An engineer configures a destination NAT policy to allow inbound access to an internal server in the DMZ. The NAT policy is configured with the following values:
- Source zone: Outside and source IP address 1.2.2.2
- Destination zone: Outside and destination IP address 2.2.2.1
The destination NAT policy translates IP address 2.2.2.1 to the real IP address 10.10.10.1 in the DMZ zone.
Which destination IP address and zone should the engineer use to configure the security policy?
An organization has recently migrated its infrastructure and configuration to NGFWs, for which Panorama manages the devices. The organization is coming from a L2-L4 firewall vendor, but wants to use App-ID while identifying policies that are no longer needed.
Which Panorama tool can provide a solution?
To ensure that a Security policy has the highest priority, how should an administrator configure a Security policy in the device group hierarchy?
An administrator wants to enable WildFire inline machine learning. Which three file types does WildFire inline ML analyze? (Choose three.)
A new firewall has the Threat Prevention subscription, but the Antivirus does not appear in Dynamic Updates.
What must occur to have Antivirus signatures update?
A network administrator is trying to prevent domain username and password submissions to phishing sites on some allowed URL categories
Which set of steps does the administrator need to take in the URL Filtering profile to prevent credential phishing on the firewall?
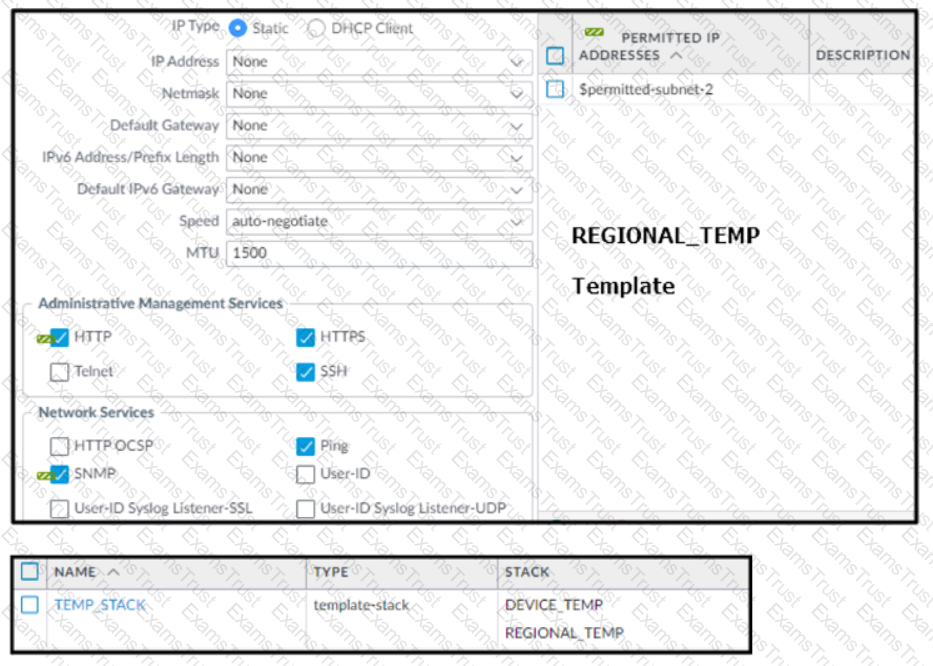
Based on the screenshots above, and with no configuration inside the Template Stack itself, what access will the device permit on its Management port?
How should an administrator enable the Advance Routing Engine on a Palo Alto Networks firewall?
An engineer is reviewing policies after a PAN-OS upgrade What are the two differences between Highlight Unused Rules and the Rule Usage Hit counters immediately after a reboot?
An engineer manages a high availability network and requires fast failover of the routing protocols. The engineer decides to implement BFD.
Which three dynamic routing protocols support BFD? (Choose three.)
An administrator plans to deploy 15 firewalls to act as GlobalProtect gateways around the world. Panorama will manage the firewalls.
The firewalls will provide access to mobile users and act as edge locations to on-premises infrastructure. The administrator wants to scale the configuration out quickly and wants all of the firewalls to use the same template configuration.
Which two solutions can the administrator use to scale this configuration? (Choose two.)
Which new PAN-OS 11.0 feature supports IPv6 traffic?
An engineer needs to configure a standardized template for all Panorama-managed firewalls. These settings will be configured on a template named "Global" and will be included in all template stacks.
Which three settings can be configured in this template? (Choose three.)
