Which SOAR feature coordinates across technologies, security teams, and external users for centralized data visibility and action?
On which security principle does virtualization have positive effects?
Which option would be an example of PII that you need to prevent from leaving your enterprise network?
Which two pieces of information are considered personally identifiable information (PII)? (Choose two.)
Which of the following is an AWS serverless service?
In which two cloud computing service models are the vendors responsible for vulnerability and patch management of the underlying operating system? (Choose two.)
Under which category does an application that is approved by the IT department, such as Office 365, fall?
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?
Which Palo Alto Networks tool is used to prevent endpoint systems from running malware executables such as viruses, trojans, and rootkits?
In which situation would a dynamic routing protocol be the quickest way to configure routes on a router?
What is the definition of a zero-day threat?
Which activities do local organization security policies cover for a SaaS application?
Which Palo Alto Networks tools enable a proactive, prevention-based approach to network automation that accelerates security analysis?
Which of the following is a service that allows you to control permissions assigned to users in order for them to access and utilize cloud resources?
In addition to local analysis, what can send unknown files to WildFire for discovery and deeper analysis to rapidly detect potentially unknown malware?
When signature-based antivirus software detects malware, what three things does it do to provide protection? (Choose three.)
Which product from Palo Alto Networks extends the Security Operating Platform with the global threat intelligence and attack context needed to accelerate analysis, forensics, and hunting workflows?
Which native Windows application can be used to inspect actions taken at a specific time?
Which of the following is a CI/CD platform?
How does DevSecOps improve the Continuous Integration/Continuous Deployment (CI/CD) pipeline?
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
What are two disadvantages of Static Rout ng? (Choose two.)
In addition to integrating the network and endpoint components, what other component does Cortex integrate to speed up IoC investigations?
Which subnet does the host 192.168.19.36/27 belong?
What is the recommended method for collecting security logs from multiple endpoints?
What does SOAR technology use to automate and coordinate workflows?
Why have software developers widely embraced the use of containers?
Systems that allow for accelerated incident response through the execution of standardized and automated playbooks that work upon inputs from security technology and other data flows are known as what?
Which attacker profile acts independently or as part of an unlawful organization?
Which statement describes DevOps?
SecOps consists of interfaces, visibility, technology, and which other three elements? (Choose three.)
Which network device breaks networks into separate broadcast domains?
Which classification of IDS/IPS uses a database of known vulnerabilities and attack profiles to identify intrusion attempts?
How does Prisma SaaS provide protection for Sanctioned SaaS applications?
Which type of malware takes advantage of a vulnerability on an endpoint or server?
Which VM-Series virtual firewall cloud deployment use case reduces your environment's attack surface?
What are two key characteristics of a Type 1 hypervisor? (Choose two.)
Based on how much is managed by the vendor, where can CaaS be situated in the spread of cloud computing services?
Which action must Secunty Operations take when dealing with a known attack?
In which phase of the cyberattack lifecycle do attackers establish encrypted communication channels back to servers across the internet so that they can modify their attack objectives and methods?
Organizations that transmit, process, or store payment-card information must comply with what standard?
What is the purpose of SIEM?
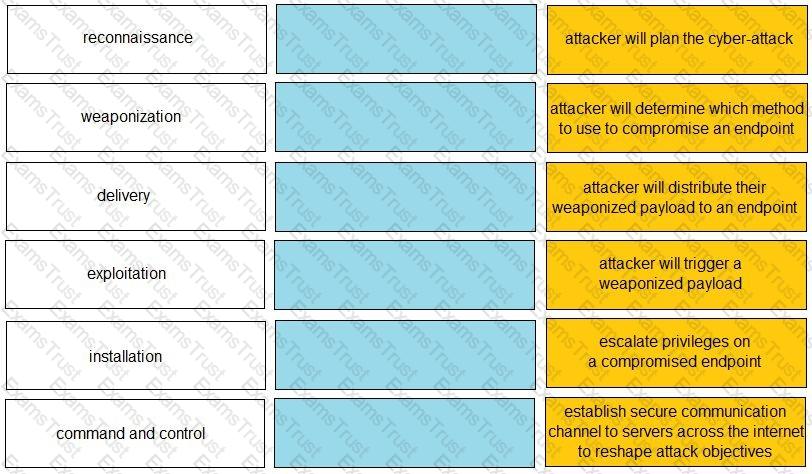
Given the graphic, match each stage of the cyber-attack lifecycle to its description.

TCP is the protocol of which layer of the OSI model?
Which capability of a Zero Trust network security architecture leverages the combination of application, user, and content identification to prevent unauthorized access?
At which layer of the OSI model are routing protocols defined?