An API implementation is updated. When must the RAML definition of the API also be updated?
An established communications company is beginning its API-led connectivity journey, The company has been using a successful Enterprise Data Model for many years. The company has identified a self-service account management app as the first effort for API-led, and it has identified the following APIs.
Experience layer: Mobile Account Management EAPI, Browser Account Management EAPI
Process layer: Customer Lookup PAPI, Service Lookup PAPI, Account Lookup PAPI
System layer: Customer SAPI, Account SAPI, Product SAPI, Service SAPI
According to MuleSoft's API-led connectivity approach, which API would not be served by the Enterprise Data Model?
When should idempotency be taken into account?
What is true about API implementations when dealing with legal regulations that require all data processing to be performed within a certain jurisdiction (such as in the USA or the EU)?
A circuit breaker strategy is planned in order to meet the goal of improved response time and demand on a downstream API.
* Circuit Open: More than 10 errors per minute for three minutes
* Circuit Half-Open: One error per minute
* Circuit Closed: Less than one error per minute for five minutes
Out of several proposals from the engineering team, which option will meet this goal?
A Platform Architect inherits a legacy monolithic SOAP-based web service that performs a number of tasks, including showing all policies belonging to a client. The service connects to two back-end systems — a life-insurance administration system and a general-insurance administration system — and then queries for insurance policy information within each system, aggregates the results, and presents a SOAP-based response to a user interface (UI).
The architect wants to break up the monolithic web service to follow API-led conventions.
Which part of the service should be put into the process layer?
Refer to the exhibit. An organization is running a Mule standalone runtime and has configured Active Directory as the Anypoint Platform external Identity Provider. The organization does not have budget for other system components.
What policy should be applied to all instances of APIs in the organization to most effecuvelyKestrict access to a specific group of internal users?
What is true about the technology architecture of Anypoint VPCs?
What is true about where an API policy is defined in Anypoint Platform and how it is then applied to API instances?
An API has been updated in Anypoint exchange by its API producer from version 3.1.1 to 3.2.0 following accepted semantic versioning practices and the changes have been communicated via the APIs public portal. The API endpoint does NOT change in the new version. How should the developer of an API client respond to this change?
A customer wants to host their MuleSoft applications in CloudHub 1.0, and these applications should be available at the domain
After creating a dedicated load balancer (DLB) called acme-dib-prod, which further action must the customer take to complete the configuration?
What are the major benefits of MuleSoft proposed IT Operating Model?
An API is protected with a Client ID Enforcement policy and uses the default configuration. Access is requested for the client application to the API, and an approved
contract now exists between the client application and the API
How can a consumer of this API avoid a 401 error "Unauthorized or invalid client application credentials"?
A retail company with thousands of stores has an API to receive data about purchases and insert it into a single database. Each individual store sends a batch of purchase data to the API about every 30 minutes. The API implementation uses a database bulk insert command to submit all the purchase data to a database using a custom JDBC driver provided by a data analytics solution provider. The API implementation is deployed to a single CloudHub worker. The JDBC driver processes the data into a set of several temporary disk files on the CloudHub worker, and then the data is sent to an analytics engine using a proprietary protocol. This process usually takes less than a few minutes. Sometimes a request fails. In this case, the logs show a message from the JDBC driver indicating an out-of-file-space message. When the request is resubmitted, it is successful. What is the best way to try to resolve this throughput issue?
A team is planning to enhance an Experience API specification, and they are following API-led connectivity design principles.
What is their motivation for enhancing the API?
A Rate Limiting policy is applied to an API implementation to protect the back-end system. Recently, there have been surges in demand that cause some API client
POST requests to the API implementation to be rejected with policy-related errors, causing delays and complications to the API clients.
How should the API policies that are applied to the API implementation be changed to reduce the frequency of errors returned to API clients, while still protecting the back-end
system?
Which of the following sequence is correct?
Which component monitors APIs and endpoints at scheduled intervals, receives reports about whether tests pass or fail, and displays statistics about API and endpoint
performance?
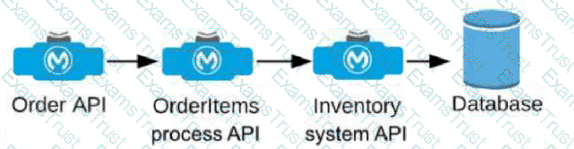
An Order API triggers a sequence of other API calls to look up details of an order's items in a back-end inventory database. The Order API calls the OrderItems process API, which calls the Inventory system API. The Inventory system API performs database operations in the back-end inventory database.
The network connection between the Inventory system API and the database is known to be unreliable and hang at unpredictable times.