An engineer must configure a new SSL decryption deployment.
Which profile or certificate is required before any traffic that matches an SSL decryption rule is decrypted?
An engineer needs to collect User-ID mappings from the company’s existing proxies. What two methods can be used to pull this data from third-party proxies? (Choose two)
Which configuration change will improve network reliability and ensure minimal disruption during tunnel failures?
An administrator has configured OSPF with Advanced Routing enabled on a Palo Alto Networks firewall running PAN-OS 10.2. After OSPF was configured, the administrator noticed that OSPF routes were not being learned.
Which two actions could an administrator take to troubleshoot this issue? (Choose two.)
View the screenshots
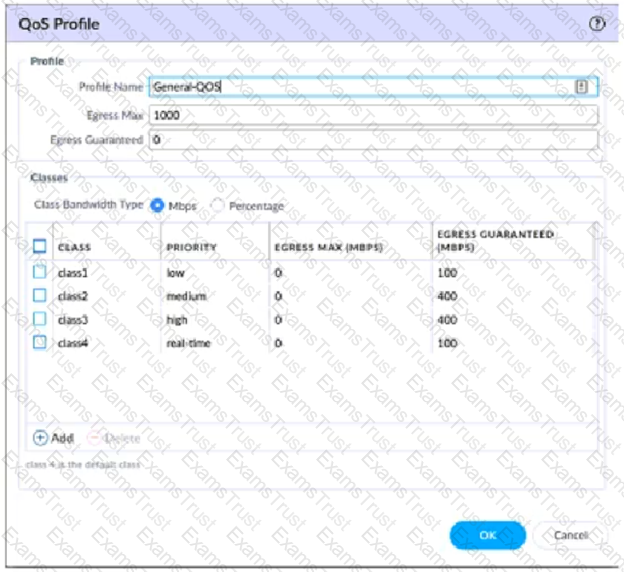
A QoS profile and policy rules are configured as shown. Based on this information which two statements are correct?
An administrator receives the following error message:
"IKE phase-2 negotiation failed when processing Proxy ID. Received local id 192.168 33 33/24 type IPv4 address protocol 0 port 0, received remote id 172.16 33.33/24 type IPv4 address protocol 0 port 0."
How should the administrator identify the root cause of this error message?
The decision to upgrade PAN-OS has been approved. The engineer begins the process by upgrading the Panorama servers, but gets an error when attempting the install. When performing an upgrade on Panorama to PAN-OS, what is the potential cause of a failed install?
An administrator has purchased WildFire subscriptions for 90 firewalls globally.
What should the administrator consider with regards to the WildFire infra-structure?
An administrator configures a site-to-site IPsec VPN tunnel between a PA-850 and an external customer on their policy-based VPN devices.
What should an administrator configure to route interesting traffic through the VPN tunnel?
During a routine security audit, the risk and compliance team notices a series of WildFire logs that contain a "malicious" verdict and the action "allow." Upon further inspection, the team confirms that these same threats are automatically blocked by the firewalls the following day. How can the existing configuration be adjusted to ensure that new threats are blocked within minutes instead of having to wait until the following day?
Following a review of firewall logs for traffic generated by malicious activity, how can an administrator confirm that WildFire has identified a virus?
What is the best description of the Cluster Synchronization Timeout (min)?
A security engineer is informed that the vulnerability protection profile of their on-premises Palo Alto Networks firewall is triggering on a common Threat ID, and which has been determined to be a false positive. The engineer is asked to resolve the issue as soon as possible because it is causing an outage for a critical service The engineer opens the vulnerability protection profile to add the exception, but the Threat ID is missing.
Which action is the most operationally efficient for the security engineer to find and implement the exception?
Certain services in a customer implementation are not working, including Palo Alto Networks Dynamic version updates. Which CLI command can the firewall administrator use to verify if the service routes were correctly installed and that they are active in the Management Plane?
Which function does the HA4 interface provide when implementing a firewall cluster which contains firewalls configured as active-passive pairs?
