Which playbook functionality allows grouping of tasks to create functional building blocks?
Why is it important to document notes from the Proof of Value (POV) for post-sales hand off?
What must a customer deploy prior to collecting endpoint data in Cortex XSIAM?
Cortex XSOAR has extracted a malicious Internet Protocol (IP) address involved in command-and-control (C2) traffic.
What is the best method to block this IP from communicating with endpoints without requiring a configuration change on the firewall?
A Cortex XSIAM customer is unable to access their Cortex XSIAM tenant.
Which resource can the customer use to validate the uptime of Cortex XSIAM?
A customer has purchased Cortex XDR and requires phone support for the product.
Which Palo Alto Networks offering would fulfill this need?
"Bob" is a Demisto user. Which command is used to add 'Bob" to an investigation from the War Room CLI?
Cortex XDR external data ingestion processes ingest data from which sources?
Which feature of Cortex XSIAM displays an entire picture of an attack, including the originating process or delivery point?
A General Purpose Dynamic Section can be added to which two layouts for incident types? (Choose two)
When running a Cortex XSIAM proof of value (POV), why is it important to deploy the Cortex XDR agent?
An administrator has a critical group of systems running Windows XP SP3 that cannot be upgraded The administrator wants to evaluate the ability of Traps to protect these systems and the word processing applications running on them
How should an administrator perform this evaluation?
Which Cortex XDR capability allows for the immediate termination of a process discovered during investigation of a security event?
Where is the output of the task visible when a playbook task errors out?
Why is Premium Customer Success an important part of any Cortex bill of materials?
What method does the Traps agent use to identify malware during a scheduled scan?
How does an "inline" auto-extract task affect playbook execution?
What is the function of reputation scoring in the Threat Intelligence Module of Cortex XSIAM?
Which two filter operators are available in Cortex XDR? (Choose two.)
What are two manual actions allowed on War Room entries? (Choose two.)
What is a benefit of user entity behavior analytics (UEBA) over security information and event management (SIEM)?
For which two purposes can Cortex XSOAR engines be deployed? (Choose two.)
What are two reasons incident investigation is needed in Cortex XDR? (Choose two.)
Which action should be performed by every Cortex Xpanse proof of value (POV)?
An Administrator is alerted to a Suspicious Process Creation security event from multiple users.
The users believe that these events are false positives Which two steps should the administrator take to confirm the false positives and create an exception? (Choose two )
What is the difference between an exception and an exclusion?
Which statement best describes the benefits of the combination of Prisma Cloud, Cortex Xpanse, and partner services?
Which four types of Traps logs are stored within Cortex Data Lake?
In the DBotScore context field, which context key would differentiate between multiple entries for the same indicator in a multi-TIP environment?
Which three Demisto incident type features can be customized under Settings > Advanced > Incident Types? (Choose three.)
A customer has purchased Cortex XSOAR and has a need to rapidly stand up the product in their environment. The customer has stated that their internal staff are currently occupied with other projects.
Which Palo Alto Networks service offering should be recommended to the customer?
In an Air-Gapped environment where the Docker package was manually installed after the Cortex XSOAR installation which action allows Cortex XSOAR to access Docker?
A prospective customer is interested in Cortex XDR but is enable to run a product evaluation.
Which tool can be used instead to showcase Cortex XDR?
Which technology allows a customer to integrate Cortex Xpanse with third-party applications or services, assets, and IP ranges while leveraging investigation capabilities?
Which two Cortex XSOAR incident type features can be customized under Settings > Advanced > Incident Types? (Choose two.)
Which feature of Cortex XSIAM helps analyst reduce the noise and false positives that often plague traditional SIEM systems?
What does Cortex Xpanse ingest from XDR endpoints?
Which two actions are required to add indicators to the whitelist? (Choose two.)
What allows the use of predetermined Palo Alto Networks roles to assign access rights to Cortex XDR users?
Which feature of Cortex Xpanse allows it to identify previously unknown assets?
Which service helps identify attackers by combining world-class threat intelligence with Cortex XSIAM technology?
Which attack method is a result of techniques designed to gain access through vulnerabilities in the code of an operating system (OS) or application?
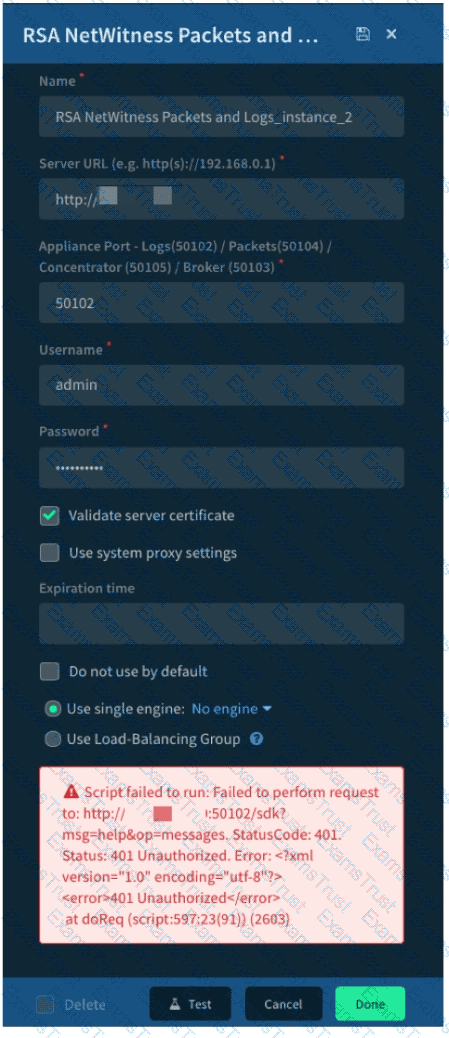
Given the integration configuration and error in the screenshot what is the cause of the problem?
Which command is used to add Cortex XSOAR "User1" to an investigation from the War Room command-line interface (CLI)?
The prospect is deciding whether to go with a phishing or a ServiceNow use case as part of their POC We have integrations for both but a playbook for phishing only Which use case should be used for the POC?
Which two troubleshooting steps should be taken when an integration is failing to connect? (Choose two.)
An EDR project was initiated by a CISO. Which resource will likely have the most heavy influence on the project?
Which product enables the discovery, exchange, and contribution of security automation playbooks, built into Cortex XSOAR?
On a multi-tenanted v6.2 Cortex XSOAR server, which path leads to the server.log for "Tenant1"?
What is a key difference between audit users and full users in Cortex XSOAR?