Where should a two-second timeout be configured in the API processing sequence so that the Order API never waits more than two seconds for a response from the Orderltems process API?
A code-centric API documentation environment should allow API consumers to investigate and execute API client source code that demonstrates invoking one or more APIs as part of representative scenarios.
What is the most effective way to provide this type of code-centric API documentation environment using Anypoint Platform?
What API policy would LEAST likely be applied to a Process API?
What is typically NOT a function of the APIs created within the framework called API-led connectivity?
A large organization with an experienced central IT department is getting started using MuleSoft. There is a project to connect a siloed back-end system to a new
Customer Relationship Management (CRM) system. The Center for Enablement is coaching them to use API-led connectivity.
What action would support the creation of an application network using API-led connectivity?
When could the API data model of a System API reasonably mimic the data model exposed by the corresponding backend system, with minimal improvements over the backend system's data model?
What CANNOT be effectively enforced using an API policy in Anypoint Platform?
An organization wants MuleSoft-hosted runtime plane features (such as HTTP load balancing, zero downtime, and horizontal and vertical scaling) in its Azure environment. What runtime plane minimizes the organization's effort to achieve these features?
What Mule application deployment scenario requires using Anypoint Platform Private Cloud Edition or Anypoint Platform for Pivotal Cloud Foundry?
An online store's marketing team has noticed an increase in customers leaving online baskets without checking out. They suspect a technology issue is at the root cause of the baskets being left behind. They approach the Center for Enablement to ask for help identifying the issue. Multiple APIs from across all the layers of their application network are involved in the shopping application.
Which feature of the Anypoint Platform can be used to view metrics from all involved APIs at the same time?
A Mule application exposes an HTTPS endpoint and is deployed to the CloudHub Shared Worker Cloud. All traffic to that Mule application must stay inside the AWS VPC.
To what TCP port do API invocations to that Mule application need to be sent?
An eCommerce company is adding a new Product Details feature to their website, A customer will launch the product catalog page, a new Product Details link will
appear by product where they can click to retrieve the product detail description. Product detail data is updated with product update releases, once or twice a year, Presently
the database response time has been very slow due to high volume.
What action retrieves the product details with the lowest response time, fault tolerant, and consistent data?
A company uses a hybrid Anypoint Platform deployment model that combines the EU control plane with customer-hosted Mule runtimes. After successfully testing a Mule API implementation in the Staging environment, the Mule API implementation is set with environment-specific properties and must be promoted to the Production environment. What is a way that MuleSoft recommends to configure the Mule API implementation and automate its promotion to the Production environment?
A Mule application exposes an HTTPS endpoint and is deployed to three CloudHub workers that do not use static IP addresses. The Mule application expects a high volume of client requests in short time periods. What is the most cost-effective infrastructure component that should be used to serve the high volume of client requests?
The responses to some HTTP requests can be cached depending on the HTTP verb used in the request. According to the HTTP specification, for what HTTP verbs is this safe to do?
Question 10: Skipped
An API implementation returns three X-RateLimit-* HTTP response headers to a requesting API client. What type of information do these response headers indicate to the API client?
A business process is being implemented within an organization's application network. The architecture group proposes using a more coarse-grained application
network design with relatively fewer APIs deployed to the application network compared to a more fine-grained design.
Overall, which factor typically increases with a more coarse-grained design for this business process implementation and deployment compared with using a more fine-grained
design?
Which of the below, when used together, makes the IT Operational Model effective?
A manufacturing company has deployed an API implementation to CloudHub and has not configured it to be automatically restarted by CloudHub when the worker is
not responding.
Which statement is true when no API Client invokes that API implementation?
In which layer of API-led connectivity, does the business logic orchestration reside?
What API policy would be LEAST LIKELY used when designing an Experience API that is intended to work with a consumer mobile phone or tablet application?
What do the API invocation metrics provided by Anypoint Platform provide?
When must an API implementation be deployed to an Anypoint VPC?
What correctly characterizes unit tests of Mule applications?
Which out-of-the-box key performance indicator measures the success of a typical Center for Enablement and is immediately available in responses from Anypoint Platform APIs?
A company is building an application network using MuleSoft's recommendations for various API layers.
What is the main (default) role of a process API in an application network?
What Mule application can have API policies applied by
Anypoint Platform to the endpoint exposed by that Mule application?
A) A Mule application that accepts requests over HTTP/1.x

B) A Mule application that accepts JSON requests over TCP but is NOT required to provide a response
C) A Mute application that accepts JSON requests over WebSocket
D) A Mule application that accepts gRPC requests over HTTP/2