A company has configured a URL Filtering profile with override action on their firewall. Which two profiles are needed to complete the configuration? (Choose two)
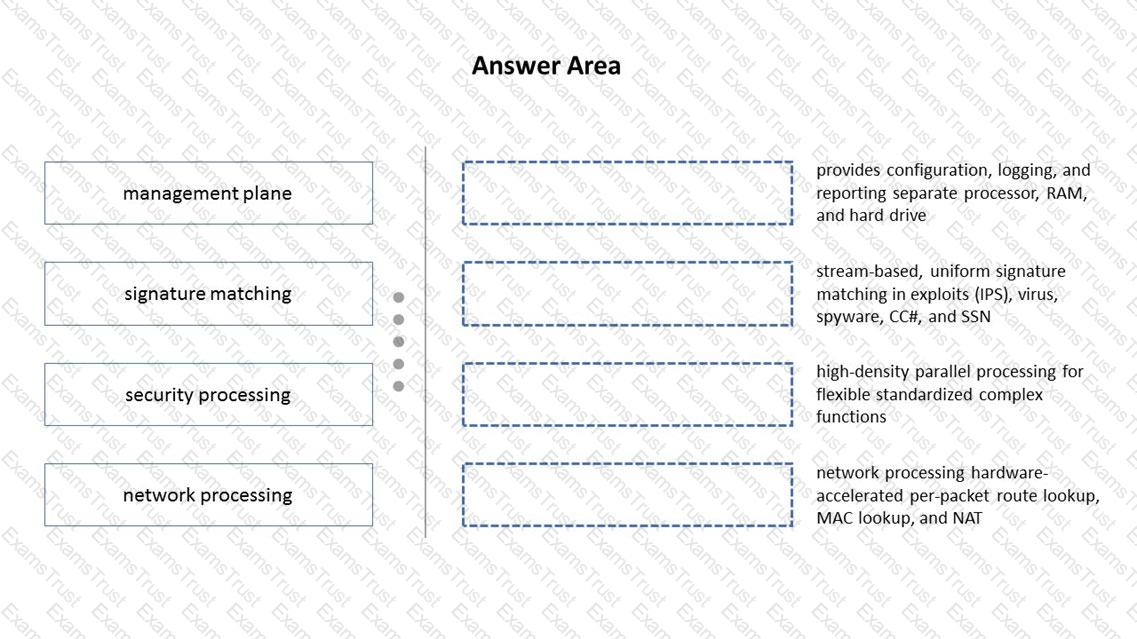
Match the terms to their corresponding definitions
An administrator would like to determine which action the firewall will take for a specific CVE. Given the screenshot below, where should the administrator navigate to view this information?
An administrator is attempting to create policies tor deployment of a device group and template stack. When creating the policies, the zone drop down list does not include the required zone.
What must the administrator do to correct this issue?
Where can a service route be configured for a specific destination IP?
A firewall engineer creates a source NAT rule to allow the company's internal private network 10.0.0.0/23 to access the internet. However, for security reasons, one server in that subnet (10.0.0.10/32) should not be allowed to access the internet, and therefore should not be translated with the NAT rule.
Which set of steps should the engineer take to accomplish this objective?
Panorama is being used to upgrade the PAN-OS version on a pair of firewalls in an active/passive high availability (HA) configuration. The Palo Alto Networks best practice upgrade steps have been completed in Panorama (Panorama upgraded, backups made, content updates, and disabling "Preemptive" pushed), and the firewalls are ready for upgrade. What is the next best step to minimize downtime and ensure a smooth transition?
What type of NAT is required to configure transparent proxy?
A network security engineer needs to ensure that virtual systems can communicate with one another within a Palo Alto Networks firewall. Separate virtual routers (VRs) are created for each virtual system.
In addition to confirming security policies, which three configuration details should the engineer focus on to ensure communication between virtual systems? (Choose three.)
Which CLI command displays the physical media that are connected to ethernet1/8?
Which statement regarding HA timer settings is true?
Which type of policy in Palo Alto Networks firewalls can use Device-ID as a match condition?
Which three actions can Panorama perform when deploying PAN-OS images to its managed devices? (Choose three.)
A remote administrator needs access to the firewall on an untrust interface. Which three options would you configure on an interface Management profile to secure management access? (Choose three)
When using certificate authentication for firewall administration, which method is used for authorization?
An administrator is creating a new Dynamic User Group to quarantine users for suspicious activity.
Which two objects can Dynamic User Groups use as match conditions for group membership? (Choose two.)
A security engineer needs firewall management access on a trusted interface.
Which three settings are required on an SSL/TLS Service Profile to provide secure Web UI authentication? (Choose three.)
A customer would like to support Apple Bonjour in their environment for ease of configuration.
Which type of interface in needed on their PA-3200 Series firewall to enable Bonjour Reflector in a segmented network?
