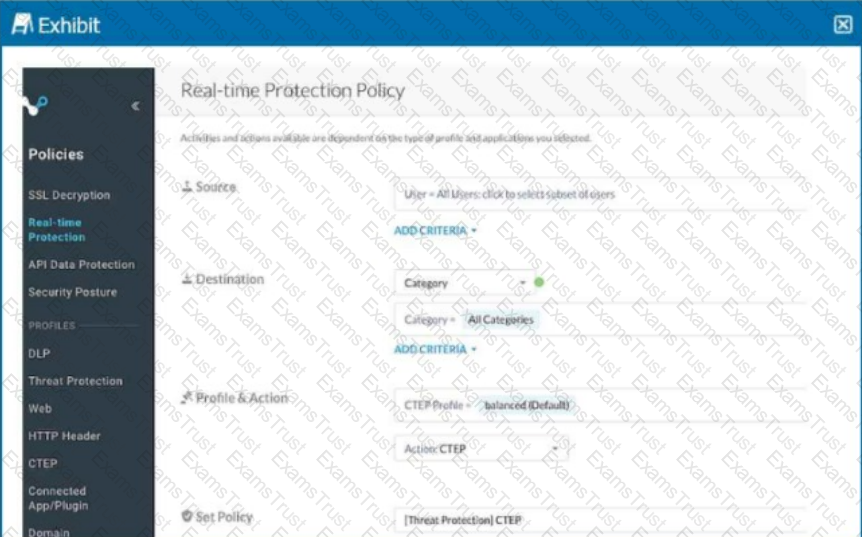
Your Real-time Protection policy contains some rules with only a browse activity. The exhibit shows a new policy rule.
Where is the correct location to place this rule?
Review the exhibit.
add log-upload syslogng parserconfig set log-upload syslogng parserconfig 0
logsource <log-source>
You are asked to deploy a virtual appliance OPLP to accept syslog messages directly from the enterprise Palo Alto Networks firewall. You believe that you have configured the OPLP to accept the firewall logs, yet they are not appearing in Risk Insights. Referring to the exhibit, which parser name would be required to complete the new configuration?
You are troubleshooting private application access from a user's computer. The user is complaining that they cannot access the corporate file share; however, the private tunnel seems to be established. You open the npadebuglog.log file in a text editor and cannot find any reference to the private application.