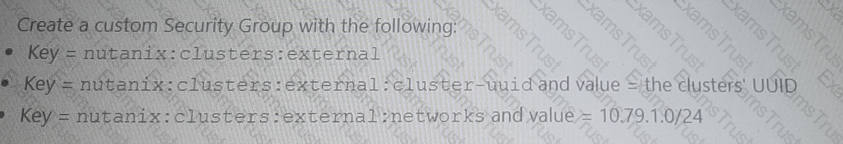
An administrator has deployed an NC2 on AWS cluster that is running mixed workloads. Multiple SQL database are running on the NC2 cluster using a native subnet of 10.78.1.0/24.
The administrator wants to ensure only application servers from source subnet 10.79.1.0/24 that reside outside of the NC2 cluster can access the databases.
Which two actions will help the administrator most securely achieve this? (Choose two.)
A)
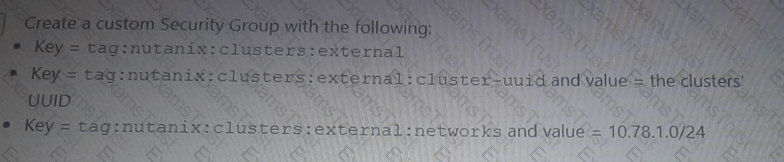
B)

C)

D)
An organization wants to control network traffic at the individual User VM (UVM) subnet level.
Which action will help achieve this goal?
Which entity should be contacted for cloud hardware supported (EC2 instances, VPC, etc) related to NC2?
An administrator is deploying an NC2 cluster into an existing AWS VPC.
The cluster deployment fails, with the following error message:

Why has the deployment failed?
An administrator has been tasked with performing a test migrating from an NC2 environment to a Nutanix on-premisesenvironment.
Where should the administrator perform this task?
An administrator has created an NC2 cluster on AWS, but the NC2 console has issued this alert:

Which two scenarios could have resulted in the cluster creation failure? (Choose two.)
Exhibit.
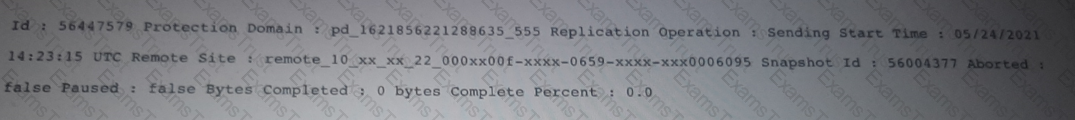
What does the exhibit indicate?
The cluster is configured as follows:
* 8 nodes
* Prism Central Deployed
* Files Deployed
Following the deployment, the administrator experiences network connectivity issues.
Which reason explains the connectivity issues?
An administrator is tasked with deploying a VM in an NC2 cluster on AWS that needs to by accessed by resources within the on-premises datacenter.
The cluster has the following characteristics:
*8 nodes
*Resides in the us-east-1a Availability Zone
*Contains 13 Subnets
*Has access to a Direct Connect connection
*Subnet that the User VM (UVM) is being deployed to:UserVM_subnet
There are multiple VMs within the cluster and the UserVM_subnet has access to the on-premises resources.
The administrator deploys the machine, but communication is not possible.
What is the most likely resolution for this situation?
What is an available log module when configuring a syslog server in the Prism Central Admin Center?
A company needs to create virtual interfaces directly to public AWS S3 services. The company also wants to bypass any internet service providers in the network path.
Which method will best satisfy this requirement?
An administrator is planning to leverage NC2 on AWS for an elastic DR scenario where the initial cluster is using 13en.metal.
Which two additional node types are supported for cluster expansion? (Choose two.)
In which two ways should an NC2 on AWS cluster be hibernated manually? (Choose two.)
An administrator needs to understand which of the services implemented on their NC2 AWS deployment will be protected with Cluster protect.
Which service of feature is Cluster Protect able to both protect and recover its associated metadata?
An administrator has deployed NC2 on AWS. The cluster deployment completed successfully.
After deployment, the administrator created a subnet in AWS, added it as a network in Prism Element, deployed Prism Central using the newly-configured network, and registered the cloud cluster with it.
The on-premises network and AWS are connected via a Site-to-Site VPN. Cluster nodes, CVM, and Prism Central can communicate with each other, but cannot be accessed from the on-premises network.
What two issues might be the cause of this problem? (Choose two.)
An administrator has been tasked with deploying a new production NC2 cluster on AWS and is studying the deployment..
AWS supports EC2 bare-metal instances in regions with at least how many partitions?
An administrator has deployed an NC2 cluster on AWS to an existing environment for VDI.
Afterwards, the corporate security teamsdirectthe administrator to reuse an existing AWS subnet, 10.79.4.0/24 that has two EC2 instances: EC2-1 (10.79.4.200) and EC2-2 (10.79.4.201). The security team indicates that this directive is to avoid overlap with the AHV IPAM.
Which two configuration actions should the administrator take to ensure there are no configuration issues? (Choose two.)
Which entity should be contacted for AOS software supported related to NC2?
An administrator needs the permissions to create and manage multiple organizations and clusters in NC2, as well as manage user access for the entire company.
What role should be assigned to meet the minimum requirements of this task?
An administrator is planning an NC2 deployment and wants to connect to AWS Services privately from the corporate VPC without going through the public internet.
Which connectivity solution should the administrator use?
Which service enables the monitoring of key metrics on various AWS services, inducing EC2, EBS, and VPC for an NC2 cluster deployments?
An organization plans to use the Cluster Protect feature to protect the cluster data.
Which license will satisfy this requirement?