An administrator needs to identify which NAT policy is being used for internet traffic.
From the Monitor tab of the firewall GUI, how can the administrator identify which NAT policy is in use for a traffic flow?
When you import the configuration of an HA pair into Panorama, how do you prevent the import from affecting ongoing traffic?
An engineer is monitoring an active/active high availability (HA) firewall pair.
Which HA firewall state describes the firewall that is experiencing a failure of a monitored path?
A network administrator is troubleshooting an issue with Phase 2 of an IPSec VPN tunnel The administrator determines that the lifetime needs to be changed to match the peer. Where should this change be made?
Which DoS Protection Profile detects and prevents session exhaustion attacks against specific destinations?
When backing up and saving configuration files, what is achieved using only the firewall and is not available in Panorama?
An administrator plans to install the Windows-Based User-ID Agent to prevent credential phishing.
Which installer package file should the administrator download from the support site?
Refer to Exhibit:
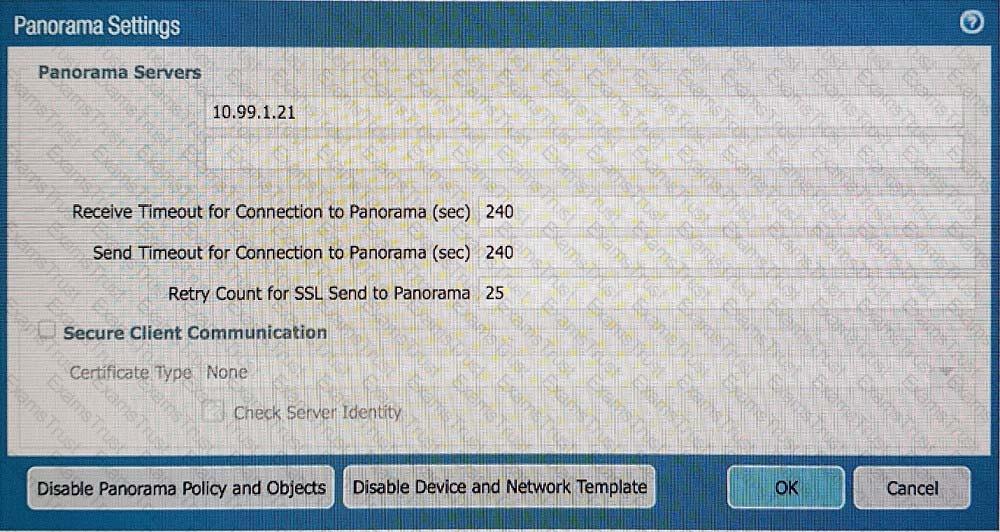
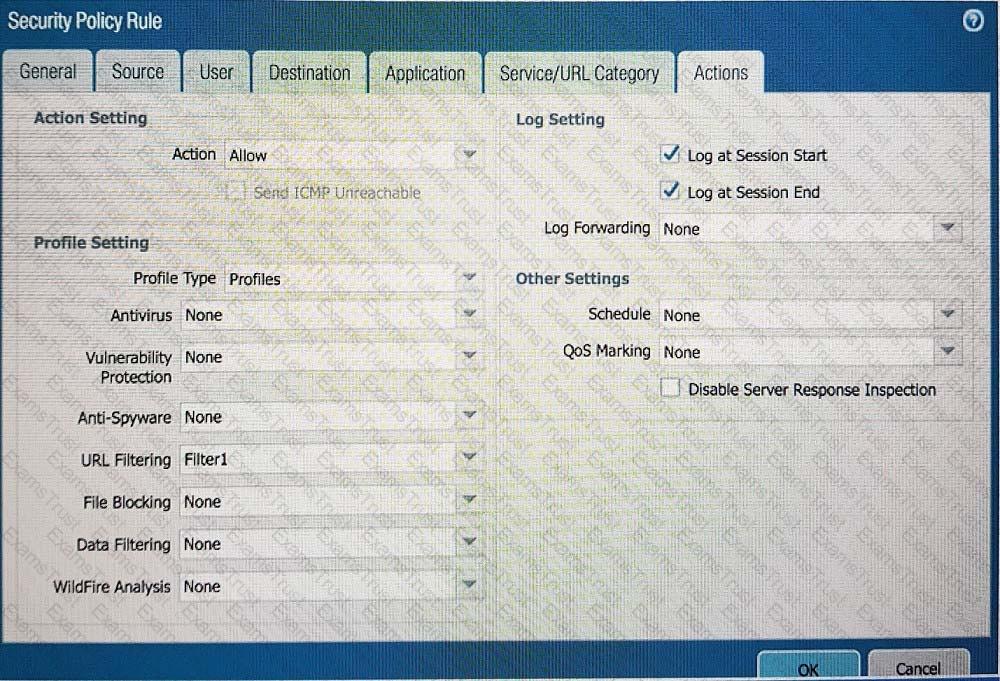
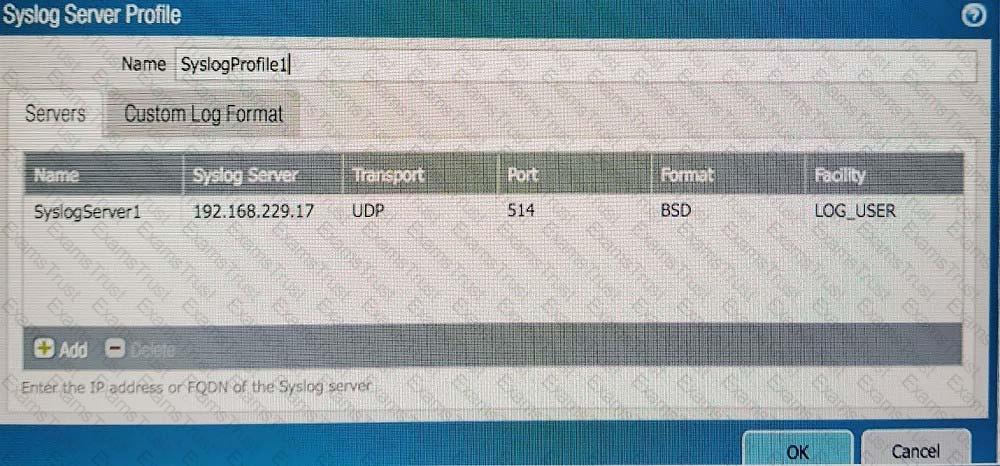
An administrator can not see any Traffic logs from the Palo Alto Networks NGFW in Panorama reports. The configuration problem seems to be on the firewall. Which settings, if configured incorrectly, most likely would stop only Traffic logs from being sent from the NGFW to Panorama?
A)
B)
C)
D)
An engineer is reviewing the following high availability (HA) settings to understand a recent HAfailover event.
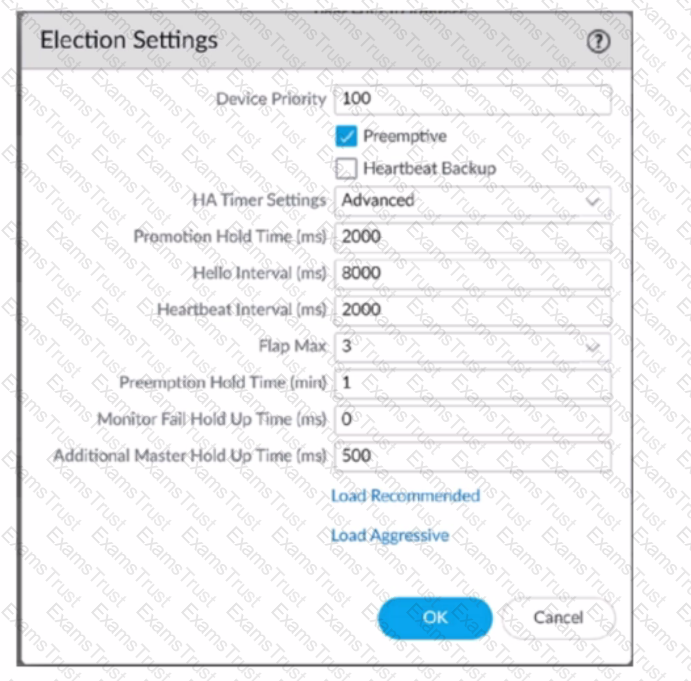
Which timer determines the frequency between packets sent to verify that the HA functionality on the other HA firewall is operational?
Which translated port number should be used when configuring a NAT rule for a transparent proxy?
An organization conducts research on the benefits of leveraging the Web Proxy feature of PAN-OS 11.0.
What are two benefits of using an explicit proxy method versus a transparent proxy method? (Choose two.)
A firewall administrator is changing a packet capture filter to troubleshoot a specific traffic flow Upon opening the newly created packet capture, the administrator still sees traffic for the previous fitter What can the administrator do to limit the captured traffic to the newly configured filter?
An enterprise Information Security team has deployed policies based on AD groups to restrict user access to critical infrastructure systems. However, a recent phishing campaign against the organization has prompted Information Security to look for more controls that can secure access to critical assets. For users that need to access these systems. Information Security wants to use PAN-OS multi-factor authentication (MFA) integration to enforce MFA.
What should the enterprise do to use PAN-OS MFA?
Given the following snippet of a WildFire submission log, did the end user successfully download a file?
A firewall engineer is tasked with defining signatures for a custom application. Which two sources can the engineer use to gather information about the application patterns'? (Choose two.)
SSL Forward Proxy decryption is configured, but the firewall uses Untrusted-CA to sign the website certificate. End-users are receiving the "security certificate is not trusted" warning. Without SSL decryption, the web browser shows that the website certificate is trusted and signed by a well-known certificate chain Well-Known-Intermediate and Well-Known-Root-CA. The network security administrator who represents the customer requires the following two behaviors when SSL Forward Proxy is enabled:
End-users must not get the warning for the website
End-users should get the warning for any other untrusted websiteWhich approach meets the two customer requirements?
When creating a Policy-Based Forwarding (PBF) policy, which two components can be used? (Choose two.)
If a URL is in multiple custom URL categories with different actions, which action will take priority?
A network security administrator wants to begin inspecting bulk user HTTPS traffic flows egressing out of the internet edge firewall. Which certificate is the best choice to configure as an SSL Forward Trust certificate?
A network security engineer is going to enable Zone Protection on several security zones How can the engineer ensure that Zone Protection events appear in the firewall's logs?
Review the screenshot of the Certificates page.
An administrator for a small LLC has created a series of certificates as shown, to use for a planned Decryption roll out. The administrator has also installed the self-signed root certificate in all client systems.
When testing, they noticed that every time a user visited an SSL site, they received unsecured website warnings.
What is the cause of the unsecured website warnings?
An administrator has a Palo Alto Networks NGFW. All security subscriptions and decryption are enabled and the system is running close to its resource limits.
Knowing that using decryption can be resource-intensive, how can the administrator reduce the load on the firewall?
A firewall architect is attempting to install a new Palo Alto Networks NGFW. The company has previously had issues moving all administrative functions onto a data plane interface to meet the design limitations of the environment. The architect is able to access the device for HTTPS and SSH; however, the NGFW can neither validate licensing nor get updates. Which action taken by the architect will resolve this issue?
A firewall administrator is configuring an IPSec tunnel between a company's HQ and a remote location. On the HQ firewall, the interface used to terminate the IPSec tunnel has a static IP. At the remote location, the interface used to terminate the IPSec tunnel has a DHCP assigned IP address.
Which two actions are required for this scenario to work? (Choose two.)
A company has recently migrated their branch office's PA-220S to a centralized Panorama. This Panorama manages a number of PA-7000 Series and PA-5200 Series devices All device group and template configuration is managed solely within Panorama
They notice that commit times have drastically increased for the PA-220S after the migration
What can they do to reduce commit times?
A firewall engineer is migrating port-based rules to application-based rules by using the Policy Optimizer. The engineer needs to ensure that the new application-based rules are future-proofed, and that they will continue to match if the existing signatures for a specific application are expanded with new child applications. Which action will meet the requirement while ensuring that traffic unrelated to the specific application is not matched?
An administrator connects a new fiber cable and transceiver Ethernet1/1 on a Palo Alto Networks firewall. However, the link does not come up. How can the administrator troubleshoot to confirm the transceiver type, tx-power, rxpower, vendor name, and part number by using the CLI?
The UDP-4501 protocol-port is to between which two GlobalProtect components?
A firewall engineer needs to patch the company’s Palo Alto Network firewalls to the latest version of PAN-OS. The company manages its firewalls by using panorama. Logs are forwarded to Dedicated Log Collectors, and file samples are forwarded to WildFire appliances for analysis. What must the engineer consider when planning deployment?
An engineer is bootstrapping a VM-Series Firewall Other than the /config folder, which three directories are mandatory as part of the bootstrap package directory structure? (Choose three.)
An administrator configures a preemptive active-passive high availability (HA) pair of firewalls and configures the HA election settings on firewall-02 with a device priority value of 100, and firewall-01 with a device priority value of 90.
When firewall-01 is rebooted, is there any action taken by the firewalls?
Please match the terms to their corresponding definitions.
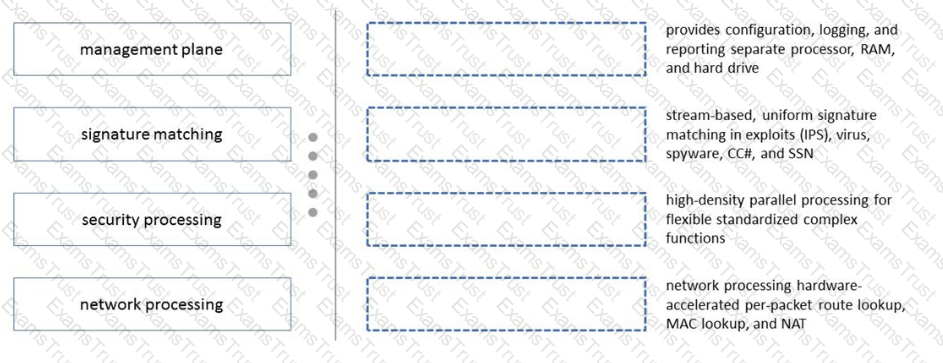
An engineer is troubleshooting a traffic-routing issue.
What is the correct packet-flow sequence?
Refer to the exhibit.
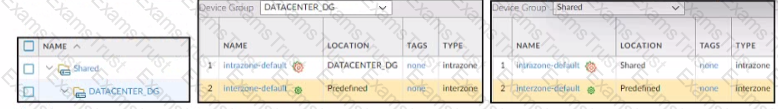
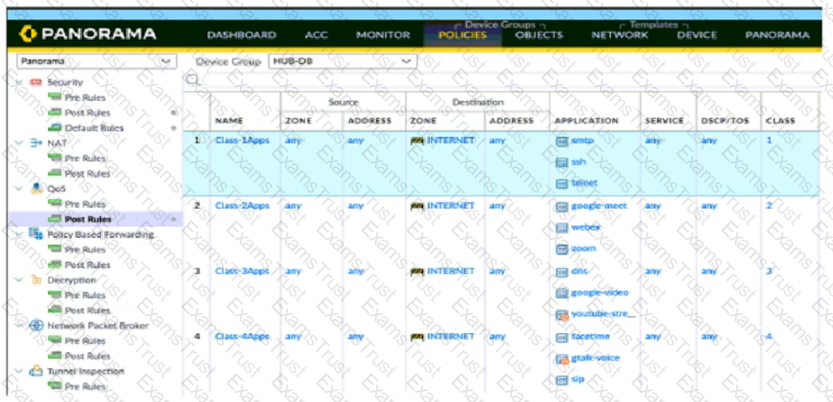
Based on the screenshots above what is the correct order in which the various rules are deployed to firewalls inside the DATACENTER_DG device group?
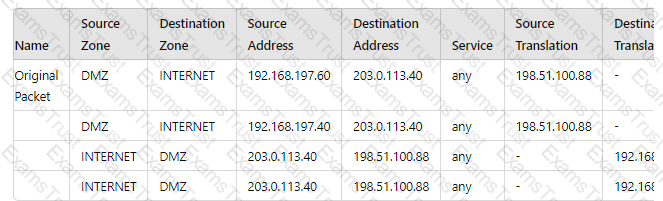
A new application server 192.168.197.40 has been deployed in the DMZ. There are no public IP addresses available resulting in the server sharing MAT IP 198 51 100 B8 with another OMZ serve that uses IP address 192 168 19? 60 Firewall security and NAT rules have been configured The application team has confirmed mat the new server is able to establish a secure connection to an external database with IP address 203.0.113.40. The database team reports that they are unable to establish a secure connection to 196 51 100 88 from 203.0.113.40 However it confirm a successful prig test to 198 51 100 88 Referring to the MAT configuration and traffic logs provided how can the firewall engineer resolve the situation and ensure inbound and outbound connections work concurrently for both DMZ servers?
A customer wants to enhance the protection provided by their Palo Alto Networks NGFW deployment to cover public-facing company-owned domains from misconfigurations that point records to third-party sources. Which two actions should the network administrator perform to achieve this goal? (Choose two)
An organization is interested in migrating from their existing web proxy architecture to the Web Proxy feature of their PAN-OS 11.0 firewalls. Currently. HTTP and SSL requests contain the c IP address of the web server and the client browser is redirected to the proxy
Which PAN-OS proxy method should be configured to maintain this type of traffic flow?
Which two components are required to configure certificate-based authentication to the web Ul when an administrator needs firewall access on a trusted interface'? (Choose two.)
An engineer is configuring a firewall with three interfaces:
• MGT connects to a switch with internet access.
• Ethernet1/1 connects to an edge router.
• Ethernet1/2 connects to a visualization network.
The engineer needs to configure dynamic updates to use a dataplane interface for internet traffic. What should be configured in Setup > Services > Service Route Configuration to allow this traffic?
An administrator is tasked to provide secure access to applications running on a server in the company's on-premises datacenter.
What must the administrator consider as they prepare to configure the decryption policy?
A company wants to implement threat prevention to take action without redesigning the network routing.
What are two best practice deployment modes for the firewall? (Choose two.)
An existing log forwarding profile is currently configured to forward all threat logs to Panorama. The firewall engineer wants to add syslog as an additional log forwarding method. The requirement is to forward only medium or higher severity threat logs to syslog. Forwarding to Panorama must not be changed.
Which set of actions should the engineer take to achieve this goal?
What should an engineer consider when setting up the DNS proxy for web proxy?
A network security administrator wants to inspect HTTPS traffic from users as it egresses through a firewall to the Internet/Untrust zone from trusted network zones.
The security admin wishes to ensure that if users are presented with invalid or untrusted security certificates, the user will see an untrusted certificate warning.
What is the best choice for an SSL Forward Untrust certificate?
Which two factors should be considered when sizing a decryption firewall deployment? (Choose two.)
An engineer configures a specific service route in an environment with multiple virtual systems instead of using the inherited global service route configuration.
What type of service route can be used for this configuration?
What does the User-ID agent use to find login and logout events in syslog messages?
An engineer is configuring secure web access (HTTPS) to a Palo Alto Networks firewall for management.
Which profile should be configured to ensure that management access via web browsers is encrypted with a trusted certificate?
A security team has enabled real-time WildFire signature lookup on all its firewalls. Which additional action will further reduce the likelihood of newly discovered malware being allowed through the firewalls?
After switching to a different WAN connection, users have reported that various websites will not load, and timeouts are occurring. The web servers work fine from other locations.
The firewall engineer discovers that some return traffic from these web servers is not reaching the users behind the firewall. The engineer later concludes that the maximum transmission unit (MTU) on an upstream router interface is set to 1400 bytes.
The engineer reviews the following CLI output for ethernet1/1.
Which setting should be modified on ethernet1/1 to remedy this problem?
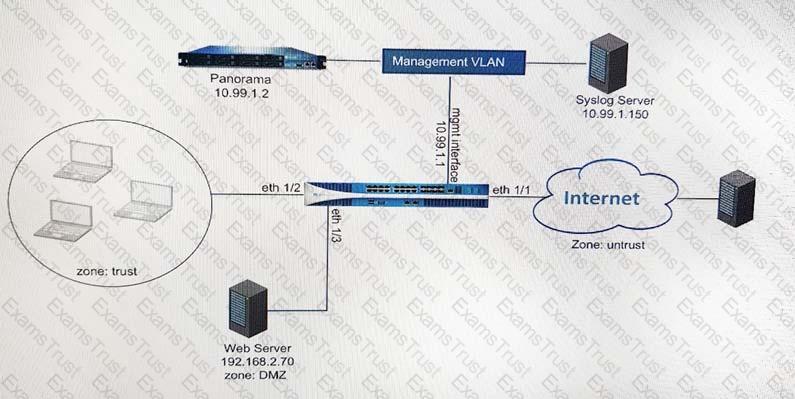
Refer to the diagram. Users at an internal system want to ssh to the SSH server. The server is configured to respond only to the ssh requests coming from IP 172.16.16.1.
In order to reach the SSH server only from the Trust zone, which Security rule and NAT rule must be configured on the firewall?
As a best practice, which URL category should you target first for SSL decryption?
An administrator is configuring a Panorama device group. Which two objects are configurable? (Choose two.)
You are auditing the work of a co-worker and need to verify that they have matched the Palo Alto Networks Best Practices for Anti-Spyware Profiles.
For which three severity levels should single-packet captures be enabled to meet the Best Practice standard? (Choose three.)